Morphisec has been recognized as a sample vendor in Gartner’s Emerging Tech: Security — Emergence Cycle for Automated Moving Target Defense Report—research covering groundbreaking security technologies that according to Gartner, “are paving the way for a new era of cyber defense possibilities.”
Cyber defense must keep pace with evolving threat techniques. Threat actors increasingly use complex and undetectable threat tactics like fileless, in-memory and zero-days, exploits and other evasive techniques to bypass traditional security controls and detection and response technologies.
Attackers are evolving and creating evasive and undetectable threats capable of bypassing traditional security controls and detection and response technologies. Next generation anti-virus (NGAV), endpoint detection and response (EDR), and extended detection and response (XDR) solutions are industry standard, but even these systems are challenged by these evasive techniques.
That’s because NGAV/EPP and EDR/XDR systems detect and alert on signature-based, known behavioral pattern attacks. But unknown and undetectable attacks employing evasive techniques are rising, with over 30 percent bypassing detection technologies. In response, SOC teams and security analysts are cranking setting detection system alert modes to the highest setting to better flag anomalous behavior and stop threats before they become business-impacting.
However, systems that operate in high alert mode negatively impact system performance and can produce high volumes of false positive alerts, accounting for 40 percent of total notifications, where 31 percent of alerts are never investigated. Even when set in high-alert mode, zero-day and other advanced attacks continue to bypass the industry’s best NGAV and EDR solutions. Effective defense-in-depth combines reactive detection and response with the power of best-in-class prevention to stop both known and unknown attacks.
Using Automated Moving Target Defense (AMTD) for Prevention First Security
Adversaries are constantly refining attack tools and techniques to evade popular defense technologies. Traditional malicious software and malware use executable files that leave behind evidence on disc or OS. That evidence trains defense tools to spot telltale deployment signals, enabling threat isolation.
Today, sophisticated attack chains hijack legitimate system processes and target device memory at runtime, rather than on disk or OS. This technique doesn’t leave the signatures or breadcrumbs required for behavior pattern analysis.
Evasive Techniques used by threat actors:
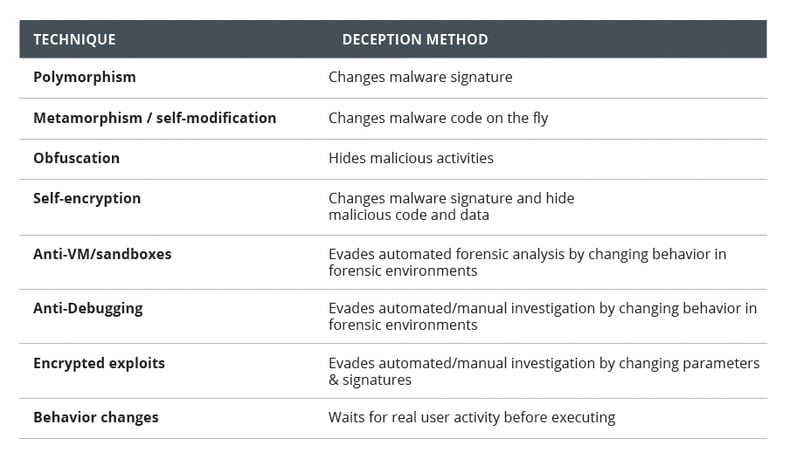
To catch attacks in real-time and pick up malicious patterns, detection tools need to scan device memory multiple times while an application is running. When detection systems are set to their most aggressive settings, scanning high volumes of data can slow down application performance.
Enter AMTD, a technology that Gartner touts as “the future of cyber.” AMTD technologies use polymorphism to move, change, obfuscate or morph attack surfaces and disrupt adversary cyber kill chains. They effectively guard against attacks by introducing complexity, uncertainty and prevention with an ultra-lightweight agent that doesn’t impact performance.
According to Gartner’s Emerging Tech: Security — Emergence Cycle for Automated Moving Target Defense Report, “By utilizing polymorphism within code and within runtime or OS environments, a threat actor quickly loses its ability to predict stored memory variables and memory scanning techniques used for exploitation within memory structures (the heap or stack). This AMTD technique can be effective at thwarting the execution of common software vulnerabilities and exposures.”
