
Earlier this year, Microsoft announced its Windows updates for business, which was proclaimed as a way to "empower IT Professionals to keep the Windows devices in their organization always up to date with the latest security defenses and Windows features." If there is one thing most IT Pros agree on, it is that patching is a pain – it is something that must be done for the long-term security of the organization, but it is disruptive so it gets delayed (and the new Microsoft service will attempt to shorten these delays). And even worse than the business interruption patching causes, on its own, patching is never sufficient.
Let's take a look at why patching Windows 10 either in the very second the patch is released or according to some predetermined Windows schedule, is still not enough to protect against modern cyber-security threats.
It's All about Applications
Microsoft Patches Microsoft. Very naturally, Microsoft cares about maintaining its own operating system. But vulnerabilities still reside in 3rd party applications such as Web browsers and PDF readers. So your Windows 10 might be updated four times a day in the last week or once a month, but your browser is still exposed to a severe remote code execution attack.
A Patch Is Born
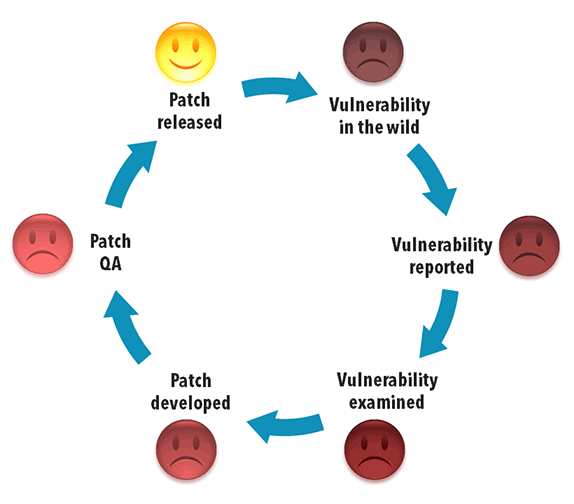
Patches make a long trip before they arrive at your computer, if at all.
First, someone has to report the vulnerability. This usually means that an exploit was alive in the wild for a while. For how long? Nobody really knows. Perhaps for years. After the vulnerability has been found and reported and dispatched to the right technical team, it is examined and checked and analyzed. At some point the vendors come up with a patch, which now the customer has to test and release. Not all patches are approved - some of them are not compatible with installed applications inside the organization - this implicates even more severe problems inside organizations. For each new patch selected to be released a full regression testing is required. Finally, the patch is approved and released to IT for deployment.
Since the vulnerability exists in the wild and until it gets patched, a long time may pass, 205 days on average according to Gartner. While that patch is just a “bun in the oven”, attackers can use the vulnerability to exploit your system.
IT Administered Systems
Computerized systems in enterprise organizations are typically maintained on a regular basis. However, once released and approved, updates are distributed to servers and endpoint systems based on the IT administrator’s schedule and priority. It can be once a week, or once a month, giving just enough time for attackers to slip in and gain a foothold in your system.
We Are in the Zero-day Business
Finally, remember that patches are aimed at stopping the vulnerabilities already known to the world. In the modern arena of targeted attacks, advanced hacking, and dark markets, zero-day vulnerabilities are widely used. Such zero-day vulnerabilities will not be patched in the next patching round, and even not the one after that. Your system will still be vulnerable to zero-day exploits regardless of the amount and frequency of the patches, even if Microsoft is trying to soften the ramification of frequent patching with a better business process.
So in the endless race between the good-guys and the bad-guys it seems that nothing has really changed, with or without Microsoft’s new patching policy. Attackers will always have a chance to exploit the vulnerability before it gets patched.
Morphisec aims to break this vicious cycle, and defend you by virtually pre-patching your system, even before the vulnerability was discovered and its related exploits are created. Our solution is capable of stopping the attacker instantly, and providing valuable forensic information about the attack.
For more information about Morphisec or to become a beta-tester, please get in touch.





.png?width=571&height=160&name=iso27001-(2).png)