
It may sound odd, but cybersecurity has a huge emotional component. Unlike other industries that are driven by optimization and financial gains, cybersecurity has all the makings of a Hollywood movie—good guys, bad guys, nation-states attacking other nation states, and entire global IT systems at risk. Unfortunately for most victims of a cyber threat or breach, the effects are all too real and don't disappear when the music stops and the lights come on.
As with a good blockbuster, in cybersecurity you can expect highs, lows, thrills and chills. When new risks and threats appear, businesses get worried (justifiably so), and demand for new and innovative solutions increases dramatically. Security managers and innovative solution providers then scramble to respond with a fresh set of tools and services aimed at mitigating the newly discovered threats.
Because cybersecurity is intrinsically linked to all levels of criminal activity—from petty thieves to large-scale organized crime syndicates—cybersecurity is a never-ending story.
Yet, curiously, these vicious cycles of new threats followed by new innovations, present subtle patterns that, once identified, can help us make better decisions to not only address the damage, but also manage demand for better solutions faster and more efficiently.
Cybersecurity Du Jour
When you've been in the cybersecurity industry for a while like I have, you notice that in each era, there is always a popular defense paradigm "du jour" that occupies and defines the industry state-of-mind. This paradigm becomes the defining model (at least temporarily) that everyone—analysts, tool builders, and even the technology end users—advocate fiercely. By the same token, the "roster" of terms that define these security paradigms is also cyclical. The core defense concepts (borrowed from the military) of prevention, detection, and containment keep cropping up, however in each time period, one or another of these paradigms takes precedence. Which term is more popular can represent critical shifts in widespread thinking with regards to cybersecurity.
Dissecting the Ambiguous? Perception of Defense Paradigms
The defense paradigms of prevention, detection, and containment serve dual roles: as cyber defense strategies and as categories for different defense products. However, the first challenge encountered by both cybersecurity professionals and end users is that these terms don’t have a consistent general meaning; trying to give a single definition of each of these terms is like attempting to build a castle on shifting sand (although that doesn’t stop people from trying). From a professional security point of view, there are different worlds in which specific targets, specific threats (new and old), and a roster of defenses exist. Each specific world is a security domain in and of itself, and this domain serves as the minimum baseline context for the concepts of prevention, detection, and containment. Each particular threat in a security domain defines the boundaries and the roles of these concepts. In addition, these concepts serve as categories, where particular, but related tools can be assigned to one or more category based on the way the tool operates.
Ultimately, these defense concepts have a concrete meaning that is specific and actionable only within a specific security domain. For instance, a security domain can be defined by the type of threat, the type of target, or a combination of the two.
So, for example, there are domains that represent groups of threats with common patterns, such as advanced attacks on enterprises (of which advanced persistent attacks or APTs are a subset) or denial of service attacks on online services. In contrast, there are security domains that represent assets, such as protecting websites from a variety of different threats including defacement, denial of service, and SQL injection through its entry points. The determining factor in defining the security domain approach depends on the asset – and the magnitude of risk it can be exposed to – or on the threat group and its commonalities among multiple threats.
Examples, Please
To make this more tangible let's discuss a couple of examples by defining the security domain elements and explaining how the security concepts of prevention, detection, and containment need to be defined from within the domain.
Advanced Attacks
Let's assume that the primary attack vector for infiltration into the enterprise is via endpoints; the next phase of lateral movement takes place in the network via credential theft and exploitation; and exfiltration of data assets is conducted via HTTP covert channels as the ultimate goal.
Advanced attacks have a timeline with separate consecutive stages starting from entrance into the organization and ending with data theft. The security concepts have clearly defined meanings, related specifically to each and every stage of advanced attacks. For example, at the first stage of infiltration there are multiple ways malicious code can get into an employee computer, such as opening a malicious document or browsing a malicious website and installing a malicious executable unintentionally.
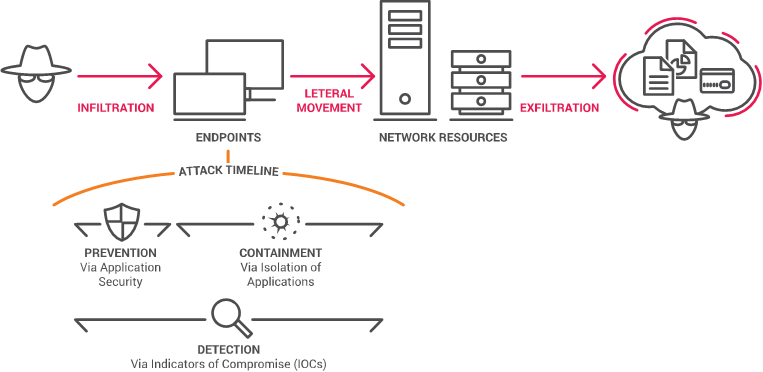
In the case of the first stage of infiltration of advanced attacks, "prevention" means making sure infiltration does not happen at all; "detection" means identifying signs of attempted infiltration or successful infiltration; and "containment" means knowing that the infiltration attempt has been stopped and the attack cannot move to the next stage.
Web Site Protection
Web sites can be a target for a variety of different types of threats, such as security vulnerabilities in one of the scripts, misconfigured file system access rights, or a malicious insider with access to the web site's backend systems. From a defensive point-of-view, the website has two binary states: compromised or uncompromised.
