Improving Threat Detection with Preemptive Security Solutions

The industry standard mix of cybersecurity technology and defensive measures most organizations use to form a break wall designed to detect inbound threats and neutralize them through early response. But for many companies, the break wall is failing— emerging and sophisticated attack techniques are effectively evading the defensive walls most companies rely on.
New risks promote new technology adoption
Like the threat landscape, cybersecurity is fluid and ever-changing. Over the years the industry has shifted from basic perimeter tools like firewalls and anti-virus systems to advanced detection and response and asset management across on-prem and cloud services and applications.
In most organizations, cybersecurity technology adoption is approached with caution and driven by a slow-moving process. Risk-averse organizations adopt emerging technology at a slower pace, or not at all, relying on “tried and tested” options. This approach ironically puts these organizations at a disadvantage, increasing their risk of breach. Attackers, always looking for the upper hand, continuously adapt threat techniques to dodge the industry-standard tools and techniques most organizations use.
Generative AI is accelerating overall risk — and the need for a new approach to cyber defense
The rapid advancement and adoption of generative AI tools is augmenting attack techniques and shifting the threat landscape at an obscene pace.
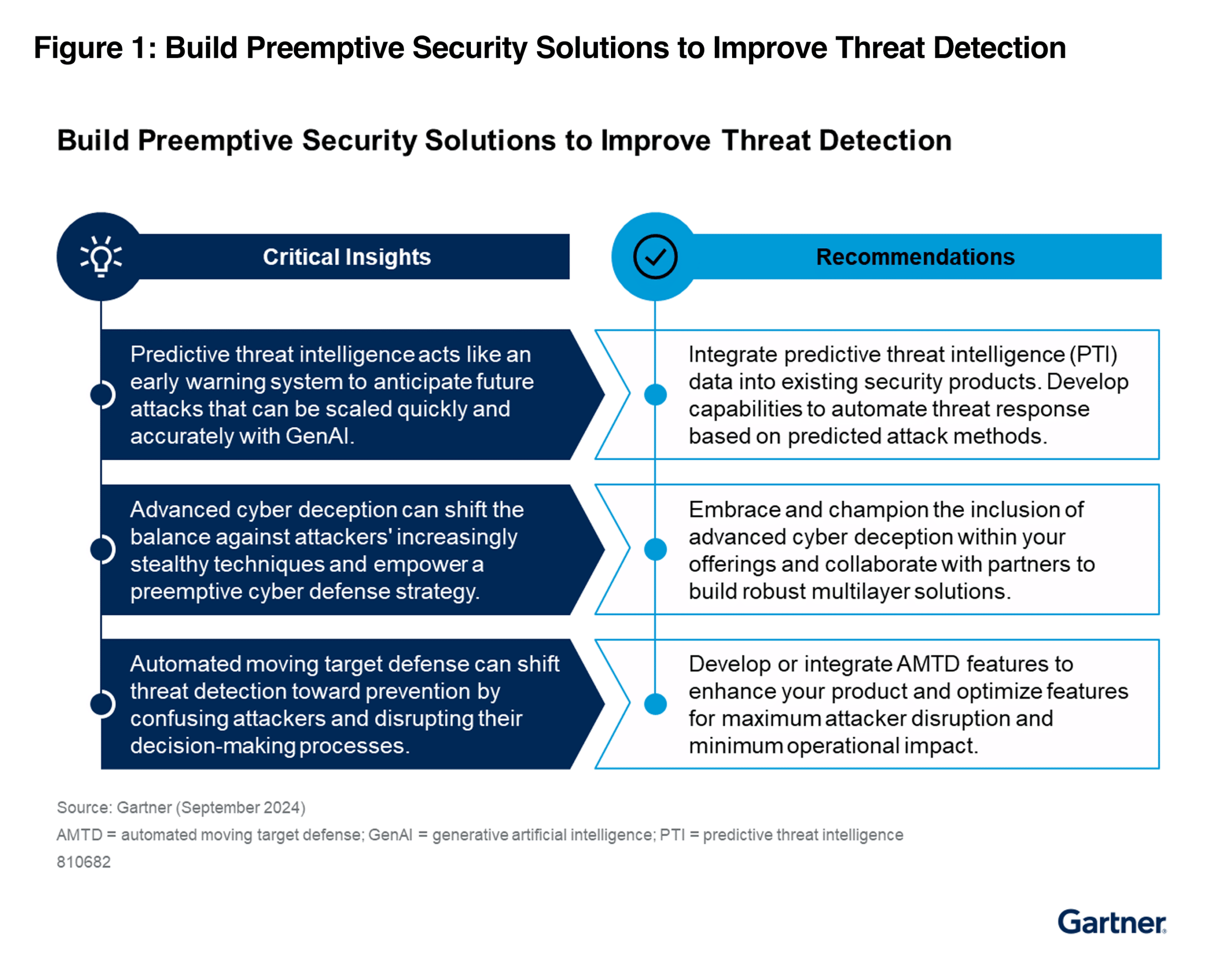
According to Gartner®: “Generative artificial intelligence (GenAI) can be exploited by malicious actors to personalize attacks at scale with frightening accuracy and speed, making it easier to deceive unsuspecting targets. Predictive threat intelligence (PTI) serves as an early warning system to anticipate future attacks and prioritize preemptive mitigation.”
Generative AI adds a new twist to old classics like social engineering and phishing attacks. With generative AI, attackers can personalize spoof emails like never before, mimicking language and tone with unnerving accuracy. AI-assisted coding is helping attackers architect and deploy increasingly sophisticated malware.
Generative AI is now used in many technologies and leveraged by both attackers and defenders, which both increases attack risk, and augments attack response.
Gartner® notes that: “The rise of generative AI is forcing a paradigm shift in cybersecurity. Traditional reactive “detect and respond” strategies are no longer adequate. Product leaders must start planning now to integrate new preemptive cyber defense technologies into their solutions to stay ahead.”
Detection and Response alone can’t stop sophisticated attacks
