Sophisticated attack techniques are increasingly bypassing traditional detection-based cybersecurity solutions. In 2023 Gartner® published a report highlighting Automated Moving Target Defense (AMTD) as “an emerging game-changing technology for improving cyber defense... [that] effectively mitigates many known threats and is likely to mitigate most zero-day exploits within a decade, rotating risks further to humans and business processes.”[1]
.png?width=1200&height=628&name=Moving%20Target%20Defense%20-blog_1200x628_v.1.2%20(1).png)
Static Defenses Are Not Enough
The evolution of cybersecurity began with anti-virus (AV) software, which offers static analysis of binaries and files to check if they correspond to known malware. Next-generation anti-virus (NGAV) software and endpoint protection platforms added dynamic analysis that executes a file in a sandboxed environment and observes it. Endpoint detection and response (EDR/XDR/MDR) took this further with behavioral analysis. EDR technology observes execution on a computer, hooks into important functions/syscalls to learn about behavior in real-time and analyzes not just the binary but everything surrounding the execution.
According to Gartner® : “Combining AMTD solutions at different layers of the technology stack provides innovation leaders with a highly effective ‘defense in depth’ strategy that significantly improves overall security posture.”[2]
What is Automated Moving Target Defense?
AMTD technology is the next evolution in cybersecurity, and unlike the technologies that came before it, rather than focusing on detection and reaction, it offers true prevention.
AMTD is based on a basic premise taken from military strategy, that a moving target is harder to attack than a stationary one. AMTD uses strategies that orchestrate movement or changes in IT environments across the attack surface to increase uncertainty and complexity for attackers.
AMTD reduces exposed attack surfaces by introducing strategic change, while increasing the cost of reconnaissance and malicious exploitation on the attacker, according to the Gartner® report. AMTD involves moving, changing, obfuscating, or morphing attack surfaces to disrupt adversaries’ cyber kill chain.

The Four Elements of AMTD
The technology incorporates four main elements, according to Gartner® : “Proactive cyber defense mechanisms; automation to orchestrate movement or change in the attack surface; the use of deception technologies, [and] the ability to execute intelligent (preplanned) change decisions.”[1]
Note that while deception is a key technological component of (A)MTD, it is not synonymous with it. Morphisec’s table below outlines the difference between deception technology, MTD, and AMTD.
Landscape: Moving Target Defense and Deception |
||
|
Technology |
How it works |
Benefits |
|
Morphisec Automated Moving Target Defense |
|
|
|
“Classic” Moving Target Defense |
|
|
|
Deception |
|
|
For example, Morphisec’s patented AMTD technology uses system polymorphism to create a randomized, dynamic runtime memory environment, moving application memory, APIs, and other operating system resources while leaving decoy traps in their place. This makes it virtually impossible for threat actors to find what they’re looking for—you can’t hit what you can’t see.
Any code that tries to execute on a decoy is automatically reported and captured for forensic analysis, while the real system resource remains safe and the attack is prevented. As Rick Schibler, VP of IT at Kentucky Trailer says, “Morphisec’s Moving Target Defense is critical to hardening our attack surface.”

AMTD's Market Impact
AMTD has proven successful within military doctrine for many years in modern warfare strategies. However, Gartner® notes that historically AMTD usage within commercial cybersecurity has been limited, but this is changing now.
Currently, reactive, detection-based technologies like next-generation anti-virus (NGAV), endpoint protection platforms (EPP), and endpoint detection and response (EDR/XDR/MDR) dominate the cybersecurity market. These technologies work by first detecting malicious files or behavior patterns and then responding to them. They are fundamentally reactive in nature.
Gartner® suggests prevention should be a greater focus: “Although prevention hasn’t been a panacea within security technologies, Gartner® sees a strong need to encourage the market to focus on promising new prevention-related technologies.”[1]

AMTD’s preventive approach is particularly important given the investment attackers put into attack reconnaissance to discover vulnerabilities and the right way to exploit a victim’s systems. Many modern cyberattacks are highly targeted and tailored to evade and bypass specific defense layers.
The Gartner® report notes the example of operational technology (OT)-related use cases. Because of industry variety and the specialized nature of industrial environments, malicious actors need to dedicate time and resources to gather the needed intelligence to be successful. AMTD methods like obfuscation and system morphing are particularly valuable in protecting against such highly targeted attacks. This preventive approach is especially effective in securing endpoints and server workloads—typically an organization’s largest attack surface.
