Globally, ransomware is big business, with millions of attacks targeting organizations every day. Not every attack is financially successful, but with keen attention to detail, attackers have (and continue to) tune tactics, making ransomware a leading and highly profitable global economy. Recent findings pegged ransomware payments at $1 billion USD in 2023. Alarmingly, the global economic impact of ransomware far exceeds ransom payments, which is estimated at $30 billion USD — this figure encompasses direct losses due to operational disruptions, expenses, indirect costs such reputation losses, and impact to company valuations.
 Regardless of size or industry, all businesses are at risk of attack. The 2023 Verizon Data Breach Investigation Report ranks ransomware as one of the top action types present in breaches. And it’s no surprise. Ransomware attacks increasingly use evasive techniques that easily bypass traditional defense solutions.
Regardless of size or industry, all businesses are at risk of attack. The 2023 Verizon Data Breach Investigation Report ranks ransomware as one of the top action types present in breaches. And it’s no surprise. Ransomware attacks increasingly use evasive techniques that easily bypass traditional defense solutions.
While ransomware attacks are prolific today, they’ve been a persistent threat over several decades, morphing as attackers refine their methods. Defense tactics and technologies have changed, too. While no silver bullet currently exists, new technologies can stop attacks before infection can initiate.
This post kicks off a series of blogs examining the history of ransomware — and its future. By understanding the evolution of ransomware, defenders can gain an upper hand, and respond proactively from a position of strength, rather than reactively managing damage control.
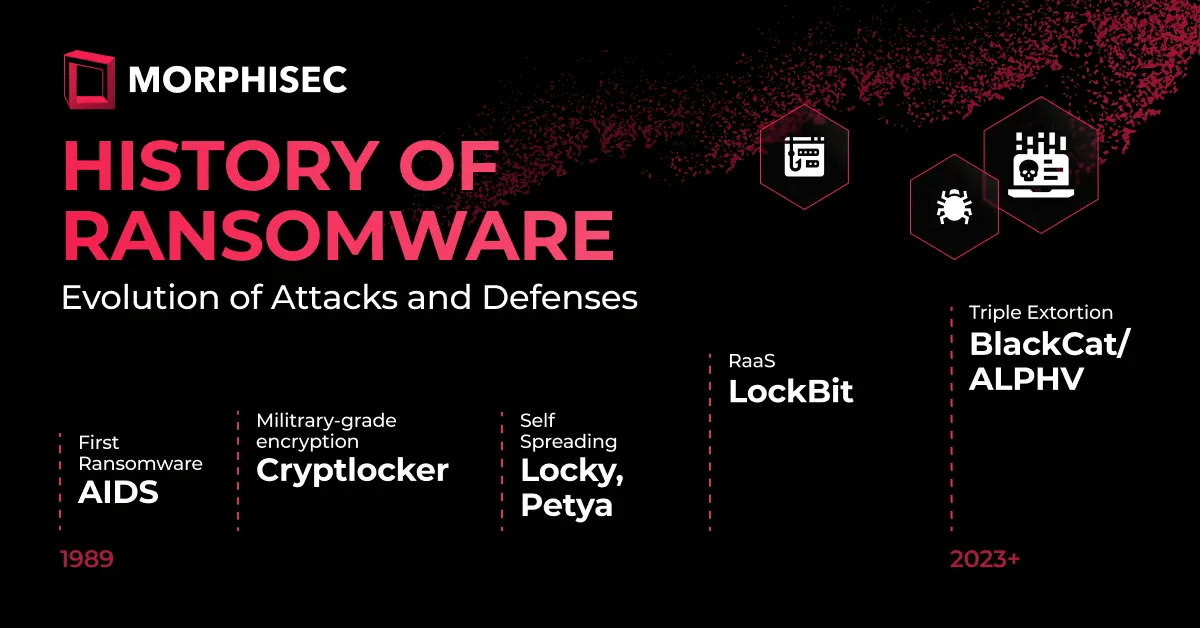
Let’s start by taking a closer look at the evolution of ransomware and notable attacks over the last few decades:
.png?width=790&height=383&name=Timeline%20of%20Ransomware(1).png)
1989 - The AIDS Trojan (also known as PC Cyborg)
Generally considered the first instance of ransomware, it was distributed via floppy disks and encrypted file names on the infected system, demanding payment for decryption.
2004-2006 - Gpcode, TROJ.RANSOM.A, Archiveus
This period saw the emergence of more sophisticated ransomware using stronger encryption methods, making it harder to recover files without paying the ransom.
2013 - CryptoLocker
A significant leap in ransomware sophistication, CryptoLocker used military-grade encryption and was spread through email attachments and existing botnets. Its success spawned many variants and inspired a new wave of ransomware development.
2016 - Locky, Petya
These ransomware variants spread through phishing emails and exploited network vulnerabilities. Petya was one of the first widely recognized ransomware strains to deviate from the then-standard practice of encrypting individual files. Instead, it targeted the entire disk volume by overwriting the Master Boot Record (MBR) to prevent the operating system from booting until a ransom was paid, effectively holding the entire system hostage.
