In the rapidly evolving landscape of cybersecurity, the Managed Detection and Response (MDR) market has undergone significant transformations. What began as a reactive approach focused on detecting and responding to threats has now matured into a more comprehensive strategy that includes proactive measures to manage and mitigate cyber risks.
At the forefront of this evolution is the integration of Exposure Management technologies, aligning with Gartner's Continuous Threat Exposure Management (CTEM) framework. This shift from a reactive to a prevention-first approach, embodied by innovations such as Adaptive Exposure Management and Automated Moving Target Defense (AMTD), is paving the way for a more resilient and adaptive cybersecurity posture.
The Traditional MDR Model: Strengths and Limitations
MDR services were initially designed to provide organizations with 24/7, human-led security operations that could quickly detect, investigate, and respond to threats. This model offered a turnkey solution that was particularly valuable for organizations lacking the internal resources to maintain a fully operational Security Operations Center (SOC).
In recent years, a vendor’s emphasis on threat response (the ‘R’ in MDR) became a key differentiator in distinguishing ‘true’ MDR providers from more immature or MSSP-centric vendors, and by extension a firm’s threat containment and remediation capabilities.
However, as cyber threats grew more sophisticated, it became clear that traditional MDR's reactive nature—focused primarily on detection and response—was not sufficient. According to Gartner: "Misnamed technology-first offerings that fail to deliver human-driven managed detection and response (MDR) services are confusing buyers looking to identify and select an outcome-driven provider."1
This highlighted the need for a more holistic approach that not only reacts to threats but also anticipates and mitigates them before they can cause harm. As the adage goes, an ounce of prevention is worth a pound of cure; in the realm of MDR true threat prevention remains a challenge. Yet the nature of increasingly complex cyber threats like fileless and in-memory attacks means that even the most sophisticated MDR provider may not be able to stop evasive attacks before they do significant damage.

The Integration of Exposure Management
The next logical step in the evolution of MDR is the integration of Exposure Management. This proactive approach focuses on identifying and mitigating vulnerabilities and other security gaps before they can be exploited by attackers. Gartner's CTEM framework emphasizes the importance of continuous monitoring and adaptation to new threats, which aligns perfectly with the goals of Exposure Management.

What is Exposure Management?
Exposure Management involves a series of proactive measures designed to reduce the attack surface and manage security risks more effectively.
Key components include:
- Continuous Monitoring: Regularly scanning for vulnerabilities and misconfigurations in the IT environment.
- Risk Prioritization: Identifying and prioritizing risks based on their potential impact.
- Remediation Guidance: Providing actionable insights and recommendations to address identified vulnerabilities.
- Validation and Testing: Using techniques such as breach and attack simulations (BAS) to validate the effectiveness of security controls.
By incorporating these elements into MDR services, organizations can shift from a purely reactive stance to one that is both proactive and preventive.
Adding to Gartner's CTEM Framework
Gartner's Continuous Threat Exposure Management (CTEM) framework outlines a structured approach to managing and mitigating threats continuously. According to Gartner: "By 2026, Organizations prioritizing their security investments based on a continuous exposure management program will be three times less likely to suffer from a breach."2
This prediction underscores the growing importance of exposure management in the cybersecurity landscape. Key Components of CTEM include:- Visibility: Ensuring comprehensive visibility into all assets and their associated vulnerabilities.
- Prioritization: Using advanced analytics to prioritize risks based on their potential impact.
- Remediation: Implementing effective remediation strategies to address identified risks.
- Validation: Continuously validating the effectiveness of security controls through testing and simulations.
Adhering to Gartner’s CTEM Framework
Integrating these components into MDR services ensures a more robust and adaptive cybersecurity posture that:
Supports Transitioning to a Protection-First Approach — The traditional MDR model's reactive nature has its limitations. To achieve a truly resilient cybersecurity posture, organizations must adopt a protection-first approach. This involves not just detecting and responding to threats but actively preventing them through continuous risk management and adaptive security measures.
Provides Adaptive Exposure Management — Adaptive Exposure Management is a key component of this protection-first strategy. It involves dynamically adjusting security controls based on real-time threat intelligence and risk assessments. This approach ensures that security measures are always aligned with the current threat landscape.
Reduces the Attack Surface with CTEM — CTEM is a systematic approach and program used to identify, assess, and mitigate attack vectors and security risks linked to digital assets. However, pinpointing and prioritizing vulnerable digital assets with accuracy poses a challenge for IT and security teams juggling resource limitations, process inefficiencies, and an overwhelming influx of telemetry data. Recognizing this, organizations are turning their attention to Continuous Threat Exposure Management (CTEM) to contain the attack surface.
In recent years, enterprise teams have focused on implementing CTEM by enhancing vulnerability management, particularly by increasing the speed and quantity of patching, and improving the efficiency of breach detection and response. But despite these efforts, cyber risk and cyber-attacks continue to climb.
According to Gartner: “Enterprises fail to reduce their patchable and unpatchable exposures to threats, yet keep implementing siloed and narrow remediation processes. IT leaders must implement continuous and repeatable exposure management processes, optimizing short-term response and longer-term security posture.” 2
This has created a juncture point that has most cybersecurity practitioners asking three critical questions:
- Are my systems vulnerable?
- Are my security controls working properly?
- What actions should I prioritize first?
Gartner recommends that: “Security and risk management teams progressively add notions of the CTEM framework to their existing practices.” 2
Applying CTEM can be achieved considering that a full CTEM cycle defines five key stages:

