Introducing egregor ransomware
Egregor is considered to be one of the most prolific ransomware threat groups. Yet it gained this reputation in a very short time due to its uncompromising double extortion methodology.
In this report, we will provide a detailed and anonymized coverage of Egregor ransomware's tactics, techniques, and procedures (TTPs) following an incident response activity that was conducted at the end of November 2020.
The goal of this report is to shed light on some very different techniques for initial access, persistence, and exfiltration than what is typically reported on with respect to the Egregor group. In this report, you will not find any indication of Qbot or Cobalt Strike beacons.
Though we are not going to provide an exact attribution, you will find evidence in the report that may indicate a connection to the Revil group. We will provide evidence such as upload accounts, download links, and services that can result in additional community wide research which hopefully can lead to further conclusions.
We invite the research community to share additional insights that may correlate with the published IOCs.
Technical Introduction
Any incident response involving business compromise usually starts with the end - the impact. When the impact is ransomware, incident investigation is particularly difficult as it is done in parallel to containment activities.
This investigation wasn’t different from most that involve ransomware:
- The AD is compromised and the ransomware is deployed directly from the AD.
- A search and mapping of suspicious connections to the AD are correlated to legitimate activities and connections of privileged users. RDP, pass the hash, and other techniques are taken into account.
- Compromised credentials or/and a lateral movement chain is established and patient zero is identified. Obviously, if logs exist, SIEM, event viewers, VPN, AV, and other logs are considered.
- In the case of ransomware, the customer would usually like to know what was exfiltrated to be able to calculate business continuity risks.
- In the last stage, victims like to have a recommendation report for corrective actions that can be applied to the network.
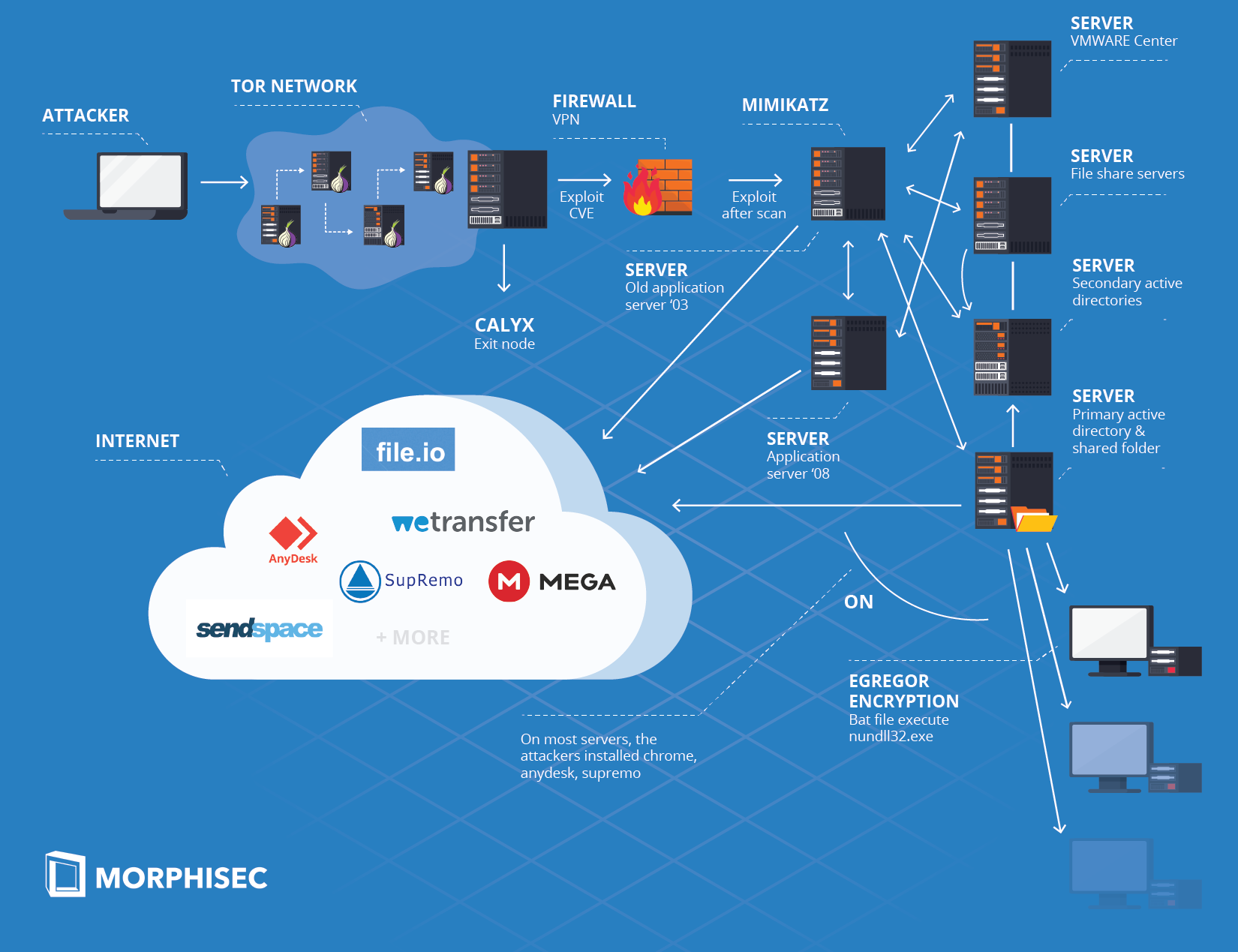
Our incident investigation revealed that the Egregor threat group most probably exploited a VPN vulnerability to access the internal network from a Tor exit node. The attackers then scanned the network while looking for a vulnerable server. They quickly identified and exploited a second vulnerability on an old 2003 application server. This application server became our patient zero. The attackers then moved laterally between file share, application, virtualization, update, and secondary AD servers until they infiltrated to the AD. Next, they exfiltrated data through known services such as MegaUpload directly from the AD. As a final step, they encrypted the network.
A number of interesting and unique details will be mentioned in this report:
- The upload account credentials and the additional file share services
- Persistence through known legitimate remote control services
- Download multiple versions of the ransomware while bypassing enterprise AV solution
- The use of AES.ONE for ransomware download
- Connection to Revil through Lalartu
Download the report "An Analysis of the Egregor Ransomware" for the rest of our analysis.





.png?width=571&height=160&name=iso27001-(2).png)