
In the current state of cyber security, the bad guys have the upper hand. Cybercrime is an industry, in which huge investments are made by criminal elements. Why? Because ROI is basically guaranteed. Building attacks takes time, requires patience, research, persistence and a good plan that considers the predictability of IT systems and users. Unfortunately, the bad guys seem to have an infinite amount of all of these, and IT systems and users are fairly predictable. So, are we forever doomed to pay millions of dollars in unsuccessful attempts to protect ourselves?
HOW MUCH DOES A SECURITY BREACH COST?
The total average cost of a data breach is now $3.8 million, up from $3.5 million a year ago, according to a study sponsored by IMB and conducted by Ponemon Institute, a data security research organization. “The direct costs include hiring experts to fix the breach, investigating the cause, setting up hotlines for customers and offering credit monitoring for victims,” the report states.
These average costs do not apply to mega-breaches affecting millions of end-customers, such as those suffered by JPMorgan Chase, Target and Home Depot, which cost the companies far greater sums. Target alone said last year its breach cost $148 million. Sony, following the 2014 breach, reported direct damage costs of up to $35M according to a Network World article. These costs do not account for reputation damages, which are hard to measure in terms of lost business, or brand preservation costs.
One must consider that targeted attacks penetrate through all the costly fences and defenses enterprises put in place to keep their data and their customers’ data safe. This means that in addition to cost of damage, all of the cybersecurity operating expenses (OPEX) prior to the breach need to enter the calculation. Money is spent on patching system vulnerabilities, installing layers of technical equipment, and handling all the false positives or negatives that these technologies alert about - one of the more irritating, time consuming and costly aspects of security operations. Once you take all this into account, the equation just does not make any business sense.
NEW LAYERS DO NOT EQUAL LESS COSTS
Today, enterprises keep adding more security layers and more personnel to manage them. It has become similar to buying additional insurance policies for the same risk. Actuarial calculations define the risk mitigation equation in which, in the big picture, the insurance company always wins. But this type of thinking does not translate to enterprise cybersecurity risk, does it?
Recently, a CISO told me he cannot identify the contribution of a specific HIPS agent his company added long time ago, one of seven agents; its value in the risk mitigation equation is long forgotten, except that it is required by regulation.
Companies, realizing this and unhappy with current prevention solutions, are adding security solutions that can detect and respond before a breach occurs, commonly known as EDR - Endpoint Detection and Response. Some of these products detect later and some earlier, but similar characteristics and limitations apply to all of them:
- They all fight a rearview mirror battle. Whatever technology they use – signatures, behavioral analysis, heuristics – they rely on what happened yesterday to try and anticipate what will happen tomorrow. These rules, heuristics, databases need continuous and frequent updates.
- In order to be effective, most new EDR tools require an attack to already be in the system; something already needs to have happened to trigger their response.
- So-called next generation Anti-Virus solutions are still file based. This is the same old game, replayed with some incremental improvements. As this fascinating article in CTOvision states, detection, inherently means decision-making which implies that there will be false alarms.
EARLY PREVENTION FOR MINIMIZED COSTS
The only way out and to significantly lessen the financial impact of cybercrime is to stop attacks very early and reduce patching and false positives. But, is it possible? If we graph the anatomy of targeted attacks versus the associated costs, the graph could look like figure 1.
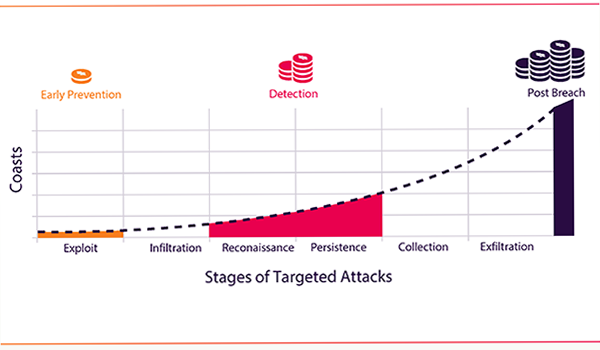
Clearly, early prevention, i.e. at the first step of an exploit, stopping application and OS based attacks before they ever start can provide the largest benefit: a) no breach brand damages; b) better patching cost management; c) far fewer detection-related false alarm costs; and d) no breach remediation costs.
Is this the case where both the “insurance company” and the “insured” could be winners, and the attacker becomes the only loser? Can there be a “policy premium” that would be worth every penny spent? Yes it is, and yes there could be, but for this to work a new approach to End Point Prevention is needed. An approach where the attacker never finds the target application or vulnerability it is trying to exploit. What would be the key requirements for such effective prevention?
- Make OS, applications and file based vulnerabilities inaccessible to the attackers, by constantly and unpredictably hiding them, or “moving them around,” so attackers cannot find them; you can’t attack that which you don’t see.
- Complement anti virus; add defense-in-depth prevention layer where AV notoriously fails, but yet leverage the value of AV.
- Be simple to install and manage. The challenge is to provide a powerful prevention system but yet one that is simple to deploy and manage and one that does not affect performance.
A new breed of solutions based on Moving Target Defense - the essence of moving the attack targets around before an attack – fits all three key requirements.
Schedule a demo for more information about how Morphisec Moving Target Defense can help you to cut your security costs.




.png?width=571&height=160&name=iso27001-(2).png)