
How an organization handles the time between the unleashing of a zero-day and the availability of a patch is telling. There are basically two kinds of companies – those that try to mitigate the risk as best they can while they wait for a patch and those that have a security tool able to prevent zero-days. The latest Flash-Player zero-day CVE-2018-4878 is yet another example.
Companies are being advised to uninstall Flash player until they can patch the vulnerability but Morphisec customers never had to worry about this zero-day. Organizations with Morphisec as a memory defense layer in their security stack get immediate prevention and continuous protection throughout the patching gap.
In the video below, Michael Gorelik, CTO and VP of R&D at Morphisec, shows you how Morphisec prevents the attack with ease.
Background
This newly spotted Adobe Flash zero-day vulnerability (CVE-2018-4878) is currently exploited in the wild. The flaw exists in Adobe Flash Player 28.0.0.137 and earlier versions; a patch by Adobe Systems is expected by the end of this week. First to report the vulnerability was South Korea’s KISA (KrCERT); Cisco Talos and FireEye performed initial investigations of the attack leveraging CVE-2018-4878.
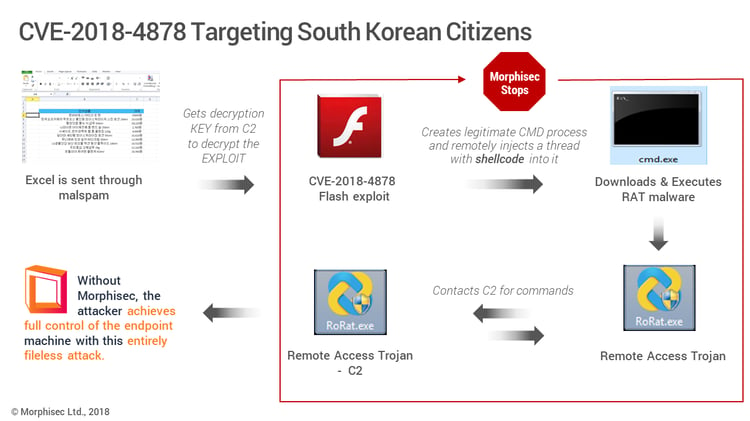
The currently active attack campaign is attributed to a North Korean hacking group, which Talos refers to as Group 123 and FireEye names TEMP.Reaper. Whatever the name, these threat actors are known to target the South Korean government and military, and demonstrate a rapidly accelerating ability to launch sophisticated attacks. This is the first known use of a zero-day by this group. The current attack installs ROKRAT, a remote administration tool that can exfiltrate data by capturing screenshots, logging keystrokes and evading analysis.
How Morphisec Prevents CVE-2018-4878 Exploits
In accordance with our standards for responsible reporting and to protect companies that are not our customers, we will only publish a deep-dive analysis of this attack after a patch is available.
 UPDATE 2/6/2018, 9mp! We are happy to report that Adobe has now released a new version, Flash Player 28.0.0.161, as the fix. Please return to our blog tomorrow for a deep-dive analysis with technical details that we could not publish until a patch was available. Our evaluation indicates that CVE-2018-4878 is likely to become one of the most targeted vulnerabilities of 2018 and will become a staple of the most prominent exploit kits.
UPDATE 2/6/2018, 9mp! We are happy to report that Adobe has now released a new version, Flash Player 28.0.0.161, as the fix. Please return to our blog tomorrow for a deep-dive analysis with technical details that we could not publish until a patch was available. Our evaluation indicates that CVE-2018-4878 is likely to become one of the most targeted vulnerabilities of 2018 and will become a staple of the most prominent exploit kits.
The below graphic describes phases of the attack, as well as at which points Morphisec Endpoint Threat Prevention solution stops the attack.
Resources
https://blog.talosintelligence.com/2018/02/group-123-goes-wild.html
https://www.fireeye.com/blog/threat-research/2018/02/attacks-leveraging-adobe-zero-day.html





.png?width=571&height=160&name=iso27001-(2).png)