Google, SpaceX, and even NASA, recently banning employee use of Zoom as they shift to work-from-home workforces in response to COVID-19 have shined a spotlight on the widely popular video conferencing tool’s security flaws. While “ZoomBombing” trolls can certainly be embarrassing, those types of breaches are only a harbinger for more sophisticated ransomware, zero-day attacks, and malware that can be carried out targeting Zoom security weaknesses.
Over the past few weeks, Morphisec Labs researchers identified a flaw in the Zoom application that can enable threat actors to voluntarily record Zoom sessions and capture chat text without any of the meeting participants’ knowledge. The Zoom malware is even able to do this when the host has disabled recording functionality for participants.

The trigger is a malware that injects its code into a Zoom process without any interaction of the user and even if the host did not enable the participant to record. When recording in this way, none of the participants are notified that the meeting is being recorded while the malware fully controls the output.
This, in effect, enables spying on a Zoom session. There is an increased risk of this happening, especially knowing that malicious actors have been amassing Zoom credentials and there are over 500,000 accounts currently available to purchase on the dark web. Furthermore, Zoom is usually a trusted application; turning it into an info-stealer in this way acts as a means of evading detection and bypassing prevention.
We’ve alerted the teleconferencing company to this current security weakness and how it can be targeted by malicious actors. The video below demonstrates an attack simulation to illustrate in detail this Zoom flaw.
Overview: The malware simulation shows a security attack that takes place during a discussion between a victim and the attacker. Both are using the latest version of Zoom with all of its security features turned on and antivirus software installed and running. The victim host (Michael) in the video disables recording for participants; the attacker (Sally) leverages a weakness in the Zoom application to record the session, despite the fact that she doesn’t have recording privileges. She is also to record the session without the host’s knowledge.
Here’s how:
- Michael sends his meeting invite over to Sally.
- Sally accepts the invite and joins the conference with Michael.
- Michael sends a chat illustrating that messages can be sent/received, and now Sally can reply.
- Sally asks Michael access to record the session. However, he denies this request by disabling recording privileges for attendees as he is about to share confidential information.
- However, here, Sally launches malicious code that triggers the system. On her screen, she’s able to view that the session is indeed being recorded. But on Michael’s host screen, there’s no indication that the meeting is being recorded.
- After the session ends, the software manipulates Zoom so that the unauthorized recording can be delivered to Sally in a location that she chose. She now has access to a full decrypted session, including the chat that supposedly wasn’t recorded and all videos that were shared. If webcams had been used, she would have those videos, too.
Note: In a normal meeting, once the host begins recording the discussion, the participants will be notified that it’s being recorded. Likewise, in regular meeting, Michael can disable Sally’s or anyone else’s recording privileges should they have tried to record on their own. Further, although anyone can record a Zoom meeting locally using built-in recording apps, the difference with this malicious software is the ability to export everything even when Zoom is minimized.
Weak spots such as the one demonstrated above, which leverage trusted collaboration applications like Zoom to steal information, are particularly alarming. As Zoom is trusted, signed, and perhaps even whitelisted in some cases, it won’t flag any alarms on detection logic that might be thrown with other recording software. Furthermore, similar techniques could also be used to turn Zoom into a RAT for full remote control for the adversary, which could be even more devastating. Traditional antivirus software would have no remedy for defending against this type of breach. Unlike these signature-based defenses, Morphisec’s Moving Target Defense technology is one of the few, if only solutions, that can defend against this type of threat.
Morphisec’s Moving Target Defense Sets Decoy For Zoom Malware
As the video depicts, we also ran the invasion simulation a second time. The only difference with the simulation was using the Morphisec agent to protect the Zoom application. This approach immunizes Zoom against attacks such as this variant, which are attempting to abuse memory resources. This is even with all the Windows 10 hardening features turned on, such as ASR and Defender AV. This malware completely bypasses even those strengthened Windows OS security features.
