“If an attacker successfully hacks our workstations or trading terminals, they’d have full access to the firm’s critical infrastructure.” This quote from a Chief Information Security Officer at a leading US-based hedge fund shines a light on the...
Read MoreIn today’s threat landscape, multiple defense-in-depth layers are one of the only ways security teams can achieve peace of mind. Why? Two reasons stand out:
Read MoreGartner® has published a new report focused onAutomated Moving Target Defense (AMTD) technology innovation. According to Gartner: “Combining AMTD solutions at different layers of the technology stack provides innovation leaders with a highly...
Read MoreCyberattacks targeting critical OT and industrial organizations rose by 87% last year—the threat level to OT is higher than ever, and threat actors are finding new ways to compromise OT environments.
Read MoreMorphisec has been recognized as a sample vendor in Gartner’s Emerging Tech: Security — Emergence Cycle for Automated Moving Target Defense Report—research covering groundbreaking security technologies that according to Gartner, “are paving the way...
Read MoreThere’s now a new ransomware attack, on average, every 10 seconds. Threat actors have become powerful and sophisticated enough to successfully hold national governments—such as Ireland and Costa Rica—to ransom.
Read MoreThe Aurora stealer is a notorious Golang-based information stealer that's been gaining popularity from the end of 2022 through the first quarter of 2023. The Morphisec Threat Labs team has been tracing its activities using our prevention telemetry...
Read MoreLegacy Microsoft operating systems (OSs) will probably be with us until the universe’s heat death. OS usage statistics show the total market share of legacy operating systems is still above 10 percent. With the total Windows installation base of 1.3...
Read MoreFew executives doubt their organizations must pay more attention to cybersecurity. Cybercrime costs were estimated at $8.4 trillion globally in 2022 alone, and could exceed $20 trillion by 2026. No organization can afford to ignore this risk.
Read MoreFileless malware attacks are a malicious code execution technique that works completely within process memory. In a fileless attack, no files are dropped onto a hard drive. With no artifacts on the hard drive to detect, these attacks easily evade...
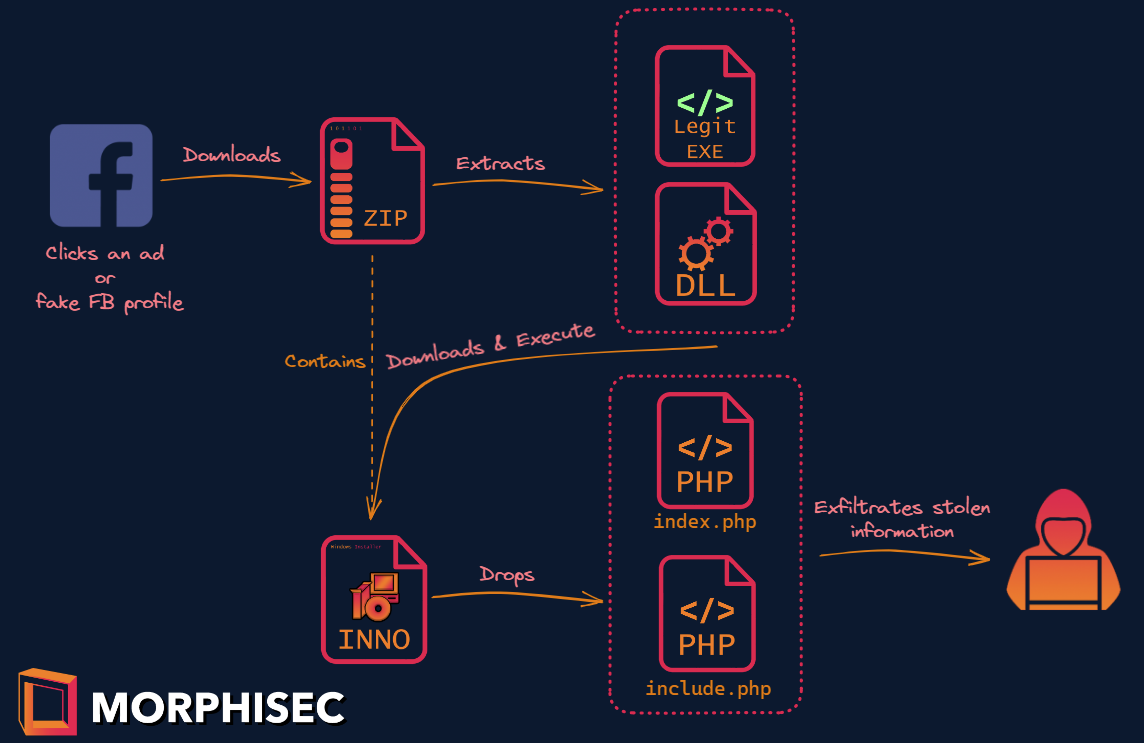
Read MoreStarting in November 2022, Morphisec has been tracking an advanced info stealer we have named “SYS01 stealer.” SYS01 stealer uses similar lures and loading techniques to another information stealer recently dubbed S1deload by the Bitdefender group,...
Read MoreSecurity success doesn't happen in a vacuum. Security conferences give practitioners, decision-makers, and vendors a chance to get outside the bubble of day-to-day life. So, what are the top in-person and virtual cybersecurity conferences in 2023?
Read MoreMorphisec has recently identified a highly evasive malware campaign delivering ProxyShellMiner to Windows endpoints.
Read MoreAs of January 10th 2023, Windows 7, Windows 8, 8.1, their Windows embedded derivatives, and Windows Server 2008 R2 will no longer receive patches from Microsoft. Millions of devices will now become "legacy" and create a suite of new legacy security...
