
July has been a busy month for the distributors of GandCrab ransomware. After about two months with no major update, the cybercrime gang behind GandCrab released version 4, and a few days later, version 4.1. The primary delivery method is via compromised WordPress websites, which have been hijacked to include fake crack application pages, which in turn redirect to the GandCrab executable. Other distribution methods are Exploit Kits (EK) and malicious email campaigns.
One of the most popular tricks of attackers is to employ packer-based malware, which is modified in the runtime memory using various sophisticated compression techniques. As with previous versions of GandCrab ransomware, this version is packed by a custom packer and uses multiple additional techniques to make it more difficult to detect the malicious code and harder to analyze by security researchers.
How Does GandCrab ransomware it Work?
Fake crack sites leading to GandCrab ransomware:
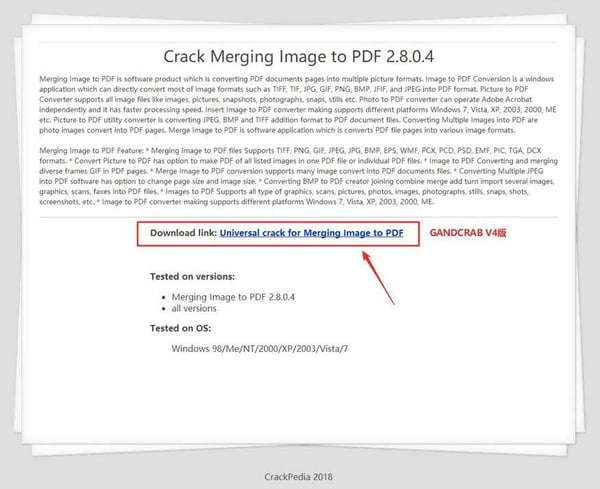
Image credit: Bleeping Computer
Highlights and Changes in Version 4.0/4.1:
GandCrab Ransomware includes various sophisticated in-memory evasive techniques
It iterates over the PEB to find useful functions (locate GetProcAddress and LoadLibrary), build the IAT (Import Address Table) and finally jump to the unpacked sample (read more).
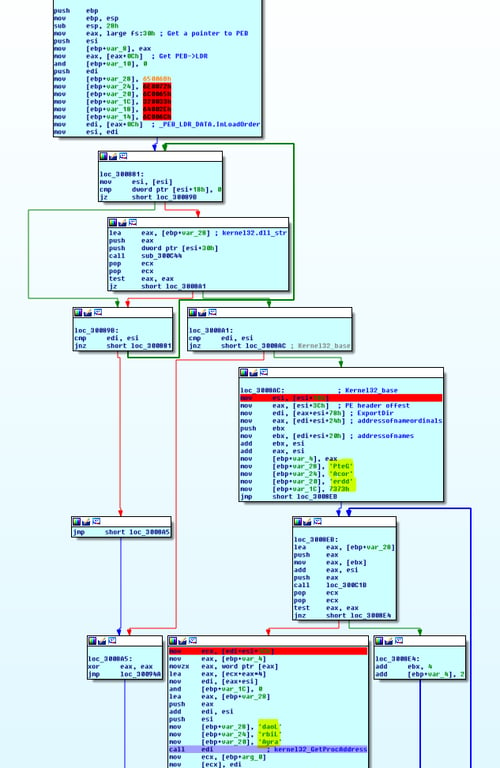
The unpacked GandCrab uses several techniques to avoid detection:
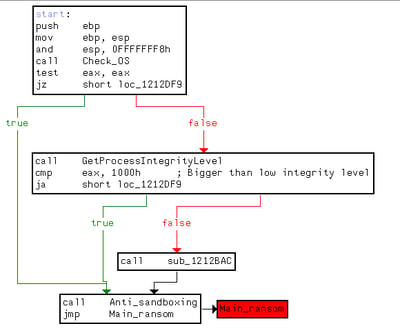
Encryption procedure:
This version of GandCrab ransomware uses the Salsa20 stream cipher to encrypt files instead of RSA-2048 encryption (RSA-2048 encryption is still used, but for a different function).
If the file <8-hex-chars>.lock exists in the AppData directory, GandCrab terminates the process without infecting the system.
Encrypted file extension:
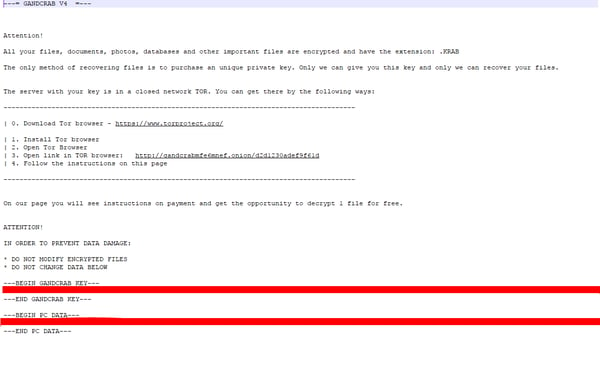
The encrypted files use .KRAB as the new file extension.
Additionally, victims receive a KRAB-DECRYPT.txt file which serves as the ransom note.
- Encrypts files procedure executes even if the device is not connected to the Internet
- Encrypts network shares and not just mapped drives
GandCrab payment page:

Image credit Fortinet
- The developers are asking for DASH or Bitcoin cryptocurrency.
- It offers 24/7 support chat service, similar to previous versions.
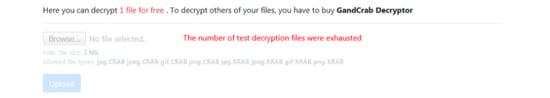
- Although the payment page says you can test decrypt one file for free, the ability to upload an encrypted file through the "Test decrypt" tab was inactive:
Additional Features in GandCrab ransomware 4.0/4.1
- Performs a user interface language check against some Russian-speaking countries. If present, does not proceed with the infection. This is in addition to the Russian keyboard layout check in previous versions.
How to Protect Yourself from GrandCrabVersion 4.1
Morphisec’s Moving Target Defense based technology prevents the attack before it can perform any type of malicious activity. Morphisec customers are and have always been protected from the attack out of the box, no updates needed.
If you don’t have Morphisec installed, you can create an <-8hex-char>.lock file in the SYSTEM APPDATA folder(e.g C:\ProgramData), which causes the malware to terminate without infecting the system. However, this is not a permanent solution as this can easily be disabled in future versions.
Resources:
- https://www.fortinet.com/blog/threat-research/gandcrab-v4-0-analysis--new-shell--same-old-menace.html
- https://www.bleepingcomputer.com/news/security/gandcrab-v4-released-with-the-new-krab-extension-for-encrypted-files/
Hashes:
- 6c1ed5eb1267d95d8a0dc8e1975923ebefd809c2027427b4ead867fb72703f82





.png?width=571&height=160&name=iso27001-(2).png)