In 2020, Morphisec introduced the Jupyter infostealer, a .NET attack that primarily targets Chromium, Firefox, and Chrome browser data while also maintaining the additional capabilities of a backdoor.
Since that time, Jupyter has remained active and highly evasive. It has continued to receive very low to zero detections in the VirusTotal database, maintaining the ability to bypass detection solutions.
Then, on 8 September 2021, we identified a new delivery chain within Jupyter that passes under the radar of security solutions. Following this discovery, the Morphisec Labs team has been made aware of multiple high-level targets that are under threat from the Jupyter infostealer. We are currently investigating the scope of the campaign.
The blog post that follows outlines the new delivery chain, showcasing how threat actors continue to develop their attacks to become more efficient and evasive.
Editor's Note: This blog post has been updated as per the request of Advanced Installer.
Technical Details
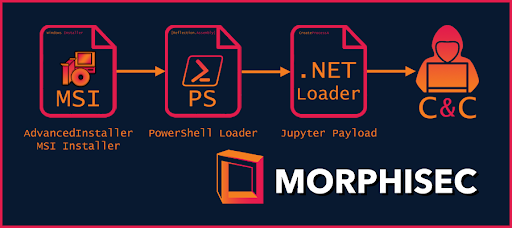
Figure 1: The attack flow of the new Jupyter infostealer
The MSI Payload
In this section, we will briefly examine some of the payload`s shared attributes in order to get an overview of what indicators to expect. This is based on the six variants that we have observed.
Payload Size and Name
Like previous Jupyter payloads, the size of the MSI payloads is consistently over 100MBs. This allows the payload to thwart online AV scanners.
The naming convention for the payload is:
- Potential document subjects
- Words are separated with a dash ‘-’
- Each word starts with a capital letter
Examples can be found in the IOCs section under the heading “MSI Payload Names.”
MSI Third-Party Installer Wizard
The payloads were generated with a trial version of Advanced Installer (version 18.6.1 build 2c9a75c6).
As described on their website, the Advanced Installer wizard is an ‘All-in-one’ application packaging tool. By using this tool, threat actors gain access to the easy implementation of obscured script executions.
Customizing installer PowerShell operations is a legitimate functionality that the attackers misuse, as with other attack chains. This same operation is frequently used as part of legitimate products or services. We advise against flagging any PowerShell scripts originating from Advanced Installer without prior evaluation of the command itself. It is worth noting as well that PowerShell functionalities are also available in other installers.
The attribution can be found either in the file properties (OLE Compound) or in the Installer property table.
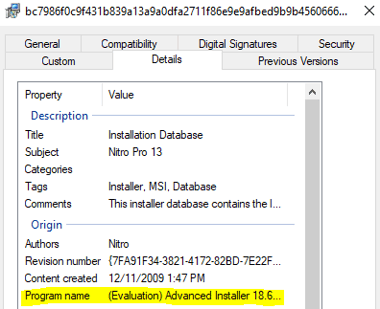
Figure 2: OLE Compound file information
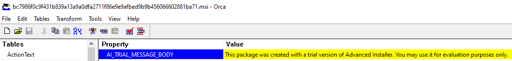
Figure 3: Property table
Decoy Installation Executable
As seen in Figure 1 above, all of the observed variants are described as Nitro Pro 13. Once the victim runs the MSI payload, it executes a legitimate installation binary of Nitro Pro 13. Correlating this attribution with the variant’s file names suggests that the delivery method disguises it as a PDF.

Figure 4: Nitro Pro 13 Installation
While all of the variants are described as Nitro, one of them actually contains SumatraPDF instead.
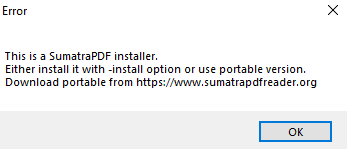
Figure 5: Sumatra PDF installation
Digital Signature
Two of the variants are signed with a (currently) valid certificate named ‘TACHOPARTS SP Z O O’.
