The evolution of fake update campaigns has advanced significantly with the emergence of CoinLurker, a sophisticated stealer designed to exfiltrate data while evading detection. Written in Go, CoinLurker employs cutting-edge obfuscation and...
Read MoreNTLM is like that stubborn relic of the past that just won’t go away – a decades-old authentication protocol, seemingly deprecated but still lurking in the shadows of every Windows environment.
Read MoreRecently, Morphisec Threat Labs identified and prevented multiple sophisticated Lua malware variants targeting the educational sector. These attacks capitalize on the popularity of Lua gaming engine supplements within the student gamer community.
Read MoreMandiant cybersecurity researchers recently released a blog on a memory-only dropper which uses a complex multi-stage infection process. This PowerShell-based downloader is being tracked as PEAKLIGHT. Mandiant researcher findings note that this...
Read MoreIn the rapidly evolving landscape of cybersecurity threats, a new adversary has emerged, drawing inspiration from one of the internet’s most enigmatic puzzles—Cicada3301. This new threat, dubbed Cicada3301 ransomware, was identified in a Morphisec...
Read MoreRecently, Morphisec researchers discovered a vulnerability in Microsoft Outlook that can lead to remote code execution (RCE). This vulnerability, identified as CVE-2024-38021, highlights a significant security flaw within the Microsoft Outlook...
Read MoreAs part of our ongoing efforts to identify newer vulnerabilities in Microsoft Office applications, Morphisec researchers have discovered two additional critical vulnerabilities in the Microsoft Outlook application which were reported to Microsoft...
Read MoreRecently, Morphisec researchers discovered a vulnerability in Microsoft Outlook, which highlights the potential for remote code execution within the context of the Outlook application. This newly identified vulnerability, CVE-2024-30103, allows...
Read MoreYou’ve Got Mail: Critical Microsoft Outlook Vulnerability CVE-2024-30103 Executes as Email is Opened
In the ever-evolving landscape of cybersecurity, staying ahead of threats is paramount. At Morphisec, our team of dedicated researchers continuously strives to identify and mitigate emerging vulnerabilities to protect organizations worldwide.
...
Read MoreMorphisec Labs has been monitoring increased activity associated with Sticky Werewolf, a group suspected to have geopolitical and/or hacktivist ties. While the group’s geographical origin and home base remain unclear, recent attack techniques...
Read MoreMorphisec Threat Labs recently discovered multiple indicators of attacks leading to threat actor, UAC-0184. This discovery sheds light on the notorious IDAT loader delivering the Remcos Remote Access Trojan (RAT) to a Ukrainian entity based in...
Read MoreThis blog examines the Akira Ransomware as a Service (RaaS) group, to understand their Tactics, Techniques, and Procedures (TTPs), and validate how Morphisec’s patented Anti-Ransomware solution powered by Automated Moving Target Defense (AMTD) can...
Read MoreIn ongoing efforts to monitor and analyze emerging cyber threats, Morphisec Threat Labs has recently turned its focus to Chae$ 4.1, an update to the Chaes malware Infostealer series. This version introduces key updates, including an improved Chronod...
Read MoreThe Cybersecurity and Infrastructure Security Agency (CISA) recently sounded the alarm on the widespread exploitation of the Citrix Bleed vulnerability. This critical security flaw has had a significant impact across various industries in the United...
Read MoreExclusive: Morphisec Threat Labs identified Chae$ 4, an advanced and previously unknown variant of the Chaes malware. Read this post for an abstract of the findings.
Download the full Chae$ 4 technical analysis containing exclusive details of the...
Read MoreThe Aurora stealer is a notorious Golang-based information stealer that's been gaining popularity from the end of 2022 through the first quarter of 2023. The Morphisec Threat Labs team has been tracing its activities using our prevention telemetry...
