This blog examines the Akira Ransomware as a Service (RaaS) group, to understand their Tactics, Techniques, and Procedures (TTPs), and validate how Morphisec’s patented Anti-Ransomware solution powered by Automated Moving Target Defense (AMTD) can prevent this ransomware threat, as well as comparative ransomware groups.

Introduction
Ransomware attacks are increasing in frequency and gaining notoriety. All ransomware incidents come with recovery costs, whether the encryption was successful or not. Business continuity, company and system downtime, combined with reputational damage and loss of trust can impact an organization’s bottom line for years after an attack strikes.
According to the Picus Security 2024 Red Report, defense evasion tactics are observed in over 30% of attacks. This means that no single security solution can be relied upon to stop threats. Instead, security teams must establish a multi-layered security obstacle course between critical assets and potential threats.
Therefore, enhancing business resiliency and fortifying the cybersecurity tech stack with dedicated anti-ransomware protection is a top priority for many organizations. Increasingly, targeted and evasive threats are bypassing detection-based solutions.
Akira Ransomware
Initially discovered in early 2023, Akira is a Ransomware as a Service (RaaS) group that gained prominence as a threat targeting small and medium-sized organizations. Like many ransomware groups, Akira employs double extortion techniques against victims by exfiltrating data prior to file encryption. This pressures victims to pay the demanded ransom, ranging from $200,000 to $4 million. Read this US HHS security advisory for technical details and Indication of Compromise (IOCs) of the Akira ransomware group.
Based on available information, Akira has primarily targeted organizations located in North America, UK and Europe, and is operating in the government, manufacturing, technology, education, consulting, pharmaceuticals, and telecommunication sectors.
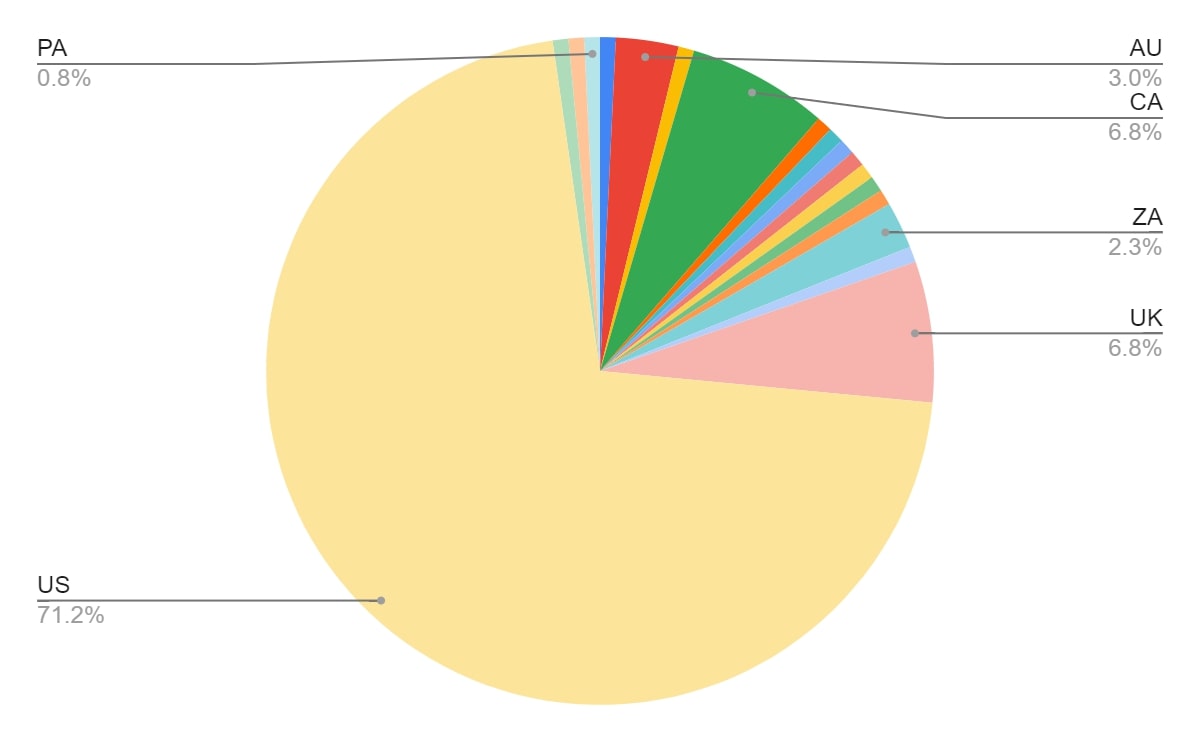 Akira victim distribution by country (Source: Trellix)
Akira victim distribution by country (Source: Trellix)
Akira is currently one of the most active global ransomware groups, accounting for dozens of monthly incidents, with over 150 published victims in H2 2023.
