UPDATED POST - NOW WITH DETAILED TECHNICAL ANALYSIS!
During October 17 to 21, Morphisec identified and prevented several malicious and sophisticated macro-based documents at the site of one of our customers delivering a fileless Kovter backdoor Trojan attack. This and similar attacks illustrate the troubling trend that macro-based malspam campaigns are attacking enterprises with modified evasion techniques now on a weekly basis. With antivirus products updating their signatures within 3-7 days of the detection of an attack, the window of opportunity is big enough for cybercriminals to score.
The security stack of our customer is composed of Kaspersky AV, Malwarebytes (an anti-malware solution), and Morphisec Endpoint Threat Prevention solution. In this case, both Malwarebytes and Kaspersky were not able to identify the malicious documents, the payloads, or any other infection step during the attack chain even when tested on isolated computers without Morphisec. Only Morphisec prevented the attack on arrival, giving our customer the peace of mind he expected when augmenting his preferred AV solution with Morphisec.In many respects, this current malspam campaign demonstrated unique qualities: Better targeted emails (see screenshots below), modified macro with click-based execution, modified payloads, and persistency mechanism.
Kovter is notorious for its sophistication and for attacking in waves: It evolved from previously pretending to be a Firefox or Chrome update to being delivered through JavaScript inside Zip files in August 2016.
A description of a previous fileless Kovter backdoor variant can be found here: http://blog.airbuscybersecurity.com/post/2016/03/FILELESS-MALWARE-%E2%80%93-A-BEHAVIOURAL-ANALYSIS-OF-KOVTER-PERSISTENCE.
The following analysis describes the attack chain in full detail, starting from the emails and ending with the persistent Kovter backdoor. The full report is also available as PDF.
TECHNICAL ANALYSIS
1. Use of Targeted Emails
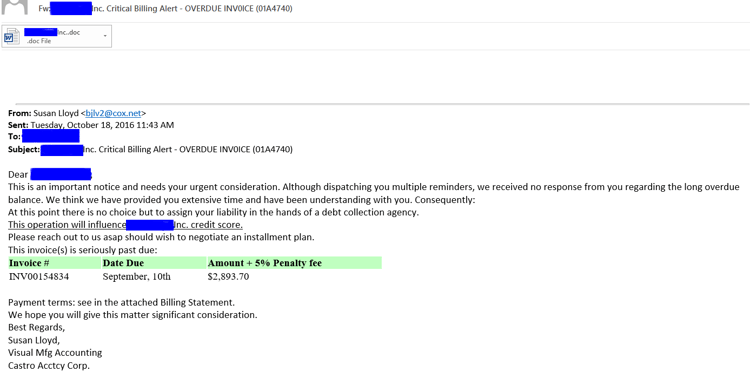
Monitoring the latest campaigns, we found the often used “invoice/bill” email pattern. The subject and content pretend to inform the recipient about a due invoice and that payment needs immediate attention. A sense of urgency is created by threatening the recipient with consequences in case this email is ignored.
The Kovter attack under discussion is of a more targeted nature: The attackers name the attached files with the company name, and on some of the mails they address the employee by his/her name and job title.
All the emails in this campaign originated from Cox email service users, as you can see by looking at the “from” field. [Cox allows to use its service in a 60-days free trial.]