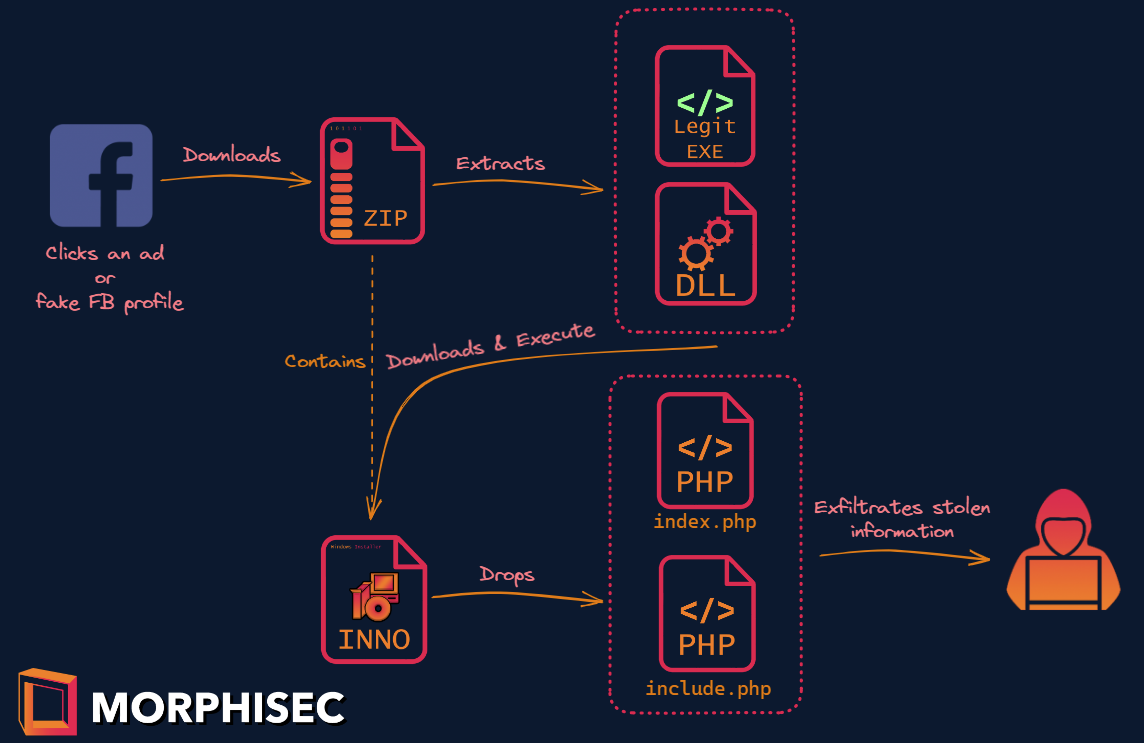
Read MoreStarting in November 2022, Morphisec has been tracking an advanced info stealer we have named “SYS01 stealer.” SYS01 stealer uses similar lures and loading techniques to another information stealer recently dubbed S1deload by the Bitdefender group,...
Read MoreMorphisec has recently identified a highly evasive malware campaign delivering ProxyShellMiner to Windows endpoints.
Read MoreDuring November, Morphisec identified a brand-new variant of Babuk ransomware while investigating a customer's prevention event. Babuk was first discovered at the beginning of 2021, when it began targeting businesses to steal and encrypt data in...
Read MoreSearch Our Site
Recent Posts
Posts by Tag
- Automated Moving Target Defense (157)
- Threat Research (135)
- Cyber Security News (132)
- Morphisec Labs (126)
- Morphisec News (54)
- Adaptive Exposure Management (14)
- Defense-in-Depth (13)
- Ransomware (12)
- Preemptive Security (11)
- Gartner (10)
- Continuous Threat Exposure Management (CTEM) (9)
- Microsoft (8)
- In-Memory Attacks (7)
- Healthcare Cybersecurity (6)
- Advanced Threat Defense (5)
- Financial Cybersecurity (5)
- Legacy Security (5)
- Artificial Intelligence (4)
- Linux Cybersecurity (4)
- Fileless Malware (3)
- Threat and Vulnerability Management (2)
- Managed Service Providers (1)























.png?width=571&height=160&name=iso27001-(2).png)