Already we’re seeing a shift in the managed detection and response (MDR) market. While traditionally reactive, managed detection and response is maturing into a comprehensive strategy that includes proactive measures to manage and mitigate cyber risks.
All detection-based approaches detect and alert on signature-based, known behavioral pattern attacks. Traditional malware typically relies on executable files, leaving traces on disk or within the operating system. These traces help train defense systems to recognize and isolate threats by detecting familiar deployment patterns.
However, modern attack chains have evolved. Instead of relying on disk-based artifacts, they hijack legitimate system processes and target device memory during runtime. This approach leaves no detectable signatures or breadcrumbs, making it much harder for conventional behavior-based detection tools (or a block-and-tackle style of MDR) to identify and respond to these threats.
According to Gartner®: “Adversaries are becoming more stealthy in their techniques to bypass traditional cyber defenses. Advanced cyber deception solutions can shift the balance against attackers, and empower a preemptive cyber defense strategy.”
What is preemptive cyber defense?
In theory, preemptive cyber defense is straightforward: it involves anticipating and acting against potential attacks before they occur. The objective is to stay ahead of threats by evading, outsmarting, or neutralizing them early, rather than waiting for the damage to unfold which can be the case with reactive defenses.
The advantages of this approach are equally clear: preventing cyberattacks before they can cause harm, rather than trying to mitigate the fallout after an attack has already occurred.
However, in practice, preemptive cyber defense has been hard to achieve — until now.
Gartner® notes that: “Preemptive cyber defense is an emerging category of cybersecurity technologies that are designed to prevent, stop or deter cyberattacks from achieving their objectives. Preemptive cyber defense technologies can be used either as stand-alone solutions or they can be integrated with existing security or technology products. Some use additional software-based agents, decoys, and other sensors to add their own unique detection capabilities to continuously monitor and analyze activity within an environment. This allows them to more rapidly identify any unusual, unexpected or potentially malicious activity. In these solutions, anomalies trigger automation that moves beyond basic blocking, asset isolation and process termination.”
A proactive and preemptive approach allows organizations to achieve a holistic and flexible security stance that can adapt and scale over time to meet and combat threats regardless of what techniques are dominant at any point in time.
