The Aurora stealer is a notorious Golang-based information stealer that's been gaining popularity from the end of 2022 through the first quarter of 2023. The Morphisec Threat Labs team has been tracing its activities using our prevention telemetry along with dark-web activities.
In this blog post however, we aren’t going to cover Aurora, but a sometimes overlooked, extremely critical component of the attack delivery chain. The component that makes Aurora’s delivery stealthy and dangerous is a highly evasive loader we named “in2al5d p3in4er.”
The in2al5d p3in4er loader is compiled with Embarcadero RAD Studio and targets endpoint workstations using advanced anti-VM (virtual machine) technique we describe in detail in this post.
We also cover new techniques with significant negative outcomes that represent a concerning change in the landscape, especially in the new era of ChatGPT.
Delivery
Threat actors always find innovative ways to spread malware and access sensitive information. One growing trend is using YouTube as a malware distribution channel. Hackers take over popular YouTube accounts and post videos with links to malicious websites or downloads. To increase video visibility, they use search engine optimization (SEO) tags to make a video rank higher in search results.
Stealing YouTube accounts is a lucrative business for cybercriminals. Many underground forums and marketplaces offer these services for a fee. The threat actor in this post appears to be using this method as a service, including the websites the videos redirect to.
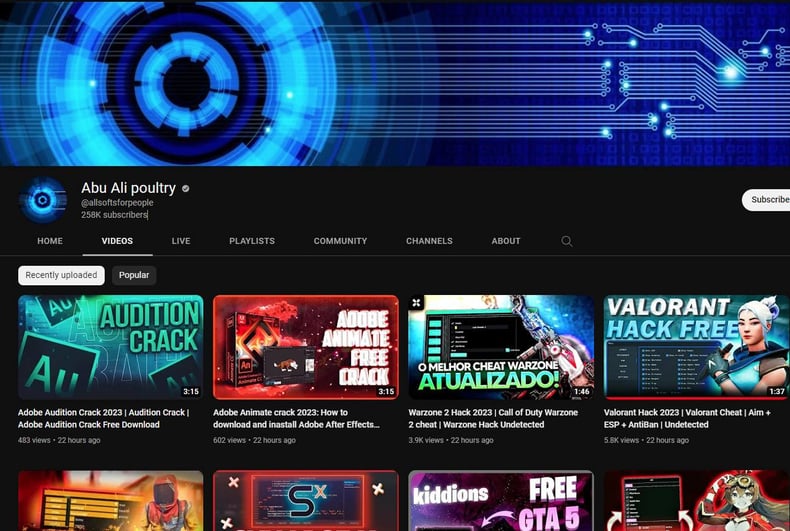
Compromised YouTube channel
The service uses artificial intelligence (AI) to generate videos. This streamlines the process of creating convincing budget backed content. And it allows threat actors to automate diverse lure creation, such as fake software that tricks users into clicking on links.
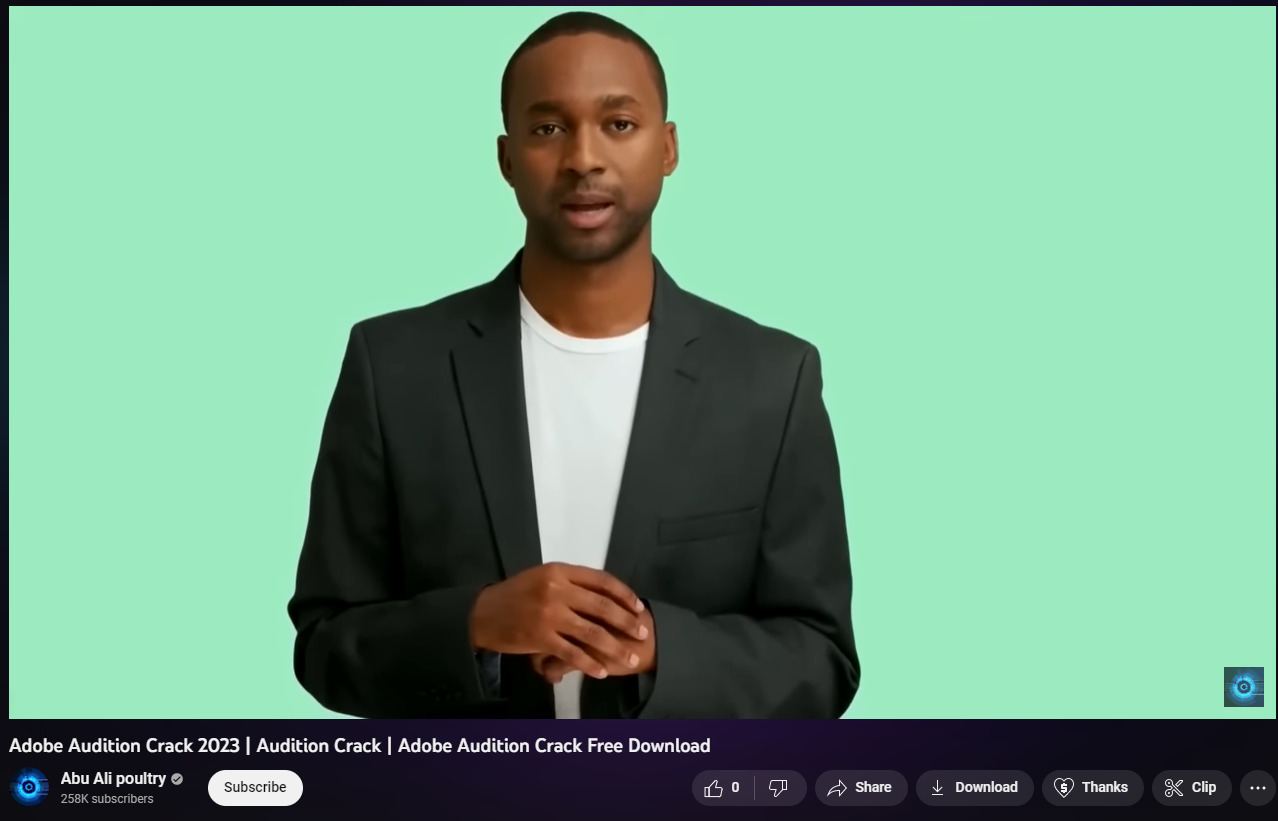
Example video with download instructions
The above video redirects to different websites that look legitimate.

Fake websites redirected by the YouTube video
The service the threat actors are using enables the creation of decoy websites that look identical to the original websites. These fake websites use similar URLs, logos, and branding to convincingly appear legitimate. Once a user visits one of these sites, they’re enticed to download an application containing malware or lured to enter sensitive/personal information into the decoy generated website. These websites use geographical targeting to deliver content based on the visitor’s geo-location.