Email Example 1
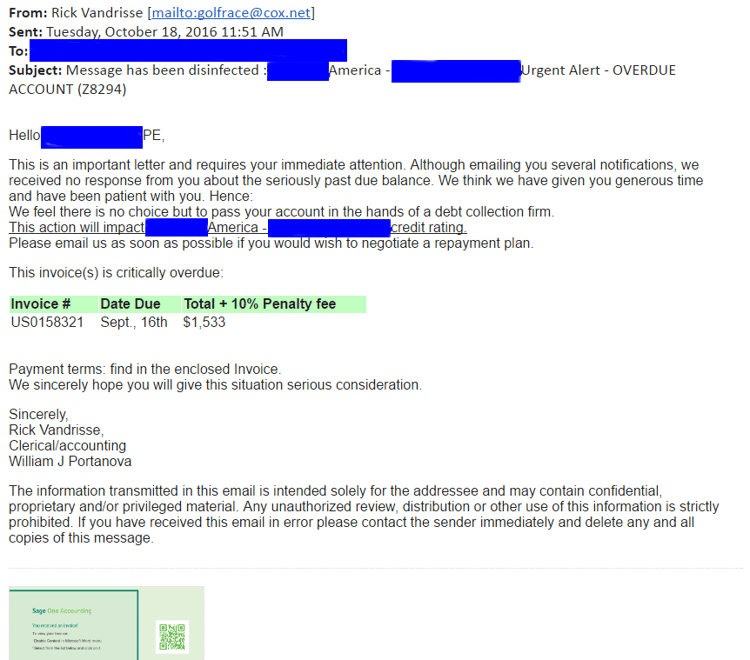
Email Example 1
2. Malicious Macro
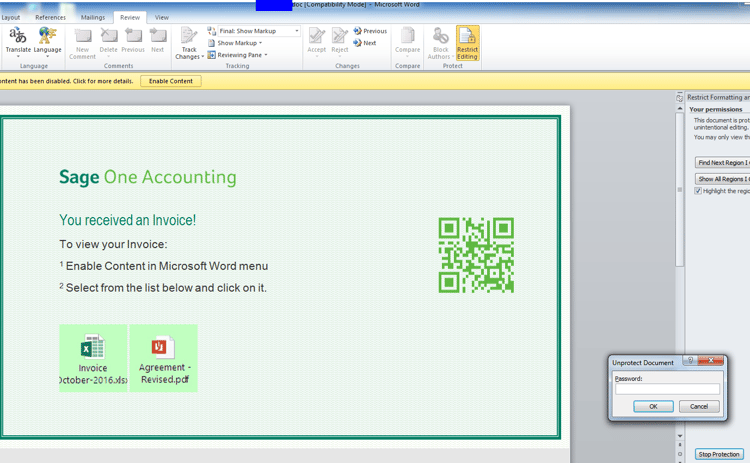
This time the macro has a slight modification in its delivery method. It is not enough to just enable the macro content.
The code is activated if the macro is enabled and the user clicks on one of the images in the macro: This way it can easily evade simple sandbox services which have simulated the enable macro content only.
To make detection even harder, the macro writers restricted the edit and view of the macro mapping to the different image clicks. Adding a restriction password on image edit also disables the sandbox to automatically map the macro procedures which will be activated.
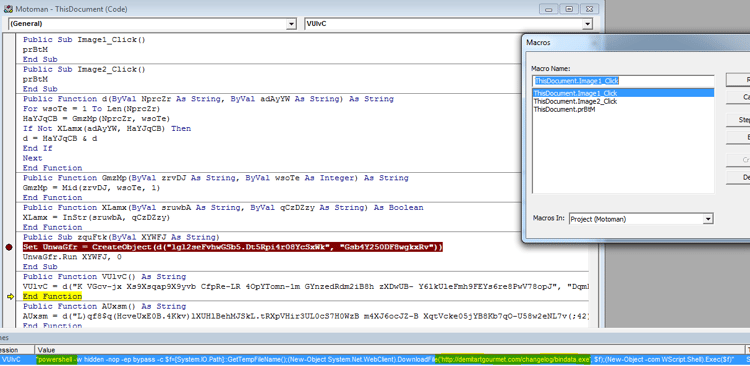
3. PowerShell - First Stage
The macro code activates a decrypted PowerShell code that downloads the Kovter downloader from hxxp://demitartgourmet[.]com/changelog/bindata[.]exe. Note that any image click will eventually result in the execution of the same PowerShell code.
4. Double Persistency through File-Less mshta Scripts
To gain persistency, Kovter trojan uses both the Run key in HKCU (*) and the “Start Menu/Programs/Start” path.