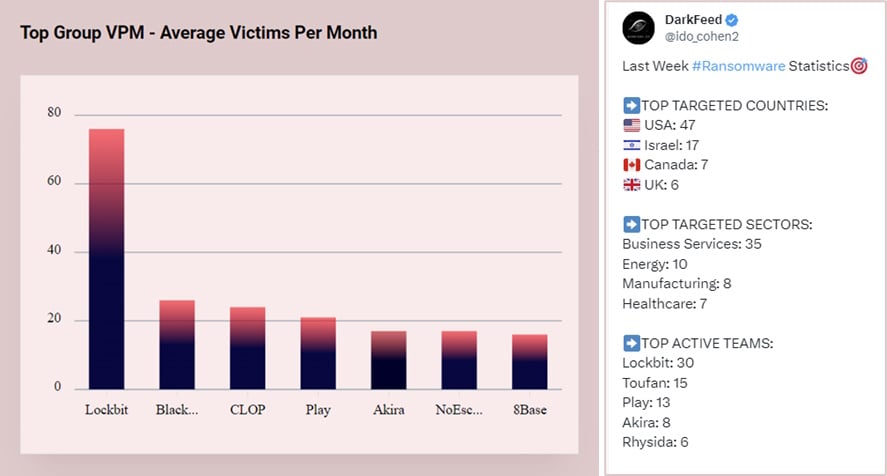
Top Active Ransomware Groups (Source: Darkfeed)
Earlier this year Akira achieved notoriety via a high-impact attack on Finnish cloud hosting provider Tietoevry. In this incident, Akira ransomware encrypted the provider’s data centers in Sweden, impacting multiple organizations including hospitals and businesses.
The costs and impacts of a ransomware attack
The reality is that all ransomware incidents carry costs, irrespective of whether the incident achieved data encryption/destruction and/or data exfiltration. Therefore, it is important for organizations to be aware of associated ransomware costs and incorporate them within their cyber defense strategy.
Factors to consider include:
|
# |
Factors |
|
1 |
Business Impact (Downtime) |
|
2 |
Engage Incident Response Specialist (Forensic Analysis) |
|
3 |
Man Hours (Recovery) |
|
4 |
Reputation Loss |
|
5 |
Brand Impact |
|
6 |
Higher Insurance Premium |
|
7 |
Investments in Additional Security Controls |
|
8 |
Legal Costs |
How Morphisec mitigates Akira ransomware
Rather than relying on detection, Morphisec’s Automated Moving Target Defense (AMTD) protects endpoints by morphing and randomizing system resources. This creates an unpredictable attack surface, whereby malicious code attempting to execute is instantly trapped and blocked.
Prevention of Akira ransomware – by TTPs
The following table explores the TTPs used by Akira and how Morphisec’s patented AMTD-powered ransomware prevention technology offers modular functionalities to prevent a ransomware incident like Akira, while ensuring the mean cost of recovery is minimized.
|
Tactics |
Description |
Methodology |
Morphisec Protection |
|
Escalation and Lateral Movement |
Elevate Privileges and steal credentials to further infiltrate into the organizations |
|
Morphisec’s AMTD-powered credential theft protection prevents LSASS DUMPS, Mimikatz and LaZagne module execution. This feature would provide early visibility of attackers presence and effectively would be able to contain the attack quickly. |
|
Discovery |
Enumerate the environment |
|
Morphisec prevents Advanced IP Scanner and other tools which are used by hackers again there by providing early visibility of the attack leading to quicker containment |
|
Defense Evasion |
Evade the Cyber-security Defense stack |
|
Morphisec’s Exposure Management module provides constant validation of security controls and flags deviation to a baseline thereby discovering the tampering activity quickly and allowing quick containment of the Incident much before the Impact stage is reached. |
|
Command and Control |
Backdoor access to the environment |
|
Morphisec’s Exposure Management module provides Visibility to High Risk Software and flags presence of remote access software’s in the environment thereby allowing to manage the attack surface better. |
|
Exfiltration |
Exfiltrate Data outside of organizations |
|
Morphisec’s Exposure Management module provides Visibility to High Risk Software and flags presence of exfiltration tools like rclone and mega in the environment thereby allowing to manage the attack surface better. This module also flags usage of chrome in the environment which is mostly used by adversary group to download malicious software on the system. This feature provides early visibility of the attack which would lead to quicker containment |
|
Impact |
Execute the ransomware payload to encrypt data |
Customized executables to encrypt data. |
Morphisec’s AMTD-powered Ransomware Defense module protects organizations from ransomware encrypting critical data, as well as protects system recovery and backups against tampering The module works in the Impact stage and is proven to prevent a wide range of ransomware families at various stages of the encryption process |
Summary
Morphisec’s Anti-Ransomware, powered by AMTD, combines multiple security layers to prevent ransomware, including Akira from preliminary attack stages through the final impact phases.