According to Gartner®: “Preemptive cyber defense technologies help organizations improve their ability to defend against AI-enabled threat actors, advanced malware, zero-day vulnerabilities, ransomware, and a wide range of related threats. Those that typically cannot be stopped using a traditional “detect-and-respond” approach, alone.”
Achieving preemptive cyber defense with Automated Moving Target Defense
Attackers continuously adapt threat techniques to counter the predictability that detection and response solutions rely on. Conversely, organizations must embrace adaptability to ensure a robust cybersecurity posture.
Automated Moving Target Defense (AMTD) is an advanced cybersecurity strategy designed to enhance an organization’s defense by continuously and automatically changing the attack surface, making it much harder for adversaries to exploit vulnerabilities. Unlike traditional static defenses that maintain fixed system configurations and are predictable over time, AMTD introduces dynamic variability into the environment, such as shifting IP addresses, altering network paths, or frequently changing system configurations.
Description by Gartner®: “AMTD technologies orchestrate calculated change to “disrupt” attackers throughout the attack kill chain, which offers significant benefits that augment those gained with detection and response tools alone. By constantly changing or camouflaging the attack surface, defenders can confuse attackers and stop or delay their ability to establish a clear line of sight (LOS) to their target. Even if attackers get a foothold in the environment, AMTD can disrupt their ability to remain in systems for too long or move laterally. These capabilities can be highly effective in preventing cyberthreats from turning into successful cyber attacks.”
The core idea behind AMTD is to create uncertainty for attackers. By frequently altering key system attributes, it disrupts the reconnaissance and attack planning phases, making it difficult for adversaries to locate and exploit weaknesses.
This constant change forces attackers to spend more time and resources on identifying their targets, increasing the chances of detection or failure before they can launch a successful attack. AMTD is particularly useful in addressing sophisticated threats, such as in-memory attacks, zero-day attacks, and advanced persistent threats (APTs), that rely on deep system knowledge and predictable environments.
Augmenting detection and response capabilities with AMTD
By integrating AMTD into MDR services, organizations can not only meet modern security demands but also significantly strengthen their overall defense posture. Combining AMTD with Exposure Management in MDR delivers several critical advantages
- Proactive Threat Prevention: By identifying and addressing vulnerabilities before they are exploited, organizations can stop attacks before they begin.
- Minimized Attack Surface: Continuous monitoring and dynamic security control reduce potential attack vectors, limiting opportunities for threat actors.
- Increased Resilience: A protection-focused strategy ensures organizations can swiftly adapt to evolving threats, maintaining operational stability even against advanced cyberattacks.
- Operational Efficiency: Automated defenses and prioritized risk management streamline workflows, enabling security teams to focus on high-priority threats with greater effectiveness.
Additionally, Gartner® suggests that: “Integrating AMTD-enabled systems with threat detection and response operations can greatly elevate the effectiveness and scope of responses. When threats are detected and verified within an environment, AMTD-enabled systems can promptly initiate a response to counter the threat.”
Emerging threats fueled by generative AI will continue to re-shape the cybersecurity landscape. As it does, continually adapting your organization’s defense strategies and security tech stack is imperative to your organization’s ability to mitigate and manage risk.

Gartner®, Emerging Tech: Build Preemptive Security Solutions to Improve Threat Detection (Part 1), Luis Castillo, Carl Manion, 7 October 2024
GARTNER® is a registered trademark and service mark and Hype Cycle is a registered trademark of Gartner®, Inc. and/or its affiliates in the U.S. and internationally and is used herein with permission. All rights reserved.
Gartner® does not endorse any vendor, product or service depicted in its research publications, and does not advise technology users to select only those vendors with the highest ratings or other designation. Gartner® research publications consist of the opinions of Gartner®’s research organization and should not be construed as statements of fact. Gartner® disclaims all warranties, expressed or implied, with respect to this research, including any warranties of merchantability or fitness for a particular purpose.
Stay up-to-date
Get the latest resources, news, and threat research delivered to your inbox.