The website below is a clone of jobseeker.com
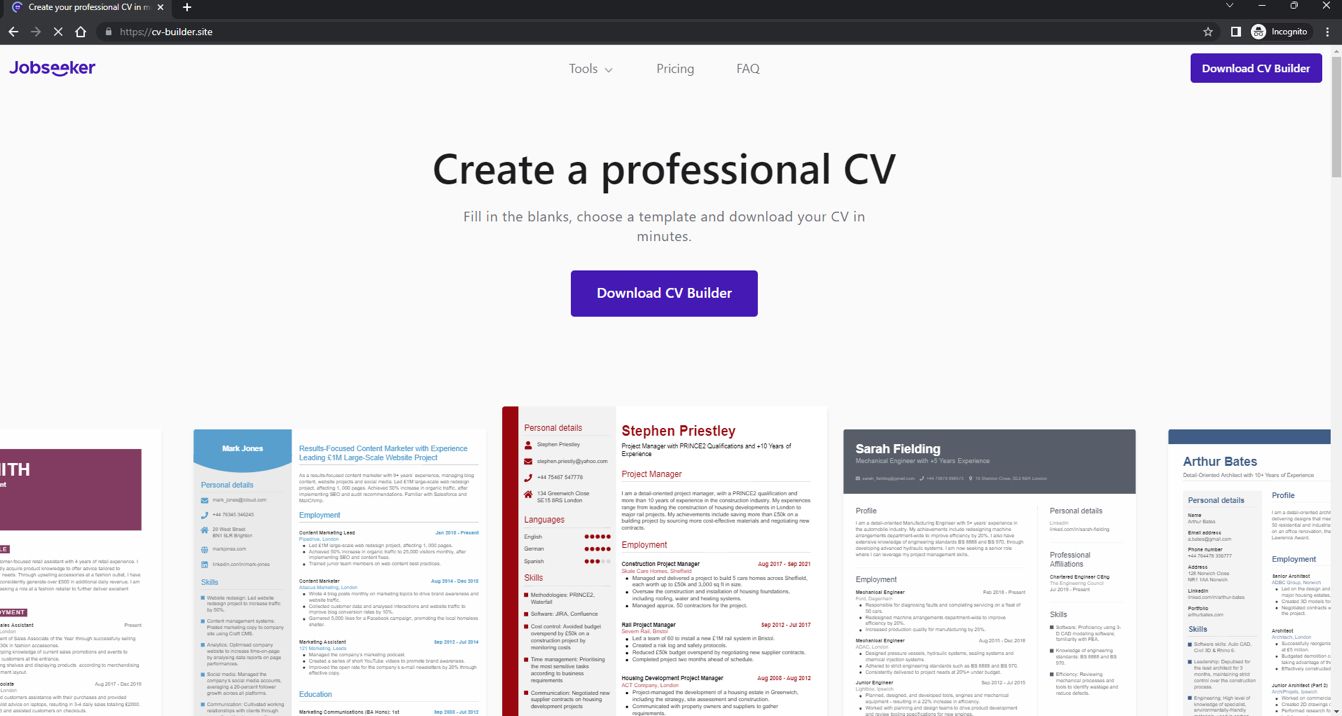
Decoy website for jobseeker.com
Technical Analysis
This loader uses a surprisingly simple yet highly effective evasion technique. It leverages the usage of CreateDXGIFactory function of dxgi.dll library to query the vendor ID of the graphics card installed on a system. The ID is then compared against a whitelist of vendor IDs; specifically, the 0x10de (NVIDIA), 0x1002 (AMD), and 0x8086 (Intel) graphics cards. If the vendor ID doesn’t match the whitelisted values, the loader makes it appear as a benign application by terminating itself.
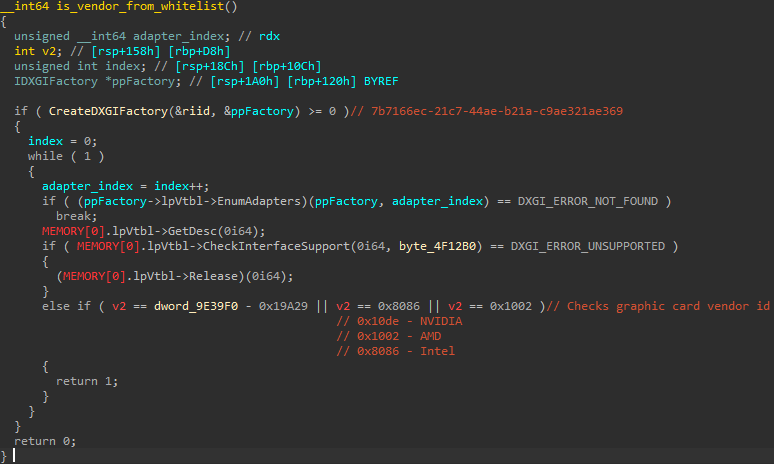
The anti-VM function checks the graphics vendor ID
After checking the vendor IDs, the loader decrypts the final payload in separate chunks and injects it into `sihost.exe` using a process hollowing technique.
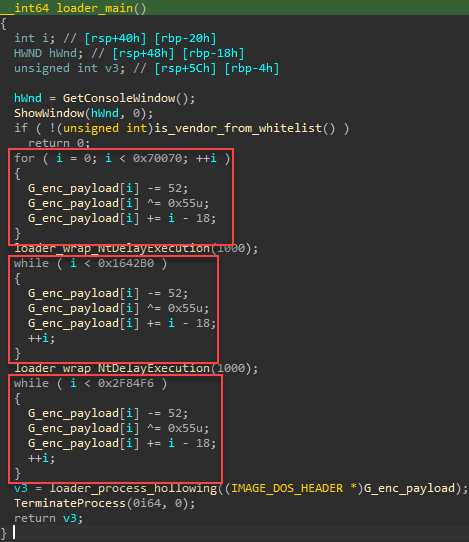
Payload decryption routine
Some samples of the loader do not use the process hollowing technique. Instead, they allocate memory to write the decrypted payload into the allocated memory, and then make a call to the payload entry point (EP).
