 In August of 2019, just a month after our publication on a targeted BitPaymer/IEncrypt campaign, Morphisec identified a new and alarming evasion technique that the same adversaries adopted while targeting yet another enterprise in the automotive industry.
In August of 2019, just a month after our publication on a targeted BitPaymer/IEncrypt campaign, Morphisec identified a new and alarming evasion technique that the same adversaries adopted while targeting yet another enterprise in the automotive industry.
This time we have identified the abuse of an Apple zero-day vulnerability in the Apple Software Update utility that comes packaged with iTunes for Windows. The Windows exploit is important to note given Apple is sunsetting iTunes for Macs with the release of macOS Catalina this week, while Windows users will still need to rely on iTunes for the foreseeable future.
The adversaries abused an unquoted path to maintain persistence and evade detection. Morphisec followed responsible disclosure policies and immediately shared the details of the attack with Apple. Within the disclosure period and while waiting for the official patch, Morphisec has identified and reported on additional vulnerable components that could be similarly misused. We are releasing the attack details following an official Apple update release that can be found here.
TECHNICAL DETAILS
As described in the introduction, the adversaries abused an unquoted path vulnerability. The unquoted path vulnerability is rarely seen in the wild, yet it is a well-known bug that has previously been identified by other vendors for more than 15 years (e.g. Intel Management Engine, ExpressVPN, ForcePointVPN). In most cases, the vulnerability is mentioned in the context of privilege escalation because it exists in a service or other process with administrative execution rights. It is so thoroughly documented that you would expect programmers to be well aware of the vulnerability. But that is not that case, and this Apple zero-day is evidence.
Software developers are using more and more object-oriented programming, and many times when assigning a variable with a path, they assume that using the String type of the variable alone is enough – well it's not! The path still needs to be surrounded by quotes ("\\").
Apple Software Update, a mechanism that Apple uses to deliver future updates, includes one of these unquoted paths. Apple Software Update has its own installation entry in the installed software section and a scheduled task to execute the process.
In most cases, people are not aware that they need to uninstall the Apple Software Update component separately when uninstalling iTunes. Because of this, machines are left with the updater task installed and working. We were surprised by the results of an investigation that showed Apple Software Update is installed on a large number of computers across different enterprises. Many of the computers uninstalled iTunes years ago while the Apple Software Update component remains silently, un-updated, and still working in the background. Following this discovery, we identified the attack surface and the motivation of the attacker to choose this process for evasion.
BYPASSING DETECTION
As many detection solutions are based on behavior monitoring, the chain of process execution (parent-child) plays a major role in alert fidelity. If a legitimate process signed by a known vendor executes a new malicious child process, an associated alert will have a lower confidence score than it would if the parent was not signed by a known vendor. Since Apple Software Update is signed and known, the adversary uses this to their advantage. Furthermore, security vendors try to minimize unnecessary conflicts with known software applications, so they will not prevent this behavior for fear of disrupting operations.
Additionally, the malicious "Program" file doesn't come with an extension such as ".exe". This means it is likely that AV products will not scan the file since these products tend to scan only specific file extensions to limit the performance impact on the machine. In this scenario, Apple Software Update was trying to run from the "Program Files" folder, but because of the unquoted path, it instead ran the BitPaymer ransomware since it was named "Program". This is how the zero-day was able to evade detection and bypass AV.
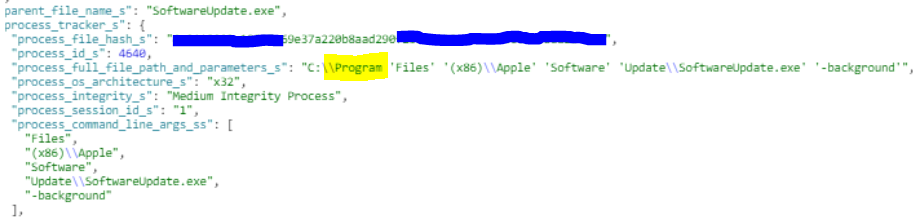
As mentioned before, following this discovery we identified more unquoted path vulnerabilities in the iTunes software and installer. We also note that the malicious file doesn't have to be placed in the C drive and called Program. It can also be called Apple or Apple Software and placed in Program Files. Of course, the adversary would need write-privileges for any of those folders. We haven't observed any possible privilege escalations due to this vulnerability.
CONCLUSION
The BitPaymer/IEncrypt group exhibits an advanced innovative spirit, previously with the identified defender emulator bypass and now with this EDR and AV bypass using the unquoted path in the Apple Software Update program. The group must have performed serious reconnaissance research to consistently stay one step ahead of the defenders.
Morphisec refrained from publishing the vulnerability while waiting for an official update.
Morphisec prevented the attack before any damage could have been caused.
10/11/19 Update: During revalidation of the exploit, and as we continue to work with Apple on further vulnerabilities that have yet to be patched or announced, we observed that the abused vulnerability relates specifically to an Apple Software Update component that is not associated with Bonjour.




.png?width=571&height=160&name=iso27001-(2).png)