
Since early March, the team at Morphisec Labs has been supporting enterprises as they shift to distributed workforces in response to COVID-19. From assisting hospitals with securing their remote workers to uncovering new weaknesses in collaboration applications that could pose a threat to business continuity, we’ve been working hand-in-hand with customers, counterparts at security companies, and authorities to stay ahead of defending against a rapidly evolving cyberattack landscape.
At the same time, we’ve been assessing how attacks targeting enterprises have shifted to take advantage of new weaknesses in remote workflows. Today, as we reach the year's midway point, we’re publishing some of the research and data we’ve collected on how COVID-19 has altered the cyberattack landscape.
ENTERPRISE ATTACK ATTEMPTS TRIPLED IN APRIL
With most enterprise employees transitioning to work-from-home environments between mid-March and early April, there’s no denying the pressure that was placed on IT teams and security staff to ensure remote workers had access to the resources they needed to be productive and protected.
It was undoubtedly a period of mass uncertainty based on questions around the pandemic’s impact on public health, the economy, and how the world’s largest work-from-home experiment would unfold. While organizations were adapting to their new normal, attackers were also evolving their methods to exploit the vulnerabilities of distributed operations.
The number of enterprise cyberattacks that Morphisec blocked in April nearly tripled. While Morphisec’s Moving Target Defense technology prevented between 60,000 and 70,000 attacks per week in February, weekly attacks skyrocketed to more than 170,000 across five million endpoints in April.
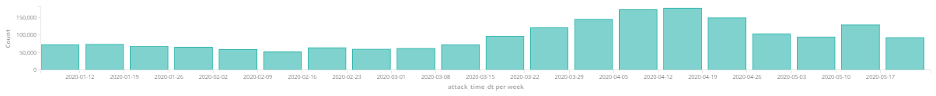
Opportunistic by nature, hackers look for the easiest ways to attack the largest number of users and reap the most significant gains. And unfortunately, the gaps that opened when millions of workers moved to spotty home-based WiFi networks and non-hardened personal devices was too luring for hackers to ignore. We recently released a report that found 56 percent of employees are using their personal computers as they work from home, while 25 percent admit to ignoring their company’s security protocols.
While Morphisec was able to prevent these enterprise cyberattacks successfully, employees operating on more vulnerable and unpatched networks could easily fall victim to determined infostealers, exploits, and code-injectors as they continue to work from home.
Adware Peaks and Subsides; Exploits Remain Steady
During the first few weeks of the pandemic, and employees working from home, adware was running rampant in the U.S. Between early March and mid-April, adware attempts catapulted from 1,000 to 5,000 per week to over 90,000 per week! These were browser-based attacks seeking to take advantage of employees who had recently shifted to working from home and who were using their personal computers for both work and personal use.
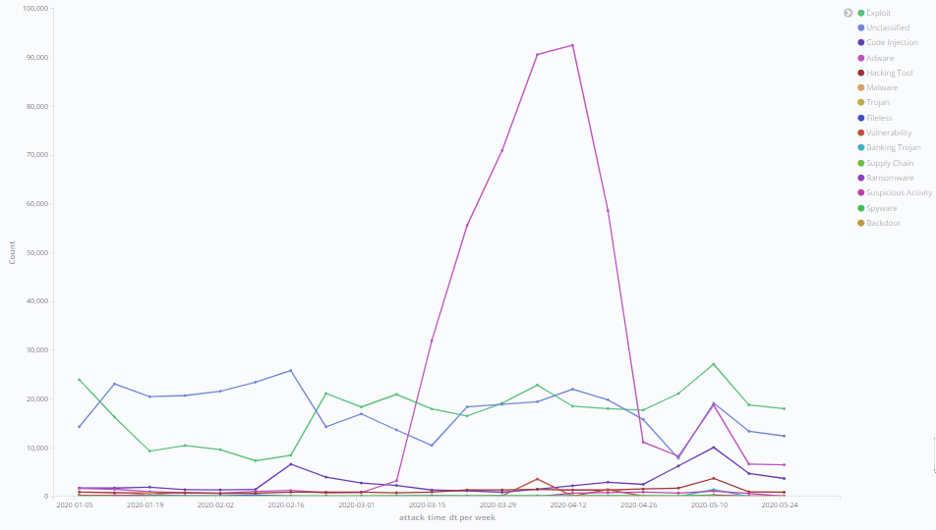
In fact, Morphisec detected adware targeting collaboration tool downloads and game downloads. With millions of American employees balancing parenting, homeschooling, and work amidst stay-at-home restrictions, sharing devices with children—whether they be personal or enterprise devices—appears to have become a common practice.
Adware attacks have thankfully drastically subsided since March and April. However, Morphisec has seen a slower, but steadier climb in the number of exploits since February, with cyberattacks progressing from 10,000 per week in early February to 27,000 by mid-May. The exploits have targeted older versions of Windows servers, most notably Windows Server 2008 R2, which reached end of life earlier this year. They are almost exclusively vulnerabilities that are integrated into the basic attack and pen-testing frameworks, such as Metasploit, Cobalt Strike, and Empire.
