Ransomware has become one of the most prevalent and damaging forms of cybercrime in recent years, affecting businesses, governments and individuals worldwide. The 2024 Verizon Data Breach Investigations Report highlights ransomware as one of the...
Read MoreIn the rapidly evolving landscape of cybersecurity threats, a new adversary has emerged, drawing inspiration from one of the internet’s most enigmatic puzzles—Cicada3301. This new threat, dubbed Cicada3301 ransomware, was identified in a Morphisec...
Read MoreThe evolution of cybersecurity has been a journey of increasingly sophisticated defense innovations. It began with basic anti-virus (AV) software, which relied on static analysis to identify known threats by scanning binaries and files.
Read MoreCyber-attacks targeting healthcare facilities ruthlessly exploit personal, vulnerable and highly sensitive information. It’s one of the few industries where attacks can lead to life and death scenarios.
Read MoreMorphisec announced the launch of the Anti-Ransomware Assurance Suite to help organizations pre-emptively reduce exposure to cyber risk, proactively prevent advance threats and ensure optimal anti-ransomware defense. Powered by Automated Moving...
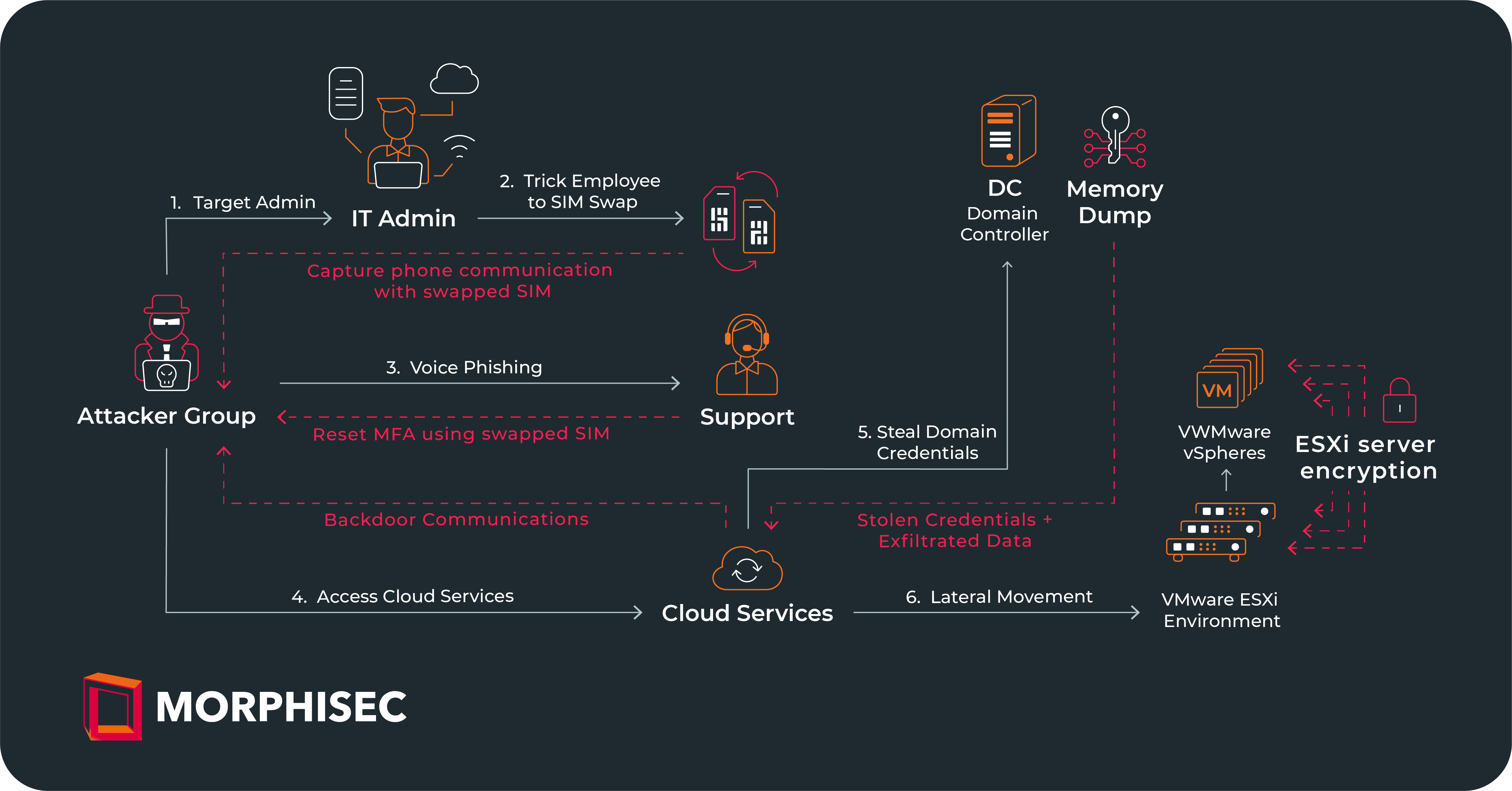
Read MoreGlobally, ransomware is big business, with millions of attacks targeting organizations every day. Not every attack is financially successful, but with keen attention to detail, attackers have (and continue to) tune tactics, making ransomware a...
Read MorePreventing Ransomware and Advanced Endpoint Threats with Morphisec + Microsoft Defender for Endpoint
When it comes to endpoint security, Microsoft Defender for Endpoint is a popular choice, and is the fastest growing endpoint protection platform, boasting over 19% market share. Additionally, the solution is consistently named a “leader” in the...
Read MoreThe ransomware attack that hitMGM Resorts International on September 10thcaptured headlines due to the company’s name recognition, reputational and customer impact,andthe overall magnitude ofbusiness disruptionthe attack caused.
Read MoreDuring November, Morphisec identified a brand-new variant of Babuk ransomware while investigating a customer's prevention event. Babuk was first discovered at the beginning of 2021, when it began targeting businesses to steal and encrypt data in...
Read MoreNow more than ever, supply chains are attracting threat actor attention. As evidenced by attacks like the one which recently targeted the IT services provider Kaseya and over 1,500 of their clients, trusted relationships between service providers...
Read MoreRansomware developers have powerful financial incentives to continue adding new features to their code. From developers to affiliates, these malicious pieces of software enrich countless cyber criminals at great expense to victims, and will likely...
Read MoreSearch Our Site
Recent Posts
Posts by Tag
- Automated Moving Target Defense (157)
- Threat Research (135)
- Cyber Security News (132)
- Morphisec Labs (124)
- Morphisec News (54)
- Adaptive Exposure Management (14)
- Defense-in-Depth (13)
- Ransomware (12)
- Preemptive Security (11)
- Gartner (10)
- Continuous Threat Exposure Management (CTEM) (9)
- Microsoft (8)
- In-Memory Attacks (7)
- Healthcare Cybersecurity (6)
- Advanced Threat Defense (5)
- Legacy Security (5)
- Artificial Intelligence (4)
- Financial Cybersecurity (4)
- Linux Cybersecurity (4)
- Fileless Malware (3)
- Threat and Vulnerability Management (2)
- Managed Service Providers (1)















.png?width=571&height=160&name=iso27001-(2).png)