
The Fallout Exploit Kit, named for its similarities to the once notorious Nuclear exploit kit, already shows signs of reaching the levels of popularity of its namesake. Since its discovery by security researchers at the end of August, Fallout has been seen distributing the SmokeLoader trojan, GandCrab ransomware, CoalaBot, various potentially unwanted programs (PUPs) and, most recently, a new ransomware strain called SAVEfiles.
The rapid rise in Fallout activity is indicative of the resurgence of exploit kits in general. While attacks are nowhere near their 2016 peaks, they are making a minor comeback, mainly thanks to the spate of new Flash, Acrobat and Internet Explorer zero-day vulnerabilities.
How it Works
Currently, Fallout is being delivered through malvertising campaigns targeting the Asia Pacific region, the Middle East and Southern Europe. Fallout checks the user browser profile to target specific victims. If a match, it redirects the user from a genuine advertiser landing page to the exploit kit URL. The exploit kit leverages two different vulnerabilities, Adobe Flash Player vulnerability CVE-2018-4878 and the VBScript flaw CVE-2018-8174. If the user’s system is patched for these flaws, or if the OS profile is incompatible with the exploits (e.g., Mac OS), then the user is rerouted to other social engineering attempts such as a fake Flash or antivirus update.
The attack first attempts to exploit the VBScript vulnerability. If that fails, it exploits the Flash Use-After-Free vulnerability. Upon successful exploitation, Fallout uses a number of techniques to evade detection. Ultimately it could download any payload the attacker wants.
The exploit kit’s most recently seen payload - SAVEfiles ransomware – encrypts all files with a .SAVEfiles extension. It also creates ransom notes in each folder with information and an email contact to get payment instructions.
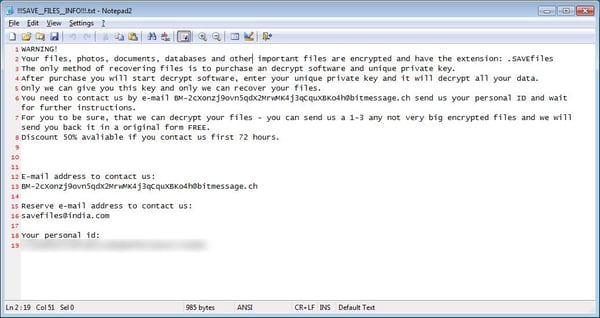
SAVEfiles Ransom Note (source: bleepingcomputer.com)
Evasive Techniques
From the onset, Fallout leverages various techniques to make analysis difficult and avoid detection by security solutions. The Fallout exploit kit landing page continuously changes URLs , which interferes with creating a good pattern recognition. This makes it harder for intrusion detection solutions that rely on pattern-detection to identify.
Protection Against Fallout and Other Exploit Kits
Currently, Fallout leverages vulnerabilities for which a patch is available so timely patching should be your first order of business. Fallout also contains a neat trick that redirects to social engineering methods, such as convincing you to download and execute a malicious fake Flash update, if the target is fully patched.
Fallout exploit kits are quick to adopt the latest zero-days. Updates may not always be available or feasible to install immediately. Morphisec prevents exploit kits across the entire attack chain, from the initial exploit to the payload. Patented Moving Target Defense acts as a “virtual patch,” preventing exploitation of application and OS vulnerabilities.
Resources
https://www.nao-sec.org/2018/09/hello-fallout-exploit-kit.html




.png?width=571&height=160&name=iso27001-(2).png)