2017 - NotPetya (Ukraine and Wiper Malware) & WannaCry
NotPetya initially masqueraded as a ransomware attack but was later identified more as a wiper with the intent to cause disruption. Although it demanded a ransom, the payload was primarily designed to irrecoverably damage data. NotPetya initially targeted Ukraine, affecting its government, financial, and energy institutions before spreading globally. The use of wiper malware in this geopolitical context marked a significant evolution in how cyber tools were used in state-sponsored activities and cyber warfare.
NotPetya and WannaCry both used the EternalBlue exploit, developed by the United States National Security Agency (NSA). WannaCry affected more than 300,000 computers across 150 countries before being disabled using a kill switch.
2019 - Maze Ransomware
This attack introduced the concept of "double extortion," where attackers not only encrypted files but also threatened to publish stolen data unless an additional ransom was paid.
2020 - EKANS (Snake) Ransomware
The first ransomware dedicated primarily for targeting of OT (operational technology) and ICS (Industrial Control System) infrastructures.
2020-2021 - LockBit - Emergence of Ransomware-as-a-Service (RaaS)
RaaS platforms allowed cybercriminals to rent ransomware infrastructure and tools, lowering the entry barrier for conducting ransomware attacks and leading to a proliferation of attacks. RaaS boosts the resilience of ransomware operators, as observed with limited success of law enforcement agents to takedown their infrastructures, only to see them emerge with newer generations and evolutions.

In February 2023, the LockBit management portal was temporarily taken down by law enforcement agencies. With its vast RaaS infrastructure and affiliates, reports of new LockBit victims returned within days (Source: UK National Crime Agency)
2020-2021 - Conti Ransomware Group Adopts Exfiltration-First Tactics
The Conti ransomware group, known for its aggressive extortion tactics and rapid operational tempo, began to increasingly focus on data exfiltration as a primary method of extortion. In some instances, they would infiltrate networks, exfiltrate a significant amount of sensitive data, and then demand a ransom not for decrypting data (as the data might not even have been encrypted) but for not releasing the stolen data.
2023 - BlackCat/ALPHV, AvosLocker -Triple Extortion Ransomware-as-a-Service
This evolution of RaaS involved not just encrypting data and threatening its release but also incorporating additional extortion methods like DDoS attacks as part of a comprehensive service offering or reporting to the SEC on a compromised victim. This approach has made ransomware attacks even more complex and harder to defend against, with attackers continuously innovating to find new ways to leverage their malicious software.
This timeline highlights the almost exponential increase in the sophistication and innovation of adversaries themselves. This innovation extends to the ransomware payment model, which is reducing transactions and rebranding sanctioned ransomware groups, and applying a support model that uses self-served help desks.
The Evolution of Ransomware Defense
Defensive strategies and technologies have evolved over time to keep pace with ransomware’s growing sophistication. From the early days of improved antivirus software with heuristics and behavioral detection, frequent data backups, application whitelisting and network segmentation, to more advanced solutions like next-generation antivirus, antimalware scan interface and endpoint and detection and response, tactics have changed.
Modern-day sophisticated evasion and double extortion-based attacks are best addressed through a combination of zero trust architecture and Automated Moving Target Defense (AMTD), a current methodology that dynamically changes the attack surface. It confuses and impedes attackers by constantly shifting the attack surfaces to make systems harder to attack.
Morphisec’s Anti-Ransomware in action, preventing a new LockBit variant:
Imminent and future AI-driven attack methods must rely on adaptive defense strategies that include AMTD as a core component of Adaptive Exposure Management solutions. This approach is aligned with Gartner's Continuous Threat Exposure Management (CTEM) framework, which advocates for an ongoing cycle of identifying, assessing, and prioritizing exposures to threats.
Morphisec and other security firms are working toward what is referred to as a "Self-Healing Endpoint". This concept involves the endpoint's ability to not only detect when it has been compromised but also to autonomously take steps to isolate the threat, eradicate it, and restore any affected systems to their pre-attack state. Self-healing is predicated on the endpoint's capacity to continually adapt its exposure—shifting and morphing through AMTD techniques—to minimize the attack surface and prevent exploitation.
Self-Healing Endpoint Explained
The self-healing process is a cycle that continuously improves a system's resilience to attacks. With AMTD integration, the system does not remain static. Instead, it frequently and unpredictably alters its own configuration and attack surface, making it a moving target that is much harder for attackers to hit. This proactive defense mechanism is designed to prevent attackers from finding a stable and predictable environment to exploit.