Read MoreDuring November, Morphisec identified a brand-new variant of Babuk ransomware while investigating a customer's prevention event. Babuk was first discovered at the beginning of 2021, when it began targeting businesses to steal and encrypt data in...
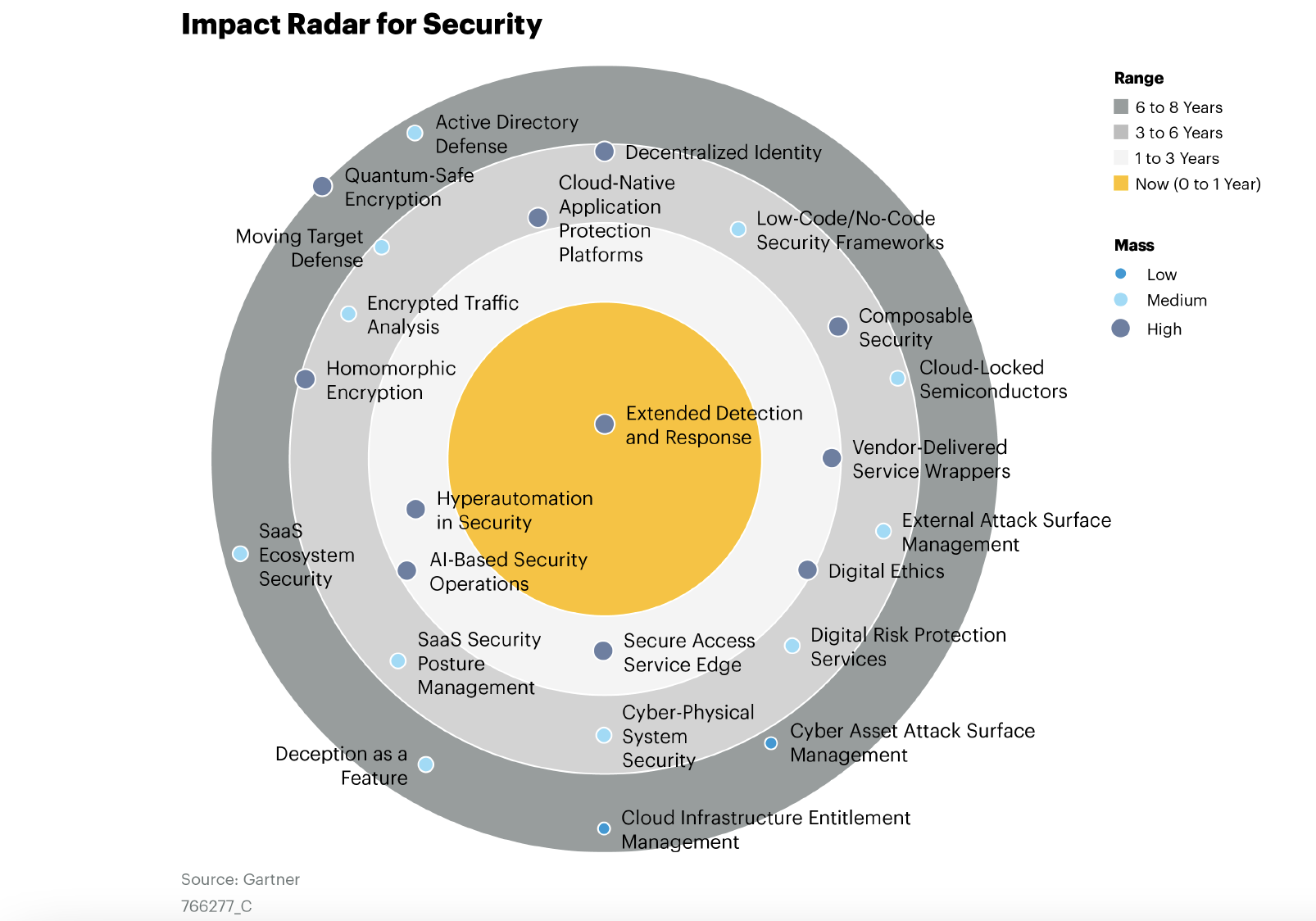
Read MoreFor the second consecutive year, Gartner has highlighted Moving Target Defense (MTD) as a featured technology, and Morphisec as a Sample Vendor for the technology in their report, Emerging Tech Impact Radar: Security. The authors define MTD as “......
Read MoreSearch Our Site
Recent Posts
Posts by Tag
- Moving Target Defense (129)
- Cyber Security News (124)
- Morphisec Labs (113)
- Threat Research (64)
- Threat Post (61)
- Morphisec News (52)
- Automated Moving Target Defense (11)
- Defense-in-Depth (6)
- in-memory attacks (6)
- Gartner (4)
- Ransomware (4)
- runtime attacks (4)
- Legacy security (3)
- Linux cyber security (3)
- advanced threat defense (3)
- threat and vulnerability management (3)
- ChatGPT (2)
- Evasive loader (2)
- Fileless malware (2)
- Gartner endpoint protection (2)
- financial cybersecurity (2)
- patch management (2)
- Adaptive Exposure Management (1)
- Anti-tampering (1)
- Gartner Emerging Tech (1)
- Healthcare cybersecurity (1)
- IoT security (1)
- Securing IoT devices (1)
- Server security (1)






















.png?width=571&height=160&name=iso27001-(2).png)