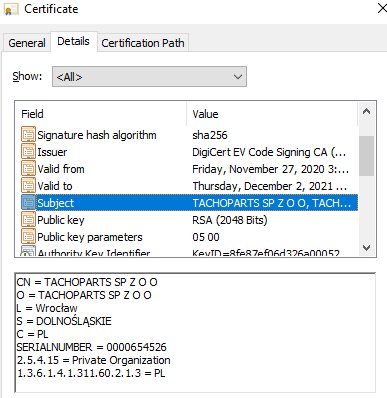
Figure 6: Tachoparts certificate
Based on the following certificate data, we can assume that the threat actor either impersonated the certificate or stole it from a legitimate business in Poland.
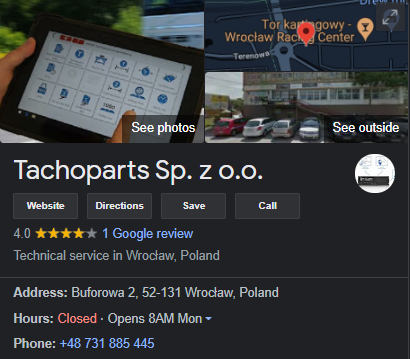
Figure 7: Tachoparts' business information from Google
Another variant was signed with a revoked certificate named ‘OOO Sistema’.
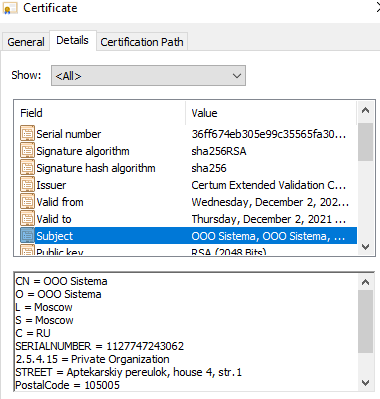
Figure 8: OOO Sistema certificate
As with the previous certificate, this one is also correlated with a legitimate business. It also was likely either an impersonation or stolen from the business.
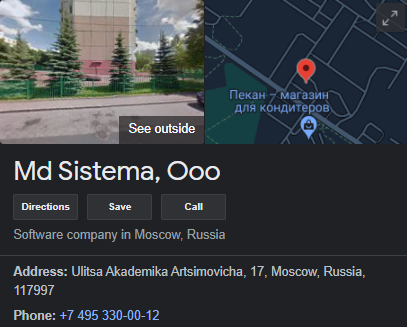
Figure 9: OOO Sistema business information from Google
The other 2 variants are signed with certificates named:
- FORMICA Solutions a.s.
- OOO Ruvents
The PowerShell Execution
The initial suspicious indicator visible in the dynamic analysis is the PowerShell command-line spawned by msiexec.exe.
Command Line
|
C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe -NoProfile -Noninteractive |
Code block 1: CMD Shell command-line
This command-line is generated by a feature in the Advanced Installer that is designed to execute the PowerShell loader as a ‘CustomAction’ attribute defined in MSI Installers.
The file names within the parameters differ between variants but keep the same pattern. For example in ‘scrEA14.ps1’, the EA14 is represented by four hex characters. These four characters are different between the payload variants.
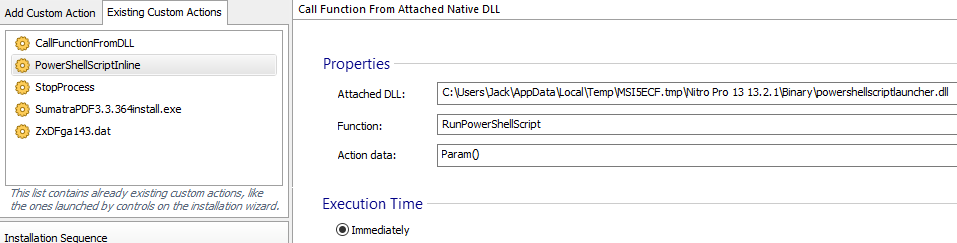
Figure 9: PowerShell loader embedded in the CustomAction within AdvancedInstaller
.png?width=653&name=unnamed%20(1).png) Figure 10: PowerShell loader embedded in the CustomAction within AdvancedInstaller
Figure 10: PowerShell loader embedded in the CustomAction within AdvancedInstaller
Jupyter PowerShell Loader
The PowerShell file in the -scriptFile parameter presented in Code block 1 represents the Jupyter PowerShell loader.
