On March 21,2018, Morphisec Labs began investigating the compromised website of a leading Hong Kong Telecommunications company after being alerted to it by malware hunter @PhysicalDrive0. The investigation, conducted by Morphisec researchers Michael Gorelik and Assaf Kachlon, determined that the Telecom group's corporate site had indeed been hacked. Attackers added an embedded Adobe Flash file that exploits the Flash vulnerability CVE-2018-4878 on the main home.php page.
The attack is a textbook case of a watering hole attack. Watering holes are a type of targeted attack where attackers plant malware on websites likely to be visited by their targeted victims, many times for cyber espionage purposes. The watering hole attack Morphisec investigated, exhibited very advanced evasive characteristics – the attack was purely fileless, without persistence or any trace on the disk, and used custom protocol on a non-filtered port. Generally, this advanced type of watering hole attack is highly targeted in nature and suggests that sophisticated threat actors are behind it.
This watering hole attack is only the latest in a huge number of attacks that utilize CVE-2018-4878 – from nation sponsored attacks to malspam campaigns to exploit kits.
Morphisec reported the infection to the site owner and the malicious Flash file has been removed from the compromised page. Morphisec customers are and were protected from this purely fileless, in-memory attack from the very first version of our Endpoint Threat Prevention solution.
This report presents the technical details of the campaign, starting from the exploit chain and ending with the in-memory Metasploit Meterpreter, its C2 and the custom 443 communication protocol that is still under research.
Exploit details
Image of the compromised website with embedded code:
The Flash exploit that was delivered has a high degree of similarity to the previously published analysis of the CVE-2018-4878. The major difference in this exploit is in the shellcode that is executed post exploitation:
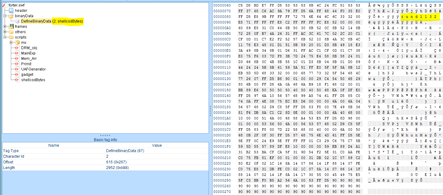
The shellcode executes rundll32.exe, a legitimate Windows process, and overwrites its memory with malicious code. The malicious code downloads additional code directly into the memory of the same rundll32 process.

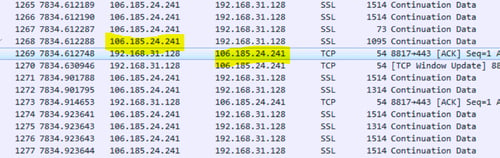
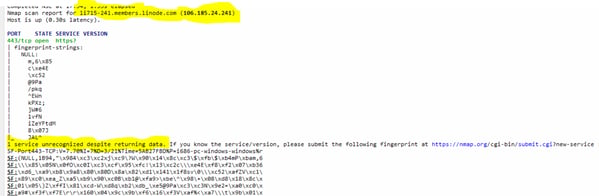
The C2 server (106[.]185.24.241) uses a custom protocol over 443 to communicate with the victim. Morphisec is still investigating the protocol and will update the blog later.
Metasploit Meterpreter:
The additional code that is downloaded into the memory of the rundll32 process includes the relevant Metasploit Meterpreter and Mimikatz modules (many of the modules are not aligned). We can clearly see that most of the modules were compiled on the 15th of February (less then a week before the attack).
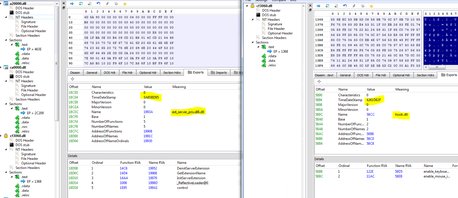
Below is a screenshot of the original Metasploit modules from Metasploit Github:
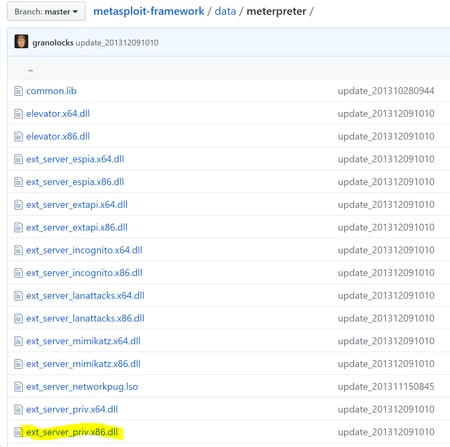
Conclusion
As our analysis shows, this watering hole attack is of advanced evasive nature. Being purely fileless, without persistence or any trace on the disk, and the use of custom protocol on a non-filtered port, makes it a perfect stepping stone for a highly targeted attack chain. This clearly suggests that very advanced threat actors are responsible for it.
On the other hand, when taking a deep look at the memory components of this attack, we identify basic Metasploit framework components that were compiled a week before the attack and do not exhibit any sophistication, obfuscation or evasion. This certainly muddies the waters.
At this time, no attribution is possible but Morphisec Labs will continue to investigate.
Looking at this attack, together with the exploit kits updated to include CVE-2018-4878, the exploit-based malspam campaign we discovered a few weeks ago and the use of the same vulnerability by nation-based groups, there is a sense of deja vu. It is like the anarchy of 2-3 years ago when we had new exploits targeting a particular vulnerability discovered every week. Each one different enough to evade detection for those crucial first moments and security solutions always racing to catch up.
Morphisec customers were always protected from this watering hole campaign, back from the first existing Morphisec production version.
Artifacts:
Flash - 58D15B7A49193022D8FB9712FAC1A9E2
C2- 106[.]185.24.241 (li715-241.members.linode[.]com:https)





.png?width=571&height=160&name=iso27001-(2).png)