During the first week of March, Morphisec intercepted and prevented an advanced Lokibot delivery campaign on some of its customers in the financial sector. While Lokibot has been lately reported to be delivered via impersonation of a known game launcher, previously it was also delivered through advanced AutoIt obfuscated Frenchy shellcode.
In the campaign Morphisec identified, the AutoIt+Frenchy shellcode is back and stronger than ever. We will dive deeper into the technical details while pointing out the innovative additions to the campaign.
LokiBot is a well-known info-stealer that scrapes information from different web browsers like Google Chrome, Firefox, Safari. It was previously also used to establish backdoors to an enterprise.
The shellcode was named “Frenchy” because of the mutex it creates and after a user named frenchy on hackforums. This shellcode has been seen with other packers loading different malware like Formbook, Netwire, AveMaria, Agent Tesla, etc.

Technical Details
The very initial stage of the delivery is through a spam/phishing email. In the figures below are the spam emails that deliver the Lokibot and AgentTesla info-stealer malware. Both are AutoIt executables that are archived with different archive extensions (for example: .cab and .zip; we saw rar and iso extensions as well), In both cases the executables contain a Frenchy shellcode loader that is responsible for reflectively injecting the next stage of the info-stealer payload. Below we will elaborate on the current loader and it’s previous versions.
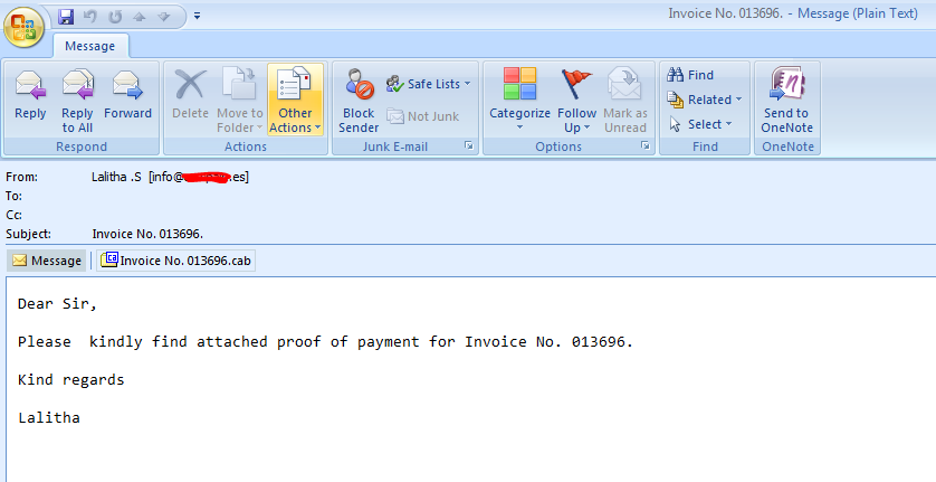
Figure 1: The original email delivering the Invoice executable through a cab file
-18.png)
Figure 2: Spam email with .zip file we recently noticed delivering Agent Tesla (from March 2020)
The executable had the name as ‘Invoice No. 013696.exe’, and we used Exe2Aut to successfully de-compile and extract the AutoIt script from the sample.
The user nicknamed Frenchy sells their shellcode framework underground for some of the known packer frameworks; below are just some of that snapshots that demonstrate a few of the details seen in almost every campaign executed and documented during the previous year
-12.png)
Figure 3: Obfuscated code showing the starting point of the script
-9.png)
Figure 4: Variables and functions renamed for easy understanding
As in previous rounds of the frenchy campaigns, the AutoIt script has its basic anti-vm evasion.
-13.png)
Figure 5: vm checks in one of the functions, pvleqyepzq
-1.png)
Figure 6: Sandbox check
-20.png)
Figure 7: Function that can download and execute the file from temp directory
It creates a visual basic script inside the user's profile directory, which is then used to install the actual malware, and a url shortcut to that vb script inside the startup directory to gain persistence.
.png)
Figure 8: VBS file created by script
-17.png)
Figure 9: Persistency shortcut
Comparison With Older AutoIt Packers Used In Other Versions of Frenchy Shellcode
Previously we have seen Frenchy shellcode used by different campaigns that were packed using both AutoIt and .Net. The first two versions came in packed with an AutoIt obfuscator and the third version was found packed with .Net. Researchers also found Frenchy shellcode version 5 (mutex_005) which was loading Lokibot, but the AutoIt script looked different from what we observed from our sample. In this section we will describe a few differences that we noticed in previous AutoIt obfuscators.
String Encryption, Shellcode and Payload Data Representation
AutoIt obfuscation used with Frenchy shellcode v001 has more functions when compared to the v002, v005, and the sample we analyzed. Some of the function names are the same in all versions, which could be due to the same technique/obfuscator used to obfuscate function and variable names, but the functionality is not similar. The string encryption technique used in the version we analyzed slightly resembled the initial packers, while the obfuscation from frenchy shellcode v005 implements a string shifting technique.
