
Cerber ransomware is one of the most sophisticated and popular ransomware families, attacking victims across the globe. Additional popular ransomware families in the cybercriminal’s arsenal include Locky (Osiris), Spora, Shade and several others.
Beginning February 16, Morphisec witnessed a new wave of Cerber. Cerber 4.0/5.0, as shown in our video, now encrypts files with random extensions. After encrypting the files, Cerber presents a ransomware note by executing an .hta file. In addition, this Cerber version also contains botnet functionality.
While in the past Cerber ransomware was mostly delivered by exploit kits, today we see a shift to email delivery, similar to the methods that have been used to deliver Locky ransomware. By turning to emails, Cerber increases its pool of victims and profits.
As of the time of this publication, there are still no decryption tools available for Cerber 4.0/5.0. This adds to the importance of preventing Cerber ransomware in first place, with a solution such as Morphisec Endpoint Threat Prevention.
The attack video below shows Morphisec in action preventing the ransomware before it can execute. It also shows what happens without Morphisec!
This wave of ransomware was delivered using two types of email attachments:
- A WORD document weaponized with a malicious macro. The document file is named with a random number. As soon as the victim enables the macro, the attack activates PowerShell from cmd. The PowerShell scripts download a Roaming.exe file, which is the actual Cerber executable. The Roaming.exe will execute from a very specific user temp directory, AppData.
- A JavaScript file. Also here the file will have a random number as its name. If executed, JavaScript activates a cmd with PowerShell; this time the PowerShell downloads a random name executable in a different lower user directory (AppData/Local/Temp).
After the execution of the Cerber malicious executable, the ransomware decrypts the files on disk within a very short time (much faster than before), and presents the visual and audio supported note to the user. Notice that the new common practice of decrypting one file for free has been incorporated (it gives victims a kind of reassurance that the decryption will work).
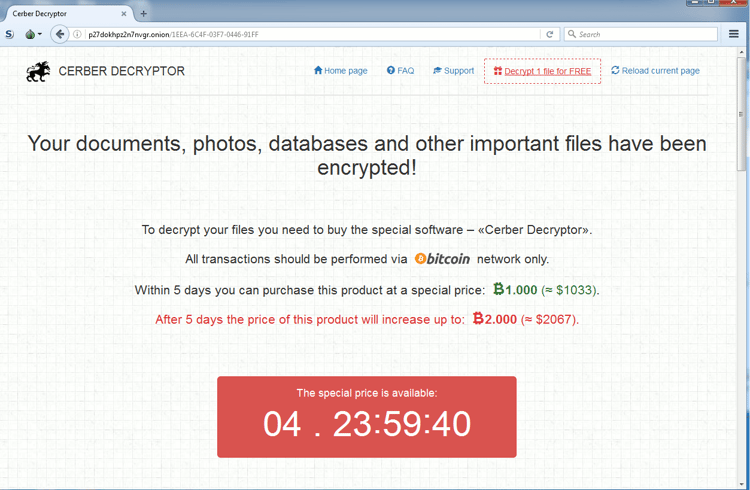
More Expensive Than Ever
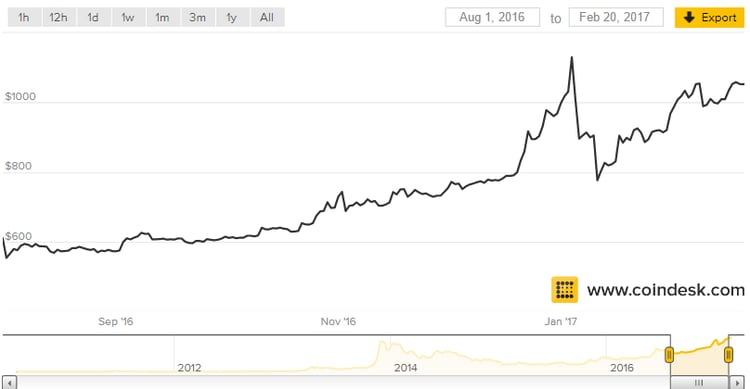
Victims will have to dig deeper into their pockets to get their files back. The decryption costs one bitcoin as before, but we can see inflation in this market as the value of a bitcoin in August, 2016 was about half of its current value ($590 vs. $1033), as shown in the chart below.





.png?width=571&height=160&name=iso27001-(2).png)