Today’s cyber security solutions aren’t countering threat actors’ advanced attacks. In the wake of the SolarWinds breach, even the largest companies and most-secure public agencies have had serious vulnerabilities exposed. If existing solutions worked, ransomware breaches wouldn’t be happening and inflicting so much financial devastation, brand erosion, and loss of business. In this environment, disruptive innovation is needed to improve cybersecurity, like Automated Moving Target Defense (AMTD).
Tech research firm Gartner cited Moving Target Defense as "The Future of Cyber" for improving security across memory, network, applications, and operating systems. This is because Moving Target Defense is proven to stop ransomware and other advanced zero day attacks, making prevention-first security a reality.
But let’s back up. Investment in cybersecurity is projected to grow to $316 billion by 2025. But damage from cyber attacks is rising exponentially faster, projected to reach over $10 trillion by 2025. Infosecurity Magazine reports the average ransomware payment in 2021 was a record $570,000, compared to $312,000 in 2020—which was 171% higher than 2019.
Traditional solutions such as next generation antivirus (NGAV), endpoint protection platforms (EPP), and endpoint detection and response (EDR) solutions do stop known attacks with recognized signatures and behavioral patterns. But they don’t prevent the advanced attacks that have been the hardest hitting ones on organizations today. Continuing with the status quo in cybersecurity will only make this situation worse.
Why? Because even traditional solutions aided by AI, machine learning, or anomaly detection need prior exposure to attacks to ‘learn’ how to stop subsequent threats. Signature and behavior-based defenses are great at thwarting known attacks. But they are essentially blind against advanced persistent threats such as zero-day, fileless, custom packed malware, in-memory whitelist bypassing, and runtime attacks.
Power Up Traditional Cybersecurity Solutions
This means currently trusted technologies miss many attacks—including the most damaging, such as the Log4J exploit, which initially attacked Minecraft. When these attacks aren’t detected or prevented, a security team can only respond after the damage has begun. Cybersecurity based solely on these solutions exposes firms to major compliance fines, lawsuits, and brand damage.
That said, known attacks must also be stopped. So signature-based and similar defenses are still indispensable for any security strategy. NGAV, EPP, and EDR are important tools in striving to achieve a zero trust architecture (ZTA) framework (explained below). However, with attacks now more nimble and novel, these tools are no longer enough. Where they end is where a ZTA strategy based on Moving Target Defense begins.
So what is ZTA? In August 2020 the National Institute of Standards and Technology (NIST) released a framework called Zero Trust Architecture (ZTA) (800-207). This document recommends a zero trust approach for endpoints to ensure a mature cybersecurity posture. Within a ZTA framework, nothing has trust status. Instead, everything must undergo verification and authorization, early and repeatedly. Moving Target Defense helps security teams to adopt ZTA and embrace the changes needed to stop advanced attacks.
Plug the Gap With Deception
The majority of security teams have significant resource and time constraints. So they’re often unable to implement a complete ZTA framework. They usually focus on building strong and sizable defenses that are static by nature—a defensive ‘wall’ around vital endpoints. This approach no longer works.
Why? A familiar, unchanging attack surface makes it easy for bad actors to find, reach, and compromise their intended targets. Threats that bypass existing defenses such as NGAV, EPP, and EDR solutions put huge pressure on IT security teams. And they result in significant financial damage. If it feels like cybersecurity is always playing catch up, that’s the result of using ‘dug-in’ defenses that are ineffective against the most evasive attacks.
But what if you could create an agile attack surface, like a fighter that is able to bob and weave? That’s the philosophy behind Moving Target Defense. It’s also the goal of ZTA cybersecurity, which is becoming the dominant paradigm for digital defense.
What is Moving Target Defense?
Moving Target Defense is a prevention-first approach to cyber attacks that operates from the insight that a moving target is harder to hit than a stationary one. It constantly shifts and hides entry points from criminals to deny them access, complementing reactive fortifications such as signature-based antivirus defenses. In addition, it sets traps to capture threat actors’ movements to further secure against future attacks. A more formal definition is as follows:
“Moving Target Defense prevents unknown and zero-day attacks by using system polymorphism to hide application, operating system and other critical asset targets from adversaries in an unpredictable manner, leading to a dramatically reduced attack surface and lower security operational costs.” [Morphisec]
Consider the following analogy for how Moving Target Defense works. Every bank has locks on the doors (next generation antivirus) to keep crooks out. And maybe video cameras (endpoint protection or endpoint detection and response) to warn perpetrators and record illicit activity if criminals penetrate defenses.
Most attacks follow a prescribed route to reach their intended target. But if entry points in that route are kept in motion, they’re unpredictable and unknown. So when attackers can’t find what they expect—a door or window into an organization—they fail. Given the extra effort and cost of perpetuating these attacks, most attackers move on to other, easier targets.