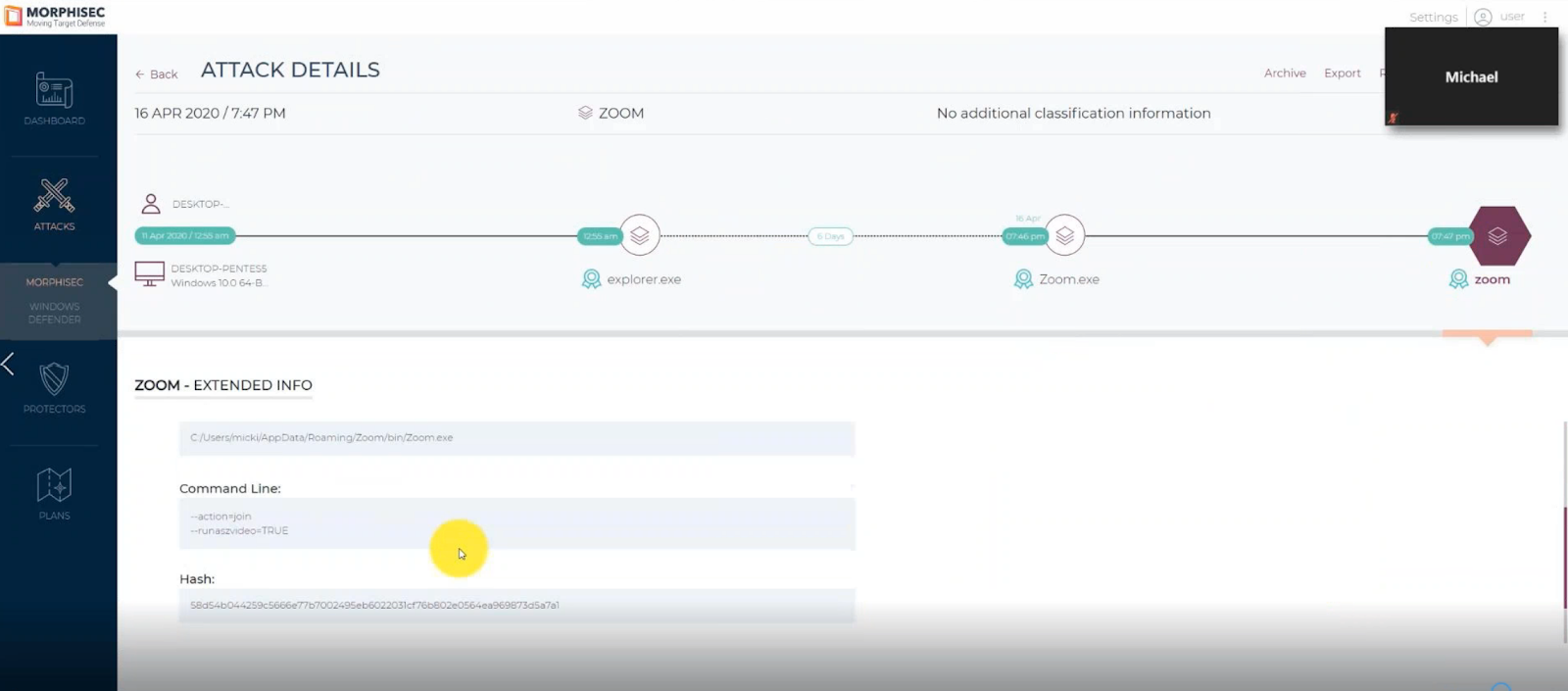
With Moving Target Defense applied to harden Zoom, Sally tries to launch the attack and it fails. What she needs to use is hidden from her and morphed; what she actually attacked was a decoy that triggers the alert and sends any forensic data to the console for further investigation.
The vast majority of cybercriminals follow usage patterns and build exploit tools that can be delivered via the documents, applications, and tools that are most widely used and most enterprises depend on. For a long time that has meant zero-day and unknown threats delivered via traditional paths such as Office and Adobe.
However, with those business solutions increasingly hardened and patched to thwart advanced threats, and demand for remote collaboration tools rapidly increasing in response to the COVID-19 crisis, attackers are putting collaboration applications such as Zoom in their crosshairs. Given patching cycles are significantly slower for these types of applications, a layer of deterministic prevention to protect against in-memory and evasive cyber attacks is urgently needed. This is why Morphisec’s Moving Target Defense technology is so vital to protect the enterprise against advanced evasive threats, extending automatic and deterministic hardening to critical applications in our increasingly work-from-home world.





.png?width=571&height=160&name=iso27001-(2).png)