- Scoping: Aligning assessments to key business priorities and risk.
- Discovery: Identifying various elements within and beyond the business infrastructure that could pose risks in a comprehensive way.
- Prioritization: Identifying threats with the highest likelihood of exploitation and flagging which could have the most significant impact on the organization.
- Validation: Validating how potential attackers could exploit identified vulnerabilities or exposures.
- Mobilization: Ensuring all stakeholders are informed and aligned toward risk remediation and measurement goals.
Gartner states: “Continuous threat exposure management (CTEM) is an umbrella program for forward-looking and sustainable approaches to exposure reduction. Implementing CTEM enables closer alignment to business needs and risk impact. CTEM involves business leadership in identifying key assets and processes to defend against cyberattacks/business disruption.” 2
Supporting Exposure Management with Automated Moving Target Defense (AMTD)
Automated Moving Target Defense (AMTD) is another critical innovation that supports a protection-first approach. AMTD leverages polymorphism in memory to lead attackers astray, making it significantly harder for them to exploit vulnerabilities. This dynamic alteration of the attack surface creates a constantly shifting target, disrupting the attacker's kill chain and enhancing overall security.
According to Gartner, "Turnkey threat detection, investigation and response (TDIR) capabilities are a core requirement for buyers of MDR services, who demand remotely delivered services deployed quickly and predictably."1

By integrating AMTD into MDR services, organizations can meet these demands while significantly enhancing their defensive capabilities. The integration of Exposure Management and AMTD into MDR services offers several key benefits including:
- Proactive Threat Mitigation: By identifying and addressing vulnerabilities before they can be exploited, organizations can prevent many attacks from occurring in the first place.
- Reduced Attack Surface: Continuous monitoring and adaptive security controls help minimize the attack surface, reducing the number of potential entry points for attackers.
- Enhanced Resilience: A protection-first approach ensures that organizations can quickly adapt to new threats, maintaining operational continuity even in the face of sophisticated attacks.
- Improved Efficiency: Automated defenses and prioritized risk management streamline security operations, allowing security teams to focus on the most critical issues.
Anti-Ransomware Assurance Suite Powered by AMTD
Morphisec is leading the charge in ransomware defense as the industry’s first provider to seamlessly integrate crucial elements — ransomware protection, AMTD, and CTEM —into a single, powerful solution.
Built on Morphisec’s pioneering AMTD technology, the Anti-Ransomware Assurance Suite provides multiple distinct layers of anti-ransomware protection, pre-emptively reducing an organization’s exposure, and proactively preventing attacks at multiple phases. Additionally, it protects critical system resources and data when ransomware attempts to execute, reducing mean time to recovery.
Its three distinct modules include:
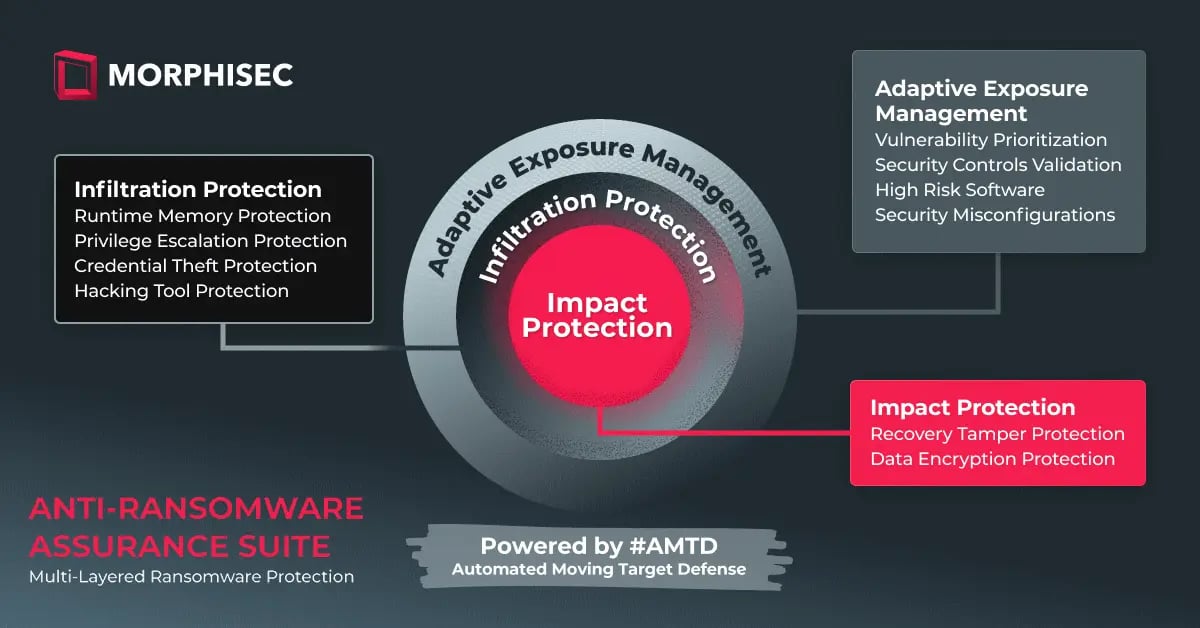
- Adaptive Exposure Management — Helping organizations adapt by elevating the overall security posture and pre-emptively defending against attacks. Adaptive Exposure Management prioritizes vulnerabilities, automates the assessment and validation of an organization’s security controls, identifies high-risk software, and addresses security misconfigurations.
- Ransomware Infiltration Protection — Preventing the execution of ransomware attacks at early infiltration stages with Morphisec's prevention-first AMTD technology that constantly changes a system's configuration or environment. This makes it harder for attackers to exploit vulnerabilities as the attack surface is always shifting.
- Ransomware Impact Protection — Defending systems against the ransomware impact phase with dedicated anti-ransomware protection that proactively defends critical assets and files with a prevention-first strategy. This minimizes recovery times and strengthens an organization’s anti-ransomware stance.
The Anti-Ransomware Assurance Suite is designed to help organizations enhance their overall security posture. It provides improved visibility into threat exposure, enabling better preparation for rapid response and recovery, ultimately ensuring operational readiness.

