As the threat landscape evolves, it presents ever-increasing risks and costs driven by progressive factors like financial incentives for threat actors, the availability of malware, expanding attack surfaces, and the sophisticated capabilities of...
Read MoreMorphisec announced the launch of the Anti-Ransomware Assurance Suite to help organizations pre-emptively reduce exposure to cyber risk, proactively prevent advance threats and ensure optimal anti-ransomware defense. Powered by Automated Moving...
Read MoreGlobally, ransomware is big business, with millions of attacks targeting organizations every day. Not every attack is financially successful, but with keen attention to detail, attackers have (and continue to) tune tactics, making ransomware a...
Read MorePreventing Ransomware and Advanced Endpoint Threats with Morphisec + Microsoft Defender for Endpoint
When it comes to endpoint security, Microsoft Defender for Endpoint is a popular choice, and is the fastest growing endpoint protection platform, boasting over 19% market share. Additionally, the solution is consistently named a “leader” in the...
Read MoreCVE-2024-2883 is a critical vulnerability found in ANGLE, a component of Google Chrome and Microsoft Edge. The vulnerability is exploitable via crafted HTML pages, allowing remote attackers to exploit heap corruption. The potential impact is high,...
Read MoreRecently, Morphisec Labs identified a significant increase in activity linked to Mispadu (also known as URSA), a banking trojan first flagged by ESET in 2019. Initially concentrated on LATAM countries and Spanish-speaking individuals, Mispadu has...
Read More(Updated March 29th, 2024)
The National Vulnerability Database (NVD) has long been a crucial resource for organizations in managing their vulnerability lifecycle and ensuring the security of their systems. However, recent developments have...
Read MoreMorphisec Threat Labs recently discovered multiple indicators of attacks leading to threat actor, UAC-0184. This discovery sheds light on the notorious IDAT loader delivering the Remcos Remote Access Trojan (RAT) to a Ukrainian entity based in...
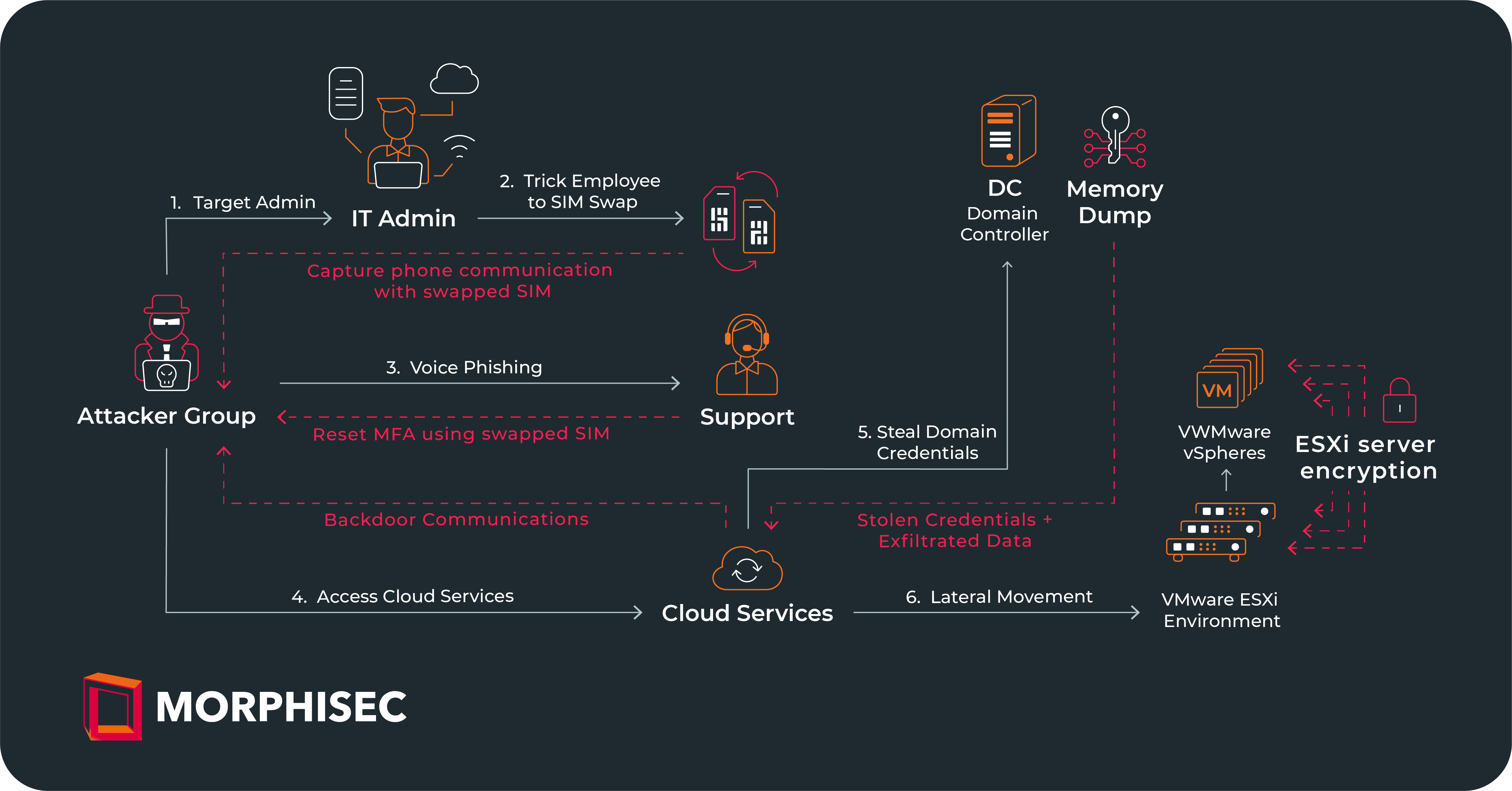
Read MoreThis blog examines the Akira Ransomware as a Service (RaaS) group, to understand their Tactics, Techniques, and Procedures (TTPs), and validate how Morphisec’s patented Anti-Ransomware solution powered by Automated Moving Target Defense (AMTD) can...