Moving Target Defense hides vulnerabilities and weaknesses from threat actors without disrupting current NGAV, EPP, or EDR functionality. It ensures zero-day, ransomware, and other advanced attacks are stopped before they can do damage.
MTD can be applied at the network, host, and application levels. All three types have value, but the application level is most important. This is because applications, operating systems, and endpoint resources are the most popular attack entry points.
Stopping attacks at the application level means even if they succeed at prior levels, they still ultimately fail. It’s the last line of defense before an attack becomes an incident. MTD stops attacks before malware deploys. And it does so without straining device resources, requiring intervention from human analysts, or even necessitating a strong internet connection.
The concept of Moving Target Defense is simple, but its impact is profound: cybersecurity no longer stands still. Instead, it outruns and outsmarts attackers. When defenses stay on the move, they stay a step ahead of attacks. Against MTD, the attackers, not the defenders, are at a disadvantage.
For a real world example, the three steps of Morphisec’s MTD include:
- Morph and Conceal: As an application loads to the memory space, Morphisec safely changes the process structures. This makes the memory constantly unpredictable to attackers.
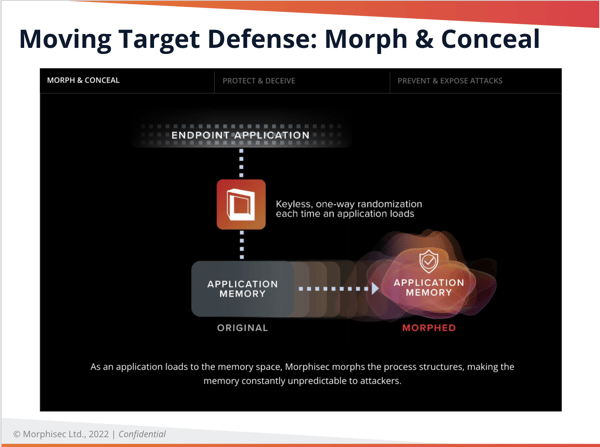
- Protect and Deceive: Legitimate application code memory is dynamically updated to use the morphed resources. Applications load and run as usual. A skeleton of the original structure is left as a trap.
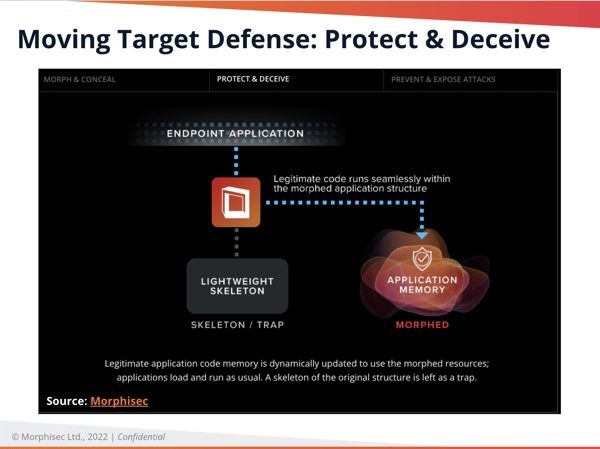
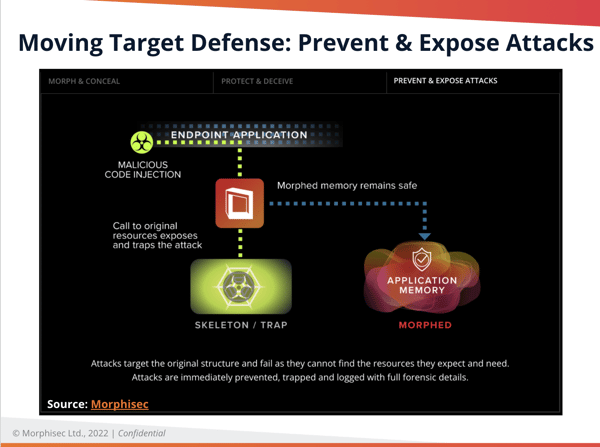
- Prevent and Expose Attacks: Attacks target the original structure but can’t find the resources they expect and need. Attacks are immediately prevented, trapped, and logged with full forensic details.
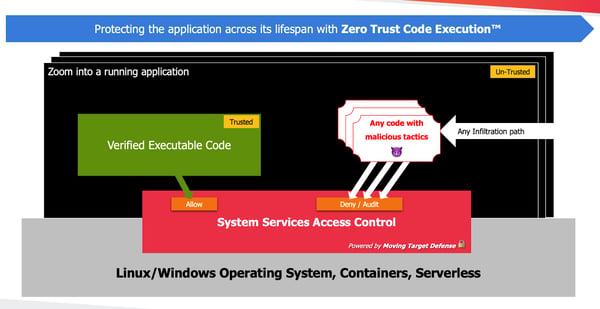
What is Zero Trust Architecture?