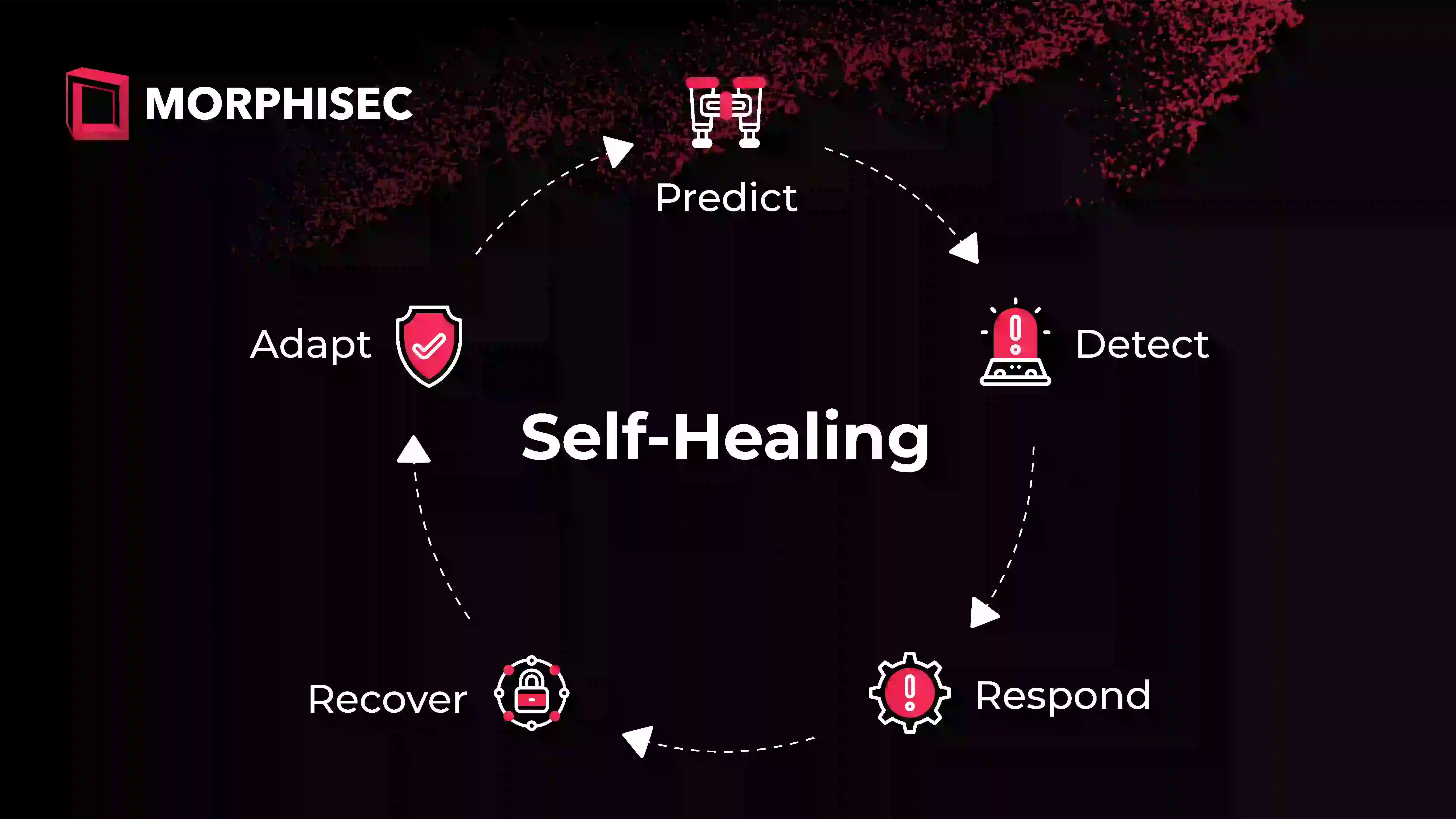
In the context of an Adaptive Exposure Management solution, self-healing refers to the system's capability to:
- Predict: Gaining analytics and insights to reduce the attack surface.
- Detect: Recognizing when a compromise has occurred or is in progress, often by using behavioral analysis and anomaly detection.
- Respond: Initiating immediate response actions to contain and neutralize the threat.
- Recover: Utilizing backups/system restore/recovery and pre-defined procedures to restore affected systems and data to their original state.
- Adapt: Modifying its defensive posture by changing the configurations or security policies to prevent the same or similar attacks from succeeding in the future.
Self-healing endpoint is a theoretical concept that’s actively in development; we’d welcome feedback from cybersecurity peers as iterations continue.
By 2030, such advanced defensive mechanisms are expected to become the standard for anti-ransomware strategies, significantly reducing the effectiveness of even the most sophisticated ransomware threats.
The emphasis will likely continue to shift toward predictive and preventive measures, leveraging AI and machine learning not just to respond to threats, but to anticipate and neutralize them before they can cause harm.
Strengthening Ransomware Defense
As ransomware attacks evolve, so will defensive measures. The key to effective ransomware mitigation lies in a multi-layered defense strategy that includes both technological solutions and human vigilance.
The introduction of AMTD represents a significant step forward in proactive defense, making systems more resilient against the adaptability of modern ransomware attacks. Future defense strategies will likely continue to evolve with an emphasis on automation, machine learning, and AI-driven security measures to anticipate and counteract emerging ransomware techniques.
Book a demo to see Morphisec AMTD and its ransomware prevention capabilities in action. Follow this series for part two, where we’ll examine the emerging landscape of AI-driven and adaptive ransomware threats, the evolution of self-healing defenses, innovative AI-based cybersecurity techniques, best practices and the crucial role of global cooperation and policy evolution in fortifying future cyber defenses.






.png?width=571&height=160&name=iso27001-(2).png)