Executives often view cybersecurity as an expense, a necessary one perhaps, but still a burden on company finances, focus and time. Instead it should be approached as an investment – an investment in protecting an organization’s systems, resources, customers and reputation. And, like any investment, cybersecurity should be able to prove its value by delivering a solid ROI. But how do you calculate cybersecurity ROI? After all, security doesn’t create earnings.
While security may not contribute revenue, loss prevention certainly impacts a company's bottom line. The ebook (download here) “Know Your Cyber Security ROI: Making the Business Case for Cyber Security” offers a methodology for determining the ROI of your organization’s cybersecurity initiatives, and points out key areas to improve your return on security investment. This blog post is the first in a series of excerpts from this ebook.
Implicit ROI of cybersecurity
Cost avoidance is the implicit ROI of cybersecurity. How do you calculate the expected value of your cybersecurity operations? It depends on how much a cyberattack would have cost your organization, which in turn depends on which system was attacked, what data was leaked, who was affected, and most importantly, how quickly the attack was brought under control.
To calculate the cost of attacks on your organization, you need to consider both the tangible costs – actual money spent on containment and repair – as well as intangible costs such as operational disruption, brand damage, lost revenue and compromised assets. Oftentimes the intangibles exact a heavier toll on your enterprise than tangible expenses. Insurance giant Lloyd’s estimates that cyberattacks cost companies $400 billion every year. During 2015, businesses fell victim to an average of 1.9 successful cyber attacks per week, racking up annual costs of $7.7 million. This is up 13.9 percent (as measured in local currencies) over 2014, according to the Ponemon Institute’s 2015 Cost of Cyber Crime Study. And while the larger the organization, the greater the total breach cost, small organizations actually incur much higher per capita costs at $1,388 per seat vs. $431.
Cyberattacks can be divided into three major phases – before an attack, while under attack and disruptions after the attack. The phases roughly correlate with the cyber kill chain stages, but from the point of view of the organization rather than the attack. There is a steeply increasing relationship between the time to contain an attack and organizational cost.
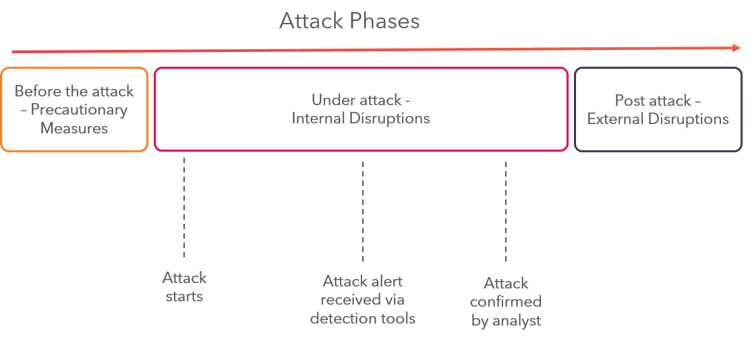
The next blog posts in this series will examine the organizational costs associated with containing an attack during each of these phases. Want it all at once, all in one place? Download the full e-book now!




.png?width=571&height=160&name=iso27001-(2).png)