
After our recent blog post about an encrypted Flash exploit, we went back to analyze some more of these exploit files. We took some of the newer exploit recordings available on a malware aggregation site, and tried to decrypt them using the same Diffie-Hellman protocol that had worked for us before. We discovered that enough time had gone by that the Nuclear Exploit Kit team had already upped their game, and the brute force decryption did not work anymore. So what’s a researcher to do?
We went off in search of new exploit files that we could find in the wild. We started with some of the known compromised sites, to see the latest malicious files the hackers are churning out. Sure enough, some of them were still compromised. But the Exploit Kit URL had been modified together with its pattern. In fact, lots of parameters had changed.
In order to bypass most security solutions, we observed that Nuclear Exploit Kit randomly polymorphs the delivered malicious files throughout the day; the URLs and URL patterns are continuously changed; the kit’s host server, which holds the encryption key, changes; and the encryption changes for each access, that is, the exploit is delivered only once to a single IP.
These are all obfuscation attempts, to ensure that endpoint protection solutions will not be able to stop the exploits. Hackers move at warp speed to overcome most defenses enterprises can throw in their way. By concealing their tracks so thoroughly through this constant dance of new code, new servers, new exploits, they can bypass most:
- signature-type defenses
- “man in the middle” exploit hijacking
- behavior-based solutions
- brute-force decryption
And they make it extremely challenging to reproduce the attack, since they work just once and then disappear.
Why Should I Care?
The exploits we researched take advantage of a vulnerability that have been patched by Flash. But this doesn’t mean you can relax, since an Exploit Kit that generates new, sophisticated variants on the fly with a formula of “changing encryption + changing servers + changing files + changing whatever else” can leverage any type of zero day exploit. You should consider implementing a solution that is indifferent to these attempts to hide the exploit.
And now for some technical details…
The Technical Details
While searching for exploits on http://www.malware-traffic-analysis.net/ we wanted see if one of the malvertising sites is still active, but what we found was quite interesting:
- At least three of the many sites are still compromised (or have been re-compromised):
kristydebono.com & ima-hospital.com & egsrentacar.com, those sites have been previously compromised by Nuclear Exploit Kit (we chose to focus on Nuclear although few other sites also are still compromised after two weeks, they deliver the Rig Exploit Kit with a less sophisticated delivery method).
- The analyzed sites have been totally synchronized in terms of traffic redirection although their site compromization techniques were a bit different– all of them redirected to the same malicious site hxxp://dfsgahfhgdhjfgyrdjyhhbd[.]ml (the host of the Nuclear EK).
- Every hour the compromised sites modified the redirection to a new Nuclear Exploit Kit host with a new URL and new pattern –dfsgahfhgdhjfgyrdjyhhbd[.]ml, ertatsvd[.]ga, ertatsvd[.]tk, fckgdfahdtsfasrdvkjsmxxz[.]ga, erghghfsdjhkajsjdmashdj[.]ga, etc…
- A client that visited any of the compromised sites cannot be infected again during this hour even if the attack was prevented (The Exploit Kit host server traces IPs during the hour and will not deliver the same exploit to the same IP address twice – this makes Man in the Middle defense nearly impossible since you need to update rules each time). This is done to prevent security researchers from replaying the attack and reverse engineering it.
