
Yet another critical Flash vulnerability was uncovered this month, thanks to researchers at FireEye. The vulnerability, CVE-2016-4117, exists in Flash 21.0.0.226 and earlier versions for Windows, Mac, Linux, and Chrome OS. It received a CVSS v3 rating of 9.8, indicating extremely critical (Adobe rushed out a patch earlier this week).
Attackers embedded the exploit in a Microsoft Office document, which they hosted on a DDNS server. When the target opens the document, for example via a phishing email attachment or a malicious URL, the exploit is triggered and the payload downloaded. In a clever twist, an innocent decoy document is then displayed.
The payload executes malware which connects to a second C2 (command and control) server, effectively giving the attacker control of the target’s system. The zero day discovered by FireEye specifically targeted newer Flash versions by including an abort feature if it detected a version older than 21.0.0.196.
Trend Micro points out that this vulnerability shares many similarities with the Flash CVE-2015-7645 vulnerability used in 2015 by Pawn Storm. Both are type confusion risk vulnerabilities with similar disassembled code. This suggests that the same vulnerable code may have been reused elsewhere, resulting in additional, as yet unknown, vulnerabilities.
Of course Morphisec users have nothing to worry about. Morphisec blocks the exploit immediately upon opening the Microsoft document; it never even connects with the remote server. Morphisec Chief Investigator Michael Gorelik shows how it works in this attack video:
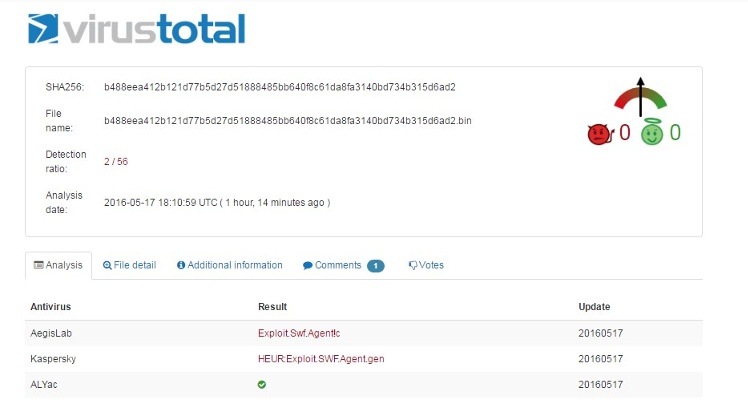
Credit goes to @PhysicalDrive0 for informing us of the new sample we demonstrate in the video. According to VirusTotal only 2 solutions identified it during the first 2 hours:





.png?width=571&height=160&name=iso27001-(2).png)