The recent leap towards cloud computing has fast-forwarded digital transformation for countless organizations. What there hasn’t been, however, is a corresponding improvement in the ability of organizations to secure the cloud. In fact, as more companies rely on the cloud to maintain their operations, they also risk accruing a cybersecurity deficit. In a survey conducted in February, over 60 percent of cybersecurity professionals indicated that their cloud implementation was already beyond their abilities to reliable secure these environments.

Since then, with cloud migration proceeding at a record pace, this gap has undoubtedly increased further. To reduce the risk of a damaging attack in the “cloud-first” era, organizations need to rapidly reassess whether their cloud security architecture is fit for purpose.
This reassessment is necessary because, even though the cloud has upended application deployment environments, businesses are still likely to use unsuitable security controls for protecting their cloud workloads.
For many, this means using a defense-in-depth approach and relying on stalwarts such as antivirus protection, application firewalls, allowlisting, and intrusion detection systems. This threat-focused approach to cybersecurity is inherently reactive in its approach. Unfortunately, this means that it's ultimately ineffective when it comes to protecting cloud workloads from the types of threats that make headlines today.
Rather than chasing down threats after they make themselves known, cloud security necessitates a proactive approach.
The unsuitability of a reactive approach, which often relies on a security analyst sorting through a barrage of false positives to identify genuine threats, is compounded by an ongoing shortage of cybersecurity staff. For understaffed cybersecurity teams, the centralized nature of reactive security approaches makes adequate cloud security impossible.
 For their companies, this also places a hard limit on cloud migration. As they expect their cloud computing workloads to scale quickly, organizations soon find that their people do not. Therefore, securing workloads, which are often run in hybrid and multi-cloud environments, requires a different approach.
For their companies, this also places a hard limit on cloud migration. As they expect their cloud computing workloads to scale quickly, organizations soon find that their people do not. Therefore, securing workloads, which are often run in hybrid and multi-cloud environments, requires a different approach.
Rather than chasing down threats after they make themselves known, cloud security necessitates a proactive approach. Being proactive means understanding the unique constraints of cloud workloads and creating a security architecture designed to get ahead of the types of attacks they face. Otherwise, by the time detection-centric platforms identify a cloud workload attack it could be too late.
Taking a Long Term View of Cloud Workload Security
Part of this process means adopting a willingness to invest in a long-term cloud security strategy. Even as the technical understanding of cloud security has advanced, many organizational approaches to security remain behind the curve. While technologies like containers and virtualization allow workloads to be isolated from both each other and host networks, IT teams often fail to secure them correctly.
This negligence is partly due to uncertainty as to whether they need to — the lines which cloud providers like AWS and Azure draw around their security responsibilities are often difficult for their customers to delineate. A recent Gartner report directly links a lack of understanding of the “shared responsibility model” common among cloud providers with many high profile data breaches.
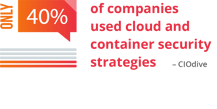
Stemming from overconfidence in the integral security of cloud environments and a misunderstanding about their responsibilities, it's clear that IT teams don't always apply appropriate security controls to cloud workloads. A study conducted last year showed that despite 93 percent of companies using a public cloud, only 40 percent used cloud and container security strategies.
As cloud computing moves security away from a command and control model to a permission-based one, securing cloud workloads now needs to become the responsibility of anyone who interacts with a cloud service.
The key to securing cloud workloads is to see their security as a long term process. Rather than just relying on shutting the door through techniques like application controls and allowlisting, cloud users need to stay ahead of threat actors by being proactive when it comes to protection.
Taking a Proactive Approach to Cloud Workload Security
The consequences of an exposed weak point in a cloud workload underscores the importance of taking a proactive approach. Threat actors are increasingly adept at finding minuscule weak points in their victims’ defenses. Whether delivered through fileless malware or more traditional methods, attacks can easily bypass controls like application control and zero trust networks by exploiting allowlisted applications and existing user permissions.
 Relying on detection-based technology to address advanced threats creates too much risk since even in a best case scenario with a mean time to remediation of less than a day, significant damage can occur. Although malicious activity might be detected in a cloud workload while an attack is in process, there can still be serious implications.
Relying on detection-based technology to address advanced threats creates too much risk since even in a best case scenario with a mean time to remediation of less than a day, significant damage can occur. Although malicious activity might be detected in a cloud workload while an attack is in process, there can still be serious implications.
Cloud-based platforms lack the security perimeter of network firewalls that corporations can use to secure on-premises servers. Ultimately, it’s this perimeter-less nature of the cloud combined with the high likelihood of misconfiguration makes cloud data breaches incredibly destructive.
In contrast, a proactive approach covers both the entry points to a cloud workload and the network itself. It does this by securing the two cornerstones of cloud cybersecurity: exploit prevention and memory protection. Cloud workload attacks are ultimately memory-based, so protecting against exploits and in-memory attacks provides the strongest security posture.
The Cornerstone of Cloud Workload Security
To make a proactive approach work, an organization needs to harden their cloud workloads against the threats that are most likely to bypass their reactive controls and make all of their cloud users security-aware. By turning cloud workloads into moving targets, Morphisec’s Automated Moving Target Defense solution prevents zero-day attacks, fileless threats, in-memory exploits, and evasive malware in cloud workloads. In doing so, it forms an ideal cornerstone for a long-term proactive cloud security framework. As part of a proactive approach to cloud workload cybersecurity, Morphisec keeps cloud users safe.





.png?width=571&height=160&name=iso27001-(2).png)