In Figure 11 below we can see that different packer versions use various techniques, like string reversing, string replacing, string shifting, doing XOR with arguments, and binary to string of hex values.
-6.png)
Figure 10: The string decryption function in different AutoIt versions
The shellcode and payload data in the sample we analyzed, and in packer with frenchy shellcode version v005 was split and concatenated as a hexadecimal string inside runPE and the main function. But in the earlier versions it was attached into the AutoIt executables as resources. Packers had the readresources and globaldata functions to load the encrypted resources by name and type.
-16.png)
Figure 11: Payload data collected from resources
-11.png)
Figure 12: Function that loads the resources and concatenates the payload
-5.png)
Figure 13: Payload split and concatenated from string
The shellcode is split and distributed within the AutoIt code, in both the packer with Frenchy shellcode v005 and in our sample.
-15.png)
Figure 14: Scattered shellcode in packer with frenchy shellcode v005
-10%20(1).png?width=1600&height=467&name=Lokibot%20with%20Frenchy%20Shellcode(in_progress)-10%20(1).png)
Figure 15: Shellcode collected into a variable (from our sample)
WinAPI Functions are back
The AutoIt packer used with frenchy shellcode v001 and v002 have the winapi functions used as public and internal functions, and was removed in frenchy shellcode v005. But the script we analyzed has these winapi functions again, which shows that the malware authors could be switching between old and new ways and using modified versions of old obfuscators to pack and load the shellcode and final payload.
No More UAC Bypass
The User Access Control (UAC) bypass techniques, using event viewer (for windows 7 and 8) and fodhelper (for windows 10) which were present in the older version of AutoIt packers that distributed formbook and tesla malware are now removed for this Lokibot version. The shellcode from the Lokibot sample analyzed by researchers at Fortinet in November 2019 had both UAC bypass techniques in it. It was not present in packers that came with frenchy shellcode v001 or 002 but it was a newer version and still had the UAC bypass techniques.
Process Injection and Hollowing
We noticed that older versions had the list of other legitimate process names inside the runPE function used for process injection and hollowing, but the version we analyzed had it set to @ScriptFullPath and did not have any other process names.
-19.png)
Figure 16: Process names for injection and hollowing (from version 005)
-8.png)
Figure 17: runPE function uses the same process for hollowing
No quickassist.bat File
One of the older versions of the AutoIt obfuscators used a .bat file (quickassist.bat) alongside the vbs file in its startup function.
-14.png)
Figure 18: BdvSOLRjPN (vbs file), and quickassist.bat file
at startup in one of the older versions of AutoIt
Shellcode Differences
In this section we will only present minor differences that we noticed in shellcode versions, because the actual functionality of the shellcode is still the same as older versions. Other researchers have already presented the shellcode’s functionality.
Initial frenchy shellcode versions had the tag with version number inside, but it was removed in later versions. Figure 15 below shows the CreateMutexW function used in version 001-005.
-7.png)
Figure 19: CreateMutexW function
Frenchy_shellcode_001 validates for IsWow64Process before mapping the DLLs from KnownDlls or KnownDlls32, which was later optimized to avoid using kernel32 overall. The DLLs mapped are advapi32.dll, user32.dll, ole32.dll, ntdll.dll, and kerne32.dll which are the same as in older versions. The API functions used to map these DLLs are NtOpenSection and NtMapViewOfSection. See below for the process validation.
-4.png)
Figure 20: IsWow64Process validation
The shellcode gets the address of GetProcAddress and LoadLibrary to load other DLLs and make required API calls.
Conclusion
It looks like Frenchy has gained popularity among malware-as-a-service providers and is being successfully utilized to deliver many info stealers without significant modifications in the code. This unfortunately magnifies the inability of detection solutions to handle memory evasive malware techniques.
Morphisec Automated Moving Target Defense protects against Frenchy and other memory evasive malwares without any dependency on malware version.
IOCs:
Samples:
AutoIT compiled executable with frenchy shellcode and lokibot (our sample)
Invoice_No._013696.cab
857BC421B19A4A2D7EFEF95B377640821041A06E
Other AutoIT executables with frenchy shellcode and different malware family payloads embedded inside:
DF9EE6A47AAD3BAD15C980C469A1857745B2D94E
3A7FBE4C15BA812B5BAB2B9F1D9A5DC247668E77
7A7F7E857121542EC8C2437690A01E3F824EEED2
45007E1BC83848F4EB4826EA4505BC70A20B4632
Extracted Shellcodes:
773E69F513A6E900112AC03498545EDAC04AE664
5F07A9E03A9086C89D29476FA39B47E3C4CB908D
56082B2C75ED7FD75BC6D39F3D9804EB1A156133
3165972381CF8393BA999B35C669E253924DB9F1




.png?width=571&height=160&name=iso27001-(2).png)