How AMTD works
The concept of Moving Target Defense is based on a classic three-prong military strategy that employs cover and concealment (making it more difficult for enemy observation), mobility (creating a moving target that’s hard to track), and deception techniques (tricking attackers by presenting decoy targets or false paths).
TruGreen, a Morphisec customer and the nation’s largest lawn care and treatment services provider ($1B+ revenue) faces a wide range of threats across more than 6,000 workstations and distributed operations. Concerned about stealth attacks, TruGreen selected Morphisec AMTD for greater security, cost-effectiveness and ultra-lightweight application. When conducting its annual third-party penetration test post-installation, the team noted that for the first time, testers were unable to access company endpoints, reporting that “normally we can get around endpoint security stuff, but we couldn’t get around Morphisec.”
Cybercriminals arm their malware with polymorphism, obfuscation, encryption and self-modification to evade detection and maintain unpredictability. These tactics give attackers an advantage over legacy security technology’s reliance on static analysis, signatures, file reputation and anomaly detection methods.
AMTD levels the playing field and hands the advantage back to defenders—it uses polymorphism for defense and deception techniques to dynamically change an organization’s attack surface, adding uncertainty and complexity that makes it more challenging for adversaries to strike. When operating systems and application targets are concealed or hidden, they become a more expensive, challenging, and time-consuming target from an attackers’ point of view.
Static defenses and standard security controls can’t catch today’s evasive threats, especially if lateral movement within a business network has already been established. Morphisec AMTD’s three-step process works to:
1. Morph and conceal by turning endpoints into unpredictable targets. As an application loads to the memory space, Morphisec morphs the process structure, relocating and transforming libraries, functions, variables and other data segments in a controlled manner. Each run is unique, per process instance, making the memory constantly unpredictable to attackers.
2. Protect and deceive by enabling controlled access to the morphed structure. Legitimate application code memory is dynamically updated to use the morphed resources. Applications continue to load and run as usual. A lightweight skeleton of the original structure is left as a trap.
3. Prevent and uncover by neutralizing and exposing attacks. Attacks target the original structure and fail, unable to access the resources they expect and need to execute. Attacks are immediately prevented, trapped and logged with full forensic details.
In practice, AMTD operates across at the network level, the host level and the application level. Morphisec’s prevention-first security software (powered by AMTD) uses a patented zero-trust at execution technology to proactively block evasive attacks.
The Benefits of AMTD
First and foremost, AMTD technology is designed to complement the detection and response tools used in existing security stacks. Morphisec AMTD enhances NGAV and EDR by boosting capabilities and hardening the overall attack surface using defense-in-depth capabilities that stop the unknown attacks that in-use technologies miss. The 7,000+ companies across Morphisec’s customer base use its AMTD technology to augment Microsoft Defender, Crowdstrike, SentinelOne, Trend Micro, Sophos and other NGAV and/or EDR solutions to stop the attacks that those solutions don’t.
According to Gartner: “Product and service integrations with existing detection and response solutions are essential ingredients for building the AMTD-enabled security solutions of the future. AMTD does not replace threat detection and response technologies; it enhances them.”
AMTD offers several advantages to defenders that include:
- Pre-emptive action that doesn’t wait for attackers to breach the organization before it works.
- Polymorphic defense that hides exploits from polymorphic attacks.
- Removing the attackers’ ability to gain persistence.
- Vulnerability protection with virtual patching until a patch is issued.
- Rapid and simple deployment with minimal performance impact.
Morphisec’s ultra-lightweight design is easy to install and run, with no additional headcount or infrastructure adjustments required. AMTD is truly prevention-first security, ushering a new era pre-emptive strategy that takes the innovation advantage away from attackers while empowering security teams.
Gartner states that: “Emerging technologies that introduce the ability to proactively and continuously morph and change IT environments and assets while simultaneously leveraging advanced deception features are set to transform the cybersecurity market over the next three to five years.”
Learn more about Morphisec’s ATMD technology and see it in action — schedule your demo today and discover why 7,000+ enterprises trust Morphisec to protect their environments against the most advanced and destructive attacks including ransomware, supply-chain, zero-day and fileless and in-memory attacks.







.png?width=571&height=160&name=iso27001-(2).png)