Read MoreEnsuring and maintaining a robust defense-in-depth strategy requires new technology investments, especially as many standard detection and response technologies can’t stop ransomware and the evasive and sophisticated techniques attackers are...
Read MoreIf you have anything to do with cyber security, you know it employs its own unique and ever-evolving language. Jargon and acronyms are the enemies of clear writing—and are beloved by cyber security experts. So Morphisec has created a comprehensive...
Read MoreGartner released two reports this month including Gartner® Emerging Tech: Security — AMTD Transforms Endpoint Protection1and Gartner Emerging Tech: AMTD Advances Proactive Cloud Defense 2 report, which each feature Morphisec as a sample vendor.
Read MoreIn ongoing efforts to monitor and analyze emerging cyber threats, Morphisec Threat Labs has recently turned its focus to Chae$ 4.1, an update to the Chaes malware Infostealer series. This version introduces key updates, including an improved Chronod...
Read MoreHeap buffer overflow in WebRTC in Google Chrome prior to 120.0.6099.129 allowed a remote attacker to potentially exploit heap corruption via a crafted HTML page.
Read MoreThe Cybersecurity and Infrastructure Security Agency (CISA) recently sounded the alarm on the widespread exploitation of the Citrix Bleed vulnerability. This critical security flaw has had a significant impact across various industries in the United...
Read MoreSecurity leaders are acutely aware of vulnerability risks. Organizations continue to allocate thousands of dollars to periodic vulnerability assessments, and thousands more to technology and resources for mitigation — yet vulnerability-based breach...
Read MoreFor the first time, Automated Moving Target Defense (AMTD) has been included in the 2023 Gartner Hype Cycle for Endpoint Security as a technology in the ‘on the rise’ category. Morphisec is named as a Sample Vendor in the AMTD category. “This Hype...
Read MoreApple Security Engineering and Architecture (SEAR) and the Citizen Lab opened a pair of critical vulnerabilities relating to the abuse of WebP images which could lead to exploitation of Google Chrome and Chromium-based browsers, as well as the...
Read MoreThe ransomware attack that hitMGM Resorts International on September 10thcaptured headlines due to the company’s name recognition, reputational and customer impact,andthe overall magnitude ofbusiness disruptionthe attack caused.
Read MoreSearch Our Site
Recent Posts
Posts by Tag
- Moving Target Defense (129)
- Cyber Security News (124)
- Morphisec Labs (113)
- Threat Research (64)
- Threat Post (61)
- Morphisec News (52)
- Automated Moving Target Defense (11)
- Defense-in-Depth (6)
- in-memory attacks (6)
- Gartner (5)
- Ransomware (4)
- runtime attacks (4)
- Legacy security (3)
- Linux cyber security (3)
- advanced threat defense (3)
- threat and vulnerability management (3)
- Adaptive Exposure Management (2)
- ChatGPT (2)
- Evasive loader (2)
- Fileless malware (2)
- Gartner endpoint protection (2)
- financial cybersecurity (2)
- patch management (2)
- Anti-tampering (1)
- Critical Threat Exposure Management (CTEM) (1)
- Gartner Emerging Tech (1)
- Healthcare cybersecurity (1)
- IoT security (1)
- Securing IoT devices (1)
- Server security (1)























.png?width=571&height=160&name=iso27001-(2).png)