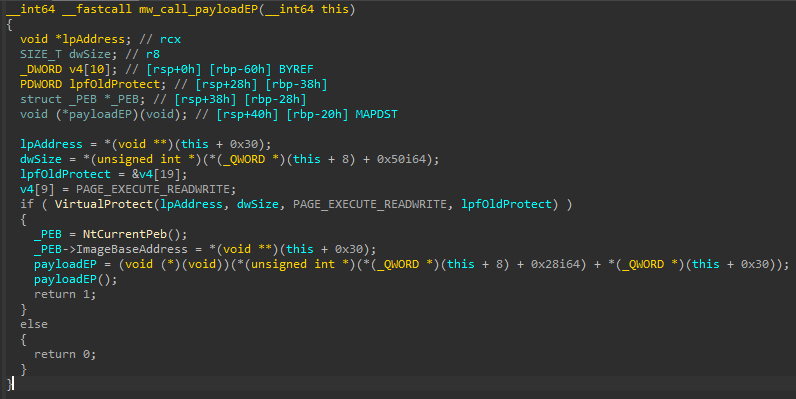 Payload injection
Payload injection
During the injection process, all loader samples resolve the necessary Win APIs dynamically and decrypt these names using a XOR key: "in2al5d p3in4er" (invalid printer), as illustrated in the figure below.
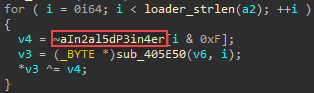
String decryption routine using the "invalid printer" key
Another element helping the low detection rate on VirusTotal is the threat actor using Embarcadero RAD Studio to generate executables. Embarcadero RAD Studio is an integrated development environment (IDE) for building software applications that runs on various platforms and operating systems.
Examining samples from our investigation, we found the threat actor is compiling executables using several options from the Embarcadero IDE. Those with the lowest detection rate on VirusTotal are compiled using “BCC64.exe”, a new Clang based C++ compiler from Embarcadero. This compiler is based on a different code base than a “Standard Library” (Dinkumware) or “Runtime Library” (compiler-rt) and generates optimized code which changes the entry point and execution flow. This breaks security vendors’ indicators, such as signatures composed from “malicious/suspicious code block.”

A zero detection rate on VirusTotal
The loader is particularly successful in evading sandboxes and virtual machines. As seen in the image below, the loader has evaded execution by multiple sandboxes. This is a testament to the effectiveness of the loader's simplicity, which leverages a specific aspect of system configuration to achieve exceptional stealth.
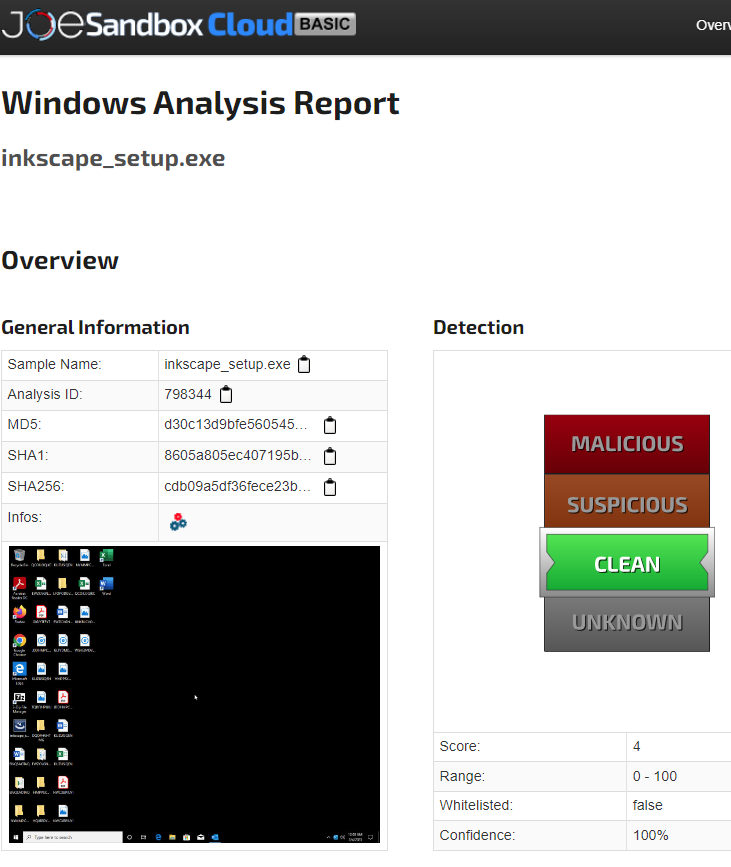
 Example of sandboxes that fail to execute
Example of sandboxes that fail to execute
Note: A similar technique for evading virtual machines was covered in 2016. It checked the graphics’ card vendor ID using the DXGI.dll. Although the anti-VM techniques observed in the wild are generally based on blacklisting, this approach uses an inverse check which only searches for graphic cards the target victim should own. This helps to evade sandbox analysis that searches for blacklists of graphic cards.