[* For a description of the use HKEY_CURRENT_USER…\Run see also https://blogs.technet.microsoft.com/mmpc/2016/07/22/kovter-becomes-almost-file-less-creates-a-new-file-type-and-gets-some-new-certificates/]
4.1. HKCU
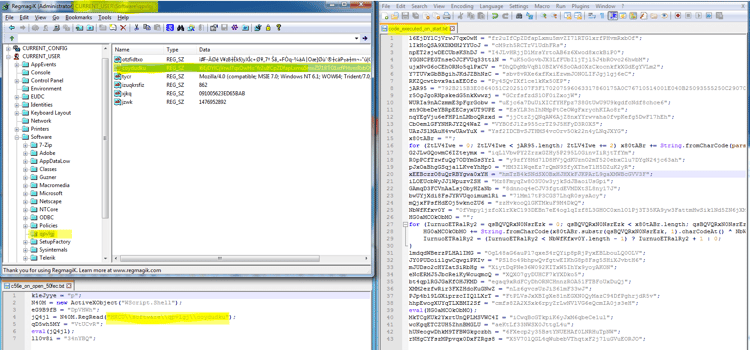
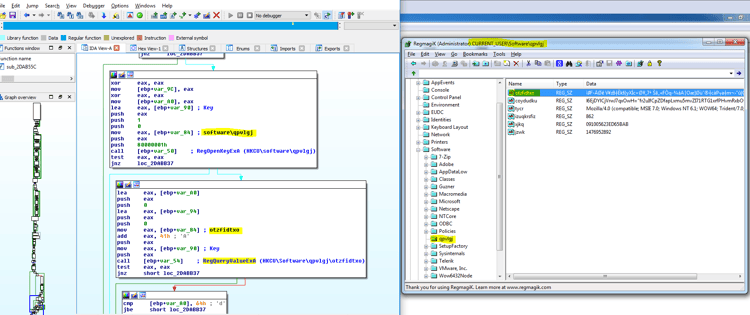
In the “HKCU\Software\Microsoft\Windows\CurrentVersion\Run” technique we can find two persistency methods which are both activated to reassure the execution of Kovter upon user login. We use RegmagiK to show you the persistent code in the registry because regular regedit.exe is not sufficient as a result of non-ASCII characters that the attackers inserted intentionally.
The first “mshta” procedure will activate a JavaScript eval () function that executes a registry parameter written in a different registry location [described further below].
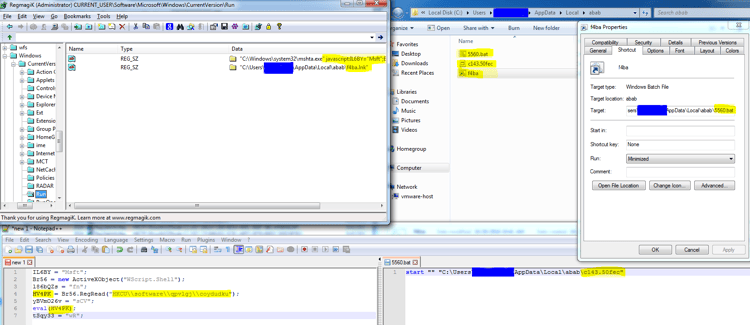
The second Run persistency method will activate a link file that is created in the local directory. This link file just activates a stub [filename].50fec (random name). The activation of the file is less interesting, but as it looks from the registry, Kovter has created an open command registry to trigger a code execution when the associated files are activated (c56e and 50fec), in this case again a mshta JavaScript code will be activated with the same code from the registry. [ For a detailed description see https://blogs.technet.microsoft.com/mmpc/2016/07/22/kovter-becomes-almost-file-less-creates-a-new-file-type-and-gets-some-new-certificates/ ]