For this reason, Gartner® predicts that: “By 2025, 25 percent of cloud applications will leverage AMTD features and concepts as built-in prevention approaches, enhancing existing Cloud Web Application and API Protection (WAAP) technologies.” Additionally, Gartner® also predicts that: “AMTD-based solutions will displace at least 15 percent of traditional solutions that are focused on detection and response only [by 2025], up from less than 2 percent in 2023.” And by 2030, Gartner® expects exploit-resistant AMTD-based hardware and software to emerge, “shifting security focus further to business process, identity misuse and social engineering prevention over application, endpoint and workload security strategies.”[1]
Gartner® offers an example of the AMTD automation concept:
- Identifying target assets
- Selecting the morphing interval
- Automating asset reconfiguration
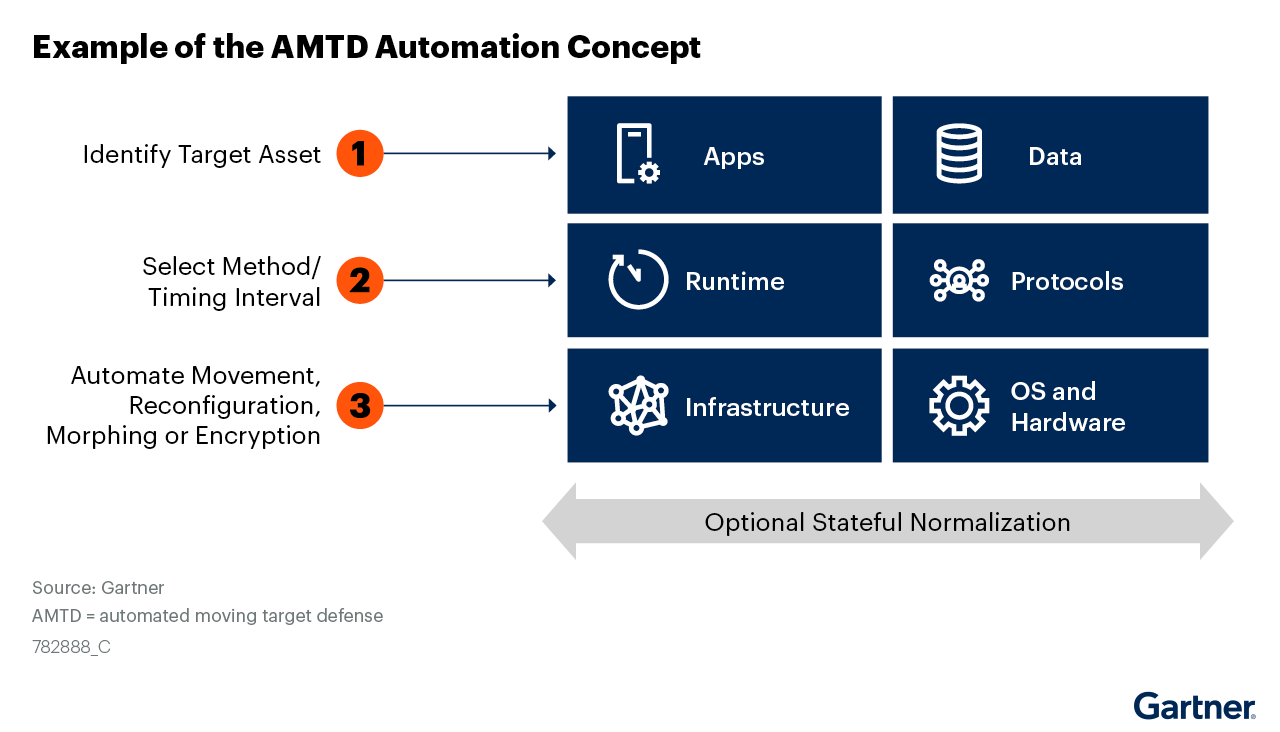
We believe Morphisec’s technology incorporates all three concepts, protects multiple system resources, and includes attack visibility thanks to deception technology.
Automated MTD is Here—And It’s Proven to Work
More than 7,000 companies have deployed Morphisec’s AMTD technology across approximately nine million endpoints and Windows and Linux servers. They use it to augment NGAV, EPP, and EDR/MDR solutions and stop the most advanced and undetectable attacks these solutions may miss. Two such examples include:
TruGreen
- Based in Memphis, Tennessee, TruGreen is America's largest customized lawn care and treatment services provider, with more than 12,000 employees and annual revenue exceeding $1.5 billion.
- TruGreen deployed Morphisec’s AMTD software and discovered that “With our previous solution, it took seven agents to accomplish the same thing we’re doing with just one Morphisec agent,” said TruGreen’s Principal Security Architect, Dale Slawinski
- The company realized a 2.3x return on investment while cutting software costs by two-thirds and slashing false positives by 95 percent.
