
The disappearance of Angler has left a gaping hole in the malware market which cybercriminals are only to happy to fill with new variants of old standbys. The latest to reemerge after a period of disuse are Locky and Dridex. A new Locky campaign spotted in the wild on June 20 is analyzed by Pierluigi Paganini on the Security Affairs site. Now a bigger and badder Dridex has reappeared, with more sophisticated evasion tactics, including a new sandbox evasion technique.
Following is an analysis of the latest Dridex version, whose campaign started on June 29, 2016 and which had 0/55 score for the first 2 days it was uploaded:
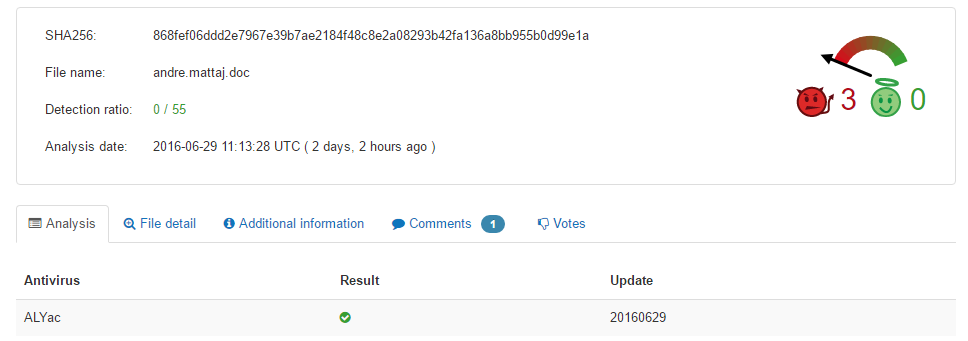
SHA256: 868fef06ddd2e7967e39b7ae2184f48c8e2a08293b42fa136a8bb955b0d99e1a

Macro Analysis:
The macro is heavily obfuscated:

Proofpoint already documented two evasion techniques:
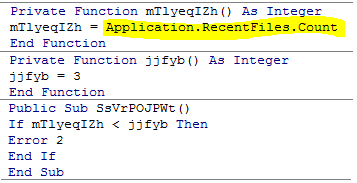
1. Check for the number of files recently accessed by Microsoft Word:
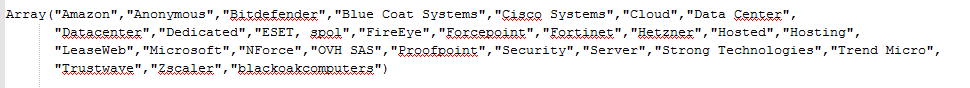
2. Contact a well-known geo-location service (https://www.maxmind.com/en/locate-my-ip-address) and check the returned result against a blocklist of strings (this time the extended the array of strings by adding “Trustwave” and “Zscaler”):
NOW THE MACRO ADDED ONE MORE EVASION TECHNIQUE:
Testing the Logged-on username against the following strings: "KR3T","PSPUBWS". If username contains one of those strings the attack is aborted.
The latest evasion technique is very interesting; it seems that the attackers tried to identify the popular https://www.hybrid-analysis.com/ vxStream Sandbox service, by going over their logs and looking for the username that is used when scanning documents.

Where “k3rt” is most likely username of some other popular scanning service (malwr.com)
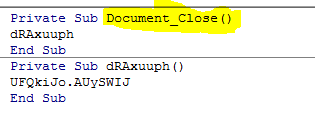
- The macro is only activated upon the closing of the document – although this is one of the weakest evasion techniques, it still works for some of the weaker dynamic sandbox analyzing tools:
Payload:
After validation that the user is a normal end-user and not a sandbox, it downloads the payload from the following site [hxxp://pawscoach.com/office.12] using the following PowerShell.

Here are some Dridex samples from the last few days:
- 839fa9189e4f3d0999b61f3a1c110aa74ff6a9a31f3f113ede8511da749bae8e (0/55)
- 414c4b62609cac1f10443087bb34d426dd24f82399eb9e9042791977913b75e1 (1/53)
- 1d624baa37217957e440643e09df18e9ef1e5a526f2dea078804cff01476f733 (2/53)
- 842ddb4eb313371d97904a6b85a84ec60e9954c36661c52b6194e135c924ba89 (7/51)
- b38341709439c85d39eeaa2575c6aba0563fef6ec8498ff9ff830d1950cd396f (7/53)
- …





.png?width=571&height=160&name=iso27001-(2).png)