
Ransomware remained a major cybersecurity threat in 2017, leaving a trail of victims across all industries, company sizes and geographical borders. Phishing emails are the top ransomware delivery mechanism and they grow in number and sophistication daily. According to IBM, the number of ransomware-infected emails increased 6,000% this year. And the days of easily spotted spelling mistakes and obvious scams are long gone. Today’s phishing attacks are clever and subtle enough to trick even security veterans.
Early October 2017, a new ransomware strain dubbed Sigma entered the scene, delivered via a phishing email pretending to come from Mastercard. The email contains an alarming message stating that the victim’s MasterCard account is at risk. Recipients are told to open the email attachment to prevent an unauthorized charge from going through.
How did Cybersecurity Solutions Cope with Sigma?
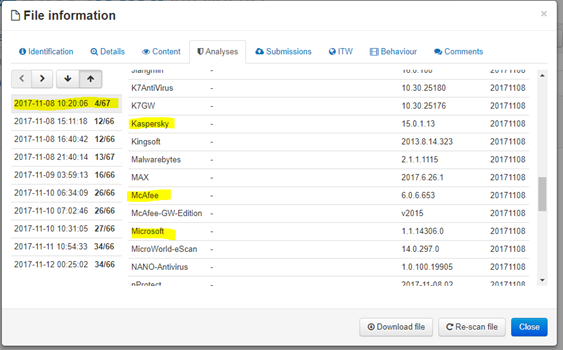
Signature-based and behavioral security solutions exposed, as expected, their weakness in stopping this new ransomware. VirusTotal (image below) shows that leading security solutions, such as Kaspersky, McAfee or Mircosoft, did not stop Sigma Ransomware on its first appearance. While detection improved over time, for the critical first 24 hours the attackers clearly had the advantage of surprise.
Morphisec Prevented Sigma Out of the Box
Morphisec’s Moving Target Defense doesn’t rely on signature or behavioral patterns to stop malware. Morphisec stopped the Sigma Ransomware executable with no delay.
How does Sigma Work?
The encrypted Microsoft Word document is attached to an email with the plaintext password given within the email body. This is a common evasive technique used to bypass sandboxing. In addition, this makes it difficult for researchers that only have the Payload (.exe file) and did not actually receive the phishing email.
Once the malicious content is enabled ("enable content" prompt), the Microsoft Word document executes a VBA macro that downloads the dropper for the Sigma ransomware executable. The dropper then uses an ICMP protocol to check for internet connectivity. As we mentioned above, the dropper utilizes some techniques to ensure that it is not being analyzed. If all anti-sandboxing, anti-VM and anti-debugging tests are successfully completed, it will drop its payload — Sigma ransomware.
Sigma encrypts the files with AES / RSA on the infected system and also uses anti-sandboxing and some shellcode techniques to evade detection.
The encrypted files are appended with random extensions, although that might change in future versions or reconfigured strains. Additionally, a ransom demand is displayed that directs victims to a Tor site payment portal. Victims must pay up to $1000 or $2000 (after 7 days) in bitcoins to unlock their files. It also gives the user the option to chat with them in XAMP (account is Sigmaxxx@jabb.im) for decrypting one or some of their files.
Resources
https://phishme.com/threat-actors-put-greek-twist-ransomware-sigma/
IBM X-Force: Ransomware tops the spam charts
Hash: 8d54dbe841c95ba67549e8e28a4fbddbf87032e8736f01ec5a4563d3f7e6bfe1





.png?width=571&height=160&name=iso27001-(2).png)