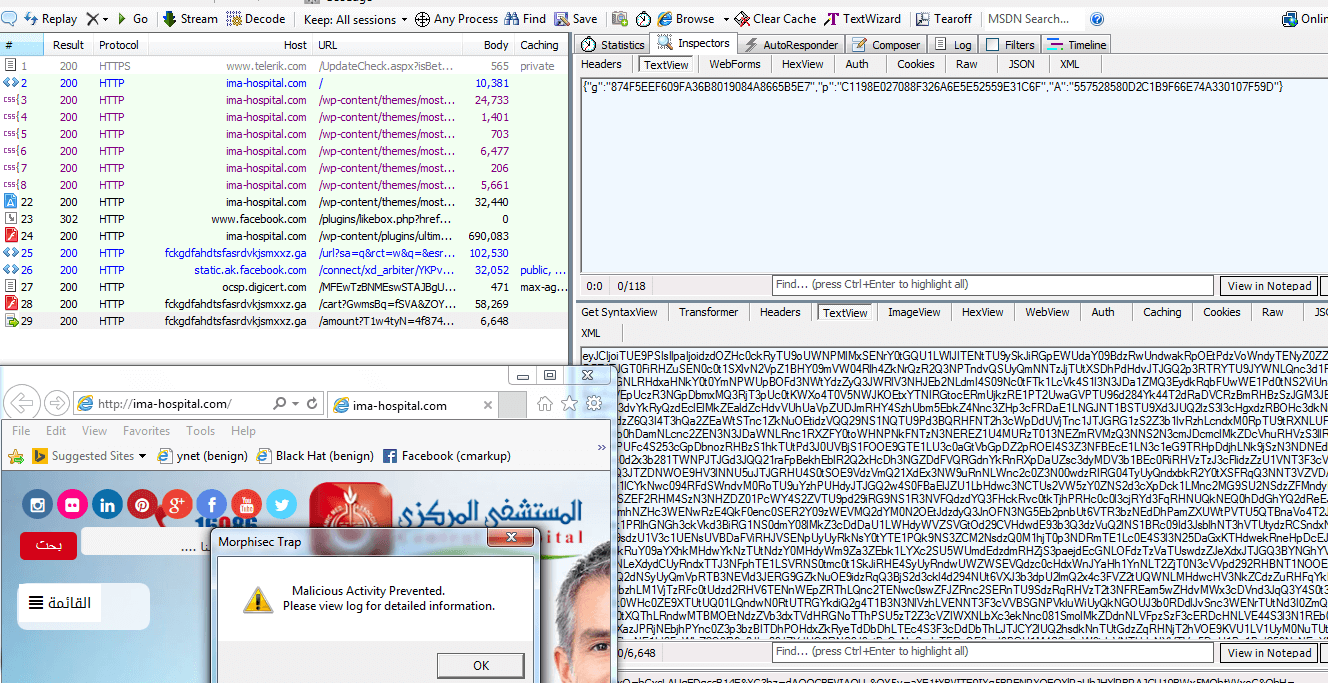
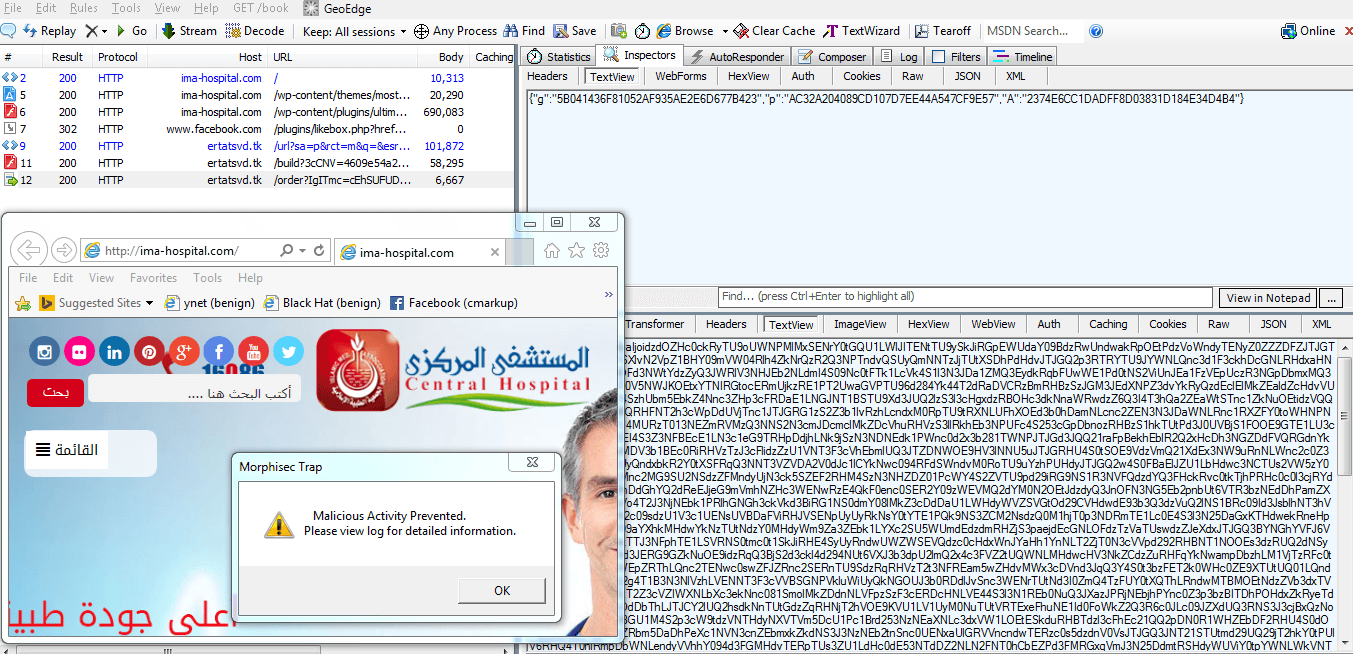
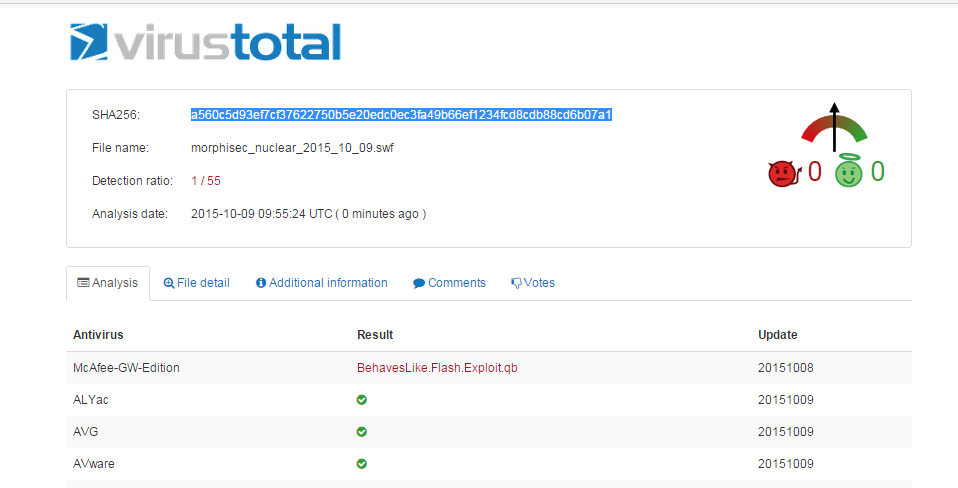
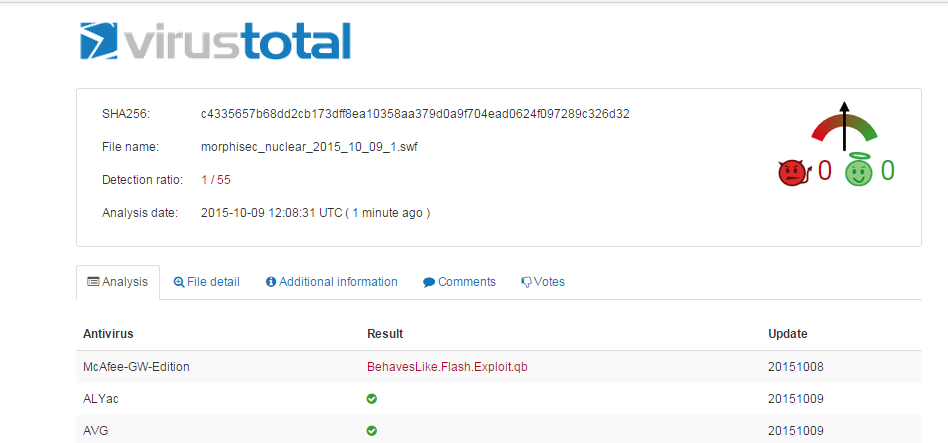
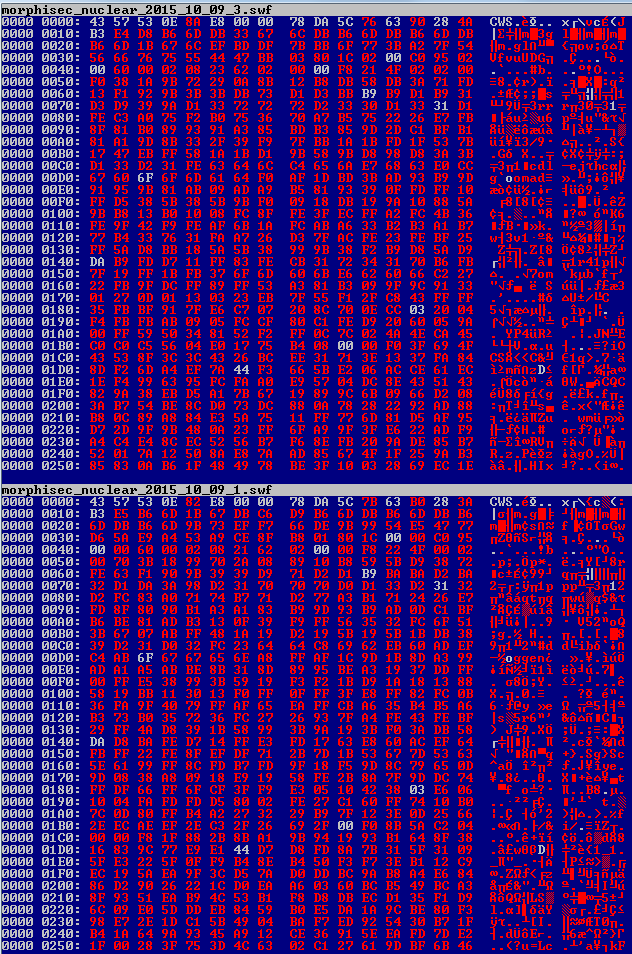
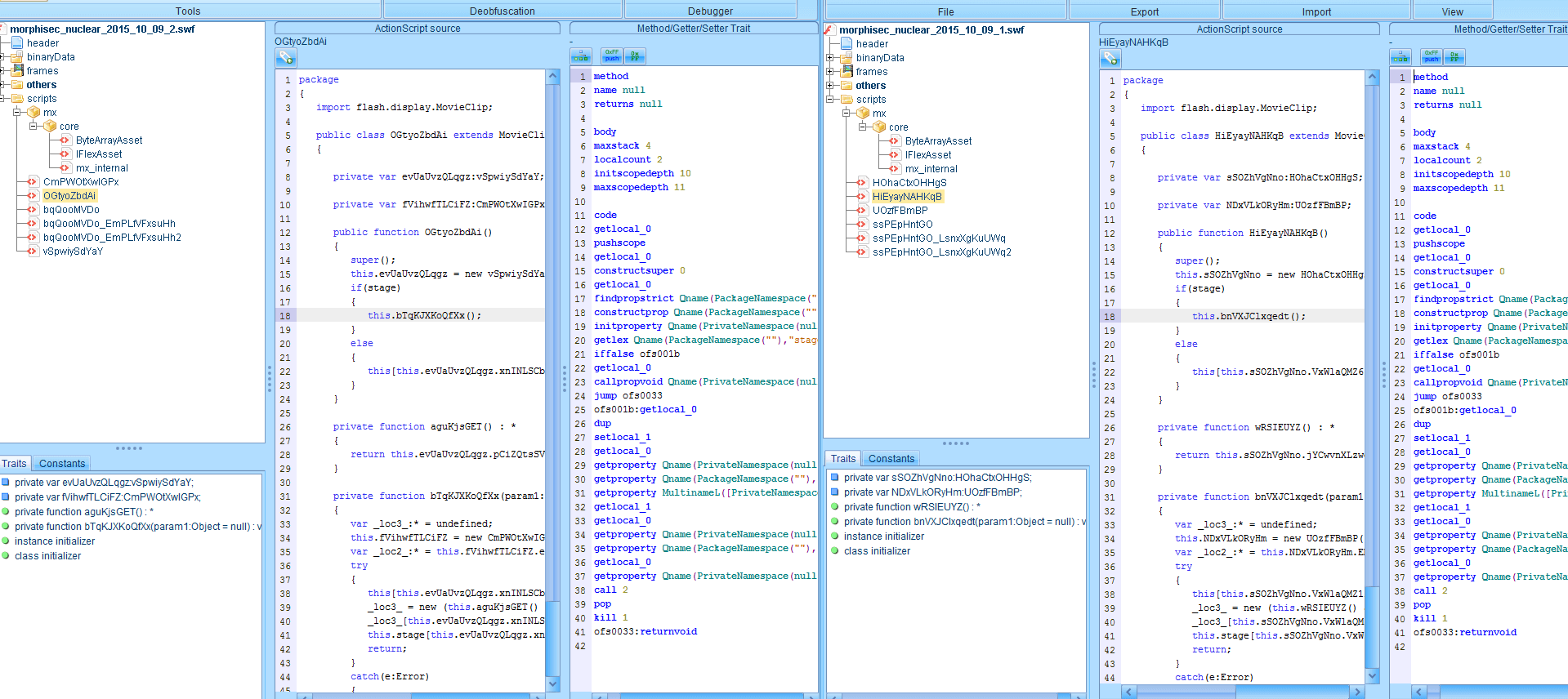
- Each of the Exploit Kit sites delivered a malicious flash file that was surprisingly varied in its contents, even though it was the same size. The flash file is the object that allows the attacker to exploit the browser, and it appears that the Exploit Kit is automatically generating a new malicious file object every time. After uploading several samples of the flash files to VirusTotal, checking our debug logs (Morphisec prevented the attack – see screenshot below), computing hex diff and decompiling