TruGreen brings in an objective third party each year to conduct penetration testing to identify vulnerabilities that cybercriminals could exploit. “This year, for the first time, we were able to prevent the tester from cracking into one of our endpoints,” said Ryan Pagan, Cyber Security Engineer at TruGreen. “After implementing Morphisec, the tester couldn’t figure out what was keeping him from breaking in. He spent several hours attempting to crack our security but couldn’t figure it out. The tester said to us, ‘Normally, we can get around endpoint security stuff, but we couldn’t get around Morphisec.'"
Anonymous Global Manufacturer
- One Morphisec customer is a large, global American manufacturer of mechanical power transmission products, with roughly 10,000 employees across dozens of countries and billions in revenue.
- The manufacturer's CIO says, “Dollars spent doesn’t correlate to security value. We spent a lot of money on our MDR provider, and yet we still were breached and had to do a lot of work ourselves.”
- They deployed Microsoft Defender with Morphisec AMTD to secure their critical infrastructure from both known and unknown attacks.
The preventative capabilities of Morphisec’s AMTD technology allowed this CIO's team to adopt an entirely new security posture with much greater operational efficiencies. So now, “We don’t spend much time on detection and response,” he said, “because we don’t need to.” Instead, they focus on training people, improving processes, and planning for emerging threats. These are high-level initiatives they now have the resources for because AMTD blocks attacks they used to detect and prevents damage they used to remediate.
Moving Target Defense explained
Check out other real-world examples of AMTD in action here.
Achieving Preemptive Cyber Defense with AMTD
In recent years AMTD has been identified as an innovative aide supporting various cybersecurity strategies including endpoint, cloud, legacy systems, continuous threat exposure management (CTEM) and more.
Gartner® covers AMTD extensively; check out this reference guide for a comprehensive list of Gartner® AMTD research and insights.
Organizations are prioritizing and shifting focus to preventative solutions in an effort to implement and achieve preemptive cyber defense, an approach that involves anticipating and acting against potential attacks before they occur.
Morphisec AMTD proactively prevents the most sophisticated and damaging cyberattacks without needing any prior knowledge of them—or even to detect them, thereby supporting preemptive cyber defense.
Morphisec’s AMTD key capabilities and benefits include:
- Anti-ransomware – Advanced ransomware prevention leveraging dedicated AMTD mechanisms for safeguarding against ransomware attacks, from early attack stages to the impact/encryption phase.
- Credential theft protection – Advanced credential theft protection leveraging AMTD for safeguarding against Infostealer/credential stealing attacks
- Enhanced cyber-resilience: Implementing AMTD to efficiently mitigate the costs associated with recovery from advanced, previously unknown evasive threats, thereby bolstering overall cyber defense strategy.
- Prevention-first security: Prevents threats without prior knowledge: signatures, behavioral patterns, or indicators of attacks (IoAs).
- Operational efficiency: Providing simple installation with negligible performance impact and no additional staffing requirements.
- Lower IT and security costs: Significantly reducing security analyst alert triage time and costs due to early prevention, exact threat classification and prioritization of high-risk alerts.
- Risk-based vulnerability prioritization for exposure management: Empowering organizations with continuous business context and risk-driven remediation recommendations, enabling effective prioritization of patching processes and reduced exposure with patchless protection, powered by AMTD.
- Flexible deployment: Offering a SaaS-based, multi-tenant and API-driven platform.
 to learn more about how you can modernize your organization’s cybersecurity strategy and harden threat defense with preemptive measures and emerging technology like AMTD.
to learn more about how you can modernize your organization’s cybersecurity strategy and harden threat defense with preemptive measures and emerging technology like AMTD.
References
[1] Emerging Tech: Security — The Future of Cyber Is Automated Moving Target Defense. Lawrence Pingree, Carl Manion, Matt Milone, Sean O'Neill, Travis Lee, Mark Pohto, Mark Wah, Ruggero Contu, Dan Ayoub, Elizabeth Kim, Rustam Malik, Nat Smith, 28 February 2023.
[2] Gartner® Emerging Tech: Security — Tech Innovators in Automated Moving Target Defense, Mark Pohto, Carl Manion, 07 June 2023
Gartner® is a registered trademark and service mark of Gartner® , Inc. and/or its affiliates in the U.S. and internationally, and is used herein with permission. All rights reserved.
This graphic was published by Gartner® , Inc. as part of a larger research document and should be evaluated in the context of the entire document. The Gartner® document is available upon request from Morphisec.
Gartner® does not endorse any vendor, product or service depicted in its research publications and does not advise technology users to select only those vendors with the highest ratings or other designation. Gartner® research publications consist of the opinions of Gartner® 's Research & Advisory organization and should not be construed as statements of fact. Gartner® disclaims all warranties, expressed or implied, with respect to this research, including any warranties of merchantability or fitness for a particular purpose.






.png?width=571&height=160&name=iso27001-(2).png)