MALICIOUS CODE injection bids SEE A SURGE
Morphisec has also seen a significant increase in code injection attempts in the wake of COVID-19. Attack attempts reached almost 7,000 per week in February before peaking in May when attacks surpassed 10,000 attempts per week. Prior to this, code injection attacks hovered around 2,000 per week. Attacks targeting LSASS, one of the most critical and sensitive Windows processes, were the most common for Morphisec to prevent. LSASS is responsible for authentication and, because of its importance, can’t be stopped--doing so ends up causing a similar effect to blue-screening. These attacks are targeting LSASS for credential theft, lateral movement, or even authentication bypass.
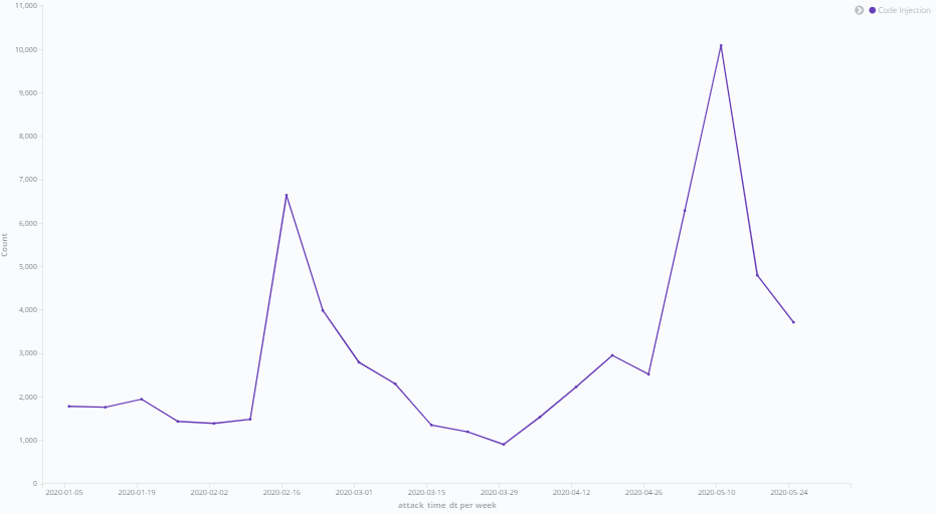
There are various possible reasons for this trend, ranging from the complex to the more mundane. For example, one potential explanation is simply that bad actors have had more time on their hands than usual as a result of stay-at-home orders.
But the fact that the Morphisec team has also seen a significant surge in the use of hacking tools to bypass identification could also be an explanation for this trend. Hacking tools and code injection attacks peaked simultaneously, so the above chart may illustrate that code injection trends soared because bad actors attempted to take advantage of remote workers installing new tools and applications.
While most modern organizations, whether in the private or public sector, have extensive network monitoring and security tools in place to catch malicious code before they even access employee computers, all that protection goes away when personal devices and networks are used for work.
Malware Proves to be a Persistent Threat
COVID-19 or not, malware proves to be a constant threat to enterprises. At the beginning of lockdown in March, the team at Morphisec Labs observed a significant increase in phishing attacks utilizing malware and info stealers (including Zoom phishing).
Phishing remains the main vector for cyberattack landscape against both enterprise and personal devices. Where personal devices are more exposed is through phishing.social engineering attacks that come with a malicious archive. This particular type of phishing attack, with executable attachments, would be filtered many times by an enterprise’s network gateways.
For example, we’ve been tracking an uptick in the delivery of Ursnif/Gozi during the COVID-19 pandemic, a high-risk trojan-type virus proliferated through spam email campaigns. We observed this specific campaign—starting at the beginning of January—that uses advanced obfuscation techniques to evade detection and record sensitive information. Many of the files have a .xlsm extension and have less than a 3 detection score. A score of less than 3 is not a high enough threshold for a static heuristic-based solution to classify the file as suspicious (nevermind malicious). For this reason, many detection-based solutions miss this type of file.
The Morphisec team hasn’t reported any significant peaks when it comes to ransomware, but make no mistake, it remains a consistent threat. Ragnar Locker, for example, deployed a virtual machine on every workstation to evade detection. The ransomware then mapped the discs to the image; no detection solutions are within the image, so there’s no ability to detect the ransomware.
With the average cost to recover from ransomware rising to more than $84,000 this year, and the overall expense of an enterprise data breach reaching almost $9 million, it’s a burden absolutely no organization wants to deal with.
The Rising Need for Advanced Endpoint Protection
Despite cyberattack landscape threats rising dramatically, enterprises have risen to the challenge of remote work. But with many companies committing to working from home in some capacity until at least the end of the year, efforts to secure these remote workers will become more important. Just as IT teams are rethinking the toolset that will make remote employees more productive, they must reimagine their cybersecurity stacks to ensure business continuity in this new distributed environment. One way to do this is through the use of moving target defense technology.
Even while working remotely themselves, IT teams can deploy moving target defense to secure their increasingly remote employees as they continue to work from home. Installing the lightweight agent on a remote endpoint enables morphing critical application memory—the target for most kinds of evasive malware, zero-days, in-memory exploits, and fileless attacks.
So if this really is our new normal, and attack trends continue to rise, enterprises can rest assured that their employees have access to the tools they need to work safely and security, when they need them.





.png?width=571&height=160&name=iso27001-(2).png)