Case Study: Implementing the Evolved MDR Model at Omega Systems
Consider the example of Omega Systems, an award-winning MSP and MSSP that recently enhanced its endpoint detection and response (EDR) solution with Automated Moving Target Defense (AMTD). Prior to this enhancement, Omega Systems relied on traditional EDR technology, which, according to market research, fails to detect or prevent as much as one-third of all endpoint security threats.
The Transition Process
- Assessment: Omega Systems conducted a thorough assessment of its existing security posture, identifying key vulnerabilities and areas for improvement.
- Integration: The organization integrated Exposure Management technologies into its EDR service, enabling continuous monitoring and risk prioritization.
- Implementation: Omega Systems deployed AMTD solutions to dynamically alter the attack surface and disrupt potential attacks.
- Validation: The effectiveness of the new security measures was validated through various security assessments and attack simulations.
Within six months of implementing AMTD, Omega Systems noticed a significant reduction in security incidents. The continuous monitoring and proactive risk management measures identified and mitigated several critical vulnerabilities, preventing potential breaches. Additionally, the implementation of AMTD created a more challenging environment for attackers, further enhancing the organization's security posture.
According to Omega Systems COO Ben Tercha, "Over time, our Security Operations team has noticed a shift in power between sophisticated threat actors and standard EDR defense capabilities – and the balance continues to tip in the wrong direction. By embedding AMTD into our existing endpoint security solution, we can deliver a fully optimized endpoint security solution and better protect our customers against these sophisticated threats."
Embrace the Future of Cybersecurity
The evolution of the MDR market to include Exposure Management and align with Gartner's CTEM framework represents a significant advancement in cybersecurity. By shifting from a reactive detection and response approach to a prevention-first strategy, organizations can achieve a more resilient and adaptive cybersecurity posture.
Morphisec is at the forefront of this evolution, offering innovative solutions such as Adaptive Exposure Management and AMTD. These technologies provide the proactive and dynamic security measures necessary to stay ahead of sophisticated cyber threats.
As the cybersecurity landscape continues to evolve, it is imperative for organizations to adopt a comprehensive approach that integrates both reactive and proactive measures. By embracing the evolved MDR model, organizations and their managed service providers can not only protect against current threats but also anticipate and mitigate future risks, ensuring continuous operational continuity and safeguarding critical assets.
MSP and MSSP product and service managers can learn more about evolving MDR with Continuous Threat Exposure Management (CTEM) and Adaptive Exposure Management in the 
References:
1Gartner, Market Guide for Managed Detection and Response, June 24, 2024
2Gartner, Implement a Continuous Threat Exposure Management (CTEM) Program, 11 October, 2023





.png?width=571&height=160&name=iso27001-(2).png)