
A new highly sophisticated botnet incorporating numerous malicious, evasive techniques is quickly spreading its tentacles. Dubbed MyloBot, the botnet uses an usually complex chain attack and combines multiple anti-analysis techniques to make it more difficult to detect the payload and harder to analyze by security researchers. Initial research published by Deep Instinct points out that everything on the victim’s end takes place in memory, while the main business logic of the botnet is executed in an external process using code injection. This makes it even harder to detect and trace.
One of the more interesting MyloBot techniques is the ability to kill other malware by deleting it from the Application Data folder and searching for folders of other botnets. Most likely in an effort to decrease the competition. It also disables Windows Defender and Windows Updates and blocks ports on the Firewall.
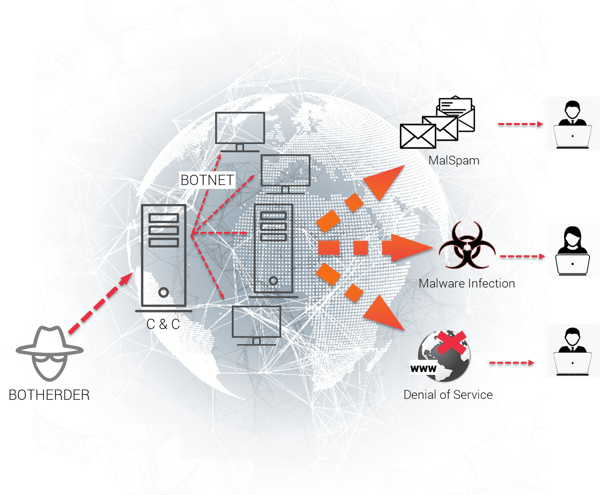
HOW DOES IT WORK?
MyloBot botnet attack vector uses a number of methods to evade detection and ultimately could download any payload the attacker wants.
Core capabilities:
Anti-Analysis Techniques
MyloBot uses various Anti VM, Anti Sandbox and and Anti Debugging systems, including identifying tools used by analysts or sandbox environments (boxmouse.sys). It detects "Sandboxie" and " Threatexpert " by checking for the existence of module "sbiedll.dll" and "dbghelp.dll". Additionally, the botnet attempts to detect "wine" by calling GetProcAddress() on "wine_get_unix_file_name".
SetUnhandledExceptionFilter -A divide-by-zero exception is triggered:

Blocks/Disables Crucial System Services
Blocks/disables Windows Defender, Windows Updates and Firewall ports:
- sc stop wuauserv
- sc config wuauserv start= disabled
- Reg add "HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows Defender" /v DisableAntiSpyware /t REG_DWORD /d 1 /f
- netsh advfirewall firewall add rule name="blockport [2900,1100,2200,3300,4400,5500….]" Dir=out action=block protocol=TCP remoteport=[2900,1100,2200,3300,4400,5500….]
Finds Useful Functions
As part of the evasive techniques, MyloBot iterates over the Process Environment Block to find useful functions.
Delaying Mechanism
It delays 14 days before accessing its command and control servers.
Establishes Persistence
Using run keys to establish persistence – "HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run"
Extracts the encrypted resource file to use in other internal parts:
Process Hollowing
Uses the technique of process hollowing to thwart the mitigation capabilities of security products ( as described in this blog), MyloBot creates process and uses a known procedure of CreateProcess in suspend state, unmapping the executable memory and replacing it with the malicious code.
Code Injection and Reflective EXE
Malicious code is written directly into memory rather than to a file on a hard drive. This kind of reflection is not very common.
Potential Impact
Once it has infected an endpoint, this botnet can execute any payload - data theft, activity monitoring, displaying advertisements, downloading and executing a file, deleting or modifying files, removing files or running background processes.
How Does Morphisec Protect You from MyloBot?
Morphisec’s Moving Target Defense stops the attack across its attack chain, at both the MyloBot and the payload malware itself. Morphisec doesn’t rely on signature or behavioral patterns. It uses patented moving target defense technology to prevent the attack at the earliest stages, before it can perform any type of malicious activity.
Resources
Hashes:
f4ba5e8f98fe70d764df71b7c390237b90ed0fc3408579a15a06ee56008a3531




.png?width=571&height=160&name=iso27001-(2).png)