Defending Against in2al5d p3in4er
Malware loaders like in2al5d p3in4er are essentially basic delivery. They establish a foothold between an attacker and their compromised target and are typically the first stage of an attack.
The attackers behind in2al5d p3in4er are combining it with widely accessible social engineering tools for a high impact campaign that takes over popular YouTube accounts and directs viewers to convincing looking fake websites. They’re then enticed to download malware from a fake website.
One of the first steps to avoid compromise by in2al5d p3in4er is training organization employees how to detect social engineering campaigns: ensuring URLs are legitimate, and not downloading cracked versions of software.
But as the detection ratio of zero on VirusTotal makes clear, reactive, detection-based cybersecurity technologies like those used in NGAV, EPP, and EDR/XDR are barely capable of detecting and stopping in2al5d p3in4er. Stopping this loader requires different technology.
Morphisec’s Automated Moving Target Defense (AMTD) technology takes a fundamentally different approach to cybersecurity that isn’t detection-based. Instead of waiting for malware to breach a system before detecting it, Morphisec proactively secures runtime memory to prevent any unauthorized code—like in2al5d p3in4er—from executing, regardless of whether a recognizable signature or behavior pattern exists for it. To learn more about Moving Target Defense, read the free white paper: Zero Trust + Moving Target Defense—The Ultimate Ransomware Strategy.
IOCs (Indicators of Compromise)
Malicious/Compromised Websites
- cv-builder[.]site
- siamaster.com[.]mx
- chatgptex[.]us
- allfreesoftware[.]online
- all-free-software[.]online
Hash - Loader |
C2 - Aurora |
|
380978251b2c661ff15b2610763770dfa14fb360ad0ca64243e0d5d5893952cb |
45.15.156.182:8081 |
|
095b9e90e1c9d7d95f362fe381512da60bb31727c068c6dfabe055ab387aed82 |
45.15.156.70:8081 |
|
5c9f5082e44e91e1aed15261e82216e59f2668ec5b25348526aad98472c5d722 |
45.132.106.77:8081 |
|
Df99a29a0fd7f62e3798260b2068c711a5356346b7b0c0477e30643138345fba |
199.127.62.3:8081 |
|
7ed926820973cd3c14b783109094604369e37cc06cb08a338b856f4e5cf2684c |
94.142.138.73:8081 |
|
1beb12971e69fb4040d60a6bd3667cb24c48a3db0fbf814d629874ee40312405 |
94.142.138.84:8081 |
|
4accbeea02170cb5215fbe937fabae030986f84ee7acc983cc15ce120e073861 |
94.142.138.218:8081 |
|
e827cde3646048c9e09a61eeb45cc37f1d8a20190762c513ddf1e9dc13e4b897 |
199.247.24.79:8081 |
|
5e4b6272dc2d955c5e52c755ea598f44e324b04466a4e3bacf6c9d845345322b |
5.34.180.208:8081 |





.png?width=571&height=160&name=iso27001-(2).png)