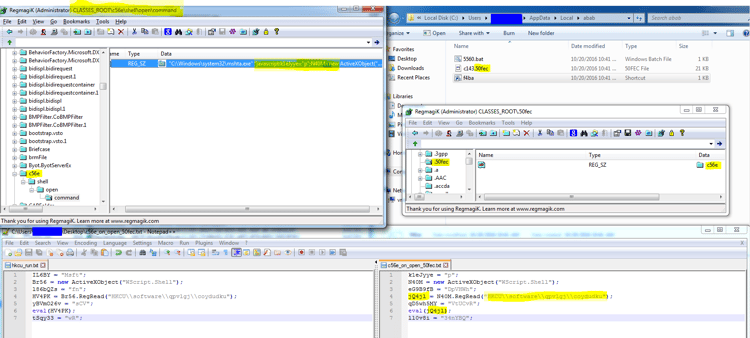
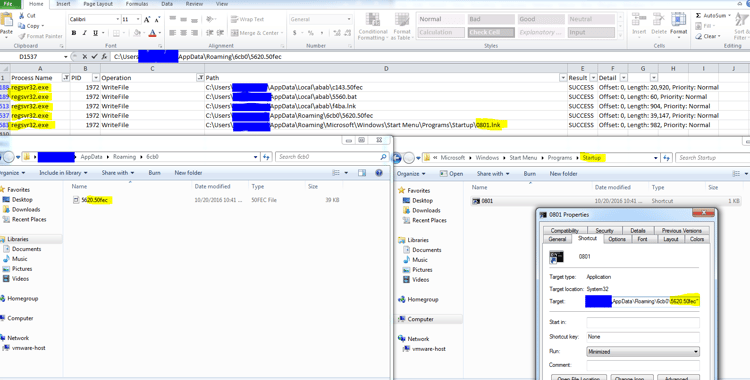
4.2. “Start Menu/Programs/Start” path
The second persistency mechanism - as can be seen from the process monitor - is the addition of a link file (.lnk) in the Startup directory. Upon login, this file is activated as well as a very similar stub file (*.50fec) and the same mshta script that is registered in the open command registry path will be activated as a trigger.
5. Mshta and PowerShell executed directly from registry
After observing the persistency steps, we are diving into the JavaScript code that is activated through the mshta (and is written in HKCU/Software/<RANDOM>/<random>). We notice that the JavaScript pattern is not very different from previous Kovter trojan patterns.
This JavaScript code eventually activates a PowerShell script. The PowerShell stage 1 script just writes to environment variable the second stage script and then activates it.
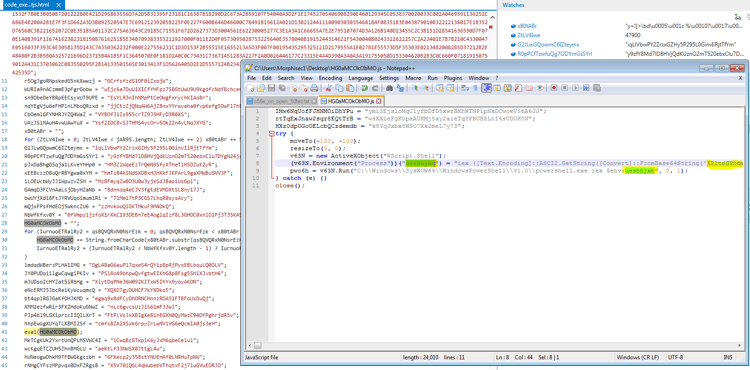
6. PowerShell - Second Stage
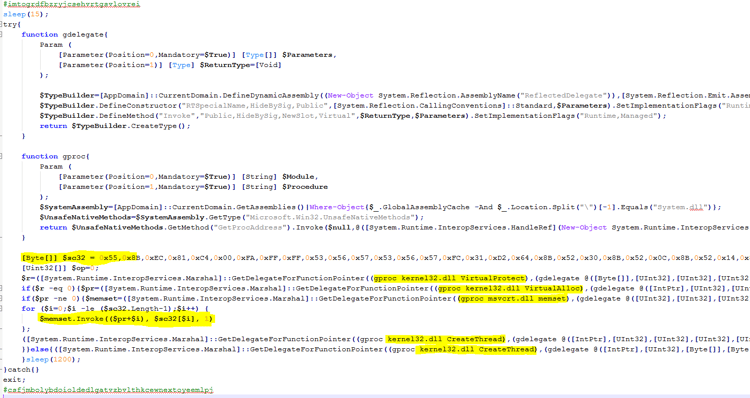
The second stage script (described previously here - https://blogs.technet.microsoft.com/mmpc/2016/07/22/kovter-becomes-almost-file-less-creates-a-new-file-type-and-gets-some-new-certificates/ ), has the main goal to stay in-memory. It creates a shellcode on the fly and injects it directly into the same PowerShell process (described further below).