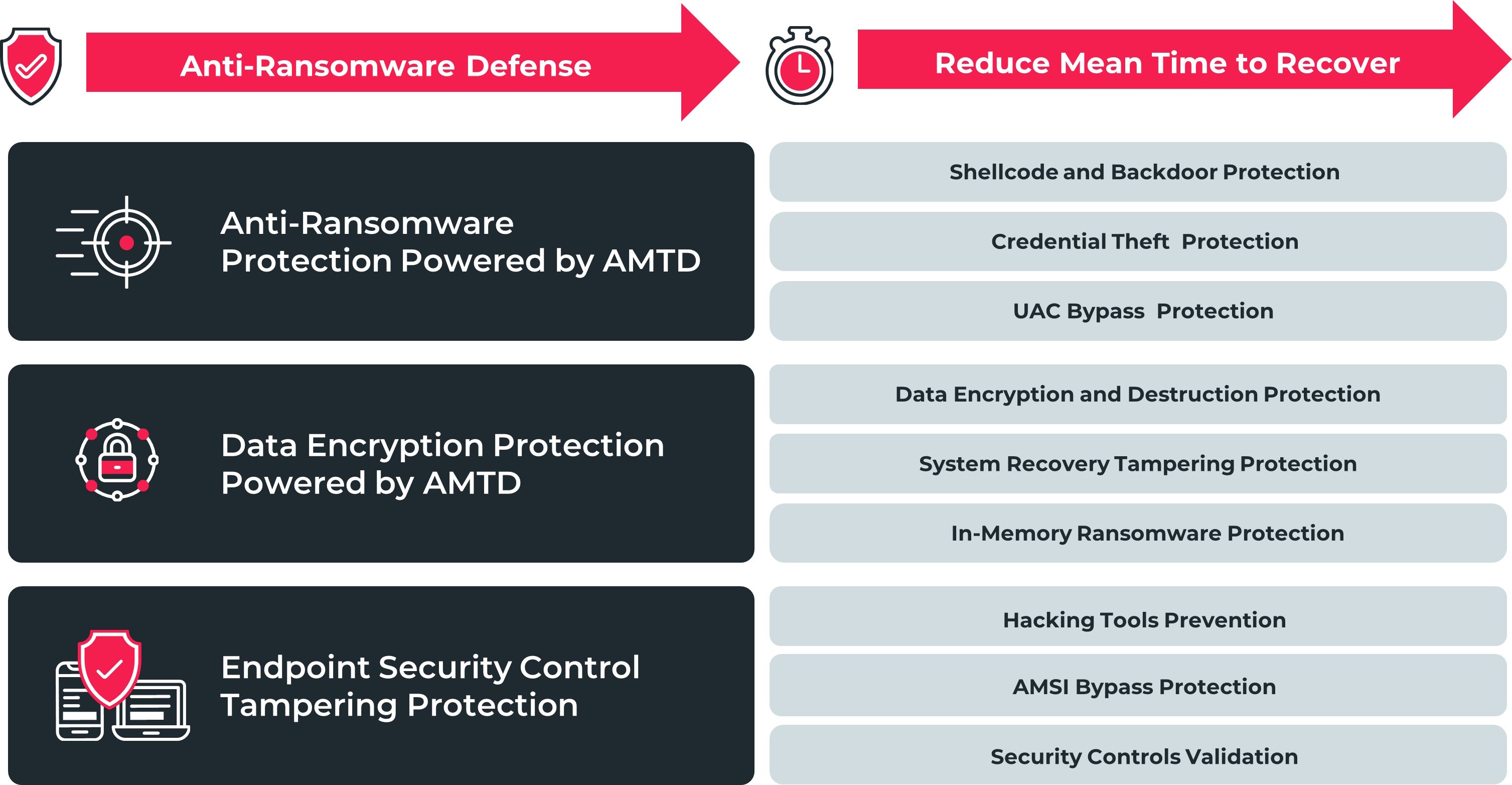
By adopting the power of AMTD, organizations can augment their existing cybersecurity tech stack, and build a credible and resilient ransomware prevention strategy.
Morphisec’s AMTD technology marks the next evolution in cybersecurity, protecting more than 9 million devices, routinely preventing ransomware and highly evasive attacks that bypass leading endpoint protection solutions, including EDR/XDRs.
Schedule a demo today and see why more than 7,000 companies trust Morphisec to secure over 9 million endpoints and servers.





.png?width=571&height=160&name=iso27001-(2).png)