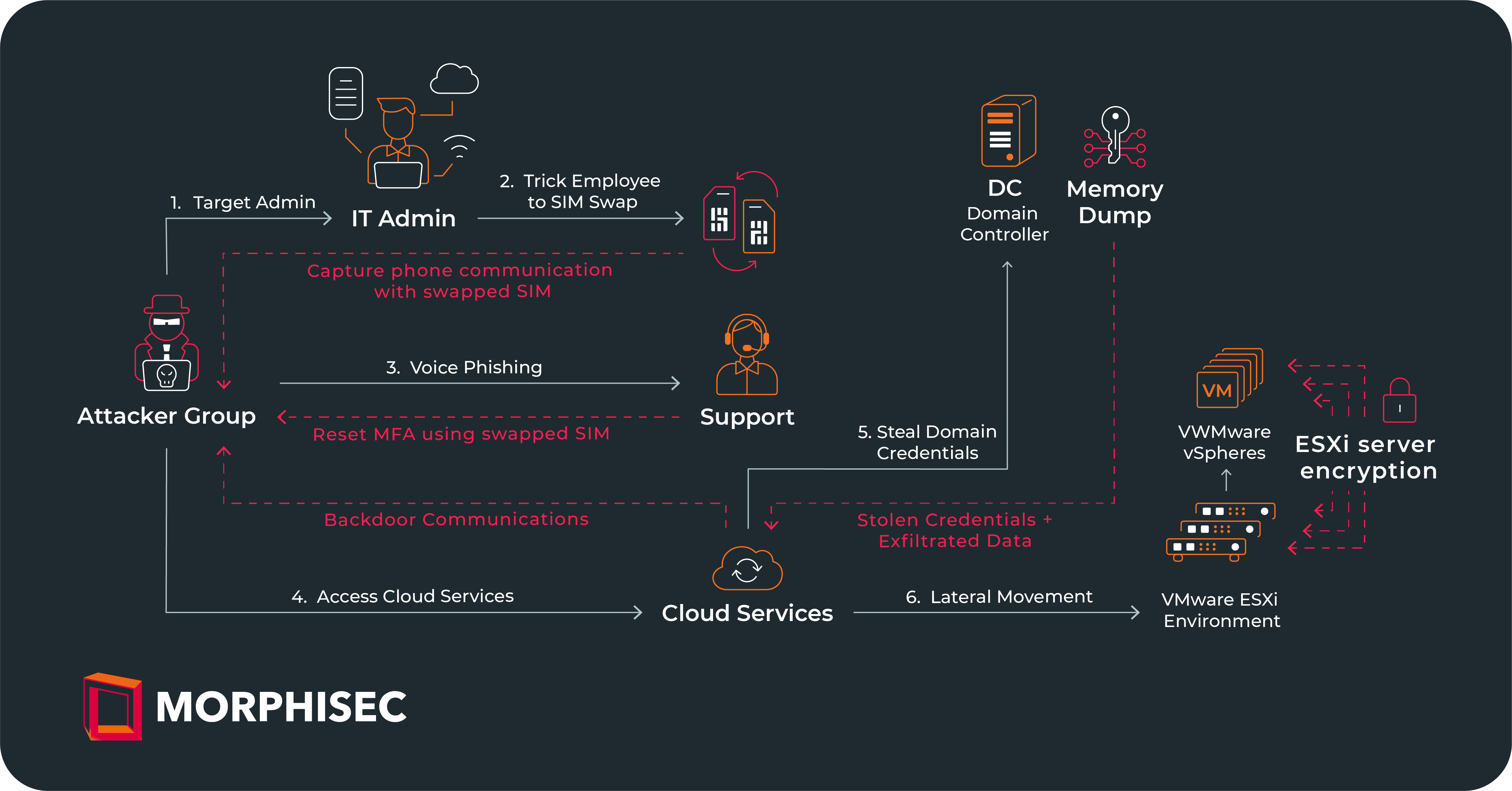
The ransomware attack that hitMGM Resorts International on September 10thcaptured headlines due to the company’s name recognition, reputational and customer impact,andthe overall magnitude ofbusiness disruptionthe attack caused.
Read More“If an attacker successfully hacks our workstations or trading terminals, they’d have full access to the firm’s critical infrastructure.” This quote from a Chief Information Security Officer at a leading US-based hedge fund shines a light on the...
Read MoreIn today’s threat landscape, multiple defense-in-depth layers are one of the only ways security teams can achieve peace of mind. Why? Two reasons stand out:
Read MoreCyberattacks targeting critical OT and industrial organizations rose by 87% last year—the threat level to OT is higher than ever, and threat actors are finding new ways to compromise OT environments.
Read MoreMorphisec has been recognized as a sample vendor in Gartner’s Emerging Tech: Security — Emergence Cycle for Automated Moving Target Defense Report—research covering groundbreaking security technologies that according to Gartner, “are paving the way...
Read MoreLegacy Microsoft operating systems (OSs) will probably be with us until the universe’s heat death. OS usage statistics show the total market share of legacy operating systems is still above 10 percent. With the total Windows installation base of 1.3...
Read MoreSearch Our Site
Recent Posts
Posts by Tag
- Automated Moving Target Defense (157)
- Threat Research (135)
- Cyber Security News (132)
- Morphisec Labs (124)
- Morphisec News (54)
- Adaptive Exposure Management (14)
- Defense-in-Depth (13)
- Ransomware (12)
- Preemptive Security (11)
- Gartner (10)
- Continuous Threat Exposure Management (CTEM) (9)
- Microsoft (8)
- In-Memory Attacks (7)
- Healthcare Cybersecurity (6)
- Advanced Threat Defense (5)
- Legacy Security (5)
- Artificial Intelligence (4)
- Financial Cybersecurity (4)
- Linux Cybersecurity (4)
- Fileless Malware (3)
- Threat and Vulnerability Management (2)
- Managed Service Providers (1)











.png?width=571&height=160&name=iso27001-(2).png)