
Have you ever wondered what happens to zero-day exploits after their big splash on day zero? Often 0-days are developed to target a specific organization, as in this Pawn Storm-related instance reported by Trend Micro, which targeted specific people within the Foreign Affairs Ministry.
However after it’s publicized, and a patch becomes available, does the zero-day go away? Of course not. Can you imagine hackers saying “oh dearie me, now there’s a patch for this so I guess I better stop using it”? Actually, it’s the opposite. Once the vulnerability becomes public, evildoers are excited to use the exploit since they know that the vast majority of organizations have not yet patched it, and won’t patch it for another few weeks/months/ dare we say years ;).
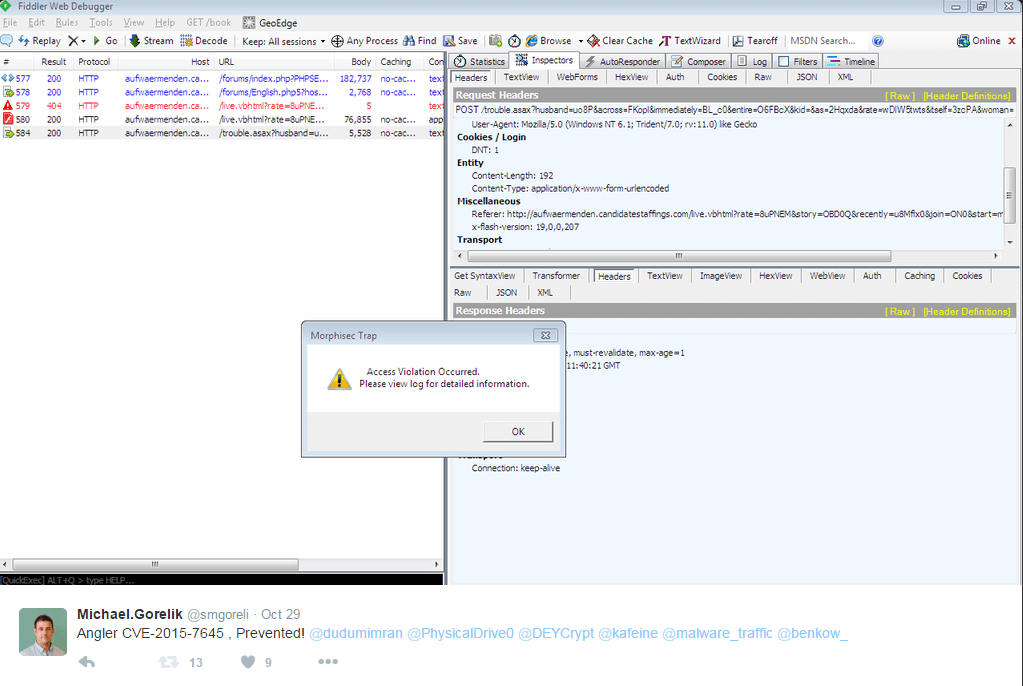
Not all hackers are equally knowledgeable about how to use these so-called exploits, so to make their lives easier, each new one is quickly integrated into exploit kits – e.g. the most popular Angler and Nuclear – which allows it to be leveraged even by entry-level hackers. That’s when it goes from being a targeted hack to more broad-based. A point in case is Angler CVE-2015-7645 caught in real-time and tweeted about on October 29, 2015, by Morphisec.
The propagation of this exploit was swift and broad. The screenshots below, from within the Morphisec Moving Target Defense management server, identify the exploit’s propagation to sites compromised by Angler.
The craftiness (and the danger) of these newest exploits is that the malicious code oftentimes isn’t actually situated within the code that injects itself into the unsuspecting user’s device. It is simply a sort of dialer that calls a host to obtain the missing malicious code components that are sitting out there on the interwebs, waiting for their moment in the sun.
And here’s where it gets really interesting. Following a zero-day, attackers inject hundreds of vulnerable websites; the propagation of the infection to new unaware sites happens quickly, and automatically. Unsuspecting surfers access these websites and trigger redirections to the malicious exploit kit hosting sites. Interesting to note we usually see a chain of redirections.
Through web crawling and site scanning managed by Morphisec’s labs, we have identified hundreds of sites around the world that are infected with forms of malware that can infect users through various known application vulnerabilities. As an exercise, we tracked this most recent version of the Pawn Storm exploits, and found that within just a few days of its publication, it had propagated far and wide to sites in east Asia and western Europe.
As you can see from the automated forensic analysis screenshots below from our Moving Target Defense solution (currently in beta), the exploit employs a chain of URL redirection that doesn’t give up until it finds a site that has the active malicious code on it. A user may be unwittingly redirected multiple times until the exploit locates the active code it is looking for.