This loader is very similar to the previous Jupyter loaders in that it keeps a very evasive file with low to 0 detections on VirusTotal, which is rare for a full PowerShell loader (loader code with an embedded payload).
While the Jupyter loaders are widely covered in our and other blogs, the new variant shares the same code pattern. The following code block is an example of a deobfuscated and beautified version of it:
|
$b64_enc_payload = 'deducted'; |
Code block 2: Deobfuscated Jupyter PowerShell loader
Note that like the previous versions, this one also reflectively loads a DLL that initializes execution under the Deimos namespace in the Mars class (Mars.Deimos).
The .NET DLL Payload
In our previous blog, we attributed the payloads to their internal version. The following table correlates the observed internal version and the MSI payload’s first submission date and detections on VirusTotal.
| Jupyter DLL Internal Version | VirusTotal First Submission |
| SP-9 | 08 September 2021 1 / 57 Malicious detections |
| SP-10 | 08 September 2021 2 / 57 Malicious detections |
| SP-11 | 10 September 2021 0 / 57 Malicious detections |
| SP-13 | 13 September 2021 0 / 57 Malicious detections |
| SP-14 | 21 September 2021 0 / 57 Malicious detections |
| SP-16 | 21 September 2021 0 / 57 Malicious detections |
While all of the .NET DLL Payloads should be obfuscated, it appears that the SP-10 variant contains source-code strings. The following figure presents the payload methods and class names.
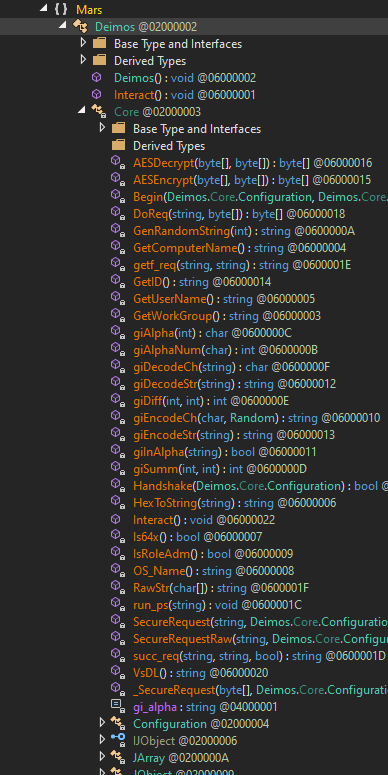
Figure 11: Jupyter .NET DLL Payload methods and classes
Conclusion
The evolution of the Jupyter info stealer/backdoor from when we first identified it in 2020 proves the truth of the statement that threat actors are always innovating. That this attack continues to have low or no detections on VirusTotal further indicates the facility with which threat actors evade detection-based solutions. It’s clear that a new approach is required to threat prevention, as it’s likely these evasive attacks will continue.
This is why Morphisec architected its solutions with Automated Moving Target Defense to emphasize deterministic prevention of evasive attacks instead of detection. Customers who leverage the Morphisec Preemptive Cyber Defense Platform on their endpoints, on-premises servers, and in the cloud can remain confident that they are secure from evasive threats such as the Jupyter infostealer, regardless of the detection rate in VirusTotal.
IOCs
MSI Payload Hashes
|
bc7986f0c9f431b839a13a9a0dfa2711f86e9e9afbed9b9b456066602881ba71 |
AdvancedInstaller PowerShell Hash
|
88748aae11029228d84aef0855f4bc084dfd70450db1f7029746d8bc85182f93 |
Jupyter PowerShell Loader Hashes
|
934cb210db692c3ebcd9ba8d113b1669573a20db79c02a2587a4bead10d8dfeb |
Jupyter Payloads
|
8bcf6506b21f67641fa753d7328d3c1045541f84bc62bbe43d485f38e3d5e3ae |
C2 IPs
|
45.42.201[.]248 |
MSI Payload Names
|
Metlife-Disability-Waiver-Of-Premium-Benefit-Rider.msi |





.png?width=571&height=160&name=iso27001-(2).png)