Therefore, the meanings of the three defense concepts are defined as prevention, any measure that can prevent the site from being compromised, and detection, identifying an already-compromised site. In this general example, containment does not have a real meaning or role as the only way to contain a successful web site infiltration is to remove the site from the network, which serves no long-term security purpose. Within specific threats against specific web sites there may be a role for containment, such as preventing malvertising from propagating to the visitors’ computers.
It’s an Emotional Decision
So, as we have seen, our three key defense concepts have different and distinctive meanings that are highly dependent on their context, making broader definitions somewhat meaningless. Still, cybersecurity professionals and lay people alike strive to assign meaning to these words, because that is what the global cybersecurity audience expects: a popular meaning based on limited knowledge, personal perception, desires and fears.
The Popular Definitions of Prevention, Detection and Containment
From a non-security expert point-of-view, prevention has a deterministic feel – if the threat is prevented, it is over and done with. Determinism gives the perception of complete control, high confidence, a guarantee. Prevention is also perceived as an active strategy, as opposed to detection which is considered more passive (you wait for the threat to come, and then you might detect it).
Unlike prevention, detection is far from deterministic, and would be classified as probabilistic, meaning that you might have a breach (85% chance). Detection tools that tie their success to probabilities gives assurance by degree, but never 100% confidence.
Interestingly, containment might sound deterministic since it gives the impression that the problem is under control, but there is always the possibility that some threat could have leaked through the perimeter, turning it into more of a probabilistic strategy. And it straddles the line between active and passive. Containment passively waits for the threat, and then actively contains it.
In the end, these deterministic, probabilistic, active and passive perceptions end up contributing to the indefinite meaning of these three terms, making them highly influenced by public opinion and emotions. The three concepts in the eyes of the layperson turn into three levels of confidence based on a virtual confidence scale, with prevention at the top, containment in the middle, and detection as a tool of last resort. Detection gets the lowest confidence grade because it is the least proactive, and the least definite.
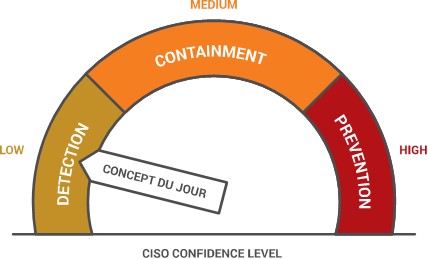
Today’s Defense Concept and What the Future Holds
Targets feel more exposed today than ever, with more and more organizations becoming victims due to newly discovered weaknesses. Attackers have the upper hand and everyone feels insecure. This imbalance is currently driving the industry to focus on detection. It also sets the stage for the "security solution du jour." When the balance leans toward the attackers, society lowers its expectations due to reduced confidence in tools, which results in a preference for detection. At a minimum, everyone wants to at least know an attack has taken place, and then they want to have the ability to mitigate and respond by minimizing damages. It is more about being realistic and setting detection as the goal, when there is an understanding that prevention is not attainable at the moment.
If and when balance returns and cybersecurity solutions are again providing the highest level of protection for the task at hand, then prevention once again becomes the holy grail. Ultimately, no one is satisfied with anything less than bullet-proof prevention tools. This shift in state-of-mind has had a dramatic impact on the industry, with some tools becoming popular and others being sent into oblivion. It also has impacted the way CISOs define their cyber strategies.
Different Standards for Different Contexts
The behavior when selecting the preferred defense concept also has a more granular resolution. Within each security domain, different preferences for a specific concept may apply depending on the state of the emergence of that domain. For example, in the enterprise world, the threat of targeted attacks in particular, and advanced attacks in general, used to be negligible. The primary threats ten years ago were general-purpose file-borne viruses targeting the computing devices held by the enterprise, not the enterprise itself or its unique assets. Prevention of such attacks was once quite effective with static and early versions of behavioral scanning engines. Technologies were initially deployed at the endpoint for scanning incoming files and later on, for greater efficiency, added into the network to conduct a centralized scan via a gateway device. Back then, when actual prevention was realistic, it became the standard security vendors were held to; since then, no one has settled for anything less than high prevention scores.
In the last five years, proliferation of advanced threat techniques, together with serious monetary incentives for cyber criminals, have created highly successful infiltration rates. The success of cyber criminals has, in turn, created a sense of despair among users of defense technologies, with daily news reports revealing the extent of their exposure. The prevalence of high-profile attacks shifted the industry's state-of-mind toward detection and containment as the only realistic course of action and damage control, since breaches seem inevitable. Today's cybersecurity environment is comprised of fear, uncertainty, and doubt, with a low confidence in defense solutions.
Yet, in this depressing atmosphere, signs of change are evident. CISOs today typically understand the magnitude of potential attacks and the level of exposure, and they understand how to handle breaches when they take place. In addition, the accelerated pace of innovation in cybersecurity tools is making a difference. Topics such as software defined networking, moving target defense, and virtualization are becoming part of the cybersecurity professional's war chest.
Cybersecurity is cyclical, and the bar is again being optimistically raised in the direction of "prevention." Unfortunately, this time around, preventing cybercrime won't be as easy as it was in the last cycle when preventative tools worked with relative simplicity. This time, cybersecurity professionals will need to be prepared with a much more complex defense ecosystem that includes collaboration among targets, vendors and even governmental entities.





.png?width=571&height=160&name=iso27001-(2).png)