them, the exploits are basically the same with variable and function name permutation. This led us to the conclusion that Nuclear Exploit Kit generates new exploits on the fly to bypass any signature or hash based solution, and it does it very successfully.
- Additionally, the Deffie-Hellman algorithm that we spoke about earlier becomes much harder to break (Exploit kit developers improved their encryption with very large prime numbers that are hard to factorize). Therefore it becomes even harder and sometimes impossible for companies to extract the exploit from the malicious file, and they left with a MITM solution (Which is limited due to 3 & 4).
Conclusion
Exploit Kit developers are still several steps ahead of traditional security companies where attacks can go unnoticed for an ever longer period of time. These findings show, for the first time, an Exploit Kit that automatically generates the exploit code on the fly. On every infection attempt, the Exploit Kit creates a new form of attack in a non-deterministic and polymorphic way. This rising level of sophistication poses a serious threat and barrier even for some next generation security products that rely on historical knowledge about attack behavioral patterns. Only attack-agnostic solutions such as Morphisec can cope with this new threat.
Some Screen Shots
NUCLEAR EK TIME X+1
Some malicious files that have been recorded during the campaign:
- swf SHA256: c4335657b68dd2cb173dff8ea10358aa379d0a9f704ead0624f097289c326d32
- swf SHA256: a560c5d93ef7cf37622750b5e20edc0ec3fa49b66ef1234fcd8cdb88cd6b07a1
- swf SHA256: 318adf498c0370d485880fabf0751bcc87d12cd02d93a74c407c7a781796e442
- swf SHA256: 1635fe87e11032f3838a911af42a3368e0bd7c2062cac5b2aa17e8fc8f1ee2f6
Some VirusTotal snapshots – known one actually recognizes it as Exploit
Hex Diff for the swf delivered within 1 hour difference by the same Nuclear EK:
Decompiled Diff for the swf delivered one hour later by the same Nuclear EK:
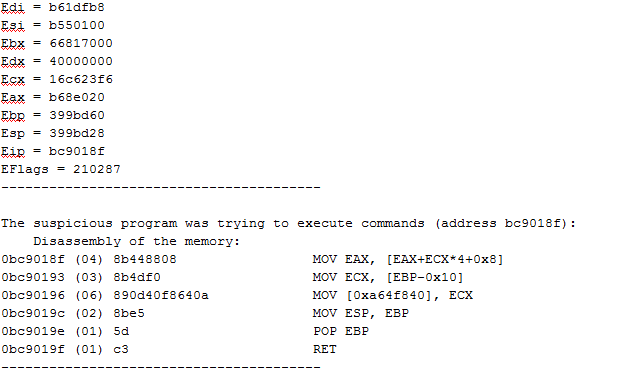
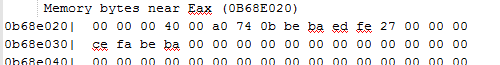
Morphisec Dump records identify the exploit and the vector corruption (without having the exploit decrypted):
The corrupted vector (size 4GB):




.png?width=571&height=160&name=iso27001-(2).png)