We can notice the usual pattern of allocating code in the process, mem copying the code into the allocated space, and using the CreateThread function to execute the shellcode.
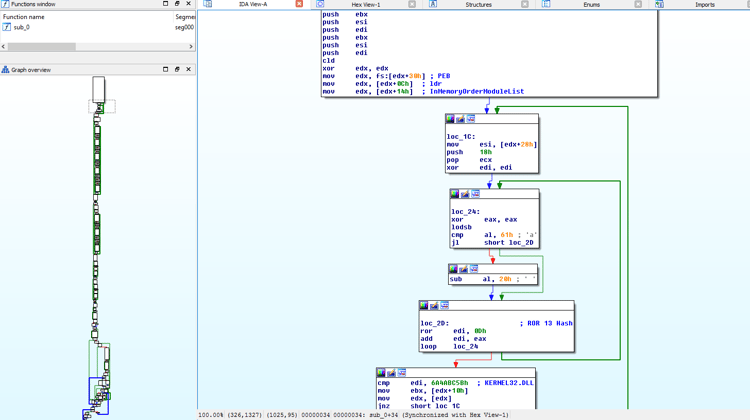
7. Shellcode
The first shellcode again will evade security solutions by staying in memory and getting its Kernel32 and Advapi32 functions from PEB.
- The shellcode will look for KERNEL32 by traversing the PEB and comparing the HASH name after applying ROR 13 hash function (popular pattern).
- The shellcode then looks in the export table for 4 functions (LoadLibraryA, GetProcAddress, VirtualAlloc, ExitProces. For faster execution, the shellcode compares the dwords instead of using regular byte compare.
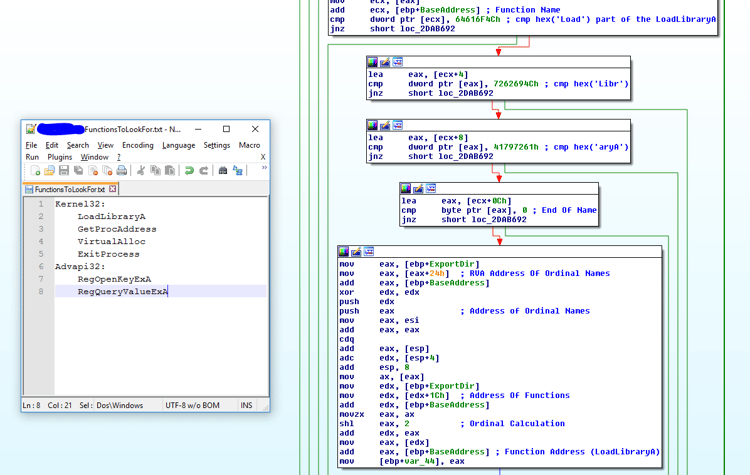
- After getting the KERNEL32 functions, it uses the LoadLibraryA and GetProcAddress to get the two advapi32 functions (RegOpenKeyExA and RegQueryValueExA). Those functions are used to read the Kovter shellcode from the registry, decrypting this shellcode, and using the VirtualAlloc to inject it again in the same PowerShell process.
