Antivirus software is kind of the lock on a window: it keeps out the most basic sorts of intruders but provides little protection against someone willing to break the glass. The analogy is even more apt because, like window locks, antivirus software...
Read MoreDefending your critical infrastructure against cyber threats has never been harder. Adversaries constantly innovate new techniques to exfiltrate or encrypt data, forcing defenders to play a cybersecurity version of “whack-a-mole” in their attempts...
Read MoreWith shut-down orders closing offices across the country, millions of Americans have started working remotely. Apps like Skype, Zoom, and dozens of others make it relatively easy to remain connected and productive. They’ve become so indispensable,...
Read MoreFor the second year in a row, Morphisec has awarded three scholarships to top female students pursuing cybersecurity degrees around the world. The latest numbers still place women’s employment in the cybersecurity industry at only 24%, but the...
Read MoreThis article is the first in a three-part series looking at Morphisec version 3.5 - Unified Threat Prevention platform. Next week we take a deep dive into the new Attack Trajectory and the ways that this powerful tool can be used. Subscribe to this...
Read MoreOn the heels of RSA 2019 and International Women’s Day, I am proud to announce Morphisec’s second annual Women in Cybersecurity Scholarship. This year’s scholarship program offers three awards totaling $8,000 aimed at encouraging women studying...
Read MoreIndustry best practices demand patching software vulnerabilities as soon as a patch is released, in order to shorten the time period in which the organization is at risk. But industry surveys show that IT organizations are overburdened with patches,...
Read MoreJust in time for the new year, Morphisec has released a new version of our Endpoint Threat Prevention platform. Version 3.0 features enhanced, advanced analytics and SOC dashboarding, richer, SOC-enabled threat intelligence capabilities, and a new...
Read MoreMorphisec is pleased to announce the 2018 winners of the Morphisec Women in Cybersecurity Scholarship. The program offers three scholarships for female students enrolled in cybersecurity-related studies to support and encourage young women exploring...
Read MoreOne of the hottest topics at last week’s RSA Conference was GDPR. Over twenty sessions covered GDPR from various angles and many more touched upon the subject in some way. This was hardly surprising – with the May 25th compliance deadline looming,...
Read MoreAlthough I’m excited to be at the RSA Conference with my Morphisec colleagues, it reminds me of the impetus for starting our Women in Cybersecurity Scholarship. Of 28 keynote speakers at RSAC, only seven are women, and six of these were added at...
Read MoreMuch has been written about the high barriers to entry for women in cybersecurity. Certainly the numbers are depressing. Women make up just 11% of the world’s information security workforce, according to the 2017 Global Information Security...
Read MoreOrganizations employ many precautions and actions in the attempt to block cyber attacks. Such measures can require significant time and resources to implement as well as maintain. This class of tools includes endpoint security solutions such as...
Read MoreMicrosoft recently announced it would extend support for its Enhanced Mitigation Experience Toolkit (EMET) until July 31, 2018. According to Microsoft, this 18 month reprieve – originally support was scheduled to end on January 21, 2017 – is the...
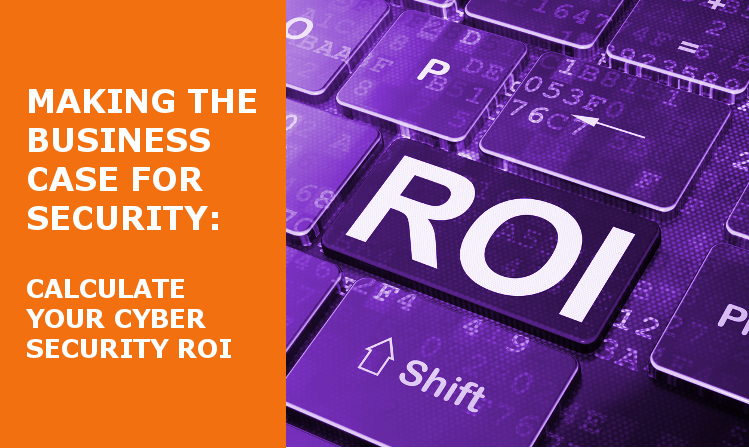
Read MoreExecutives often view cybersecurity as an expense, a necessary one perhaps, but still a burden on company finances, focus and time. Instead it should be approached as an investment – an investment in protecting an organization’s systems,...
Read MoreMicrosoft released its October patching update today and, as announced, it introduces a major change that has many system administrators wondering just what to do.
Read MoreA Brief History of vdi
Virtual Desktop Infrastructure (VDI) is not a new concept – in fact virtualized desktops can be traced back to the 1960s, when IBM divided up mainframes into virtual machines to allow for multiple, simultaneous users. The...
Read MoreSearch Our Site
Recent Posts
Posts by Tag
- Automated Moving Target Defense (157)
- Threat Research (135)
- Cyber Security News (132)
- Morphisec Labs (124)
- Morphisec News (54)
- Adaptive Exposure Management (14)
- Defense-in-Depth (13)
- Ransomware (12)
- Preemptive Security (11)
- Gartner (10)
- Continuous Threat Exposure Management (CTEM) (9)
- Microsoft (8)
- In-Memory Attacks (7)
- Healthcare Cybersecurity (6)
- Advanced Threat Defense (5)
- Legacy Security (5)
- Artificial Intelligence (4)
- Financial Cybersecurity (4)
- Linux Cybersecurity (4)
- Fileless Malware (3)
- Threat and Vulnerability Management (2)
- Managed Service Providers (1)




















.png?width=571&height=160&name=iso27001-(2).png)