Traditional cyber security is based around the idea of a defensive perimeter that admits access to anyone with authorization. It then ‘trusts’ everything happening inside the perimeter to have broad privileges.
Unfortunately, attackers are skilled at obtaining credentials to sneak through perimeters. Once inside, they weaponize their trusted status to move around at will without triggering alerts.
In a ZTA framework, nothing has trust status, including endpoints such as laptops and mobile devices. Instead, everything must undergo verification and authorization, early and repeatedly. Zero trust limits access as much as possible and verifies anything given access. When this approach is applied in all facets of cybersecurity, attacks must overcome repeated obstacles and evade constant scrutiny.
ZTA has evolved over the span of a decade from a hypothetical framework to become the centerpiece of cybersecurity. In May 2021, the Biden administration signed executive order 14028, instructing NIST to update mandates such as the ZTA framework. All federal agencies and those who do business with these agencies must comply.
Countless security teams are either embracing NIST ZTA for the first time, or pushing it to the forefront of their security strategy. All signs suggest ZTA will become even more of a cybersecurity standard.
The Anatomy of Evasive Attacks
A closer look at evasive attacks makes clear why ZTA and Moving Target Defense are mission-critical for cybersecurity. The past year has set records for zero-day exploits and ransomware attacks. With massive resources underpinning cyber crime, attackers are only getting better at dodging detection and prevention.
There are numerous ways attacks can hide malicious intent and cloak themselves in authenticity. The list is always expanding and evolving, but some key techniques include:
- Polymorphism – Changes malware signature
- Metamorphism – Changes malware code at execution
- Obfuscation – Obscures malicious activities
- Self-Encryption – Uses encryption to hide malicious code and data
- Anti-VM/Sandboxes – Changes behavior to evade forensic analysis
- Anti-Debugging – Switches tactics in forensic environments to break debugging
- Encrypted Exploits – Changes parameters and signatures to elude investigation
- Behavior Changes – Waits for use activity before executing
These evasive techniques have proven extremely effective, with attackers’ advantage expanding over time.
Zero trust acknowledges this reality. Any attempt to keep attacks at a distance from sensitive assets inevitably fails. So security must surround the assets themselves. ZTA MTD defends targets rather than entry points. This shrinks the attack surface and foils attacks that breach outer layers of security.
Endpoints: The New Front-lines of Cybersecurity
Endpoints in recent years have evolved from physical devices to various virtual equivalents. Popular examples include virtual desktop infrastructure (VDI), cloud workloads, and remote desktops, all of which have seen brisk adoption of late. They’ve become instrumental to the modern office. But they have also become a serious security liability in the process—one that attackers are acutely aware of.
- Attacks against remote desktop protocols (RDP) have more than tripled
- Attacks against cloud services have risen over 500 percent
- VDI usage has increased by 100 percent despite troubling security vulnerabilities
These examples of new endpoints have several commonalities. They aren’t easily or adequately secured by traditional methods of endpoint security. And they each rely on numerous trust relationships that expose them to exploitation for all the reasons outlined earlier.
From ransomware to zero day threats to social engineering schemes, endpoint attacks are increasingly common—and devastating. In one survey, nearly 70 percent of respondents had seen an increase in endpoint attacks and fallen victim to at least one.
The sudden shift to remote work has made many existing endpoint defenses insufficient or obsolete. It explains part of the surge in endpoint attacks. But the bigger explanation is the expansion of what constitutes an endpoint. This gives hackers a bigger target to strike at and new exploits to work with.
Moving Target Defense has an unparalleled ability to make ZTA endpoint security easy and effective. MTD focuses defenses on application memory, where most attacks seek to strike. And it foils those attacks without needing to detect them in advance or deflect their attack. It makes endpoints secure from unknown and evasive threats without an expansive security apparatus. ZTA based on MTD makes the final battle the hardest for attackers to win.
Moving Target Defense Is the Next Era of Cybersecurity
Evasive attackers are focused on endpoints. With new breaches capturing headlines, security teams must react and think differently to protect their organizations’ well-being.
The next era of cyber attacks has arrived. The next era of cybersecurity needs to respond. Best of breed cybersecurity today requires ZTA techniques with MTD technology. Security teams should focus on speed rather than strength; smarts instead of scale. Learn more about MTD ZTA in Morphisec’s white paper: Zero Trust + Moving Target Defense: Stopping Ransomware, Zero-Day, and Other Advanced Threats Where NGAV and EDR Are Failing.
Feature image courtesy Richard Patterson under an Attribution 2.0 Generic license.






.png?width=571&height=160&name=iso27001-(2).png)