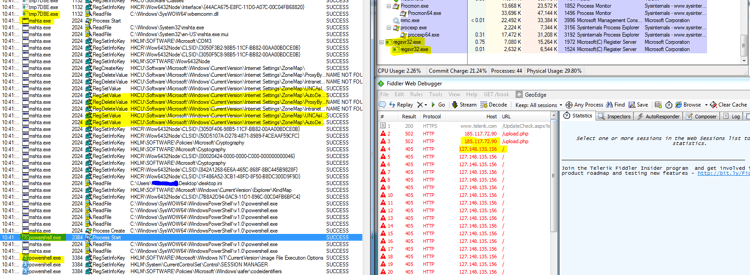
8. Communication with C&C and lowering the internet security settings
As was expected, Kovter (PowerShell stage) creates Regsrv32 processes, which communicate to many different IPs, sending computer, OS, and user encrypted information and waiting for the next command to execute. Notice that it modifies the security Zone settings by disabling UNCAsIntranet and AutoDetect keys in the Internet Settings\ZoneMap registry.
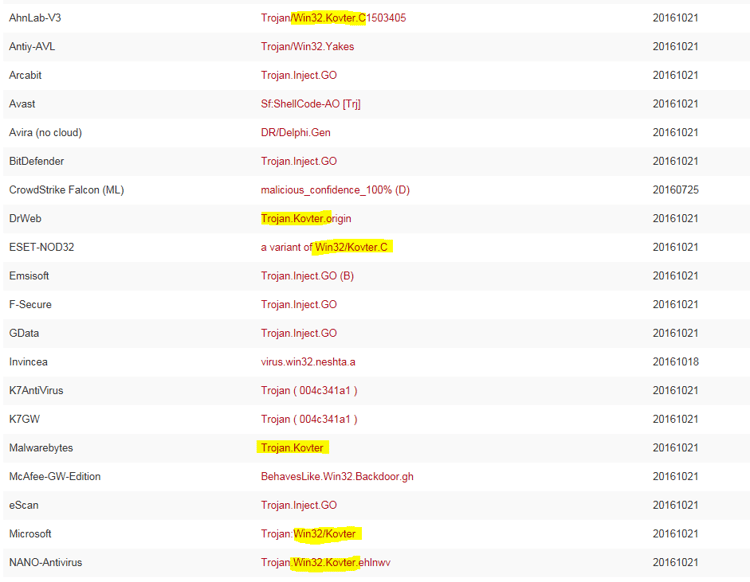
9. Detection on VirusTotal
After we wrote the decrypted Kovter code to the disk (the encrypted code resides in one of the registry keys), we uploaded it to VirusTotal. [ Note that Kovter will not write the executable it uses to the disk.]
The upload results in:
Sha256: 7178d1babda77e159936fe4e3841c7a3dad3b78a6737ba7dd9a1f3c370f6dc34
We see immediately that most of the AV solutions do recognize the Kovter signatures when written to disk.
10. How to clean this malware and be safe
- Kill the regsrv32 processes. We recommend using “Process Hacker” and run it as admin.
- Remove the persistency by deleting all the Registry described variables. Besides the RUN key, take into account that you will have different random names.
- Clean the RUN key [We would recommend to simply delete it. This will recreate the RUN key as new clean key automatically. You can also use RegmagiK or native tools to edit the registry without removing the legit values. Note: Take into consideration that previous default settings of yours will get lost if you delete the RUN key.]
- Remove all the *.lnk and bat files as described in this report. Take into account that those will be generated with different names on your machine.]
- Since Kovter modifies your Internet security settings, please use tools to fix your registry.
- To be safe, we recommend adding Morphisec to your arsenal to prevent future infections ;-)
11. Relevant artifacts:
Doc File - 97f3fb12837db7d4e27b11d310d8f441d00e65a43e95e9af2435e5e47abb1668
Kovter URL - hxxp://demitartgourmet[.]com/changelog/bindata[.]exe
Kovter Executable – 7e57dca4b9dec787e3fdbc983ee8111f97f75fa772e77a166ec18c49e1358f50
Sandbox report for the same executable - https://www.hybrid-analysis.com/sample/7e57dca4b9dec787e3fdbc983ee8111f97f75fa772e77a166ec18c49e1358f50?environmentId=100





.png?width=571&height=160&name=iso27001-(2).png)