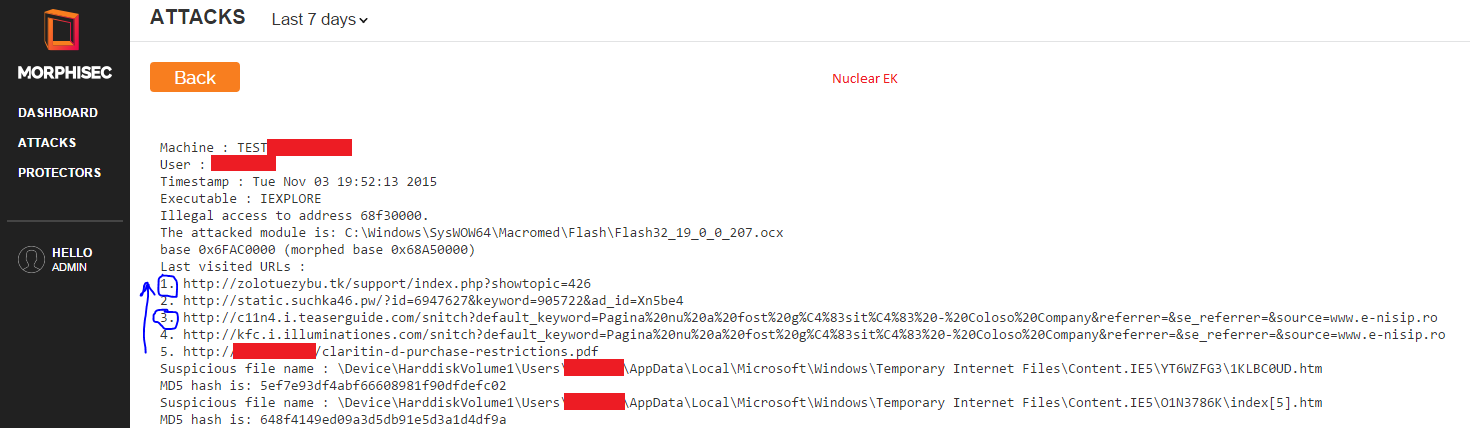
Here is a screenshot from an end-point in western Europe on which Morphisec intercepted an interesting five-site redirection chain for Nuclear EK:
When the user tried to open a PDF stored on a compromised site it was redirected to kfc.i.illuminationes.com (previously seen in other attacks as part of a big nuclear malvertising campaign compromising multiple wordpress sites and redirecting it to the Nuclear EK host). As you can see, there is a second redirection after the first one fails to hxxp://static.suchka46.pwXn5be4 that redirects further to the currently active Nuclear EK hosted site zolotuezybu.tk (as described in my previous post the redirection is modified within very short time intervals).
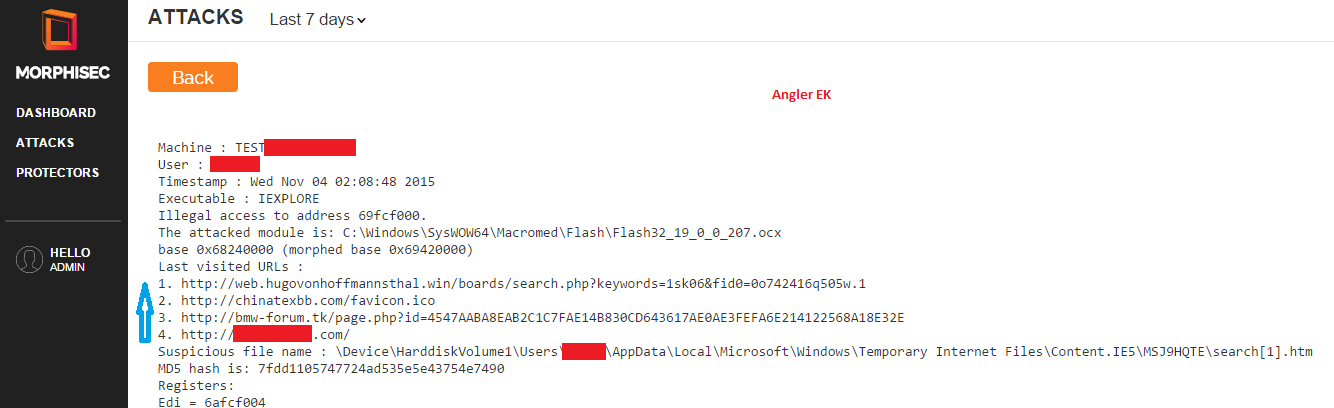
In the next screenshot, taken from an end-point in east Asia, Morphisec prevented Angler EK’s latest zero-day, and automatically and instantaneously presented the full redirection chain of four sites:
And in case you were wondering (if it wasn’t obvious from all the analysis above…), Morphisec’s Moving Target Defense (of course) blocks this exploit.




.png?width=571&height=160&name=iso27001-(2).png)